直播app hook解密
文章备份,写于2022-8-5
通过Bytecode-Viewer反编译APP,搜索X-arg字段得到加密方法
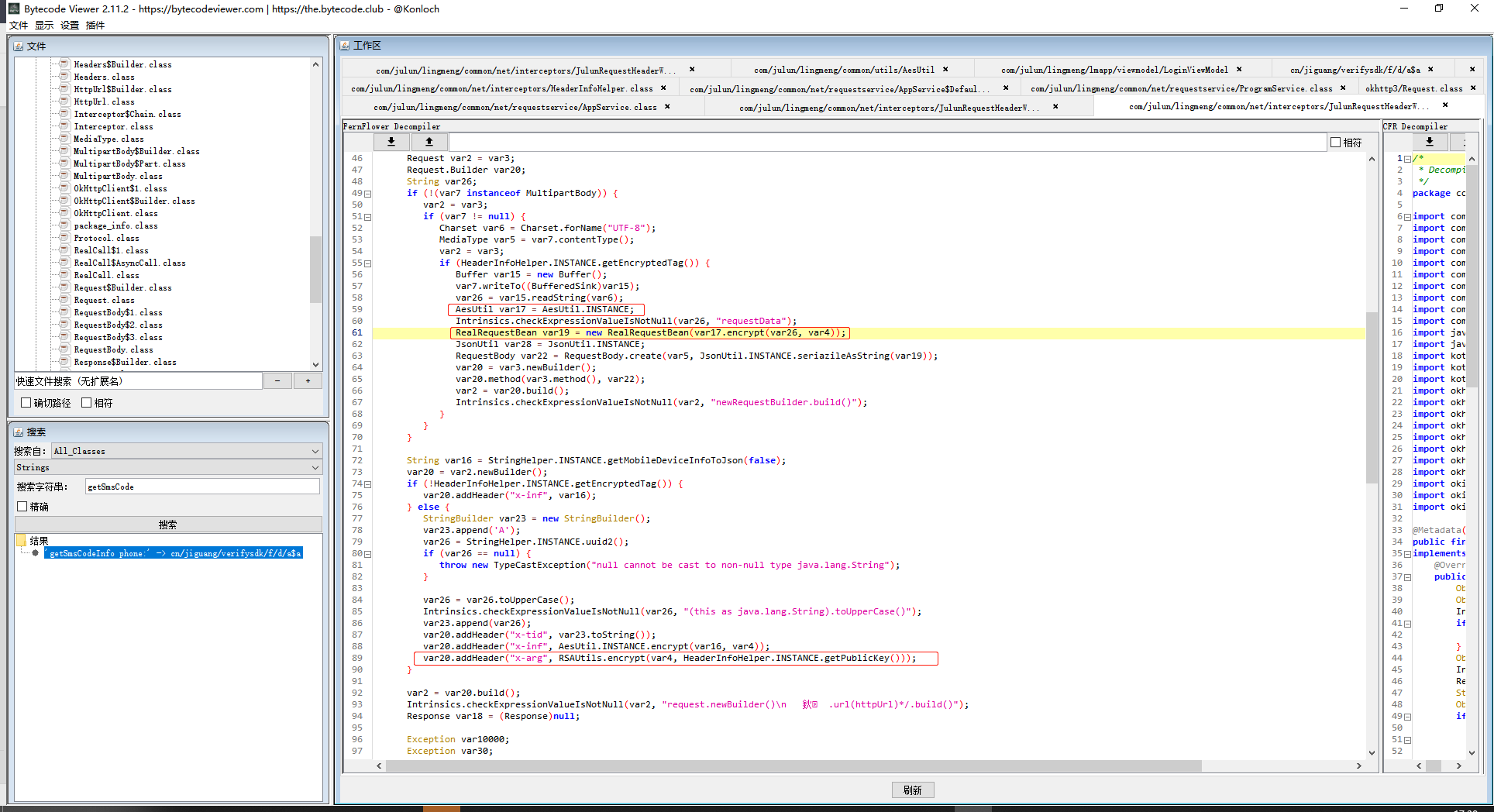
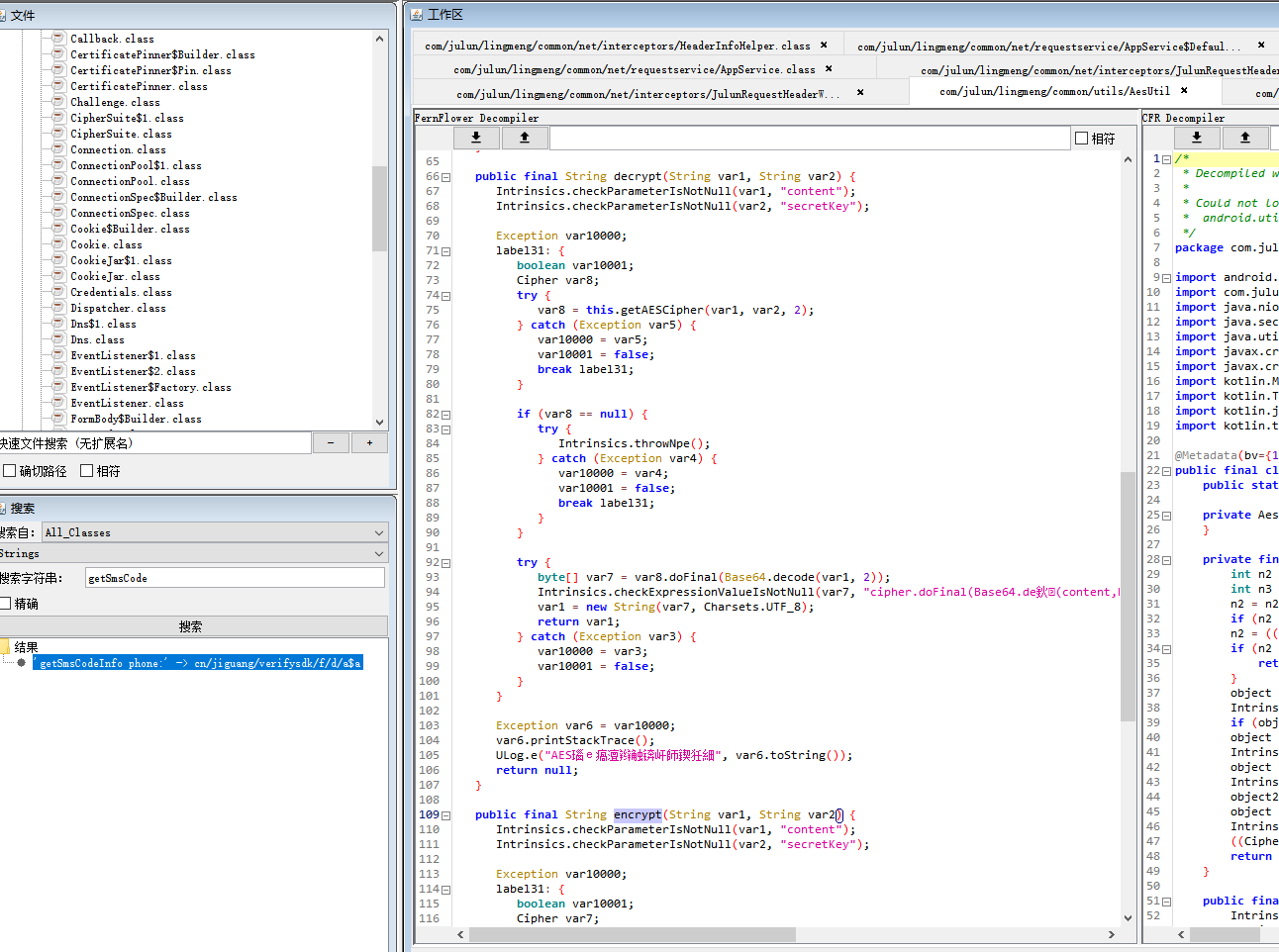
查看代码得知加密类为AesUtil,在其中找到了加密解密方法
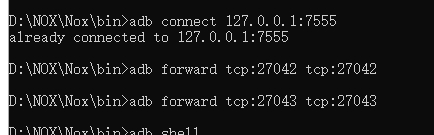
Mumu模拟器安装app。使用adb连接运行fdserver
D:\NOX\Nox\bin>adb connect 127.0.0.1:7555
already connected to 127.0.0.1:7555
D:\NOX\Nox\bin>adb forward tcp:27042 tcp:27042
D:\NOX\Nox\bin>adb forward tcp:27043 tcp:27043
