[SAA + SAP] 14. CloudFront & AWS Global Accelerator
Overview
- DDoS protection, intergration with Shield, AWS Web application Firewall.
Origins
- S3 bucket
- For distributing files and caching them at the edge
- Enhanced security with CloudFront Origin Access Identity (OAI)
- CloudFront can be used as an ingress (to upload files to S3)
- Custom Origin (HTTP)
- App load balacner
- EC2 instances
- S3 website
- Any HTTP backend you want
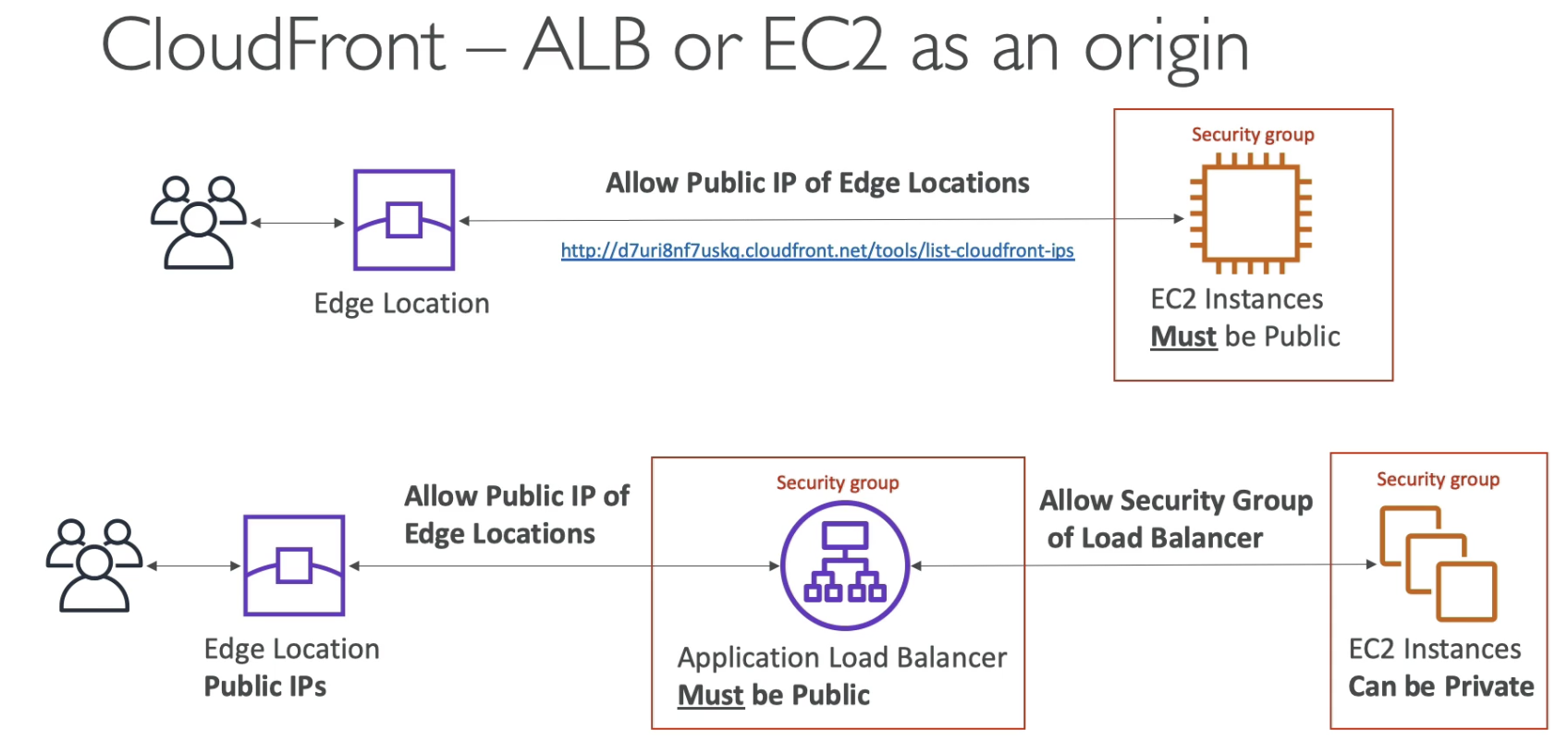
