[SAA + SAP] 02. Security
SAA
KMS
- Encrypted secrects can be stored in the code / environment variable
- data > 4 KB envolope encryption
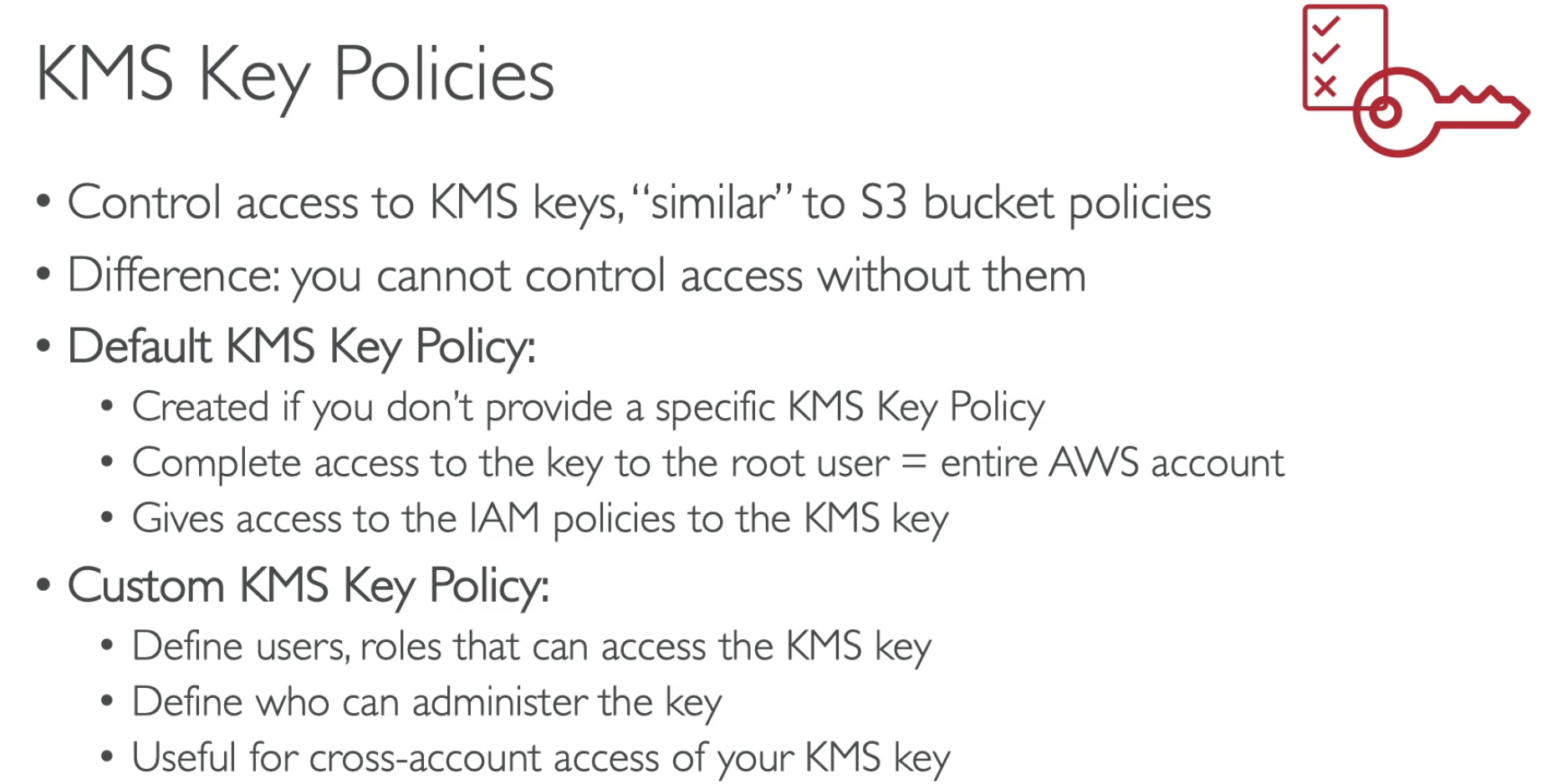
- To give access to KMS to someone:
- Make sure the Key Policy allows the user
- Make sure the IAM policy allows the API calls
- AWS managed KMS key are free to use, it is NOT necessary to create a "User Key" before using KMS
- KMS Key is regional.

Symmetric: same key for both encrypt and decrypt.
Asymmetric: Public (Encrypt) / Private key (Decrypt)

Default KMS key: Shared across all AWS account users.
Custom: Define who (include cross-account) / which role.
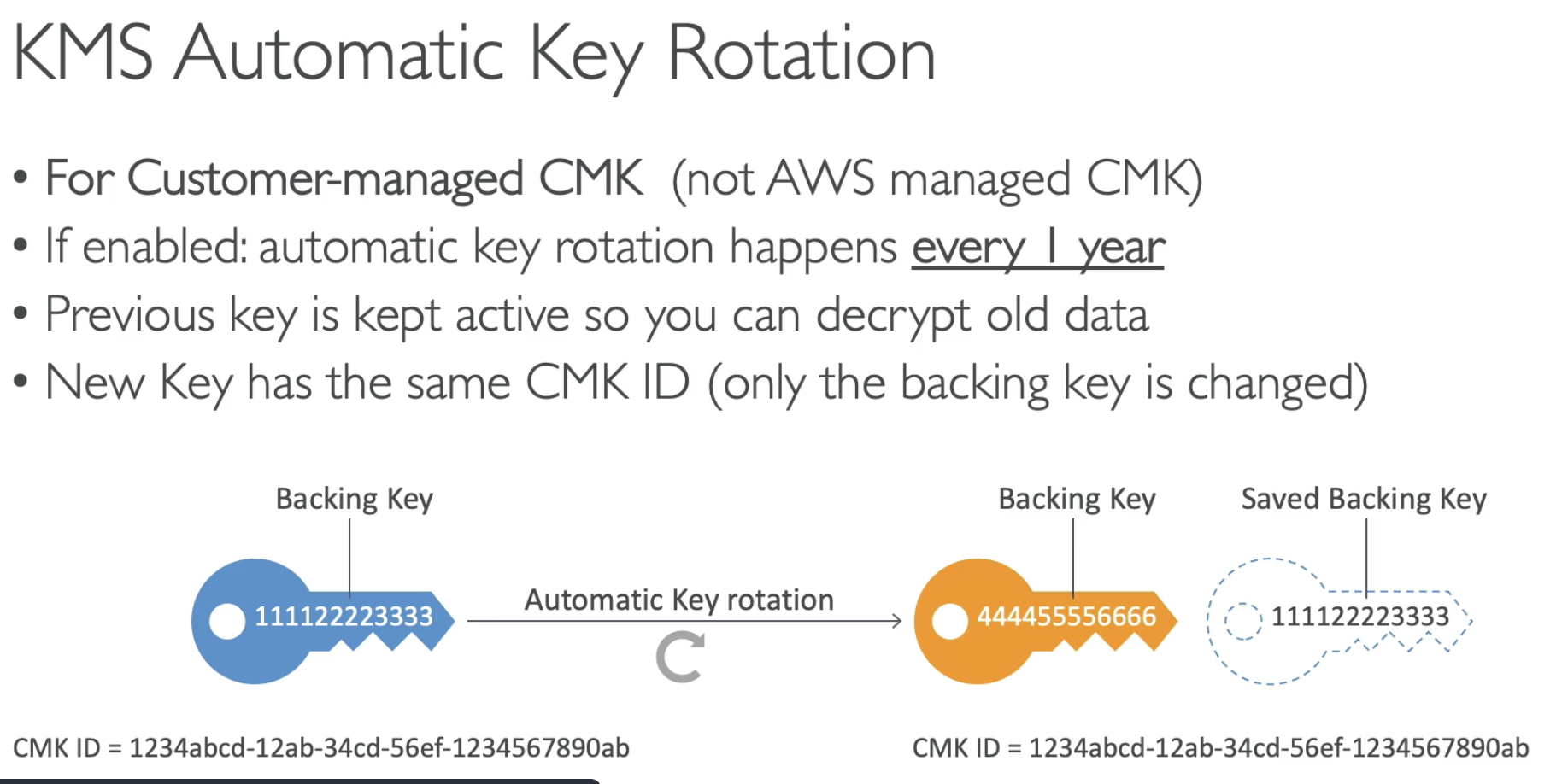
- For customer-managed CMK.
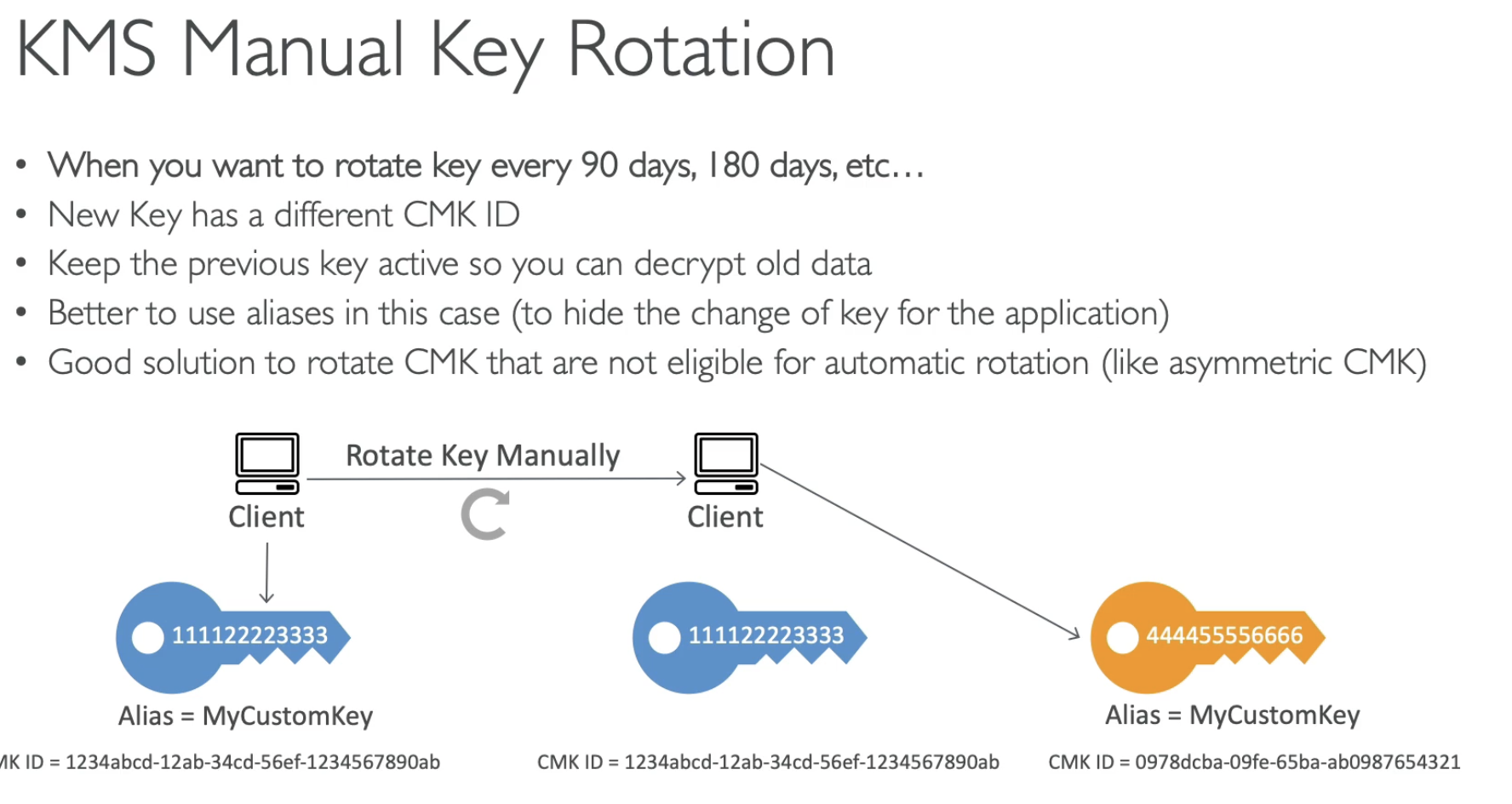
- automatic roataion 1 year
CMK auto rotation happen every year! If you want less than one year, you need to rotate it manully
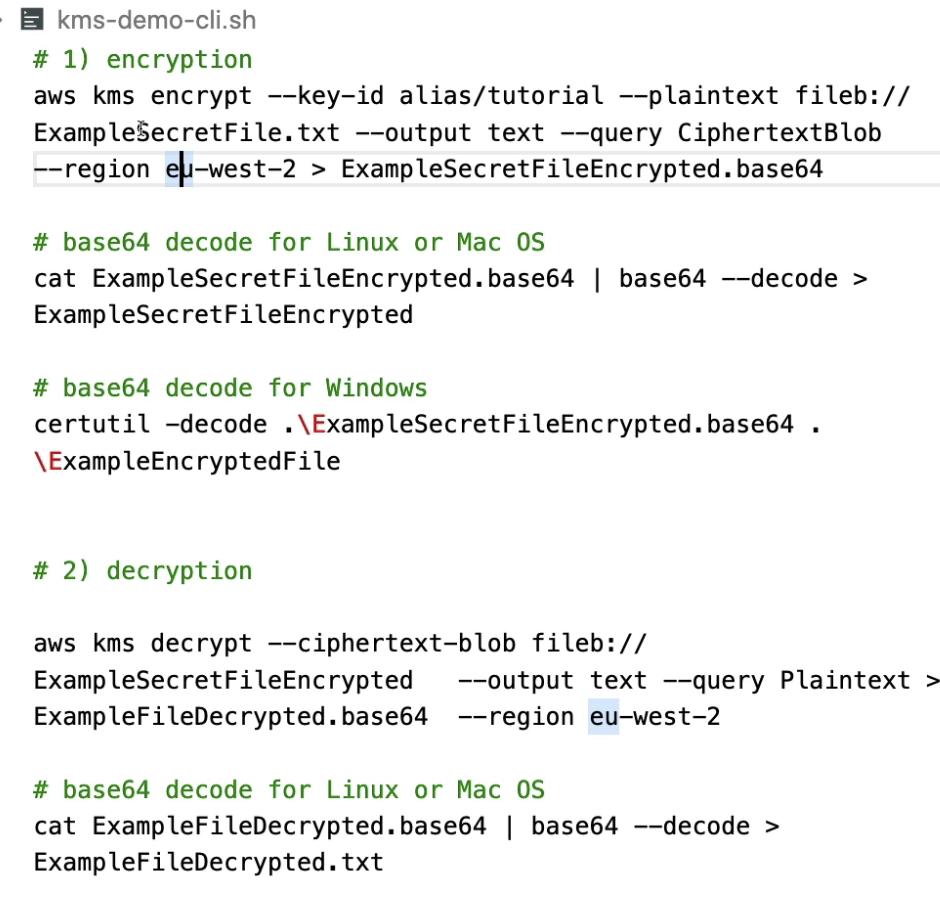
- First, encrypt to a base64 file
- Then convert this base64 file to an Encrypted file, this is the file you can share with other poeple.
- Decrypt the encrypted file to base64 file
- Decode based64 file
- Then conver based64 file to a readable file
SSM

- If using Lambda, you need to assign policy to Lambda role for ssm:readParaamter, and withDecryption; Also KMS:decrypt.
![]()
![]()
![]()
AWS Secrets Manager

Mainly for RDS.
- AWS provides hardware, you fully control the encryption key
- Use CloudHSM to generate SSE-C cncryption for S3