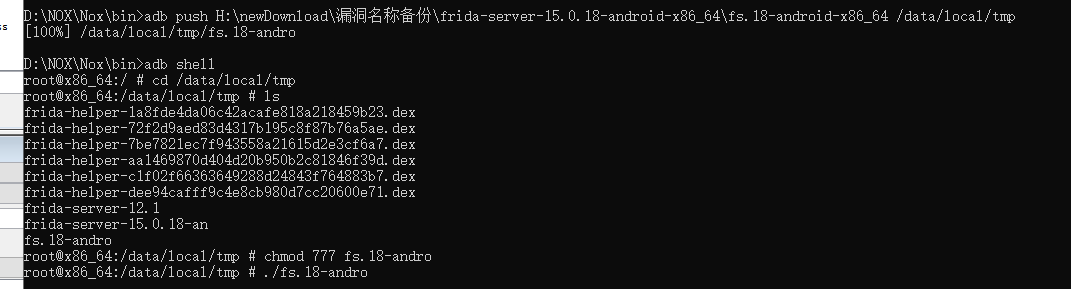
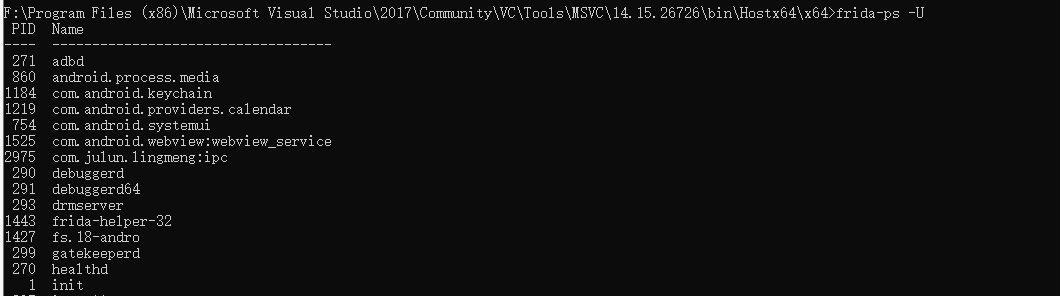
使用frida-ps -U查看是否连接正常
使用objection注入进程
objection -g com.julun.lingmeng explore
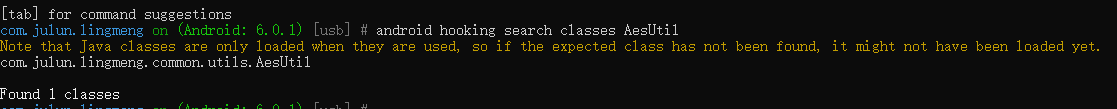
搜索加密类
android hooking search classes AesUtil
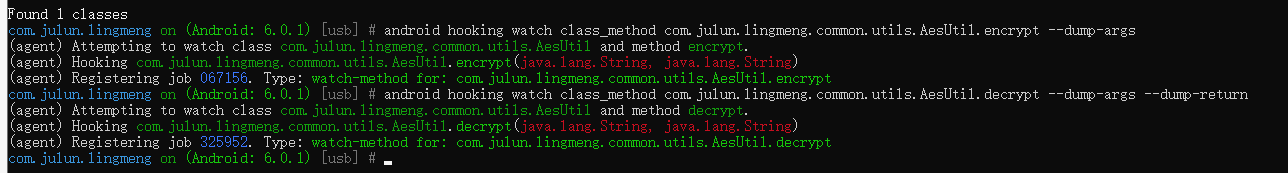
hook加密类和解密类的方法
android hooking watch class_method com.julun.lingmeng.common.utils.AesUtil.encrypt --dump-args