- Security Group should allow all Publlic IP of Edge locations
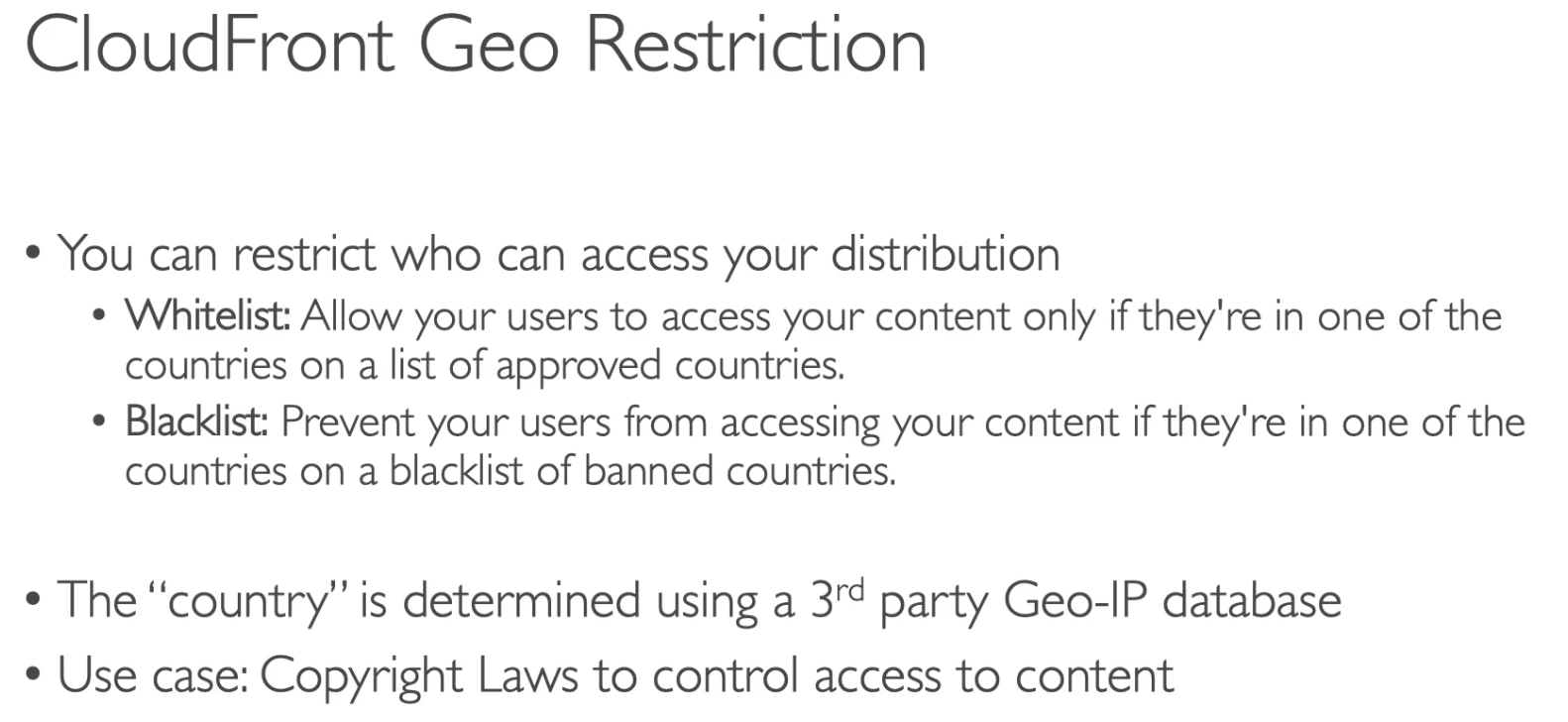

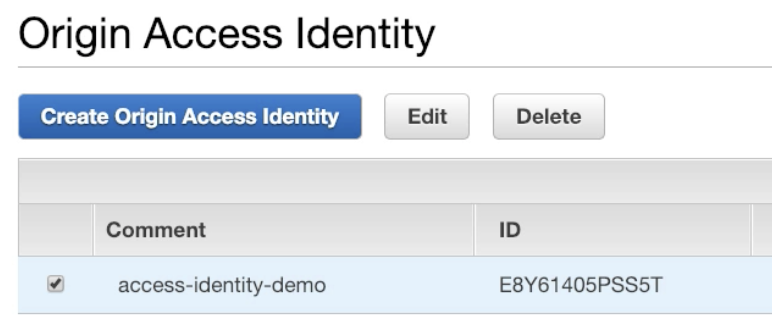
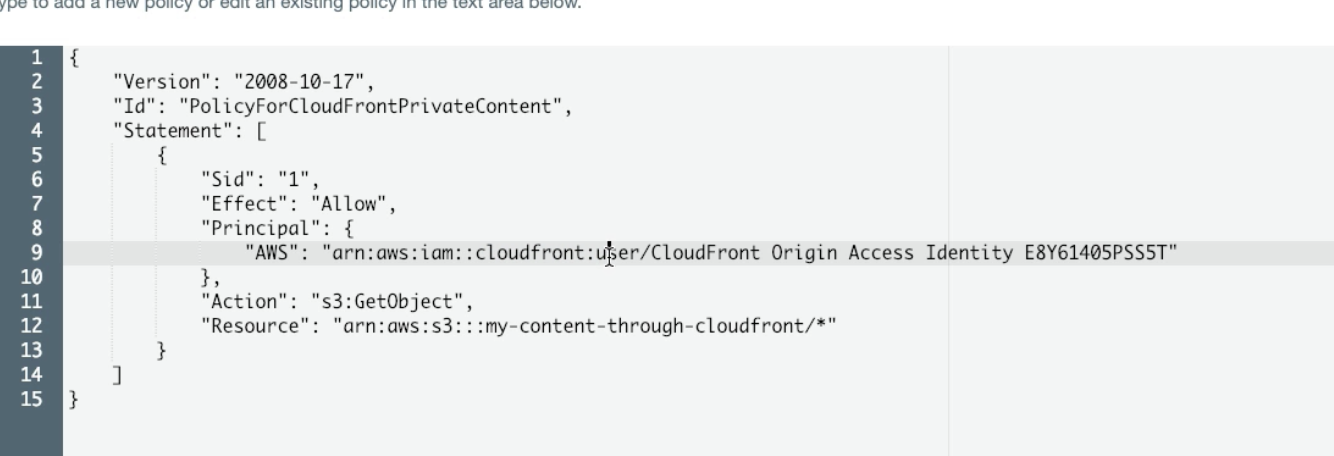
Origin Access Identity
- Origin S3 only allows CloudFront to access content

- Signed URL vs Signed Cookie
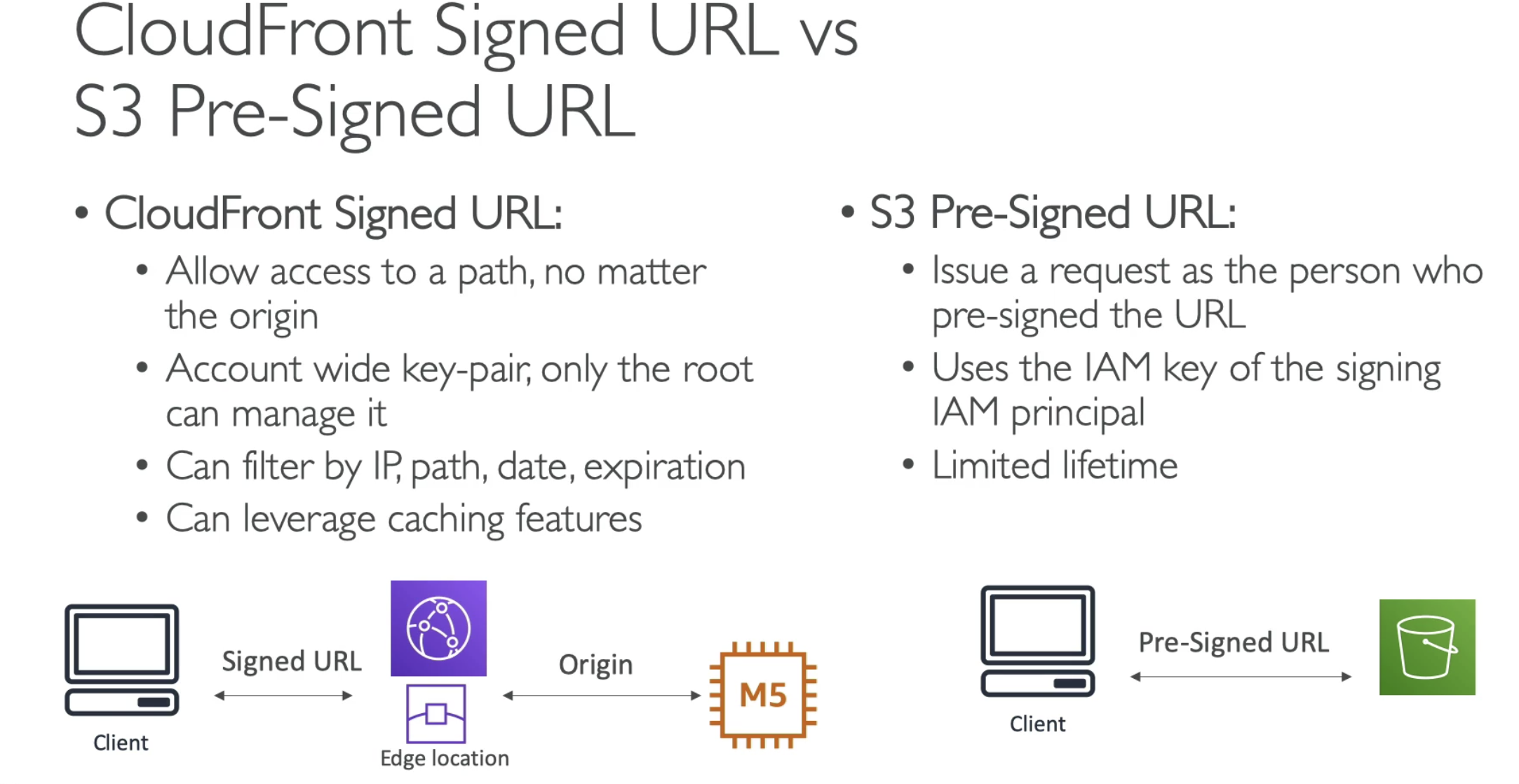
Only root user can create key-pair for cloudFront signed URL
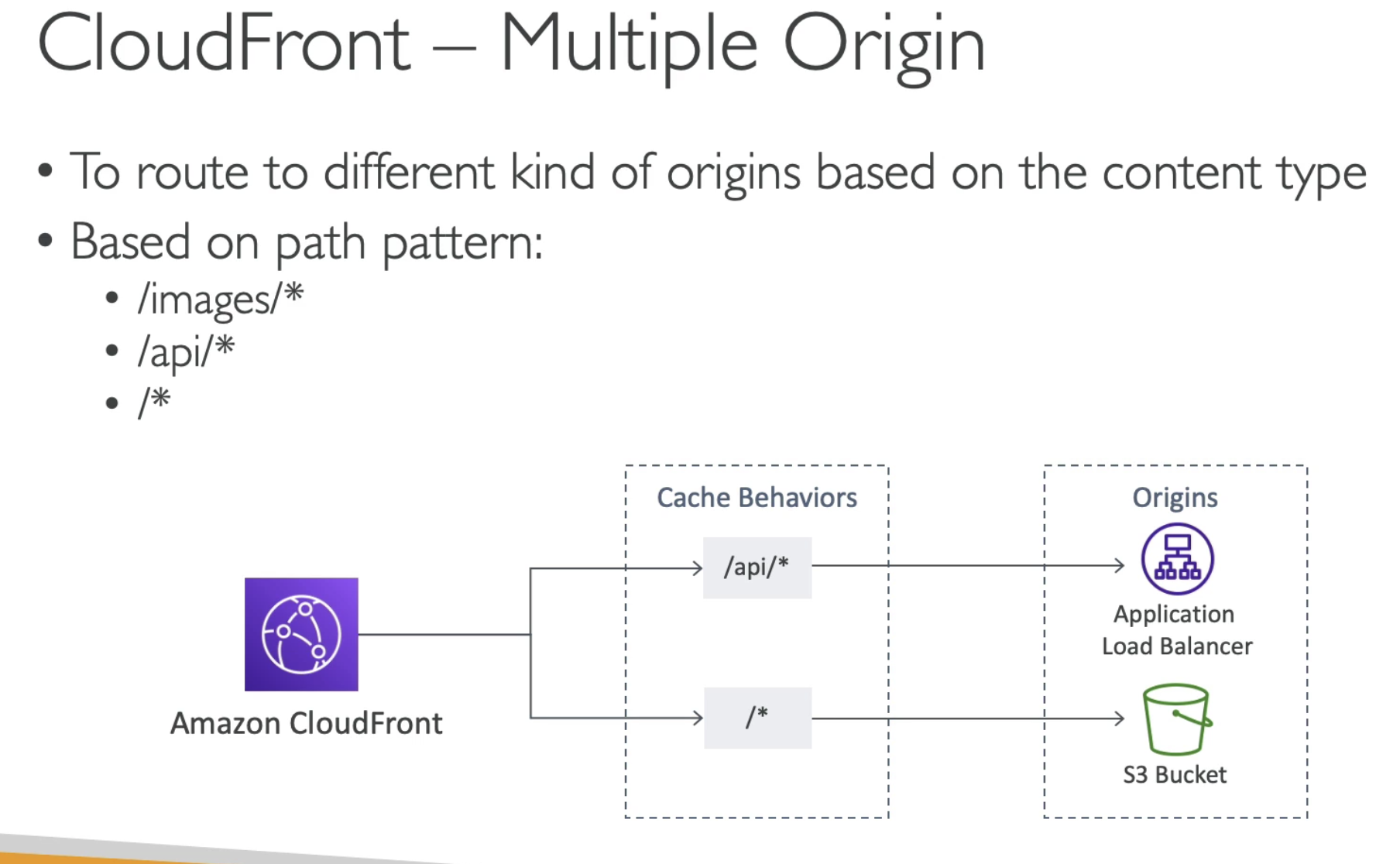
Multiple Origin is used to defined different cache behaviors.