- There need to be a check of the EC2 instances directly from within the operating system
- AWS Inspector Agent must be installed on OS in EC2 instances
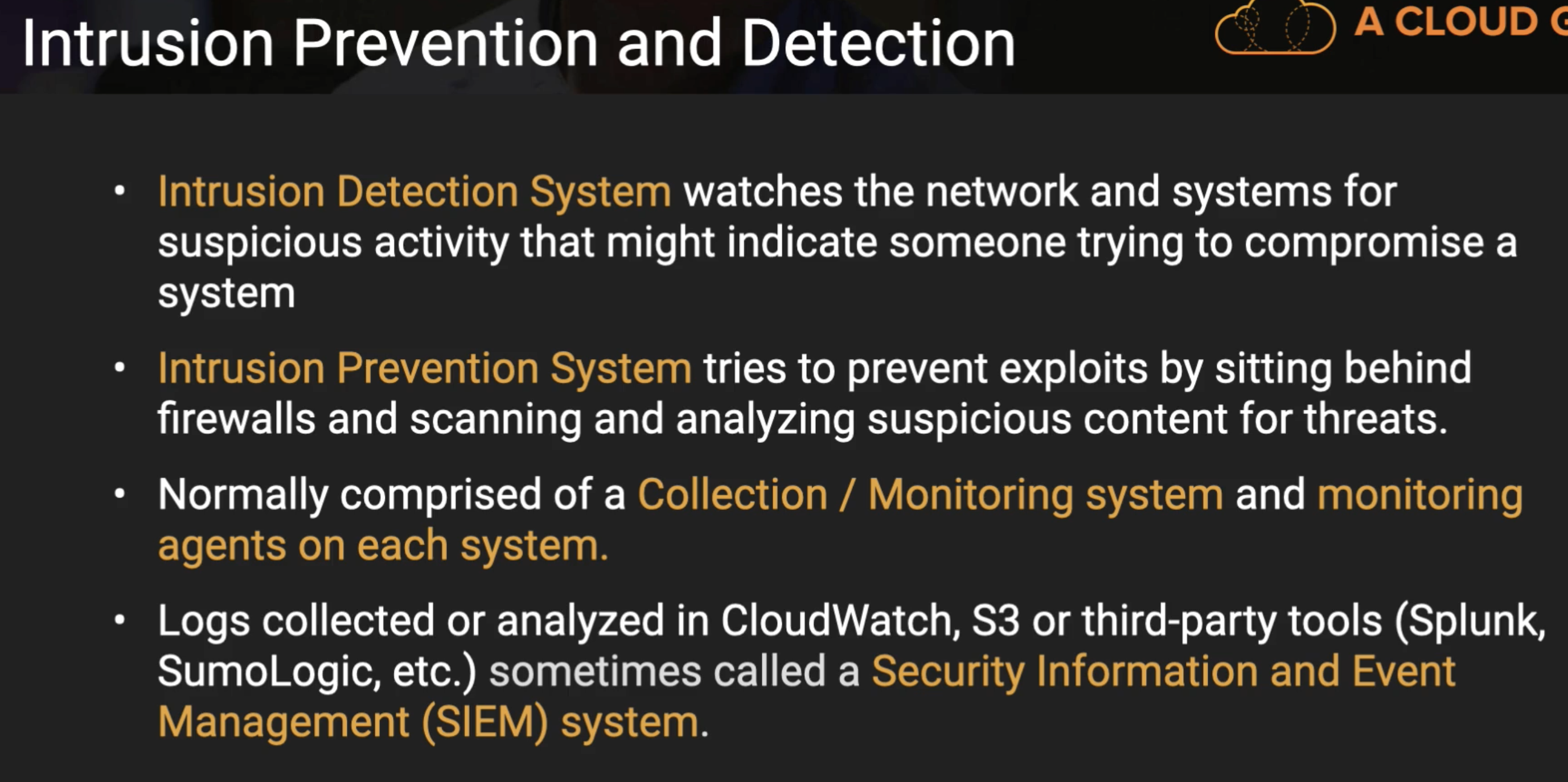
Inspector is for OS

