[Security] Verifying an Auth0 token
Auth0 returns a JWT token
- JSON that contains information about a user
- No need to send a request to Auth0 to verify JWT
- What pervents anyone to generate it?
The JWT token return by Auth0 are signed by Auth0 as well.
- We can just verify the signature
OAuth allows to use one of the two algorithms that it can use to sign a JWT token:
Symmetric (HS256)
- The same key for signing a token (by Auth0) and verifying a token (by our application)
- We need to store a key securely
- If this key leaks, an attacker can sign fradulent JWT token
Asymmetric (RS256)
- Different keys are used for signing and verifying a token
- We don't need to store the key
- Auth0 is responsible for storing a token
- We only get a sertificate to verify a token (Not signing)
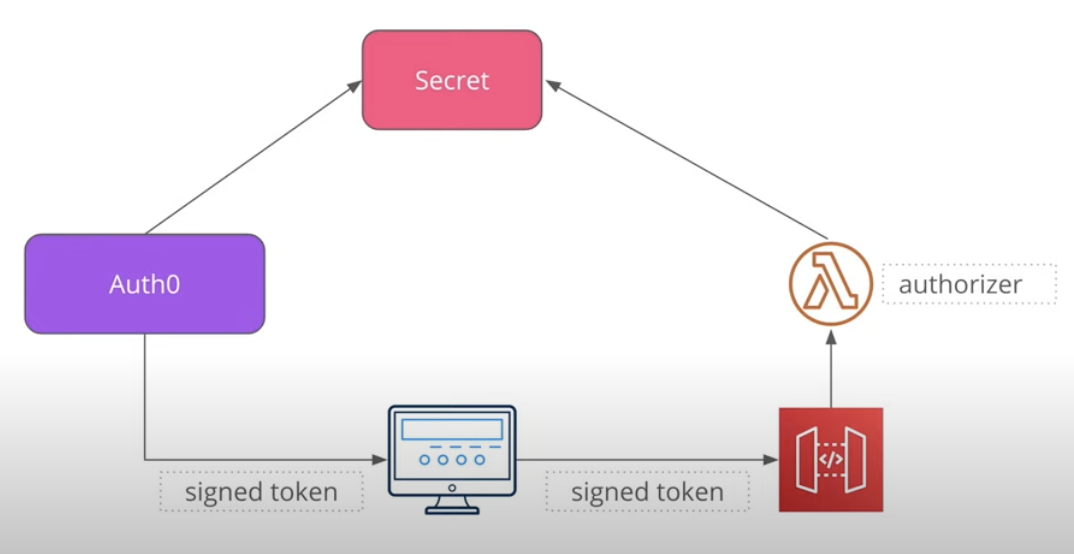
Symmetric Signing:
- Auth0 use the secret to generate a toekn
- Return a Signed token to client
- Client send signed token to API Gateway
- Api Gateway has to use the same secret to to validate the signed token to get Cerificate
Asymmetric Signing:
- Auth0 uses a Private key which only use for signing
- Return the singed token to client
- Client send signed token to API Gateway
- We have a use a Cerificate to verify the singed token

Here is a code snippet that can be used to verify a JWT token with Node.js:
import { verify } from 'jsonwebtoken'
const jwtToken = '...'
const secret = '...'
verify(jwt, secret)
// If an exception is not thrown a JWT is valid
Create an Application in Auth0
- Create an application





 浙公网安备 33010602011771号
浙公网安备 33010602011771号