Redirect to different origin based on router
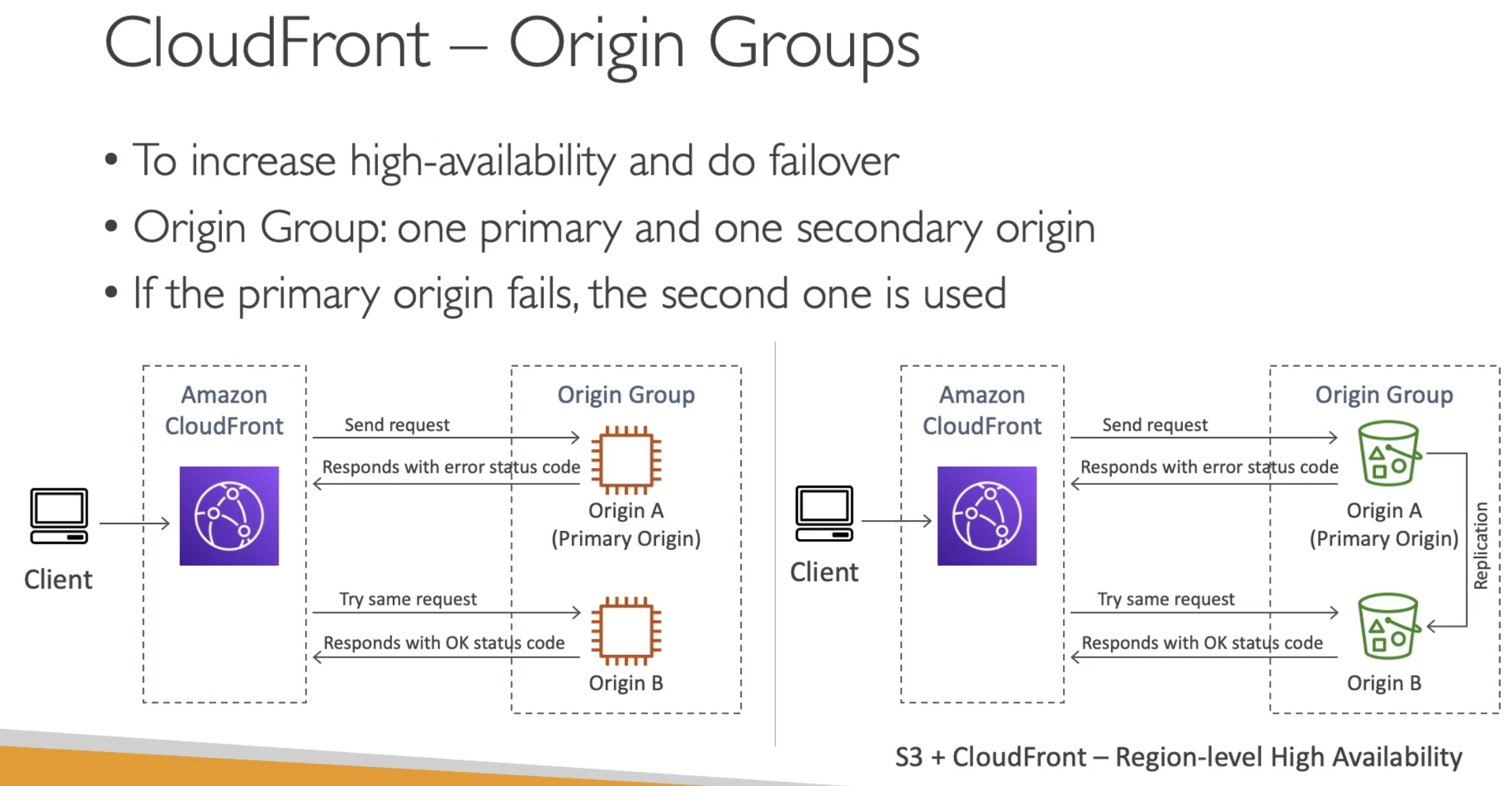
- Origin groups for failover
- S3 can have Replication CRR for high availability
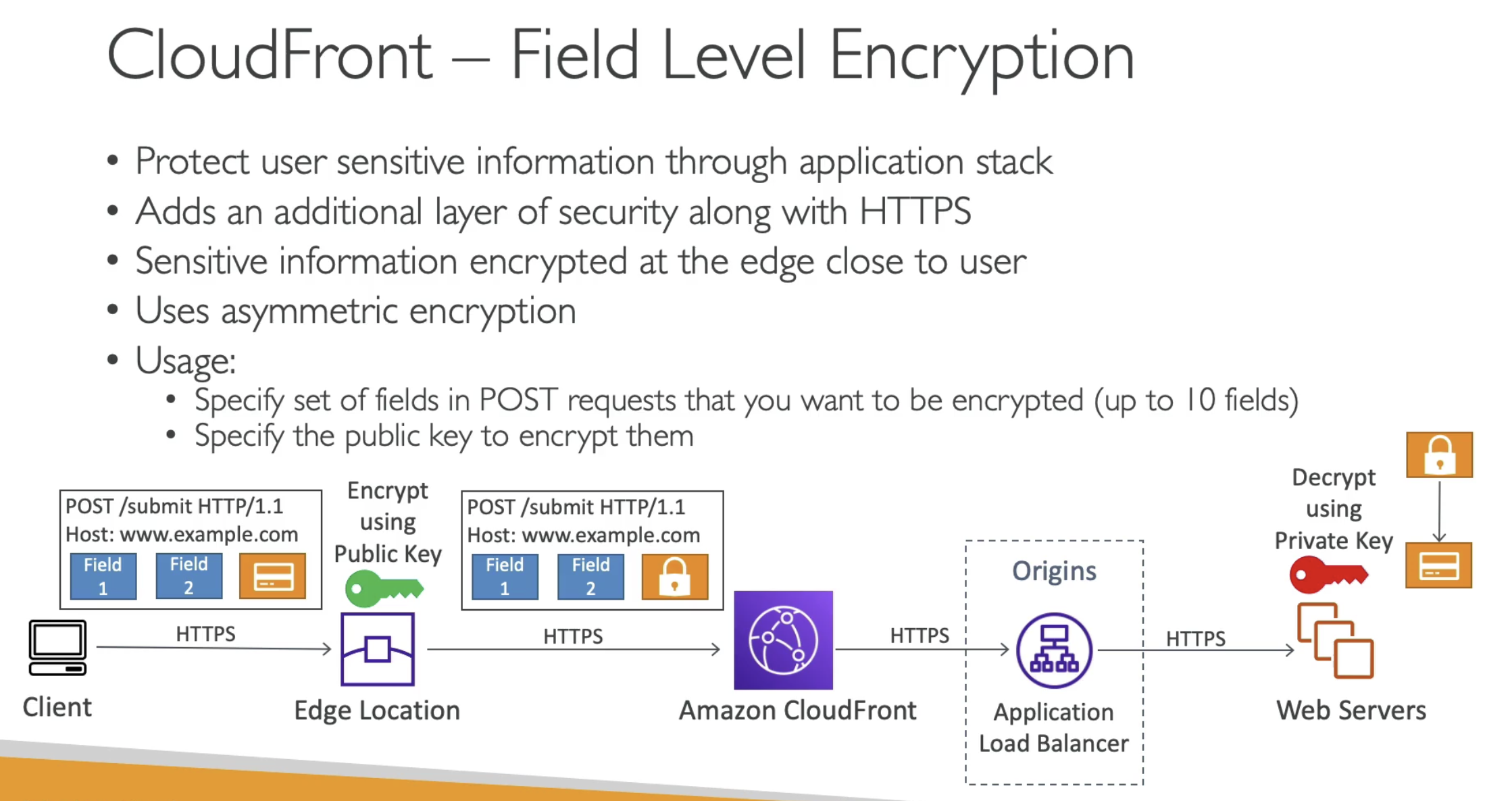
From Client side, need to defined what fields in the request should be encryption.