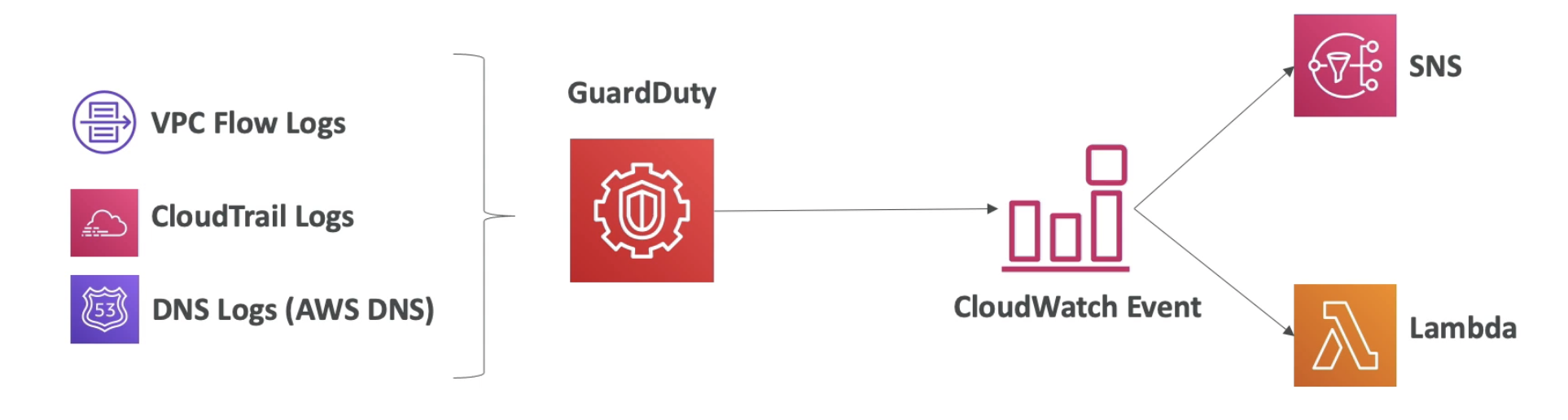
- Using Machine Learning to check Logs to detect unusal action.
AWS WAF - Web Application Firewall
- Protects your web appliations from common web exploits (Layer 7)
- Deploy on Application Load Balancer, CloudFront, API Gateway.
- Define WEB ACL (Web Access Control List):
- Role can include: IP addresses, HTTP headers, HTTP Body, or URI strings
- SQL Injection and XSS
- Size constraints, geo-match (block countries)
- Rate-based rule (to count occurrenences of event pre seconds/minute) - for DDoS pretection
AWS Firewall Manager
- Manage rules in all accounts of an AWS Organization
- Common set of security rules
- WAF rules
- AWS Shield Advanced
- Security Groups for EC2 and ENI resources in VPC
Manager -- centrally manage firewall rules, integrated with AWS Organizations
DDos attach is by overwarming the server to prevent user to access the service by sending huge amount to HTTPs request to server. So it is Layer 7.
WAF can set rule to deny some request comes in, so it works. But WAF is not designed for DDoS.
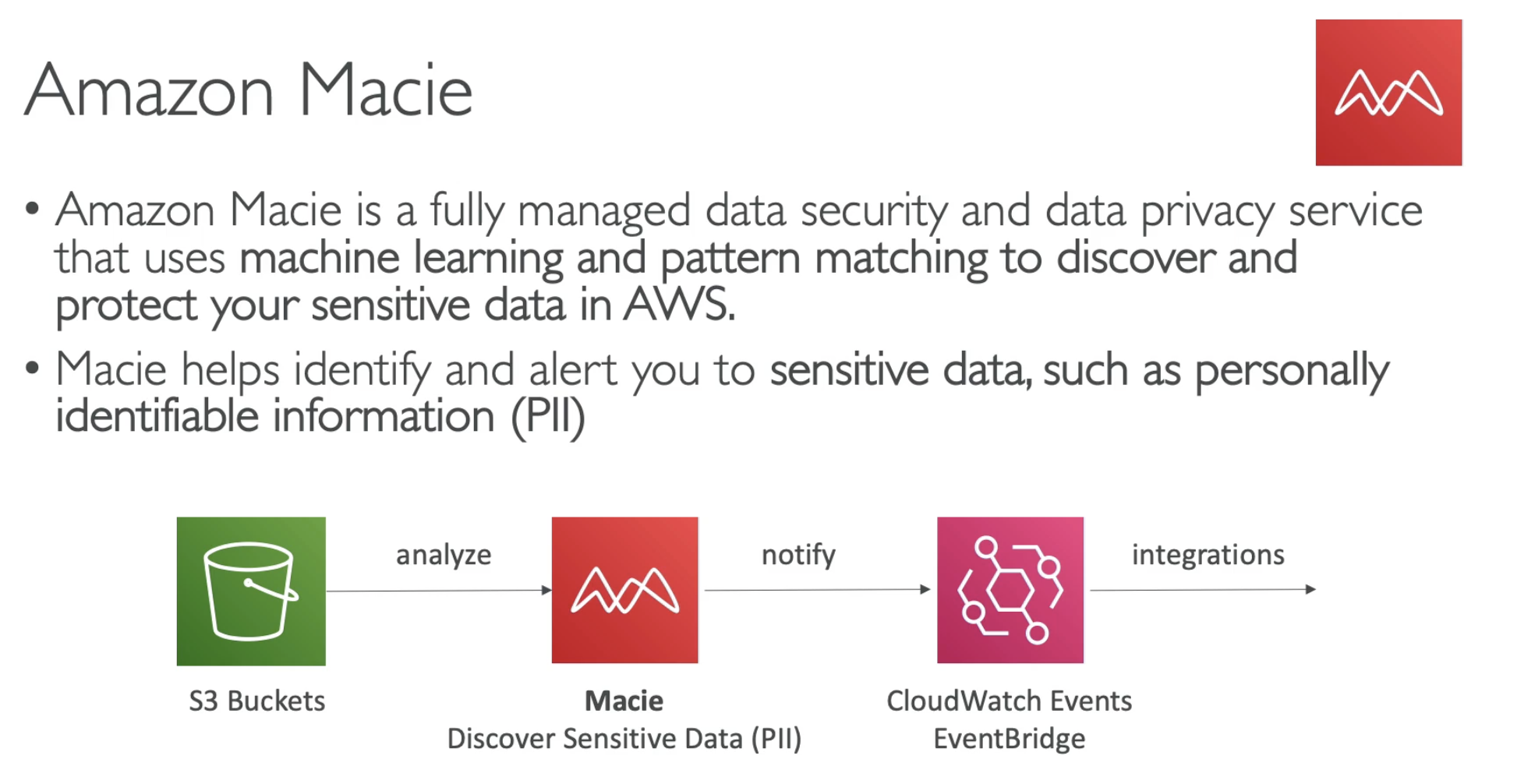
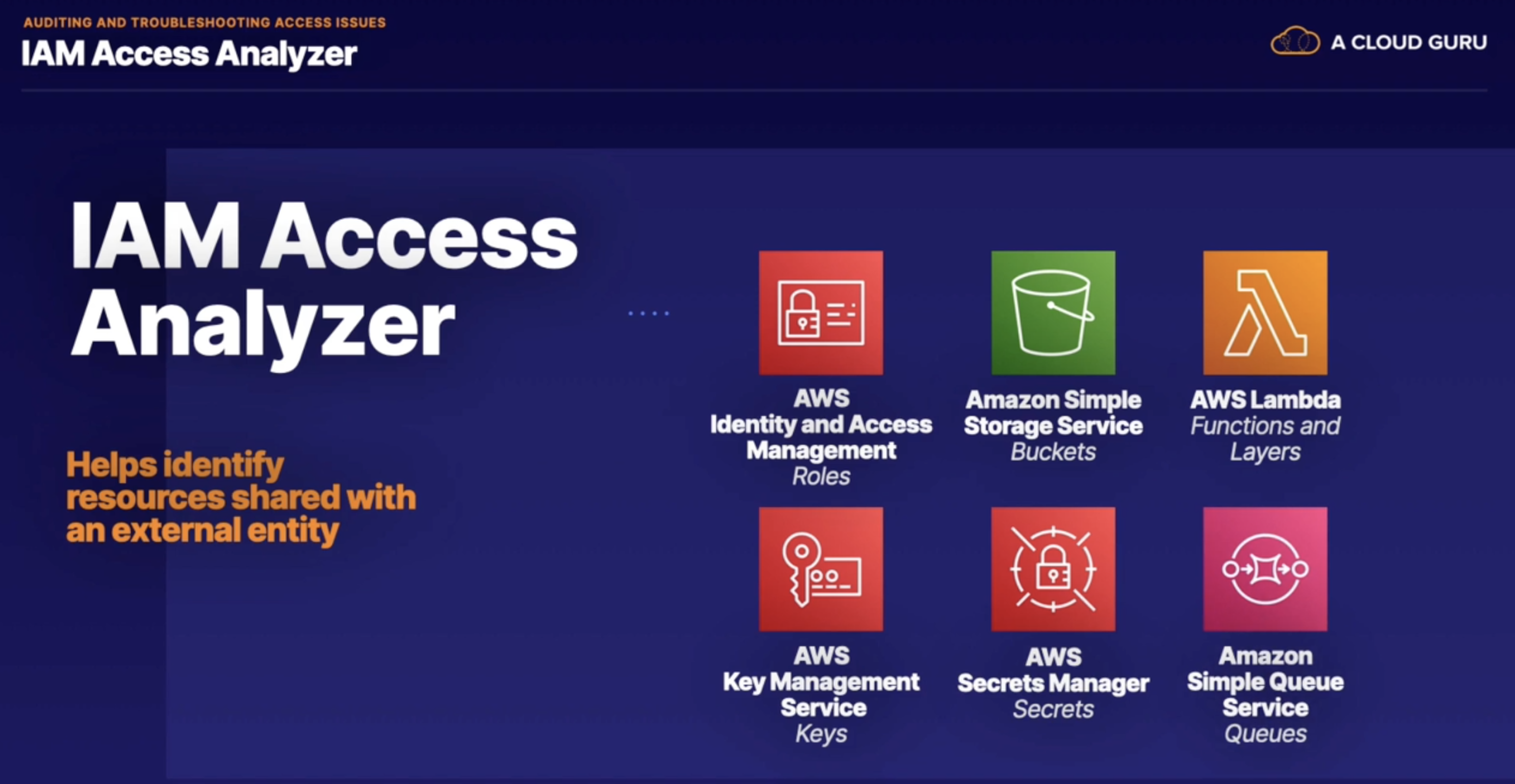
- Personaly identifiable information (PII)
SAP
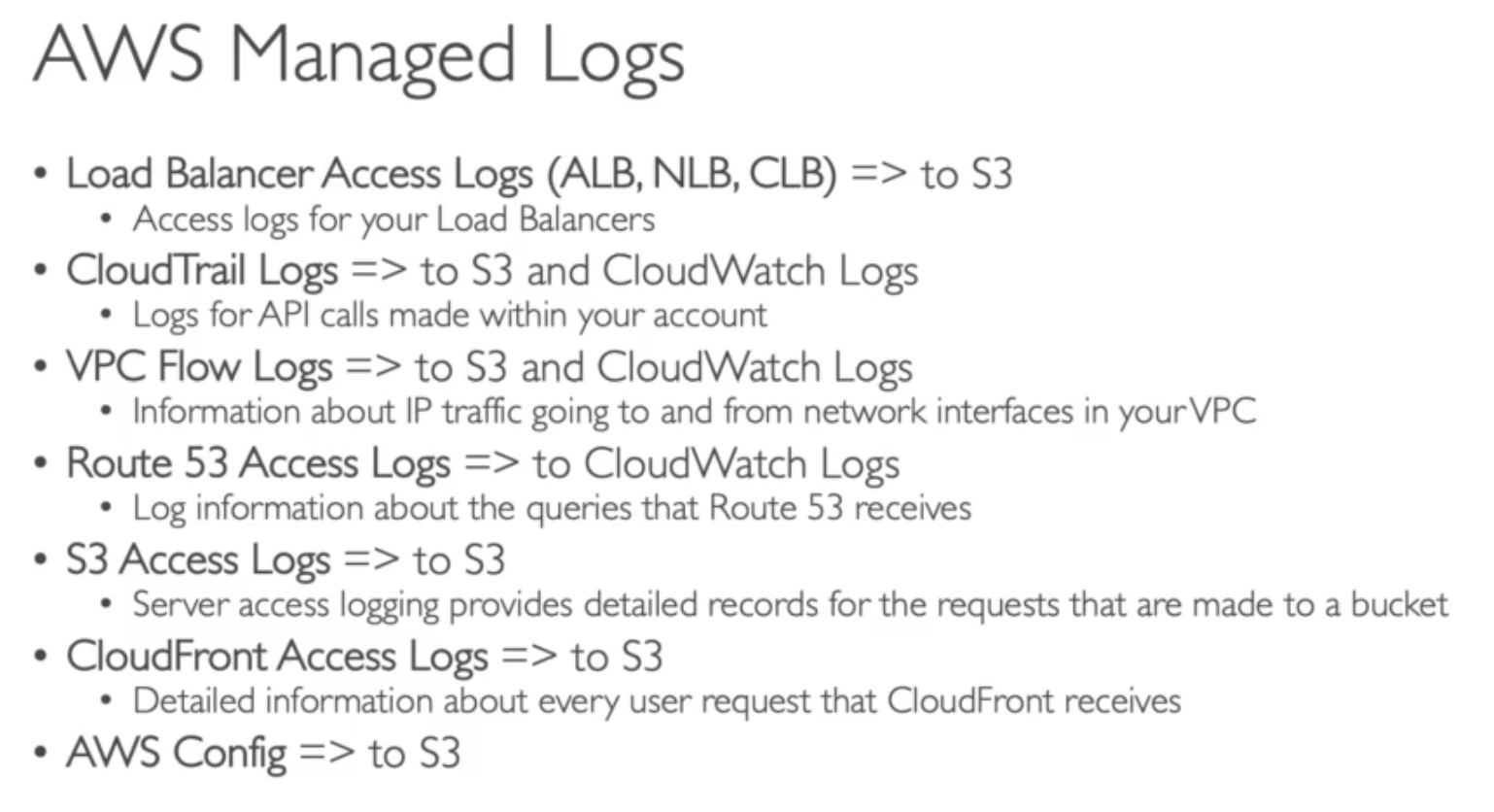
CloudTrail
- Shows past 90 days of activity
CloudTrail Trail:
- Get a detailed list of all the events you choose
- Can include events happening at the object level in S3
- Ability to store these events in S3 for further analysis
- Can be region specific or be global & include global events (IAM)
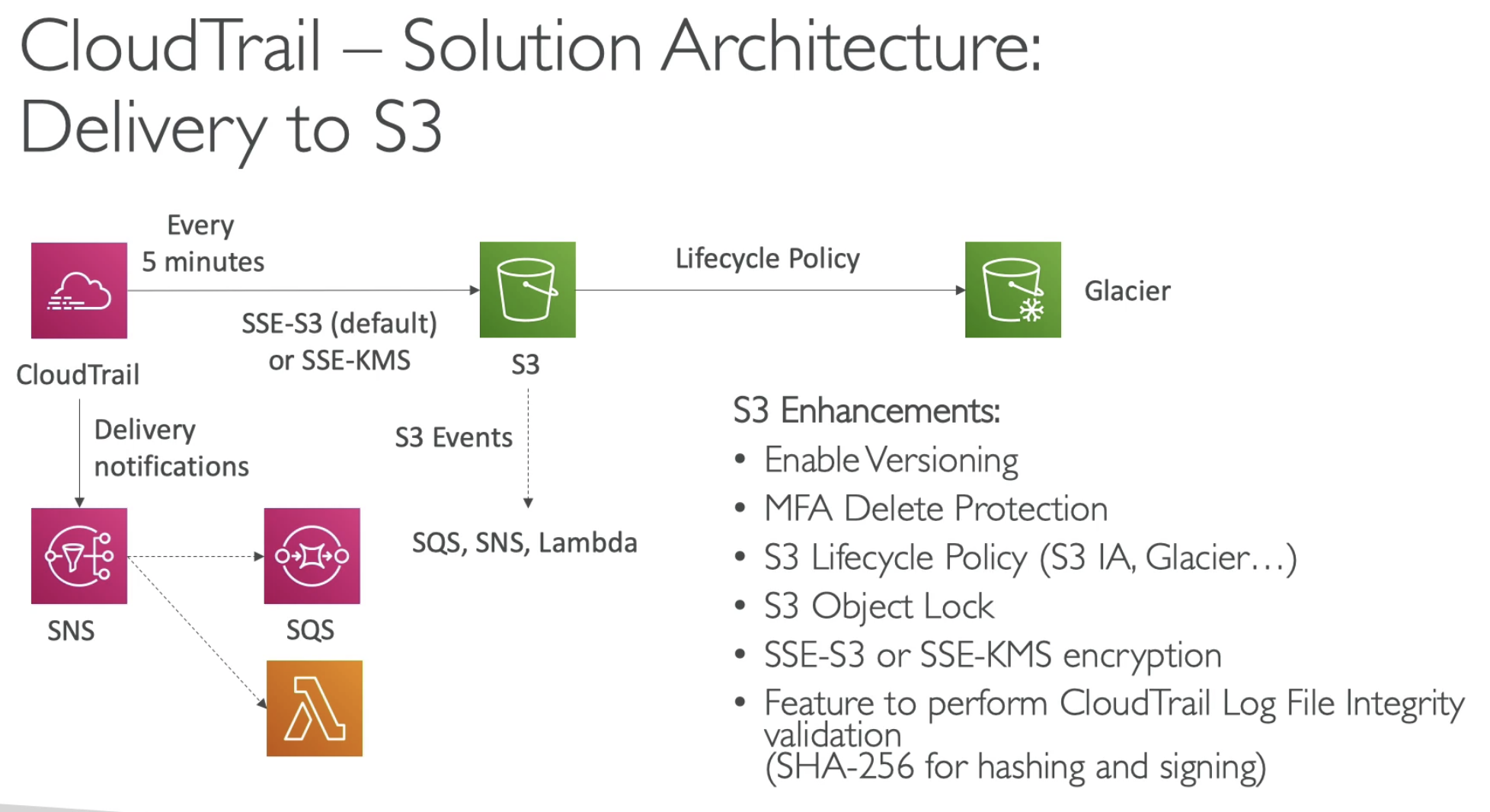
- You can dump logs into S3 every 5 mins for example
- S3 can choose to encrypt logs by using SSE-S3
- And you can setup Lifecycle policy for S3 to move older logs to Glacier