android hooking watch class_method com.julun.lingmeng.common.utils.AesUtil.decrypt --dump-args --dump-return
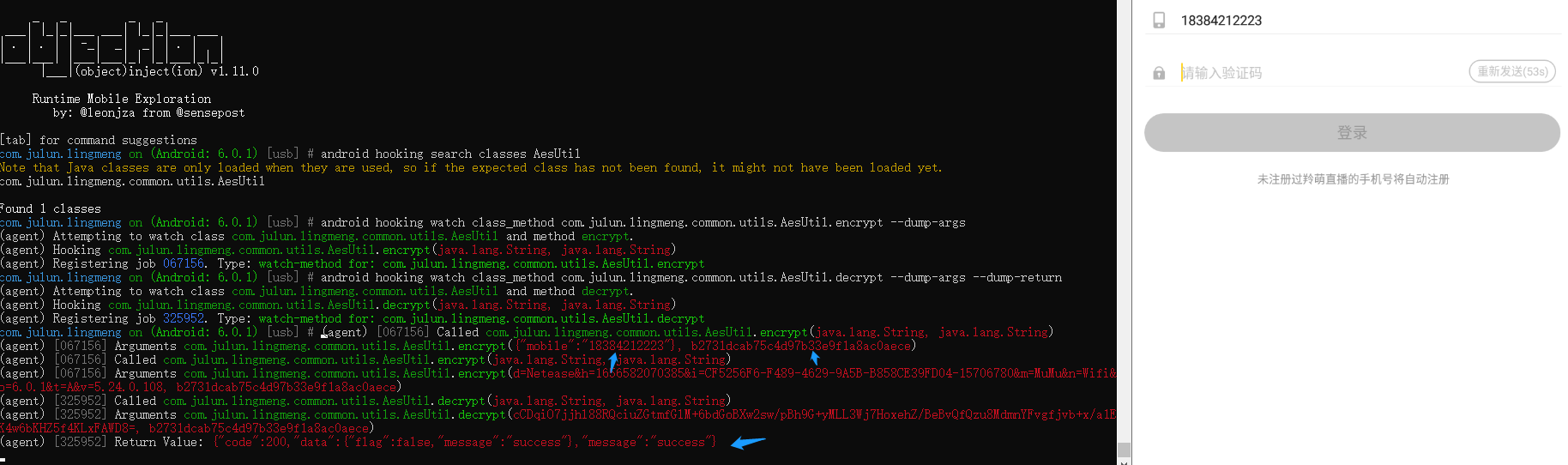
发送短信,此时可以看到已经打印出hook方法的参数
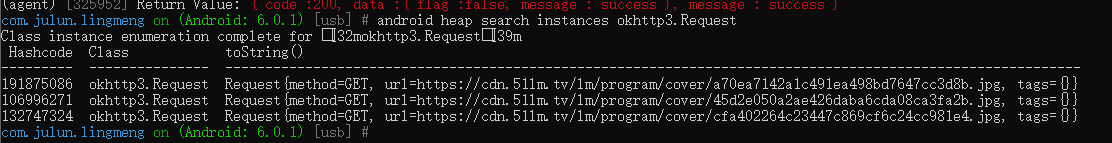
通过搜索实例可以查看url的值
android heap search instances okhttp3.Request
开启Android系统代理
adb shell settings put global http_proxy 127.0.0.1:8080
adb reverse tcp:8080 tcp:8080
adb forward tcp:27042 tcp:27042
adb shell settings delete global http_proxy
adb shell settings delete global global_http_proxy_host
adb shell settings delete global global_http_proxy_port
参考
https://www.cnblogs.com/tjp40922/p/15171898.html、
https://www.jianshu.com/p/c443ad5ace9b
https://blog.csdn.net/pfourfire/article/details/123119967
https://blog.csdn.net/zyc3545/article/details/119066335


 浙公网安备 33010602011771号
浙公网安备 33010602011771号