Then on the edge location, will encrypt the field by using an Public key
On the web server will use the private key to decrypt it.


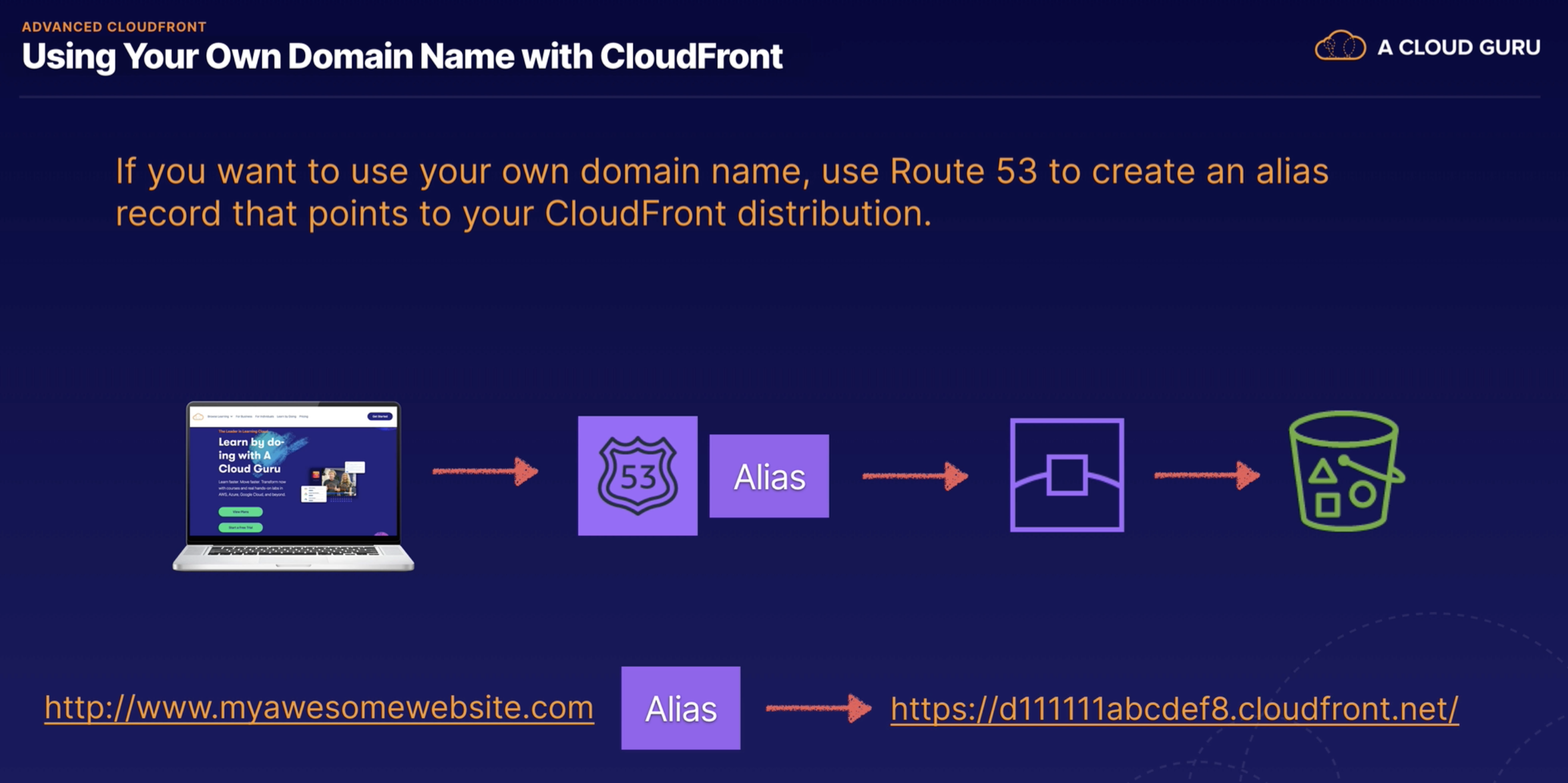
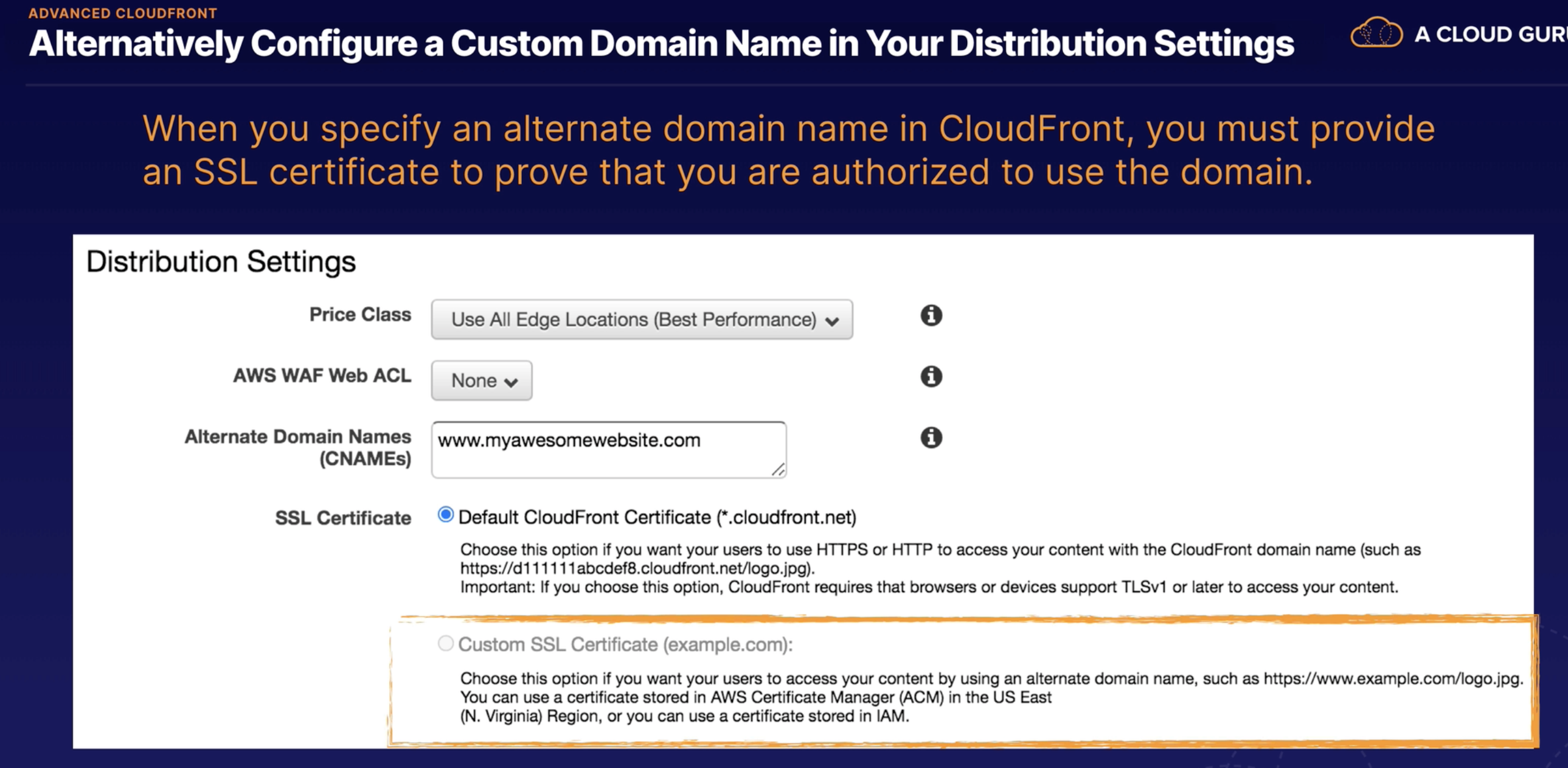
AWS Global Accelerator
Problems and Goals


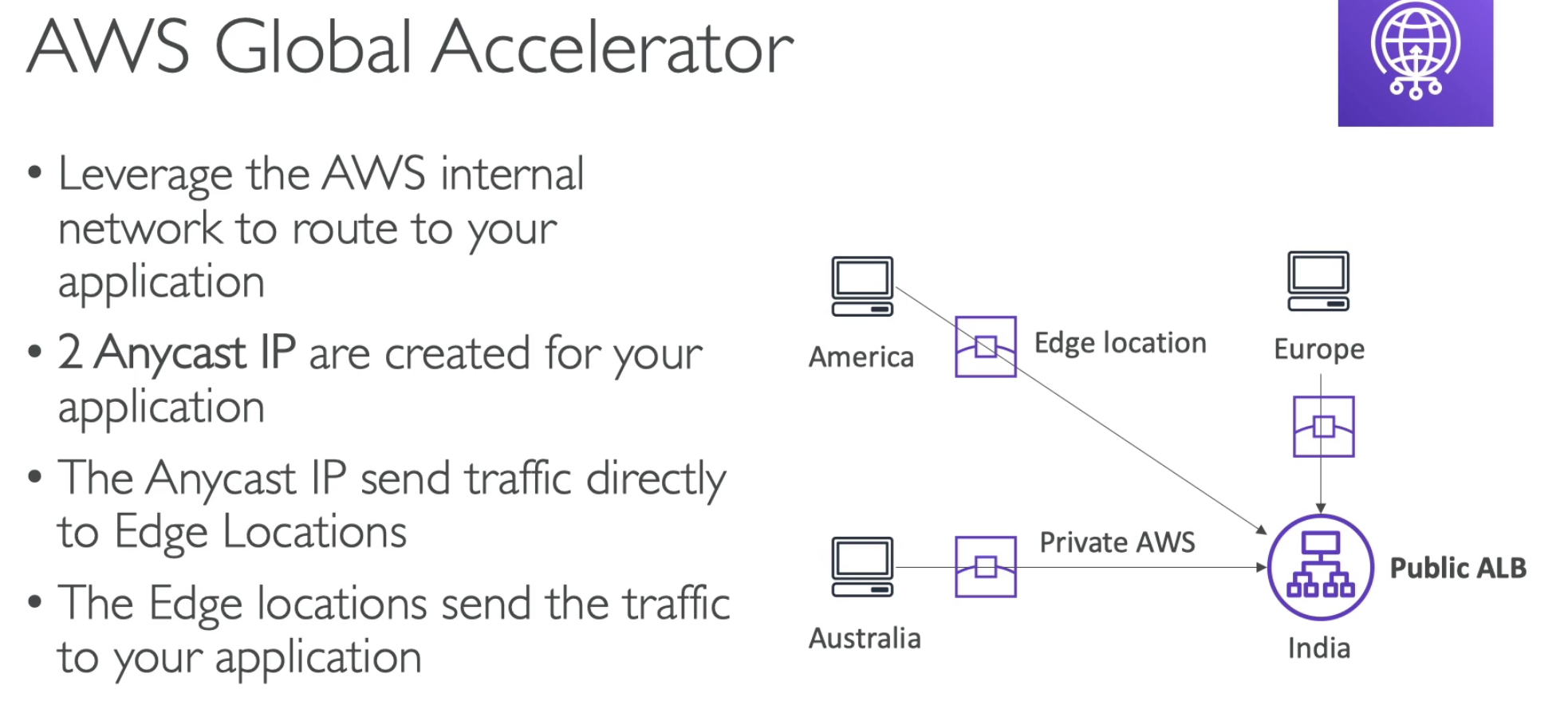