- From CloudTrail you can send notifications to SNS then fan out to SQS & Lambda
- From S3 Events notifications, you can also send to SQS, SNS, Lambda
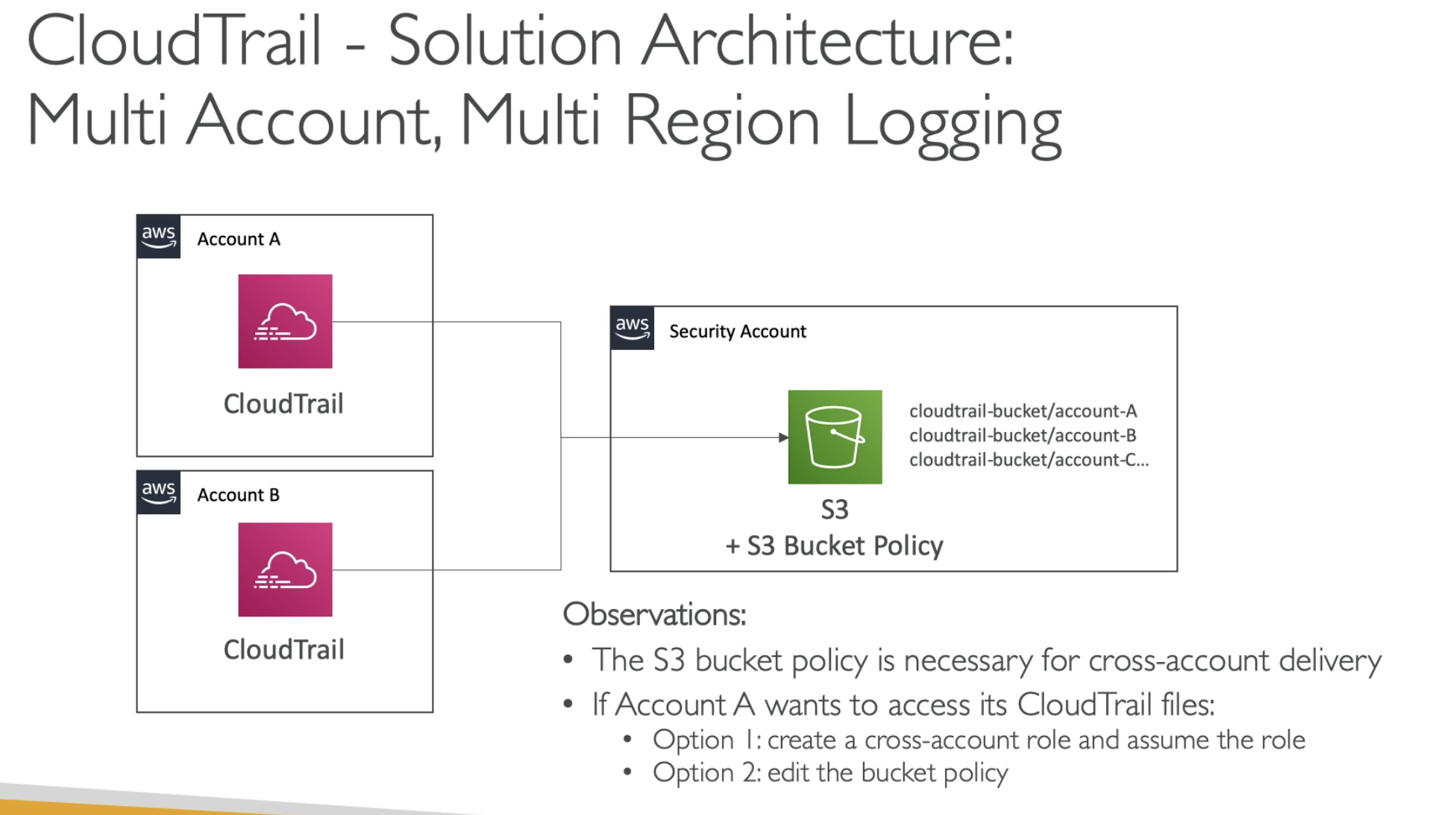
- Multi accounts CloudTrail can save logs to S3 in another Security Account
- Using S3 bucket policy to cross-account delivery
- To access logs in S3 from any CloudTrail account:
- 1 option: using s3 bucket policy
- 2 option: cross-account role and assume the role
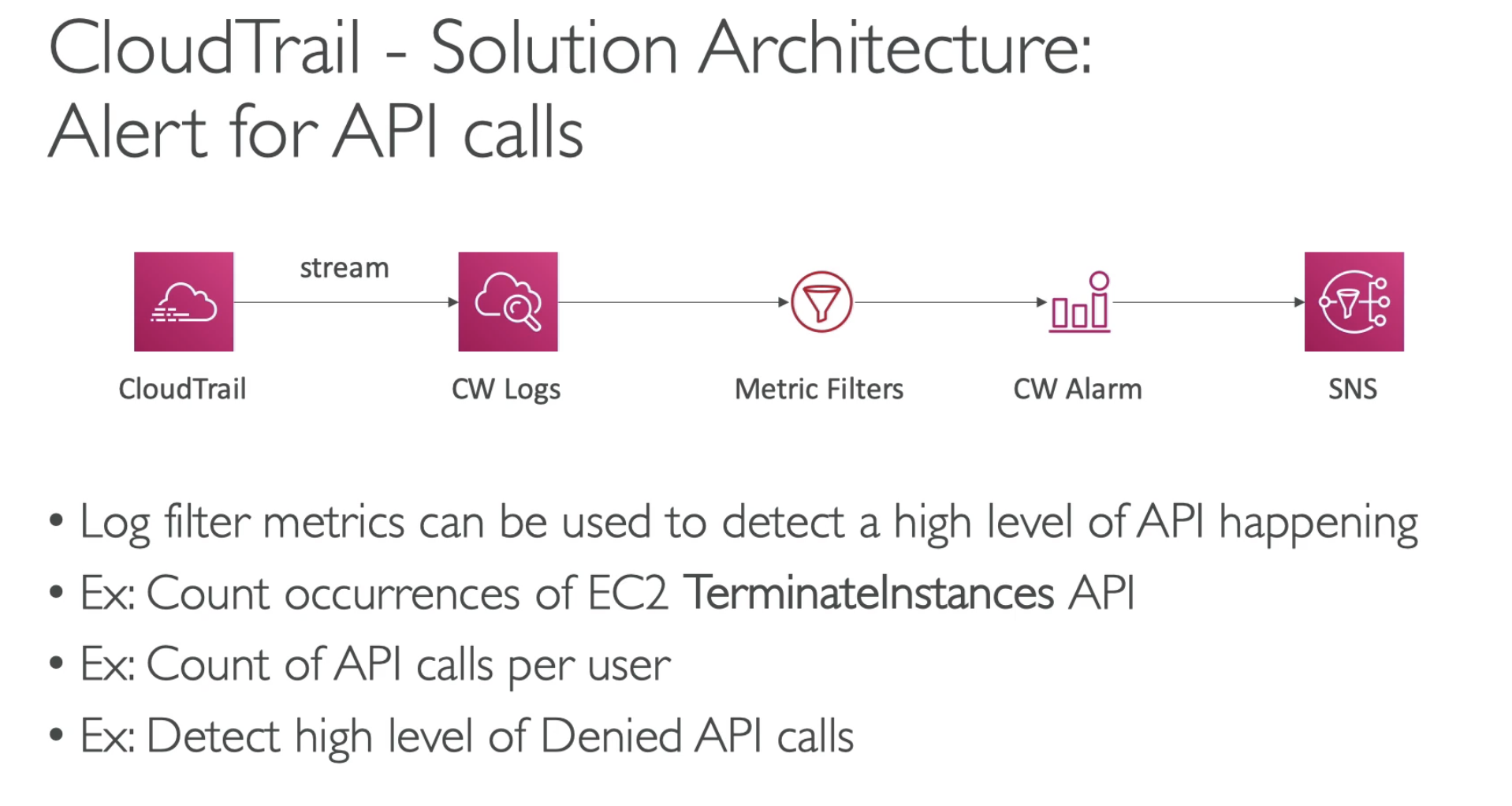
- You can stream the CloudTrail logs into CloudWatch
- Then you can set up a Metric Filters to looking for the metric you are interested
- If it pass the threadhold, you can trigger CloudWatch Alarm to send SNS topic
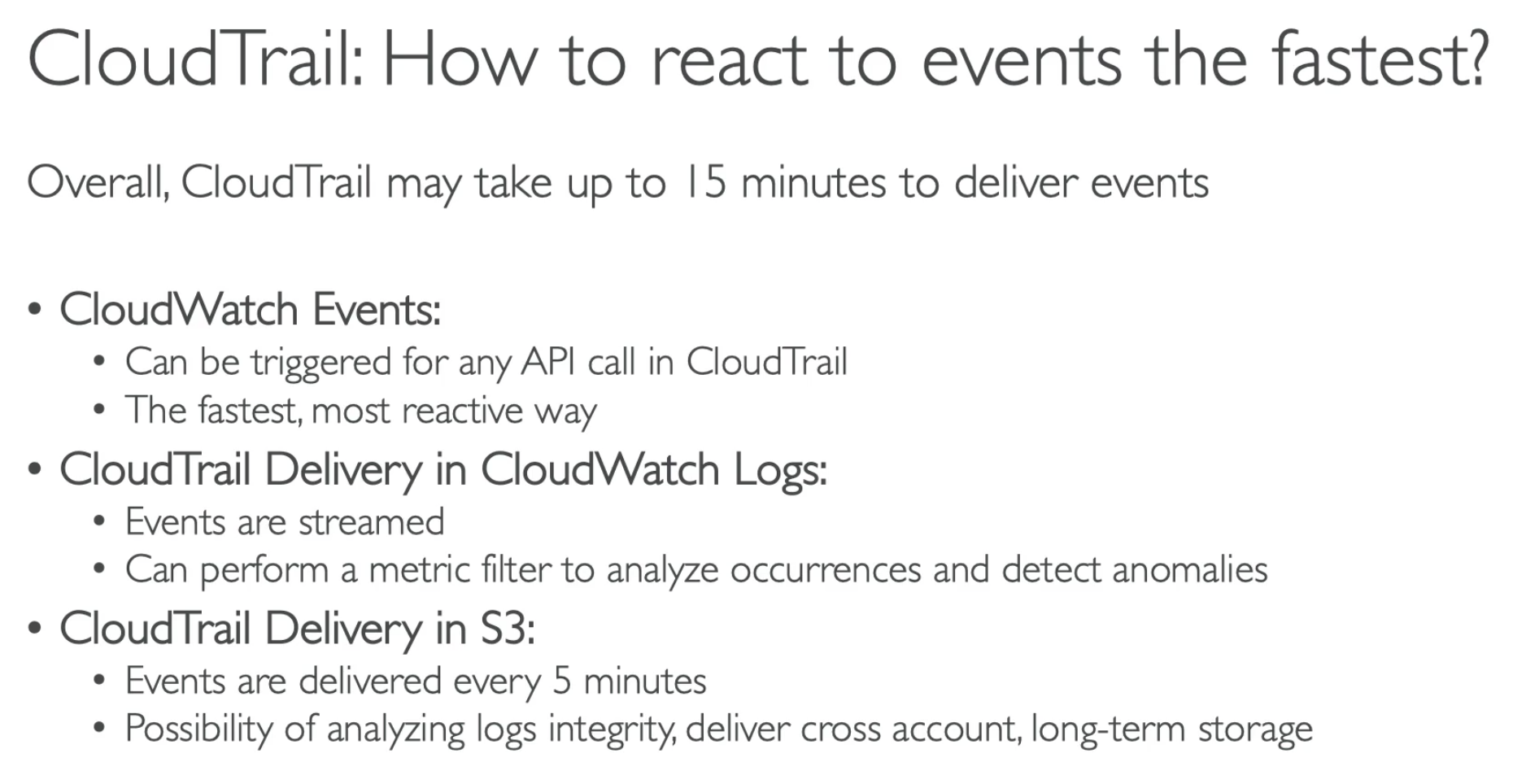
- CloudTrail may take up to 15 mins
- Fastest way is setup CloudWatch Events based on any API call in CloudTrail
KMS
- The value in KMS is that the CMK used to encrypt data can never be retrieved by the user, and the CMK can be rotated for extra security.
- Never ever store your secrets in plaintext, especially in your code
- Encrypted secrets can be stored in the code / environment variables
- KMS can only encrypting up to 4KB of data per call
- If data > 4 KB, use Envelope Encryption
- To give access to KMS to someone:
- Make sure the Key Policy allows the user
- Make sure the IAM policy allows the API calls
- Track API call by CloudTrail
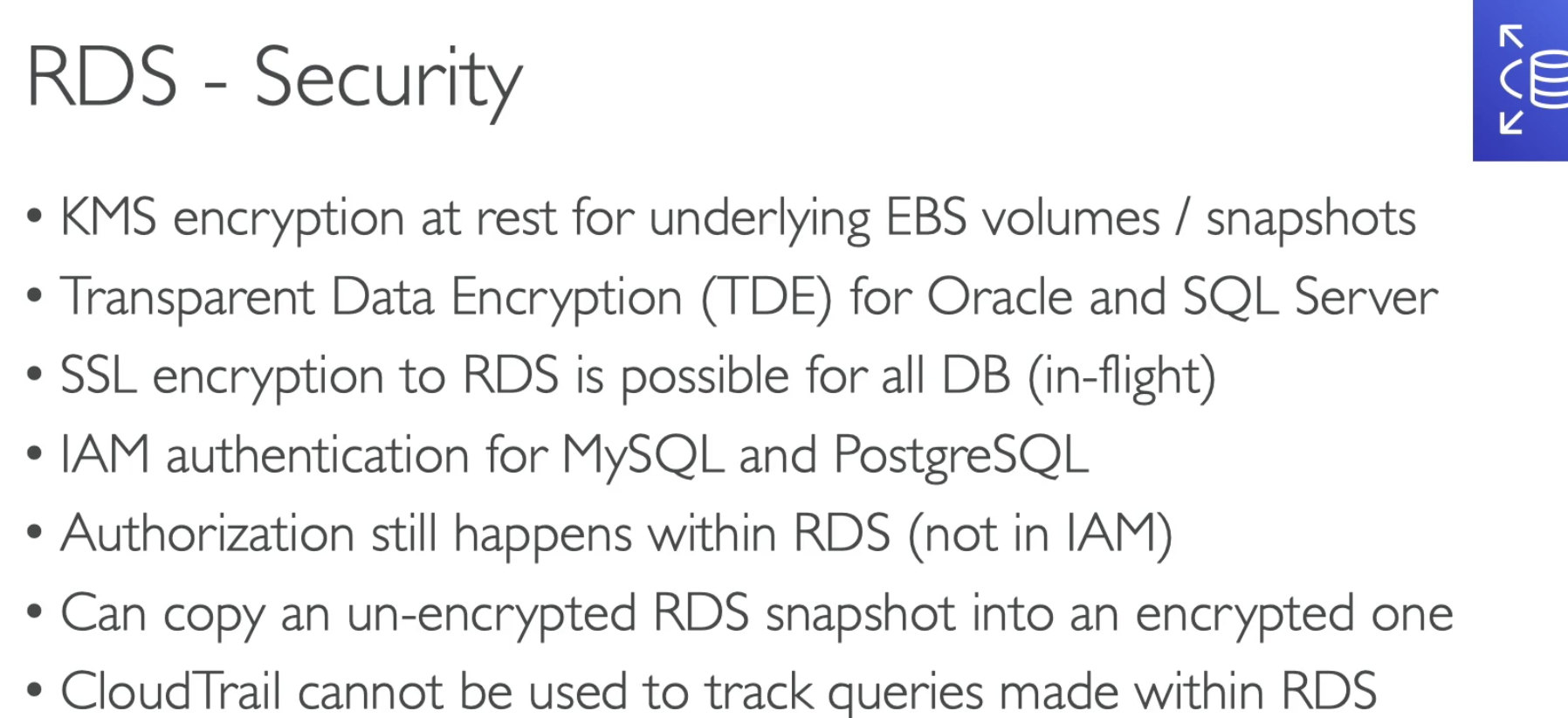
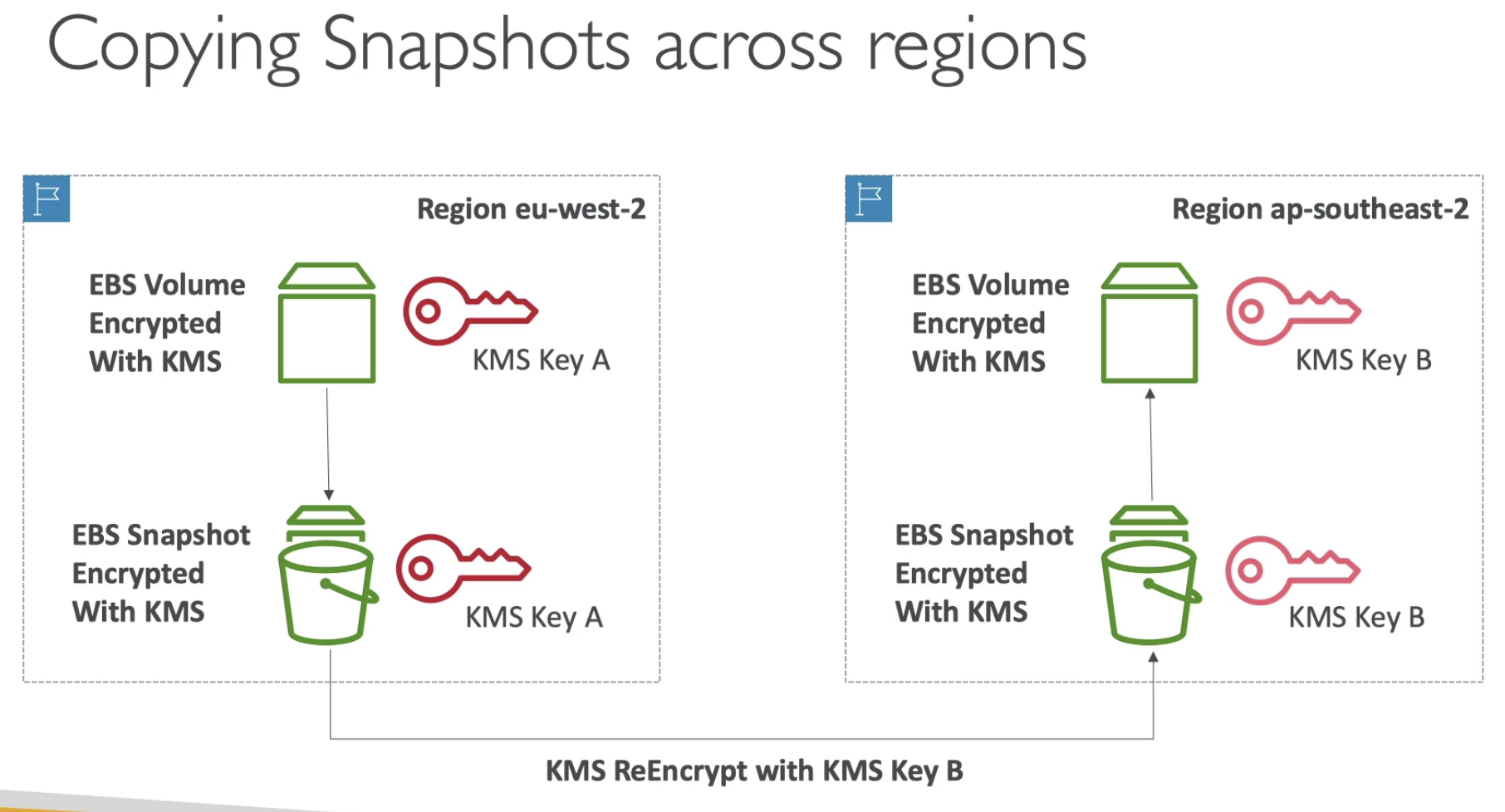
- Copy an un-encrypted RDS snapshot into an encrypted one
SSL
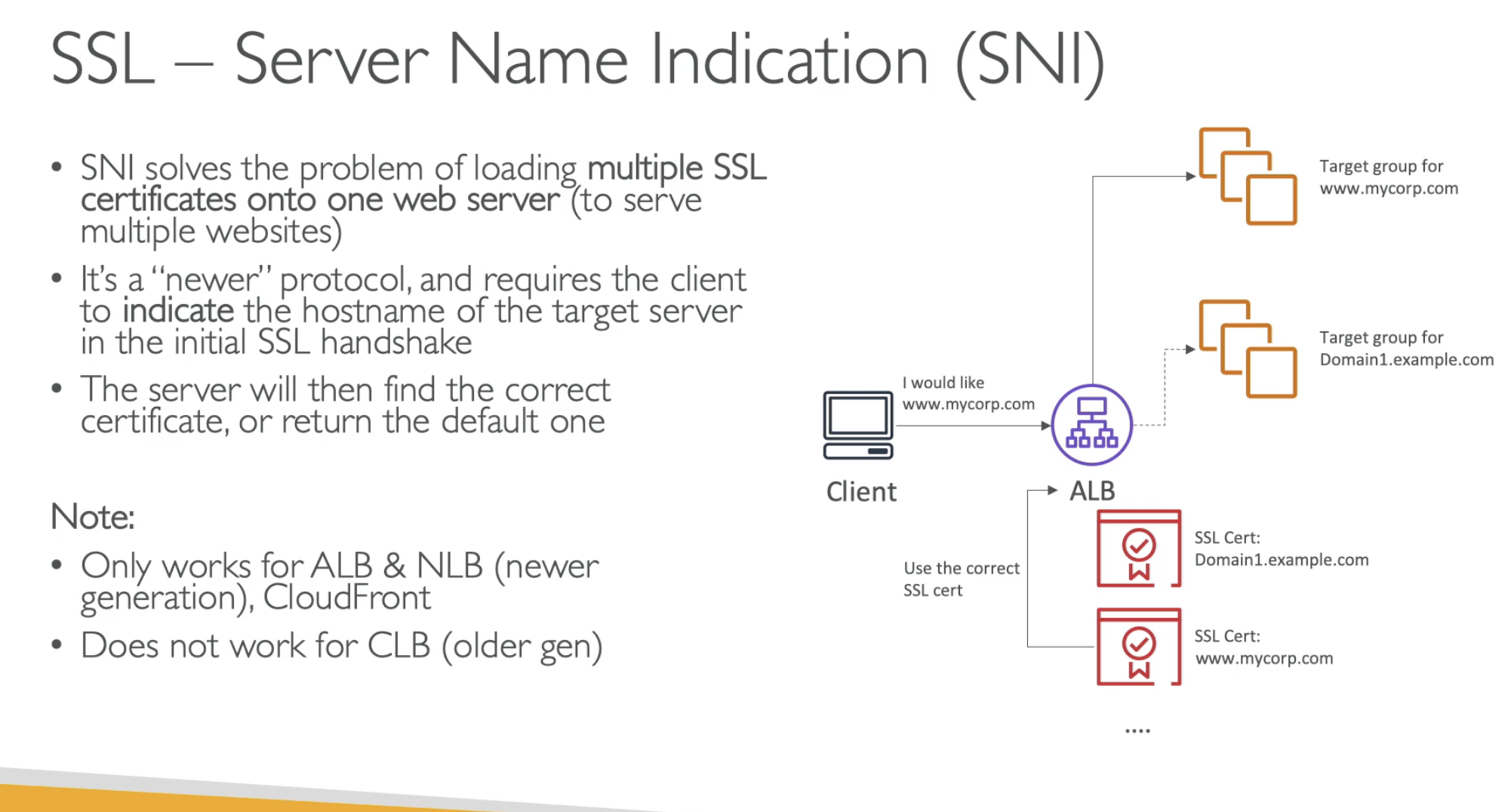
- SNI: For ALB & NLB, if you have multi domains behand ALB, you can use SNI to resolve correct certificate for each domain.
Route 53 Prevent MITM (Man in the middle attack)

