2021 ISCC MISC 做题笔记(一)
──(kali㉿kali)-[~]
└─$ binwalk -e /home/kali/桌面/hongbao2.jpg
在得到的文件夹内获得了一个文档(下位内容)
24,43,13,13,12,21,43
具体操作情况如图:
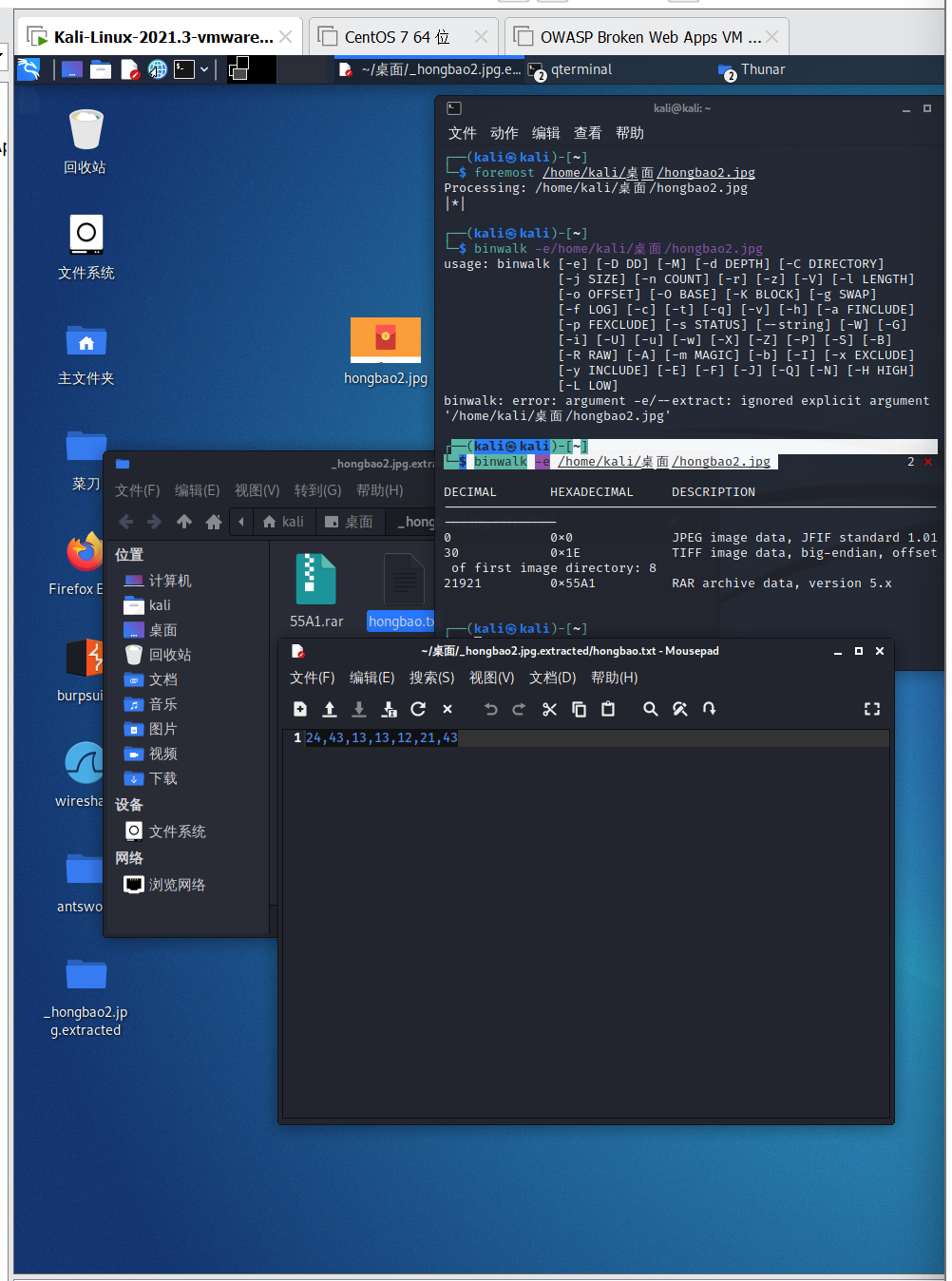
看到这串字符感觉无从下手,去查资料,关于编码,找到了一个略显靠谱的:敲击码
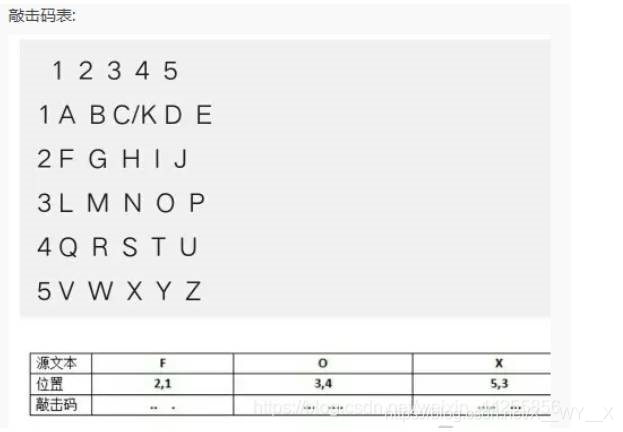
根据上述解码图进行解码,得出flag:
打开题目附件里的文件夹,发现有一个txt文件和一个rar的压缩文件。
打开rar压缩包发现需要密码,打开itxt文件
1:3:1; 1.25:3:1; 1.5:3:1; 1.75:3:1; 2:3:1; 2:2.75:1; 2:2.5:1; 2:2.25:1; 2:2:1; 2:1.75:1; 2:1.5:1; 1:2.25:1; 1.25:2.25:1; 1.5:2.25:1; 1.75:2.25:1; 1:1.5:1; 1.25:1.5:1; 1.5:1.5:1; 1.75:1.5:1; 3:3:1; 3.25:3:1; 3.5:3:1; 3.75:3:1; 4:3:1; 3.25:2.25:1; 3.5:2.25:1; 3.75:2.25:1; 4:2.25:1; 4:2:1; 4:1.75:1; 4:1.5:1; 3:1.5:1; 3.25:1.5:1; 3.5:1.5:1; 3.75:1.5:1; 3:1.75:1; 3:2:1; 3:2.25:1; 3:2.5:1; 3:2.75:1; 5:3:1; 5.25:3:1; 5.5:3:1; 5.75:3:1; 6:3:1; 6:2.25:1; 6:2:1; 6:1.75:1; 6:1.5:1; 5.75:1.5:1; 5.5:1.5:1; 5.25:1.5:1; 5:1.5:1; 5:2.25:1; 5.25:2.25:1; 5.5:2.25:1; 5.75:2.25:1; 5:2.5:1; 5:2.75:1; 7:3:1; 7.25:3:1; 