- Client goes to nearest edge location
- Form edge location goes to server through private AWS network

- Health check for DR
- No cache
- DDoS protection with AWS Shield
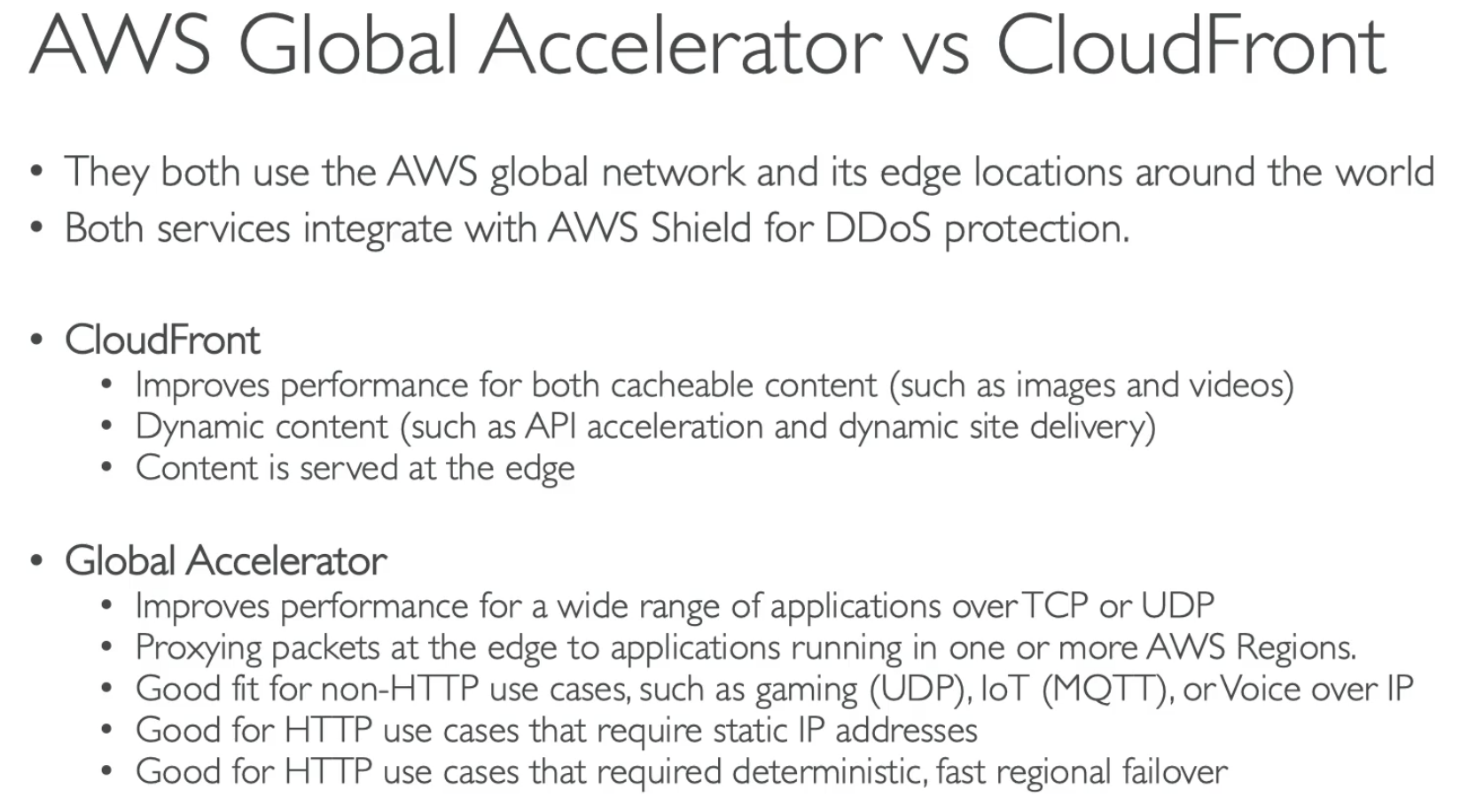
- Global accelerator: no cache, good for regional failover.