ACM

- ACM helps to manage SSL certificate intergate with ALB, CloudFront, API Gateway
Good to Know
- ACM is a regional service
- To use with a global application (multiple ALB), you need to issue an SSL certificate in each region where you application is deployed.
- You cannot copy certs across regions
- Cerficate renewal:
- Automatically done if generated provisioned by ACM
- Any manually uploaded certificates must be renewed manually and re-uploaded
- Create public certificates
- Must verify public DNS
- Must be issued by a trusted public certificate authority (CA)
- Create private certificates
- For your internal appliations
- You create your own private CA
- Your applications must trust your private CA
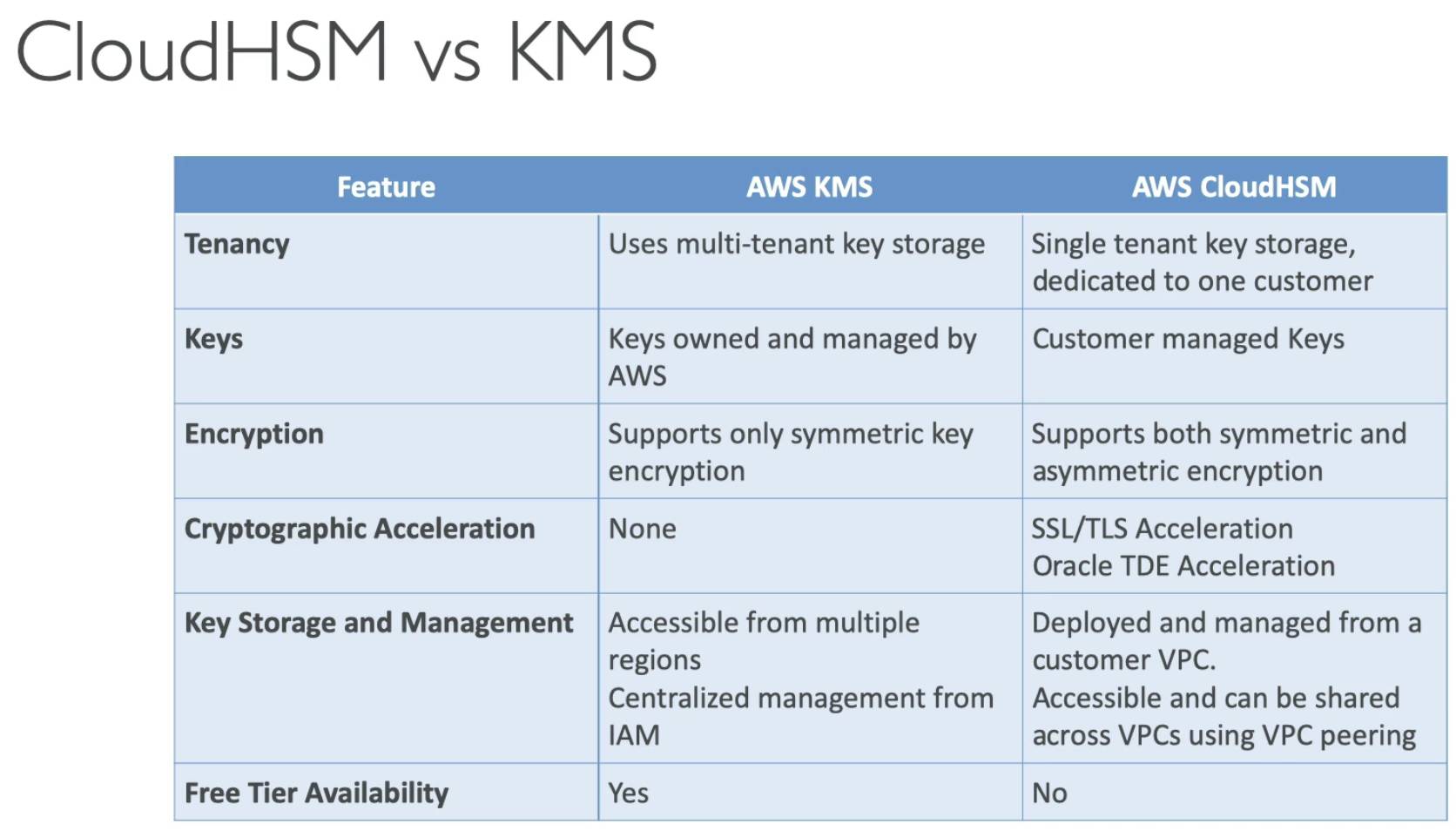
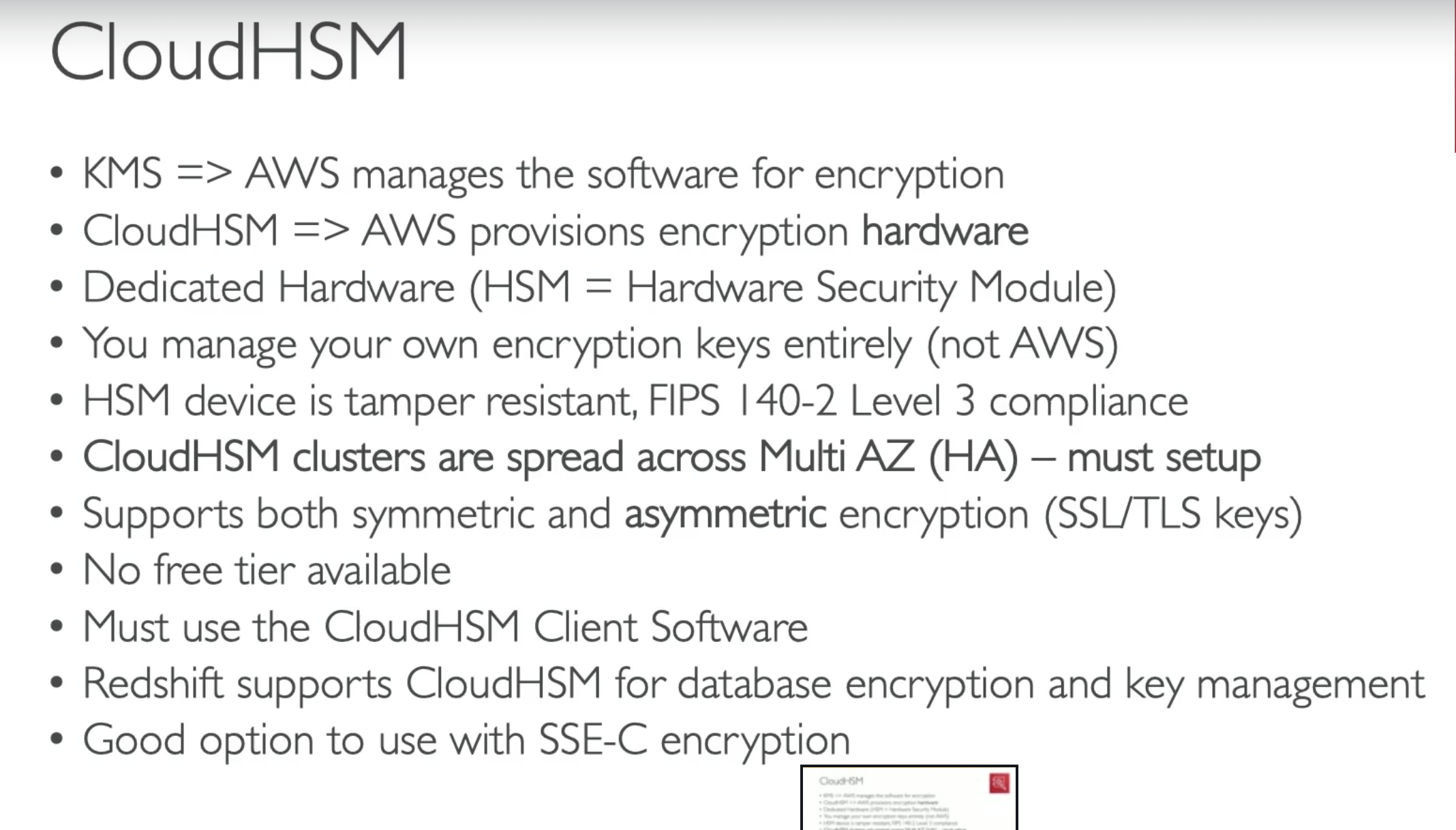
CloudHSM
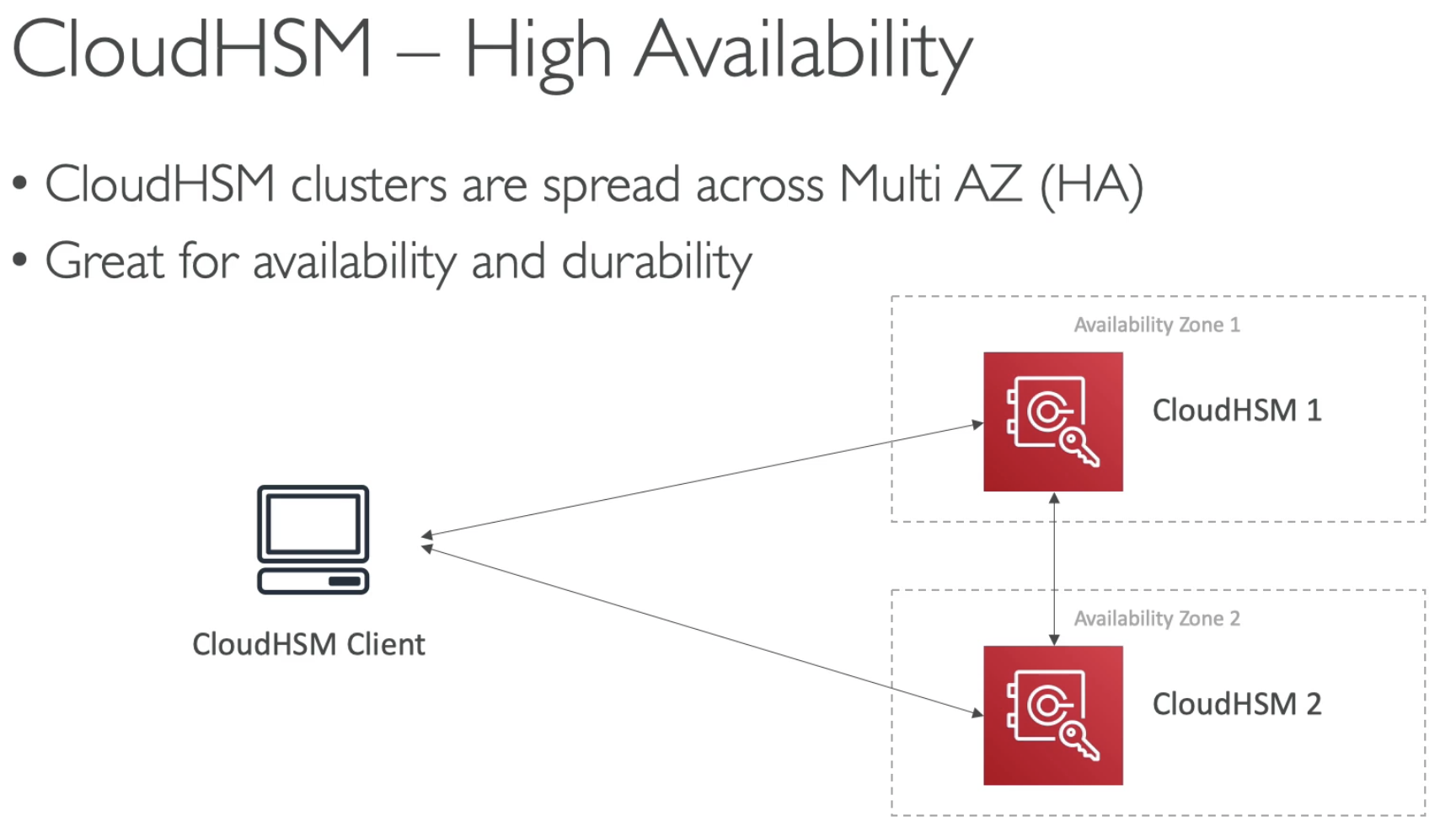
It is possible to setup Multi AZs for durability and availability
- To access cross region, you need to setup mutli VPCs and using VPC peering.
SSL & ELB
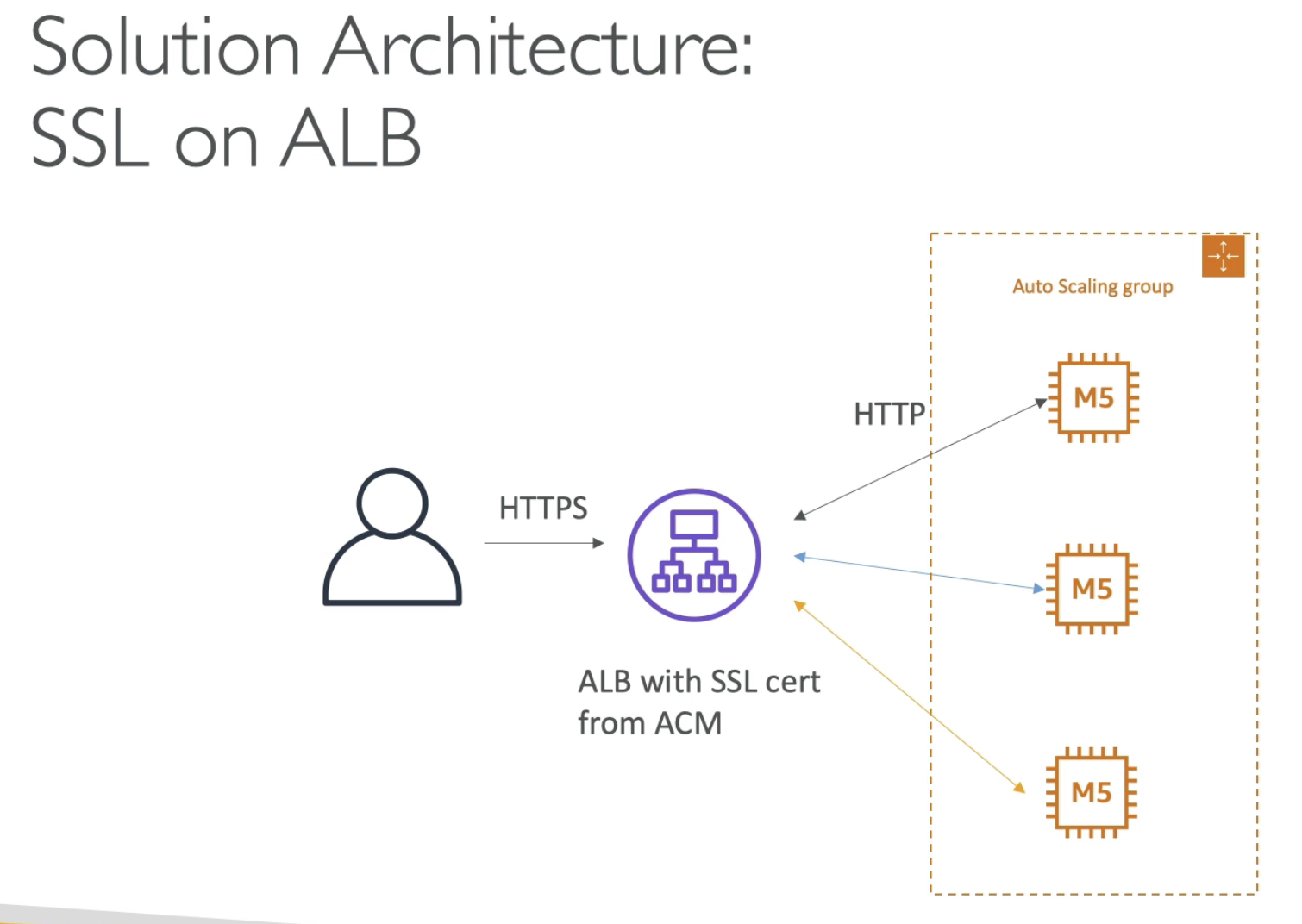
- Normally use HTTPS before ALB and load SSL by using ACM
- Then ALB talk to EC2 by using HTTP
Sometimes, you might want to set SSL directly on EC2 instances:

- Now, Client come from TCP and using NLB
- NLB talks to EC2 by using HTTPS
- But EC2 need to retrieve SSL in order to using HTTPS (during EC2 boot time)
- Using SSM and correct IAM permissions, this can work
- But performing SSL encryption / decryption can use CPU resources.
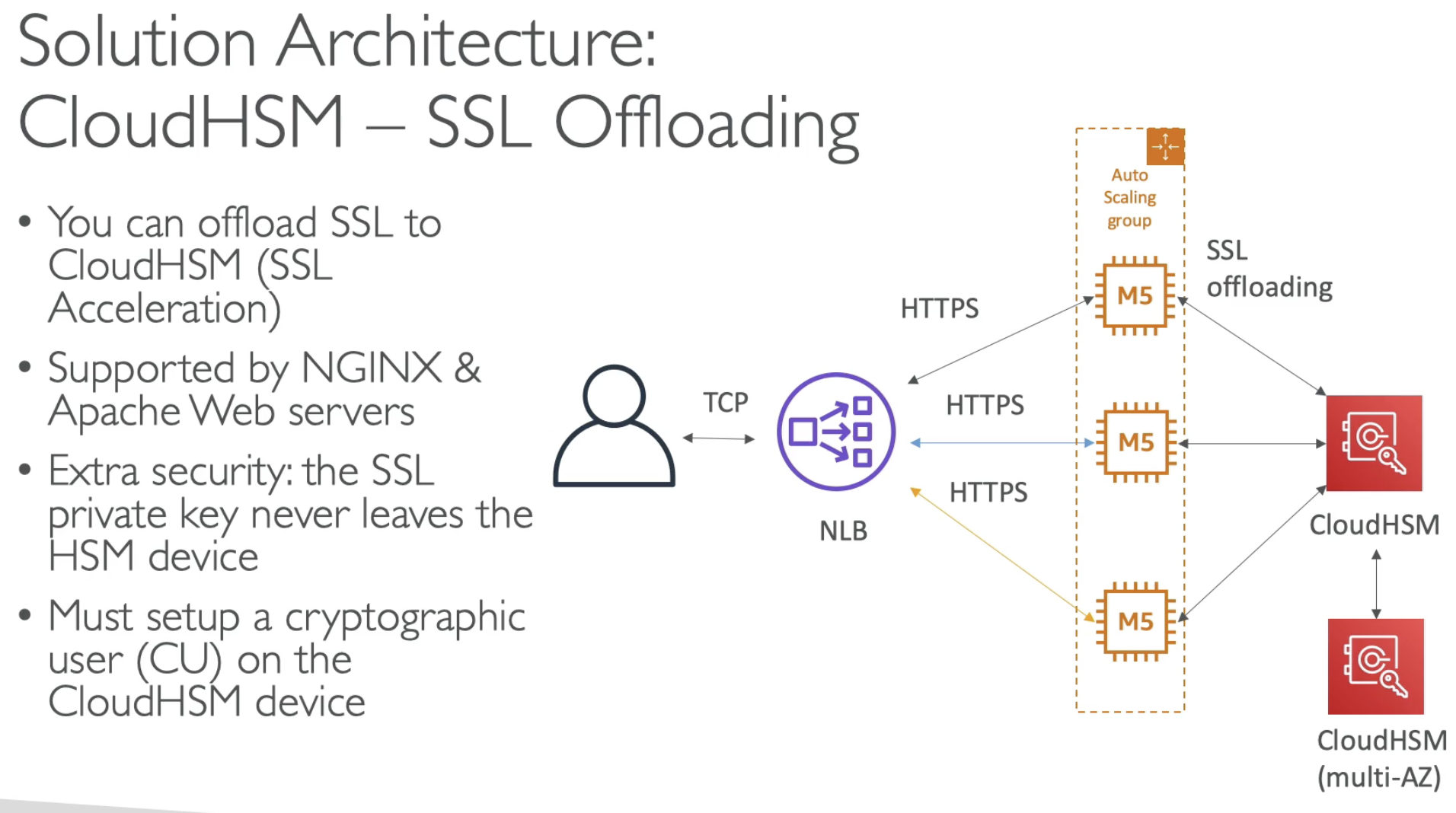
- Using CloudHSM SSL Acceleration
- Extra security
- Fast as well
S3

- You have to use HTTPS for SSE-C

- If enabled versioning, Amazon S3 event notifications are designed to be delivered at least once. If without versioning, might happens that one notification for two same object write done simultaenously.

- "Condition" for S3 bucket policies can only be applied to Public IP or Elastic IP (NOT private IP because S3 is public service)
- If EC2 inside a private VPC, can use VPC endpoint gateway to connect to S3.
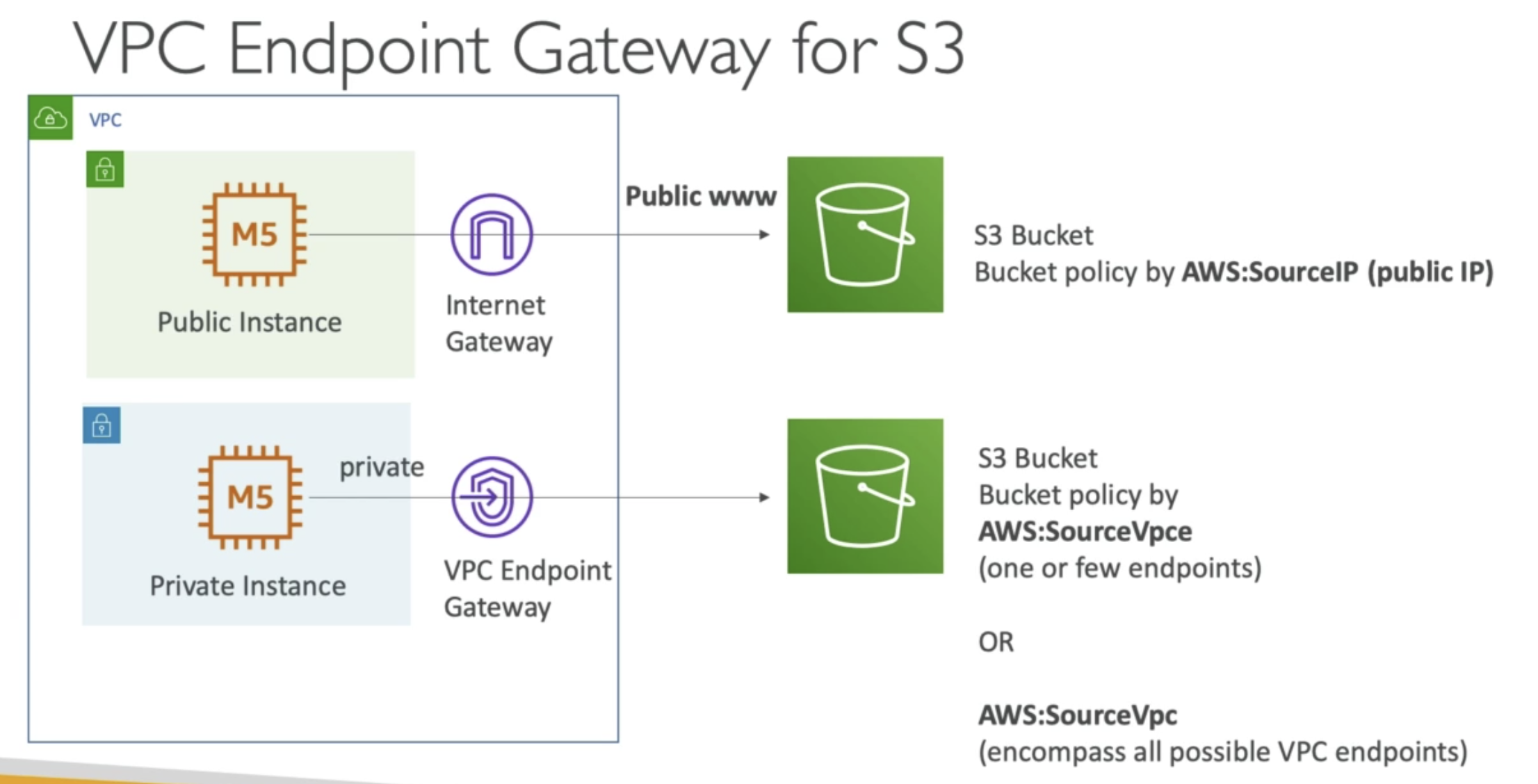
- SourceIP: Public IP
- SourceVpce or SourceVpc for VPC endpoints
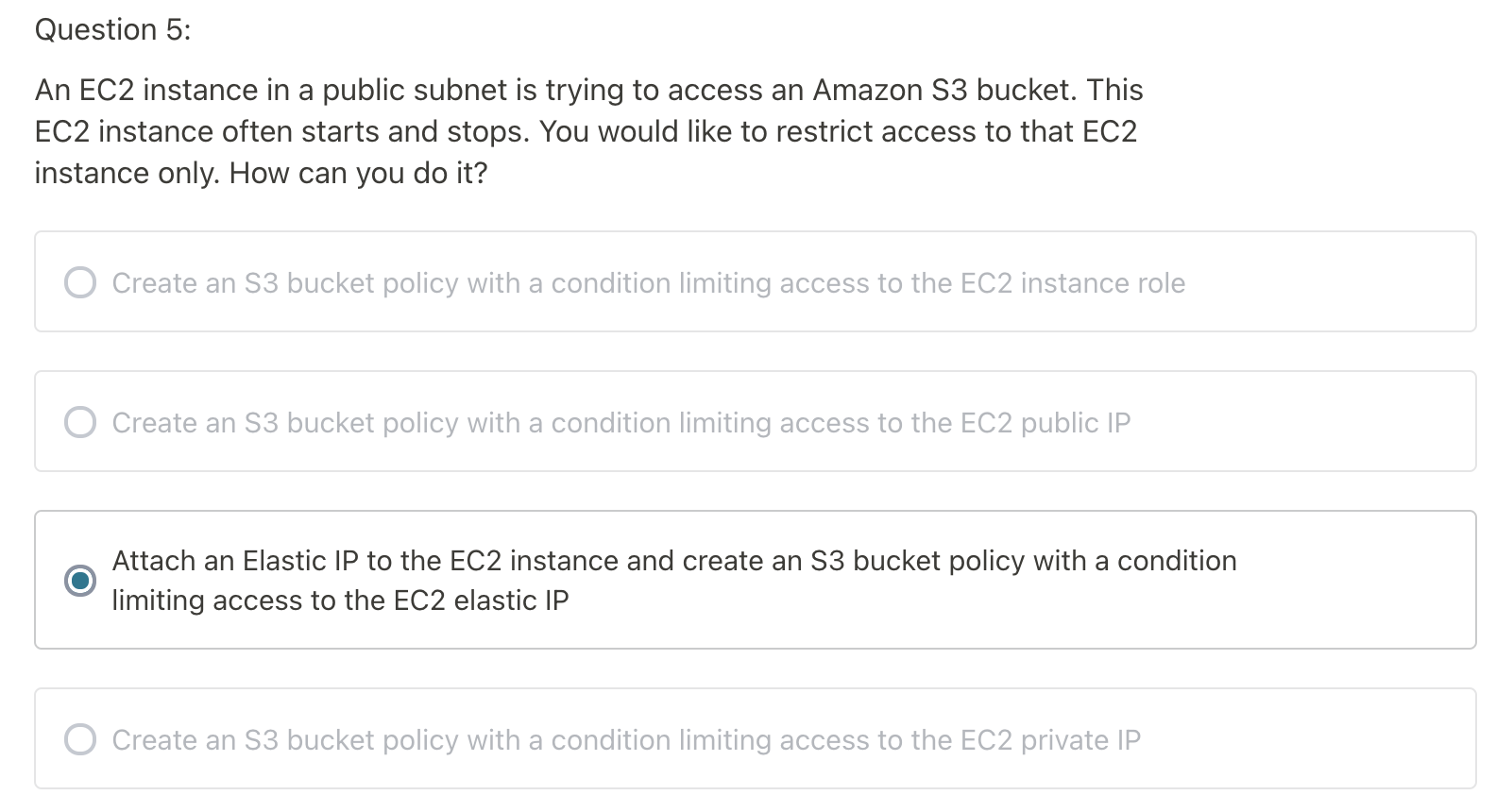
S3 is a global service, if using condition to limit source IP access to S3, have to use Elastic IP or public IP;
Everytimes, when EC2 stop/start, IP address will change
Actually, When you stop/start your instance, the IP address will change. If you reboot the instance, it will keep the same IP addresses. Unfortunately, it is not possible for us to reassign the address to your instance as that address would have been released back into the pool used by other EC2 instances.
By using an Elastic IP address, you can mask the failure of an instance or software by rapidly remapping the address to another instance in your account. Alternatively, you can specify the Elastic IP address in a DNS record for your domain, so that your domain points to your instance.


- Check with compliance
- But not deny any changes

- You can create your own rule check when sent notification
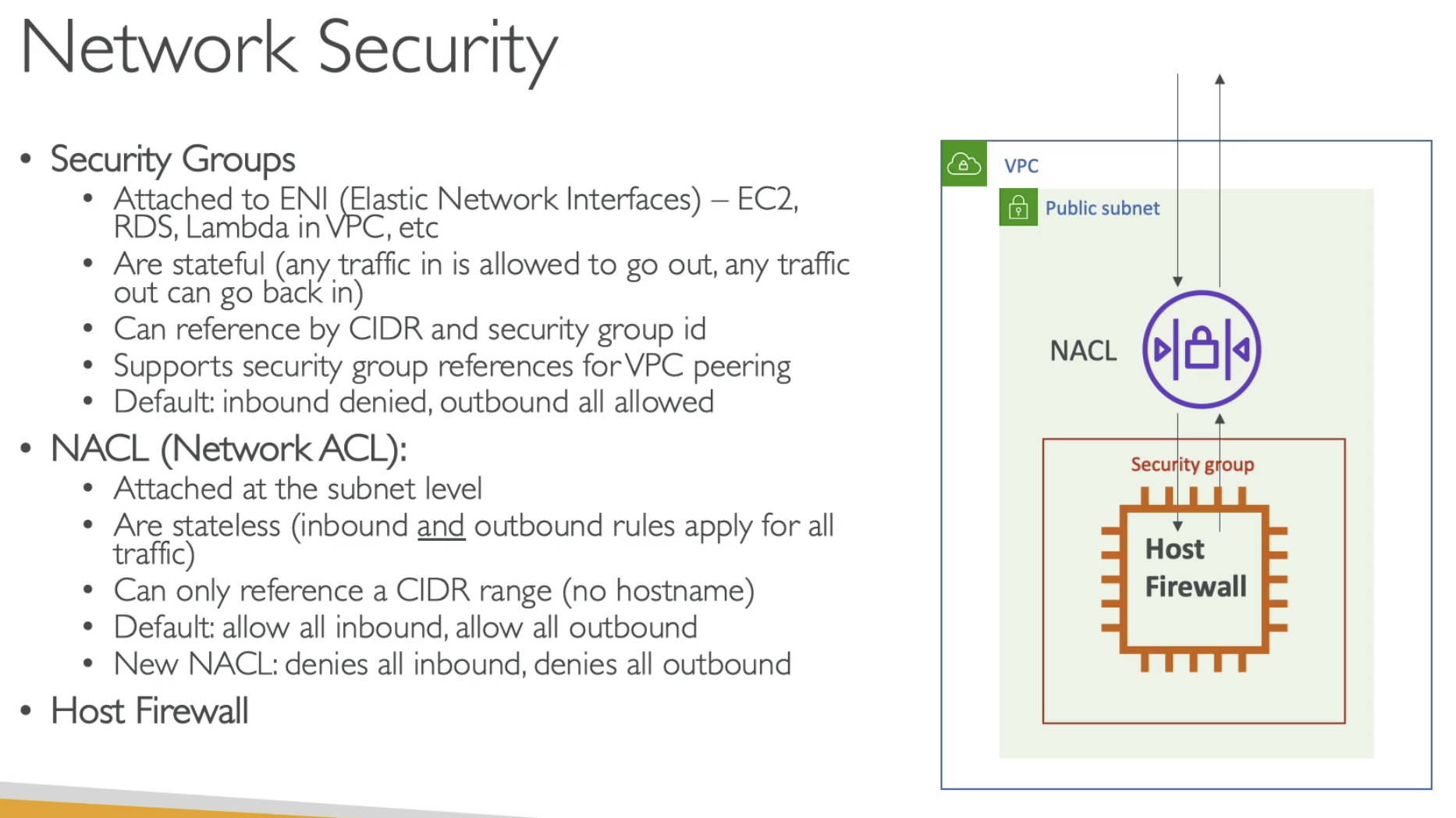
- Security Group has not deny rule, only alllow rule
- NACL can only reference IP range, not hostname
- If you want to deny some IP access, do it in NACL
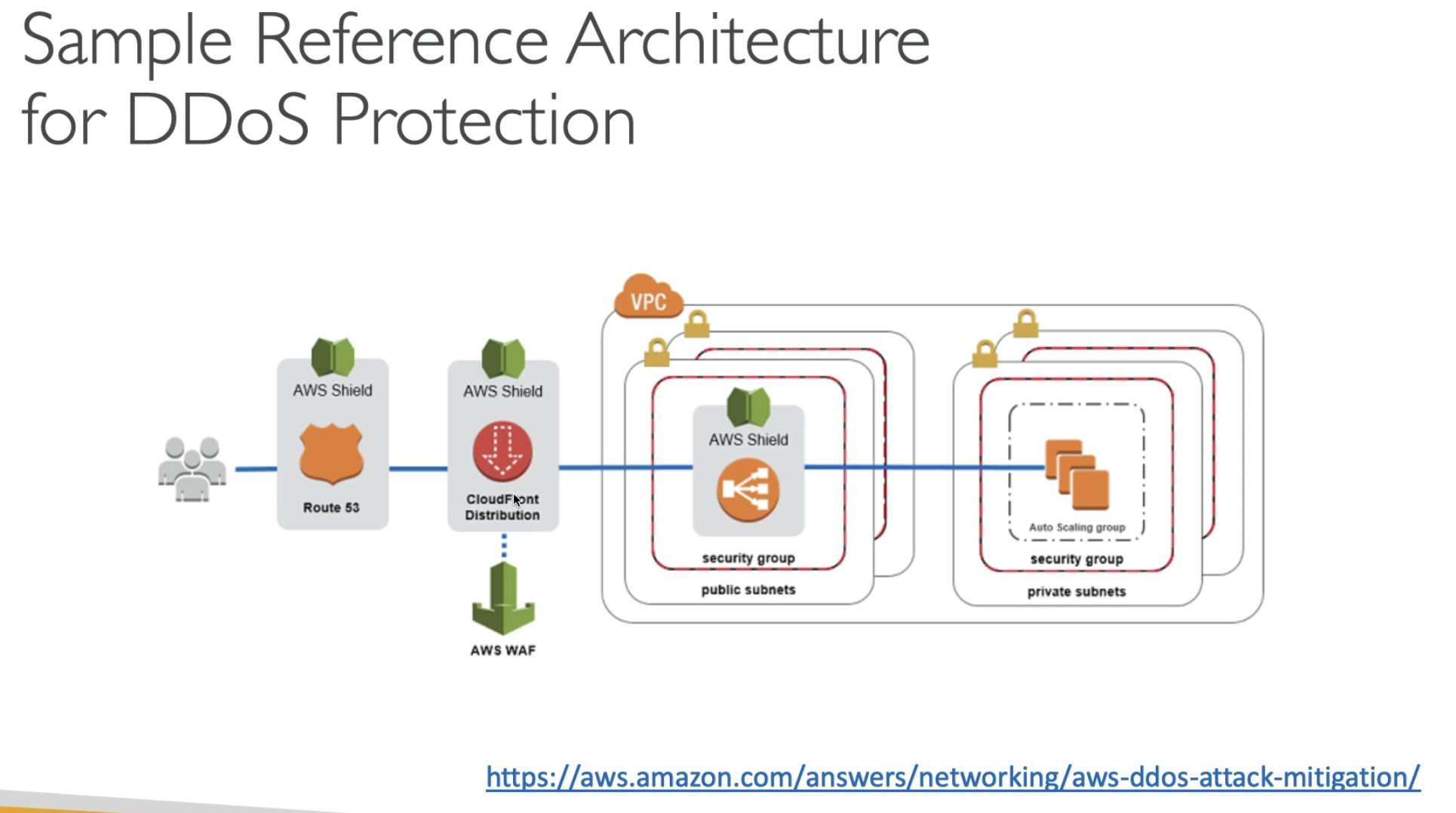
DDoS Attack