SAP
Caching

- Cache can based on many things, for example, headers, cookies, query string params.
- We want to maximize the cache hit to minimzie the origin request
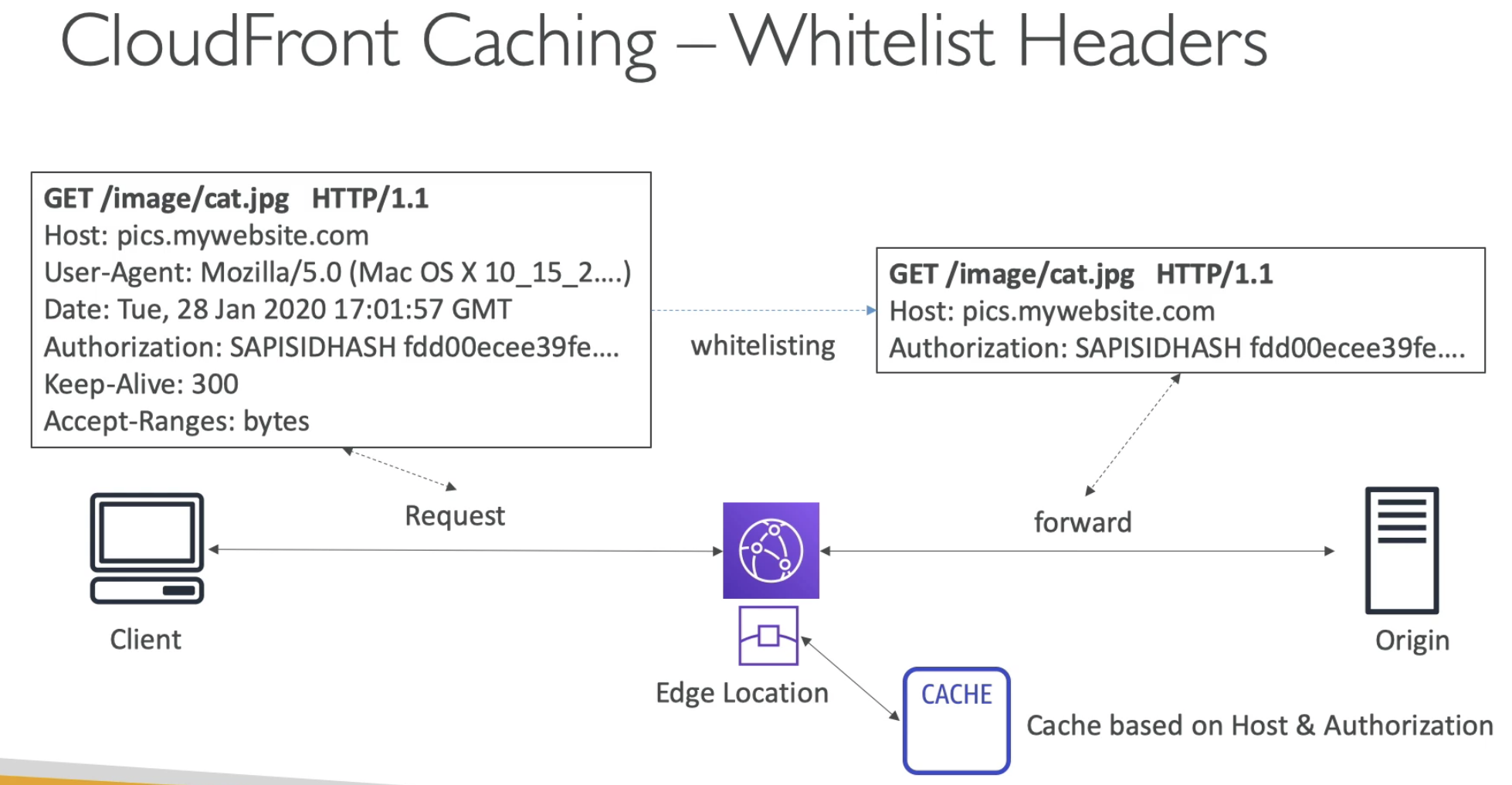
- There are many things in Headers, if we based on all the props in headers, then all the requests will be forwarded to Origin
- So we can use Whitelist to select some important header we want to consider to cache the request/response

- All the static content can be cached for maximizing cache hits, for static requests, can talk to S3 for exp.
- Dynamic content, we use Whitelist to cache the request
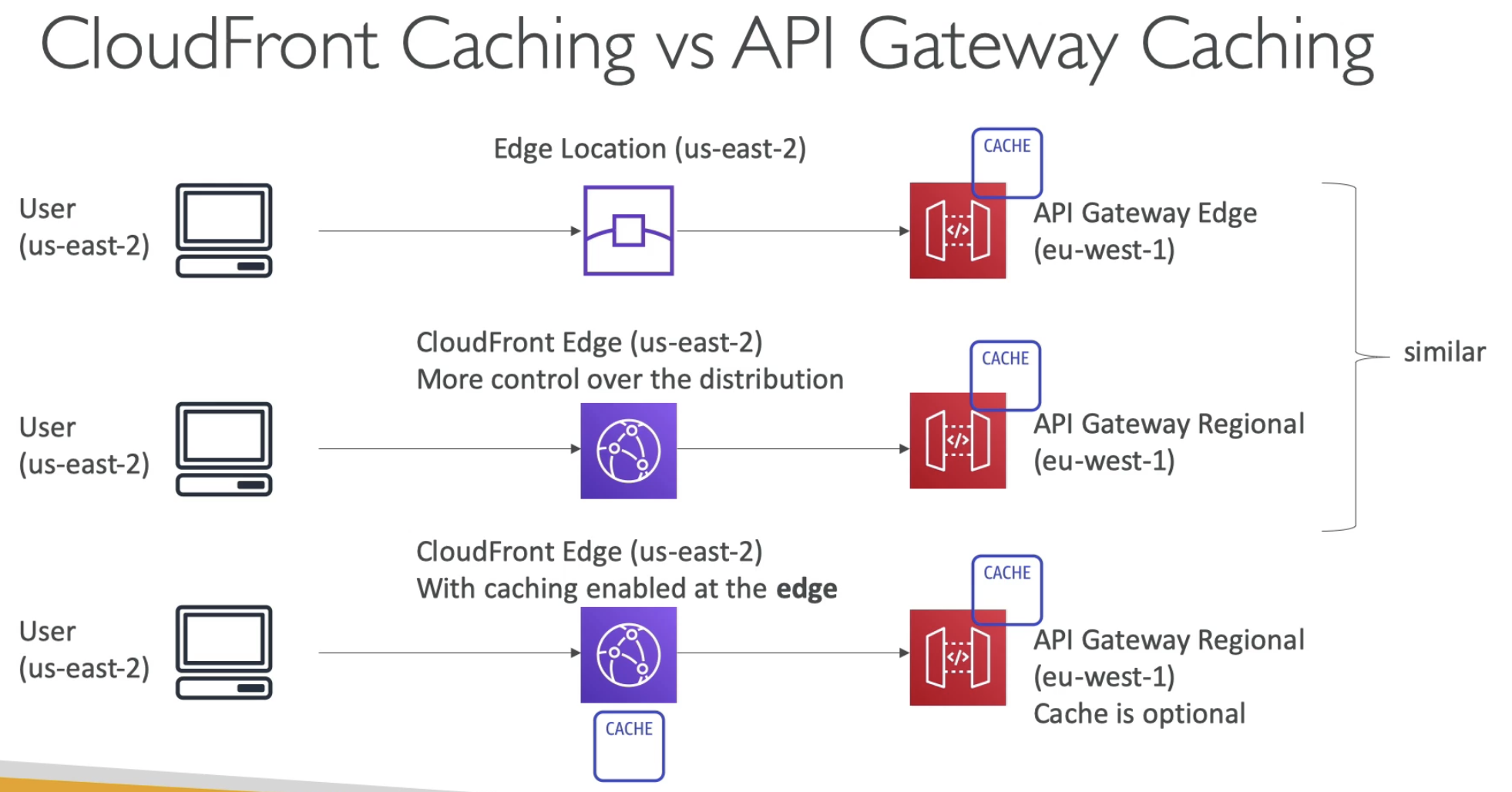
- Api gateway edge + cache on api gateway
- CloudFront edge + ( api gateways regional + cache): you can control over distribution
- (CloudFront edge + cache ) + (Api gateway + cache): you can disable api gateway cache, just rely on cache on CloudFront.