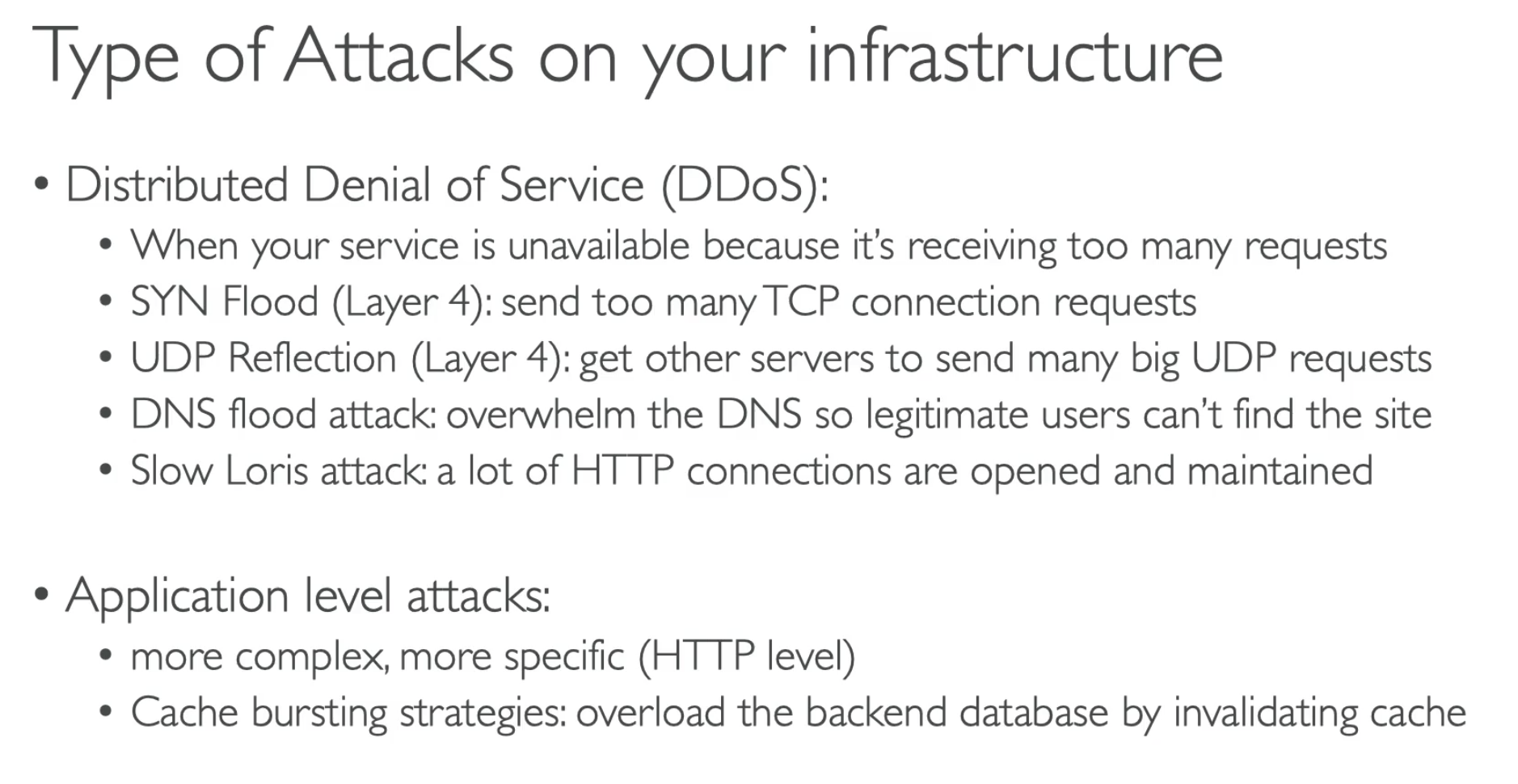
DDoS Protection on AWS
- AWS Shield Standard: protects against DDoS attack for your website and applications, for all customers at no additional cost
- AWS Shield Advanced: 24/7 premium DDoS protection
- AWS WAF: Filter spiecific requests based on the rules
- CLoudFront and Route 53:
- Availability protection using global edge network
- Combined with AWS Shield, provides DDoS attach mitigation at the edge
- Be ready to scale - leverage AWS Auto Scaling
- Separate static resource (S3/cloudfront) from dynamic one (EC23 A/ ALB)
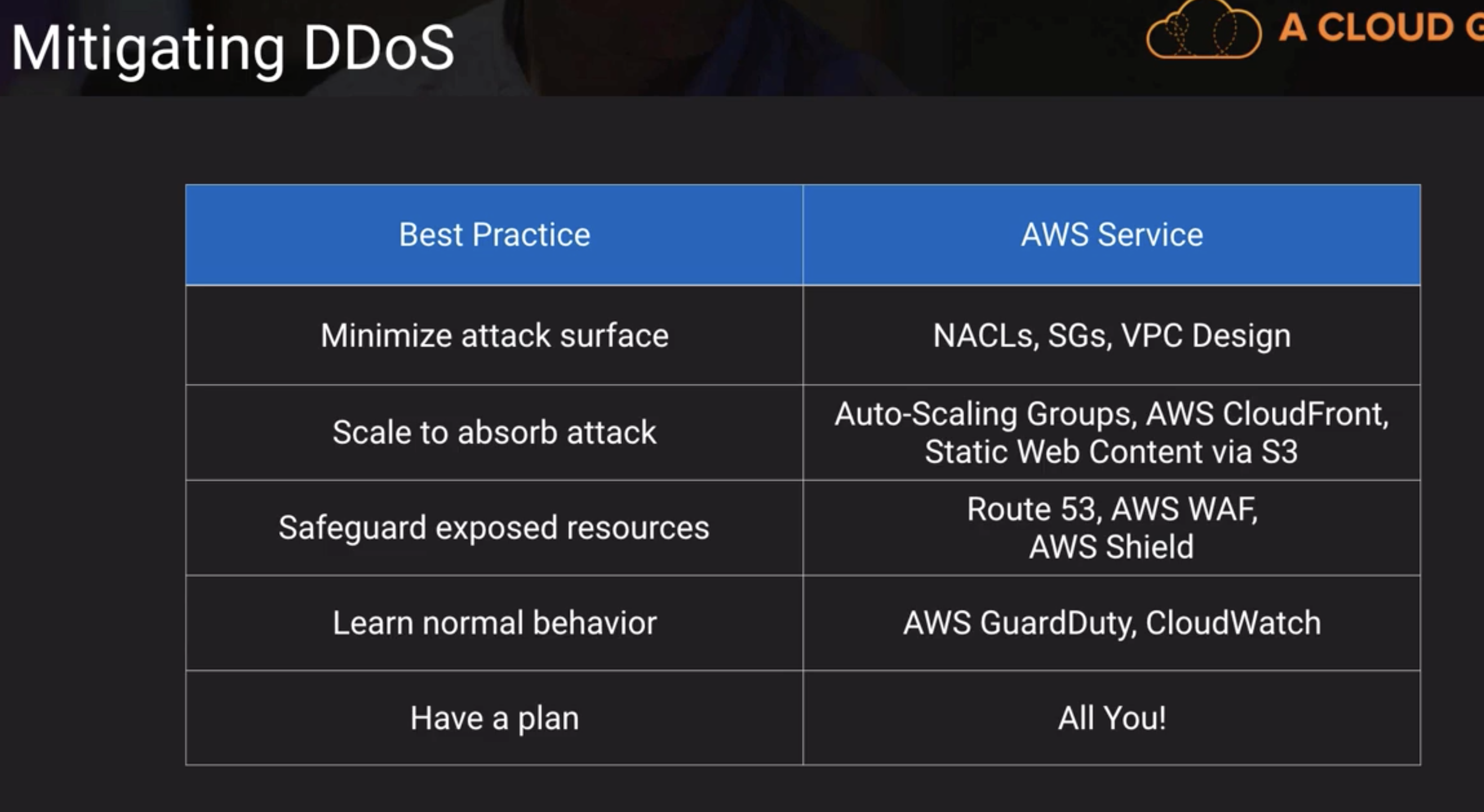
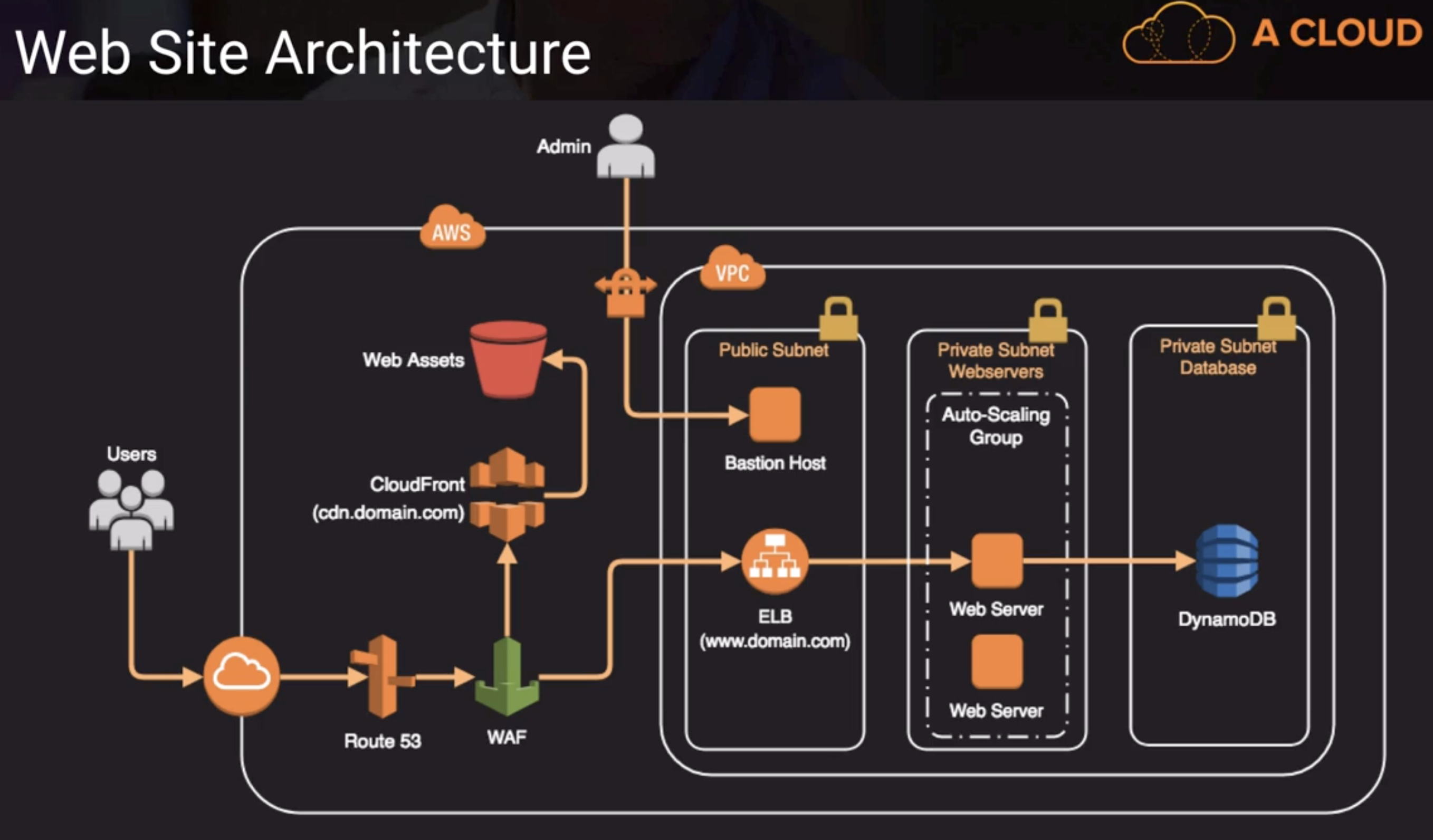
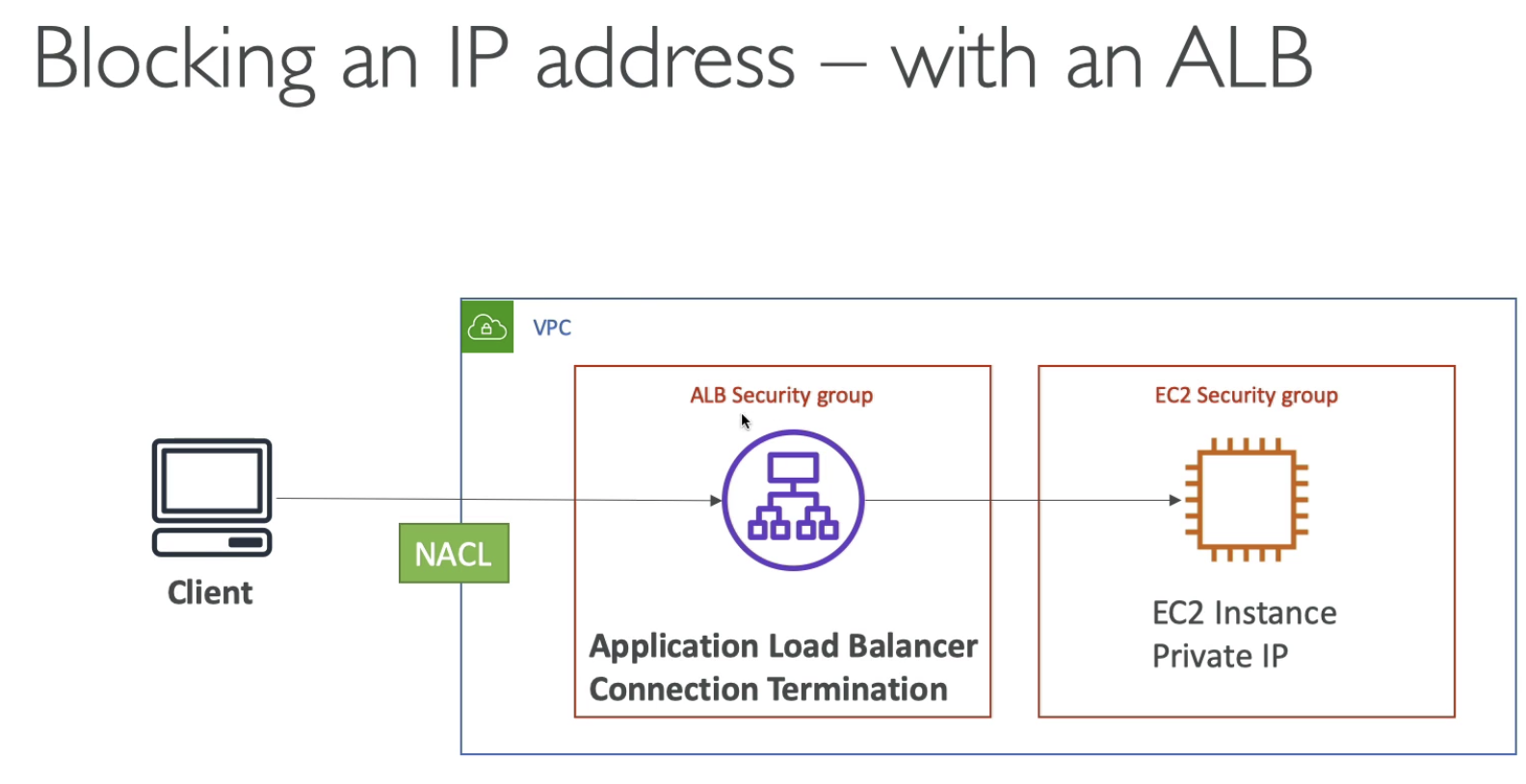
ALB has Security Group which can do Connection termination, EC2 only allow the traffic from ALB, which is secure. For ALB, has NACL as defense guard.
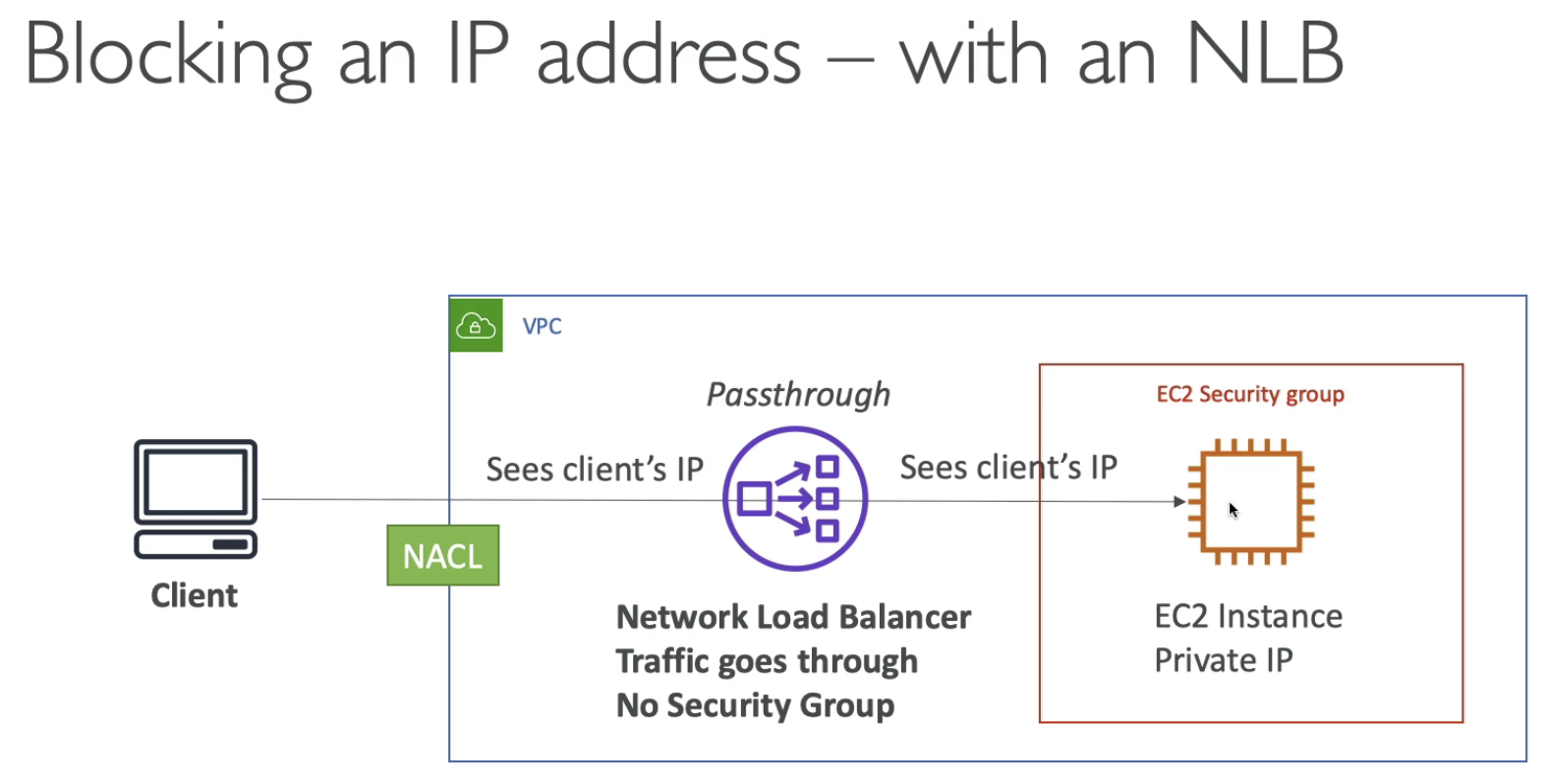
NLB doesn't have Connection Termination. The Clinet IP goes through to EC2, even EC2 is in a private IP. All the defense is in NACL.
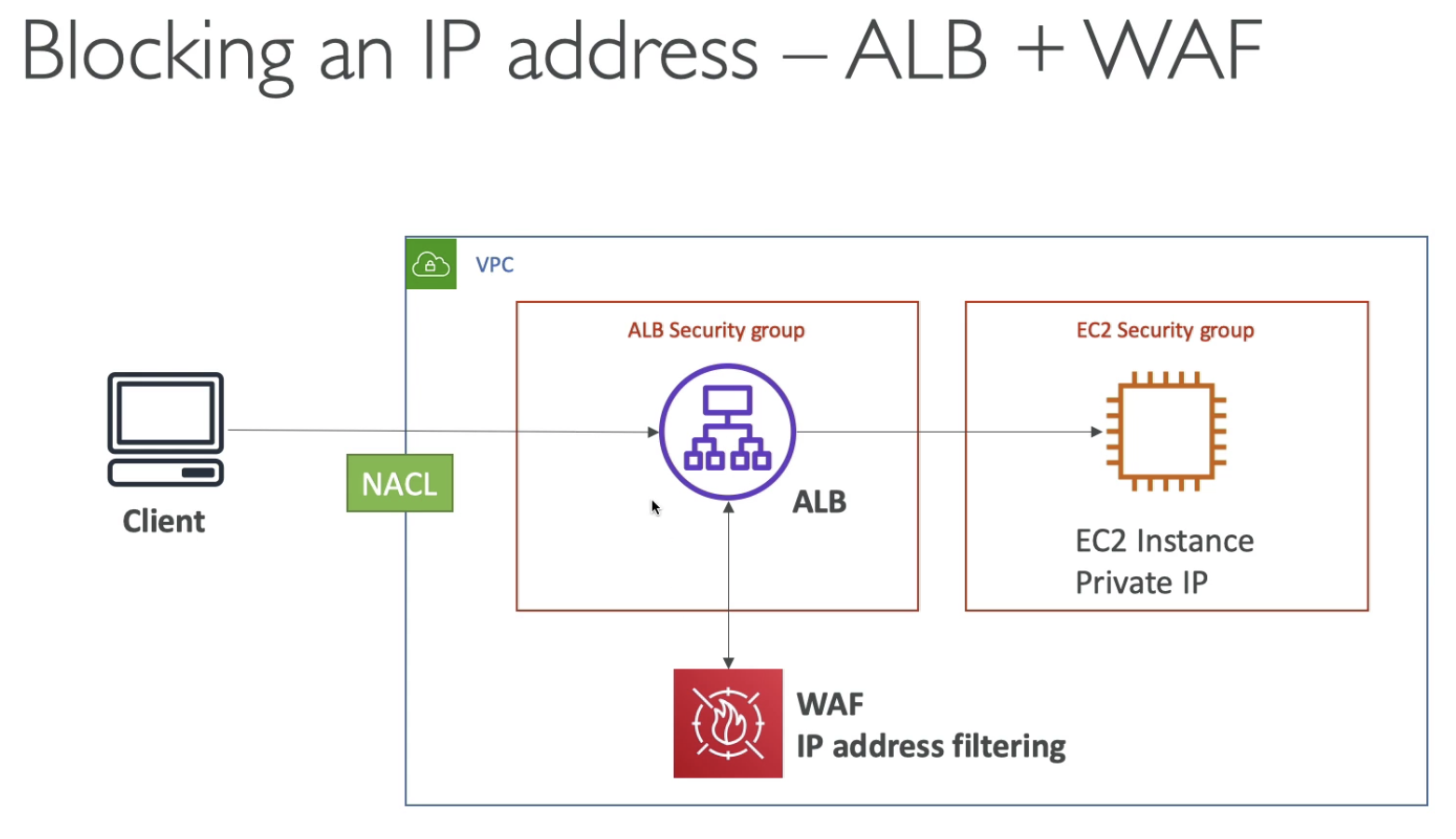
Install WAF for ALB, we can prevent some IP address attack by using the filtering. It is inside VPC.
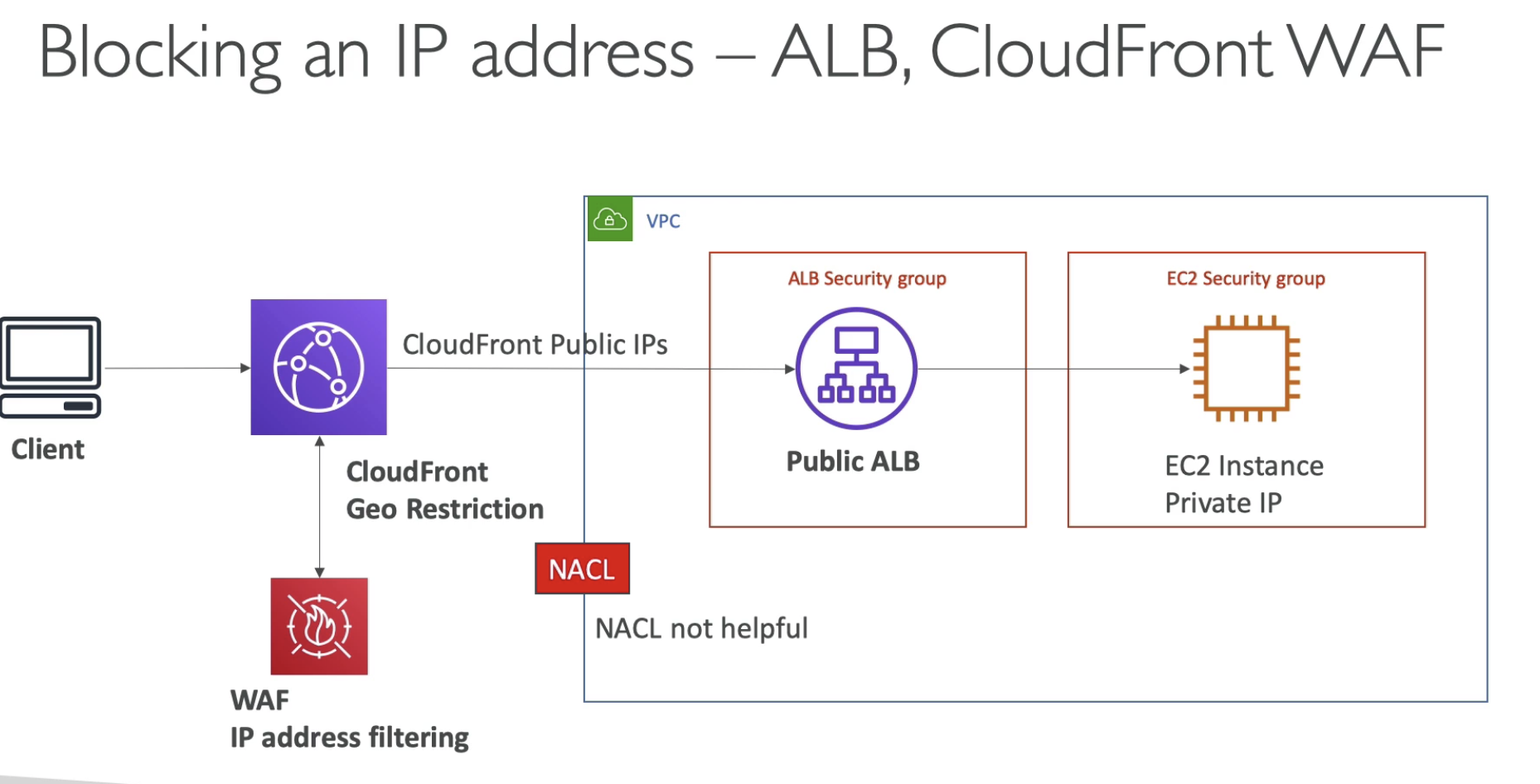
- If we have clondFront, the IP address is not coming from client anymore. It is coming from CloudFront
- In this case, NACL is not helpful anymore.
- We have to install WAF on CloudFront to do IP filtering.

KMS is not for store username and password, always for store encrption key only
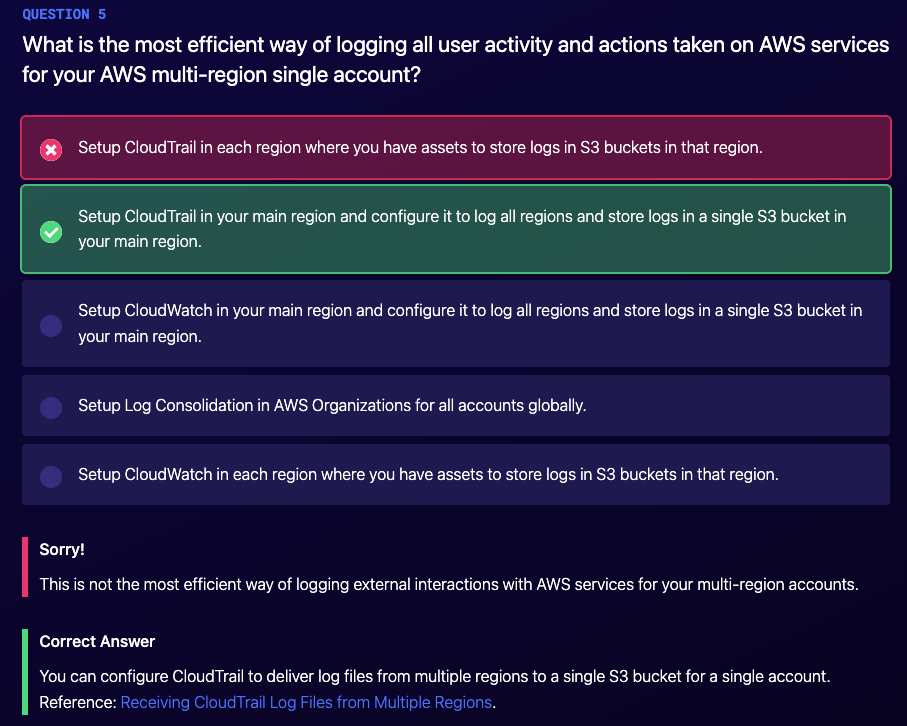
One S3 bucket for multi region cloudtrail logs



 浙公网安备 33010602011771号
浙公网安备 33010602011771号