Lambda@Edge
- You have deployed a CDN using CloudFront
- What if you want to run a global AWS Lambda alongside?
- Or how to implement request filtering before reaching your application
- For this, you can use Lambda@Edge: deploy Lambda function alongside your CloudFront CDN
- Build more responsive applications
- You don't manage servers, Lambda is deployed globally
- Customize the CDN content
- Pay only for what you use

- Lambda@Edge does NOT have any cache
- It only to change requests/response
- Lambda@Edge is able to normalize query params to improve cache ratio
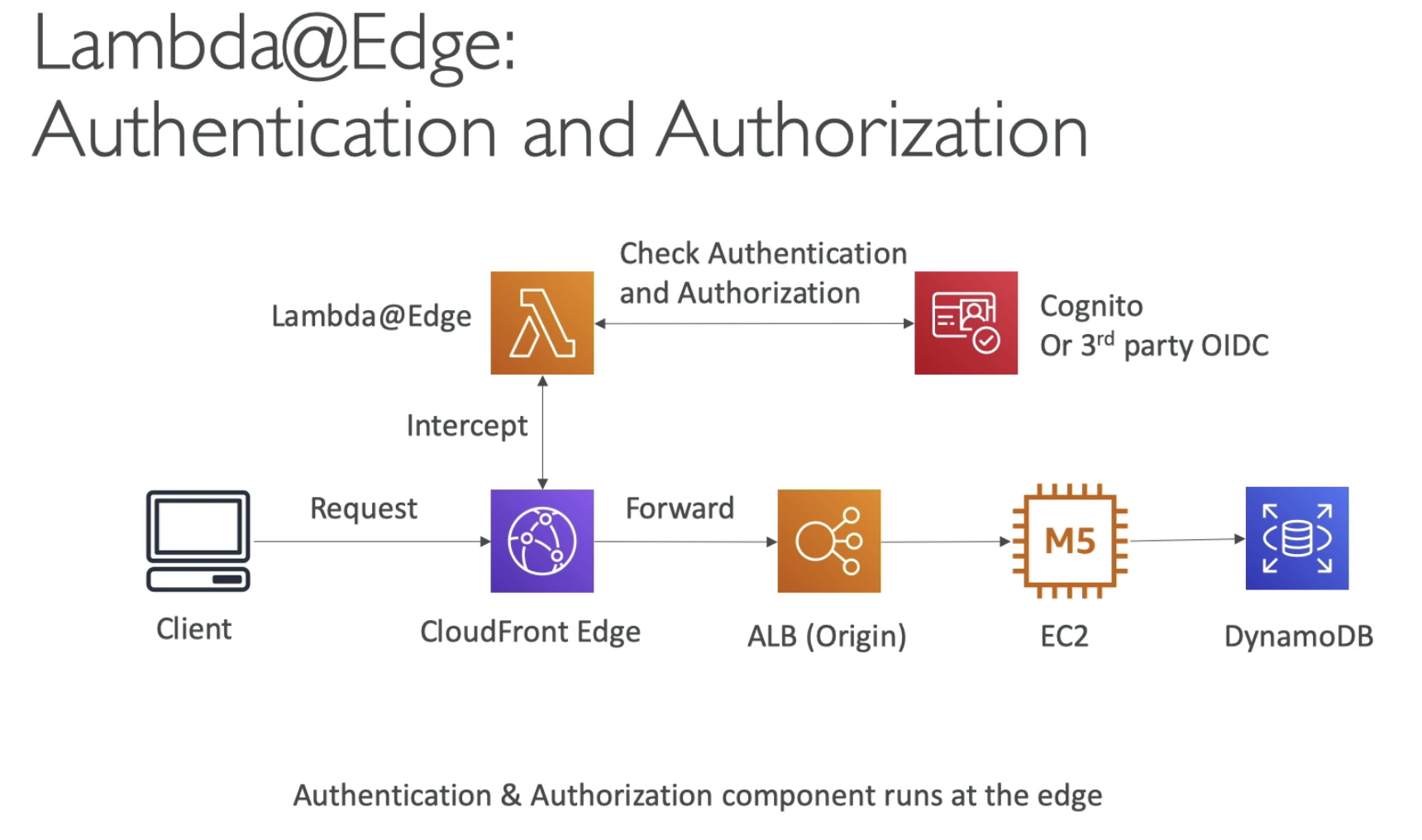
- Use for Auth at CloudFront, before reaching our server

- There are two SSL Certs to manage
- Not forward header CloudFron Origin === ALB Hostname
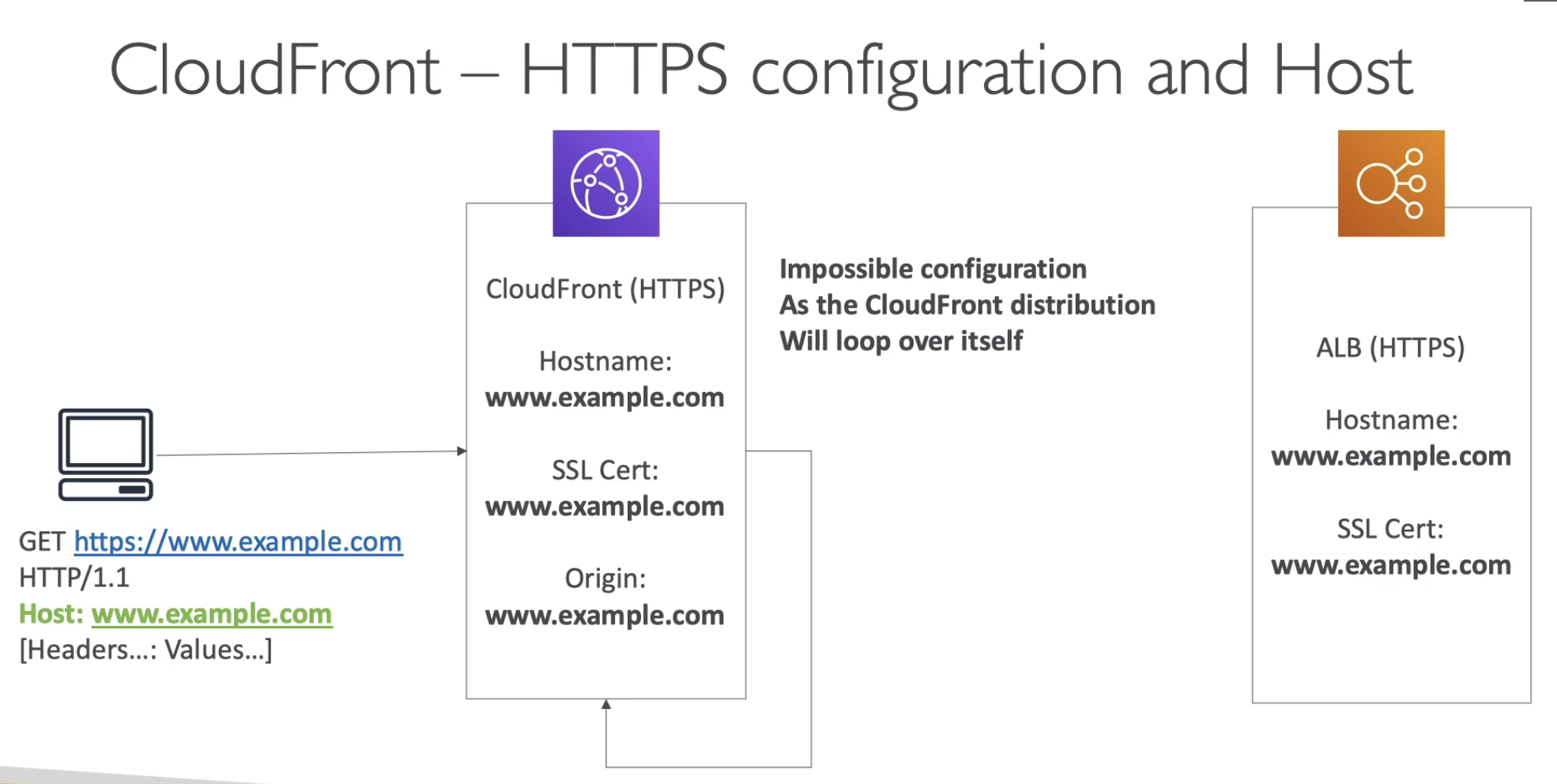
- Self loop
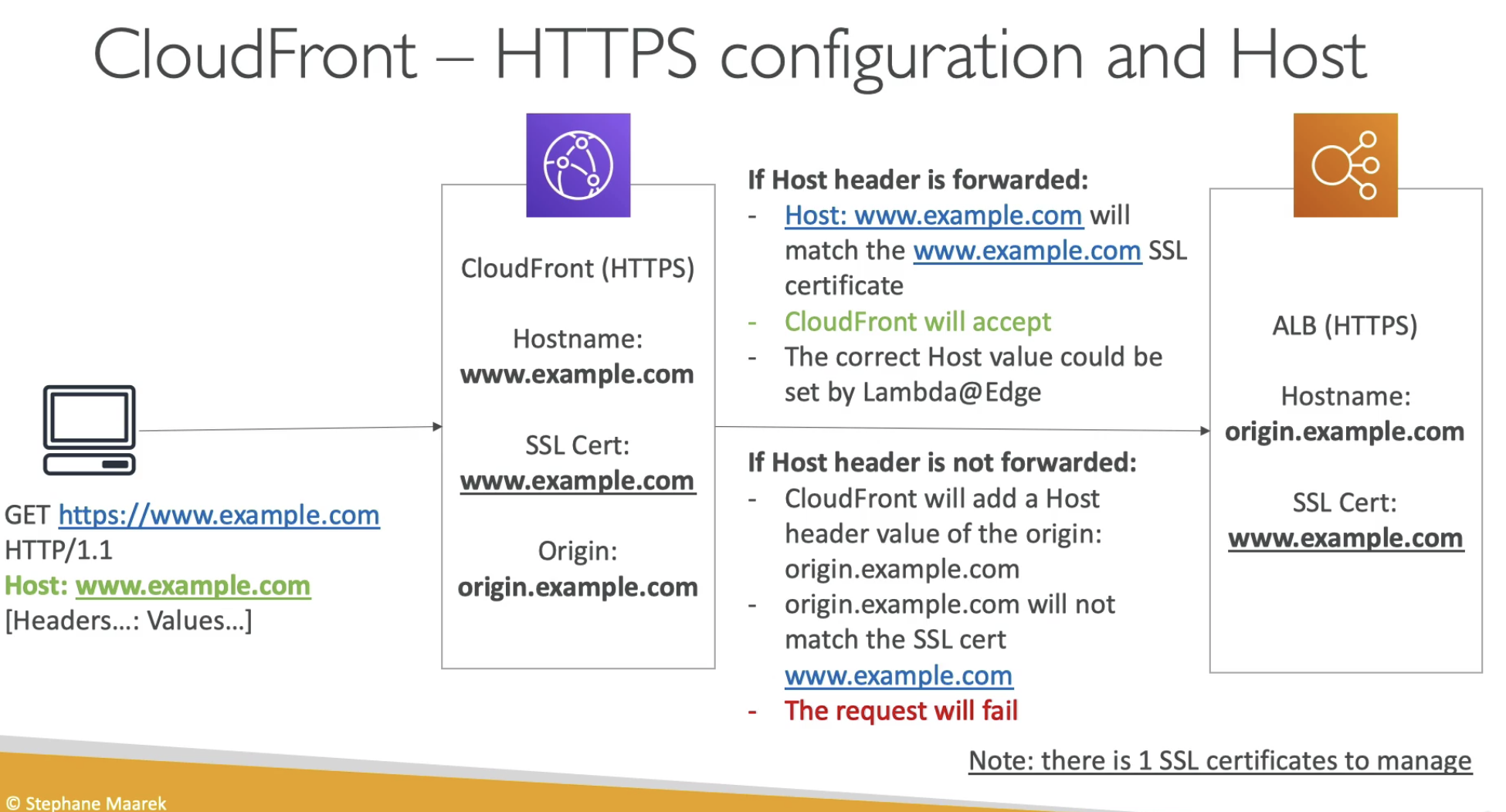
- Forward header
- CloudFront Origin === ALB Hostname
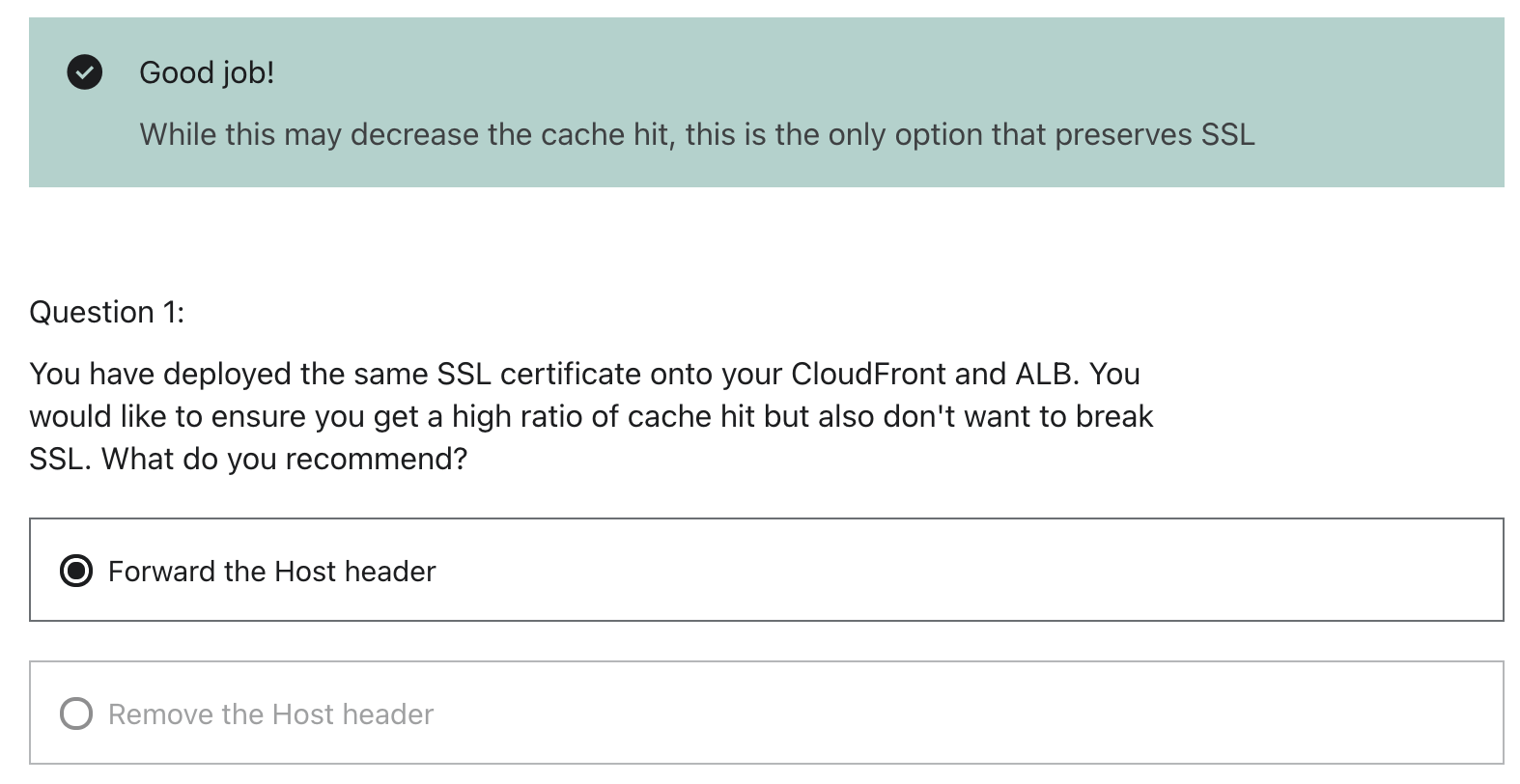
- Only 1 SSL, you need to forward the header

- ALB has to be public, otherwise, cloudFront cannot talk to it
- CloudFront should be public always



 浙公网安备 33010602011771号
浙公网安备 33010602011771号