7.5:3:1; 7.75:3:1; 8:3:1; 8:2.75:1; 8:2.5:1; 8:2.25:1; 8:2:1; 8:1.75:1; 8:1.5:1; 9:3:1; 9.25:3:1; 9.5:3:1; 9.75:3:1; 10:3:1; 10:2.75:1; 10:2.5:1; 10:2.25:1; 9.75:2.25:1; 9.5:2.25:1; 9.25:2.25:1; 9:2.25:1; 9:2:1; 9:1.75:1; 9:1.5:1; 9.25:1.5:1; 9.5:1.5:1; 9.75:1.5:1; 10:1.5:1; 11:3:1; 11.25:3:1; 11.5:3:1; 11.75:3:1; 12:3:1; 12:2.75:1; 12:2.5:1; 12:2.25:1; 12:2:1; 12:1.75:1; 12:1.5:1; 11.75:1.5:1; 11.5:1.5:1; 11.25:1.5:1; 11:1.5:1; 11:1.75:1; 11:2:1; 11:2.25:1; 11:2.5:1; 11:2.75:1; 11.25:2.25:1; 11.5:2.25:1; 11.75:2.25:1
通过百度得到一个脚本来生成3D图片:
1 from matplotlib import pyplot as plt 2 from mpl_toolkits.mplot3d import Axes3D 3 dot1 = [[1, 3, 1], [1.25, 3, 1], [1.5, 3, 1], [1.75, 3, 1], [2, 3, 1], [2, 2.75, 1], [2, 2.5, 1], [2, 2.25, 1], [2, 2, 1], [2, 1.75, 1], [2, 1.5, 1], [1, 2.25, 1], [1.25, 2.25, 1], [1.5, 2.25, 1], [1.75, 2.25, 1], [1, 1.5, 1], [1.25, 1.5, 1], [1.5, 1.5, 1], [1.75, 1.5, 1], [3, 3, 1], [3.25, 3, 1], [3.5, 3, 1], [3.75, 3, 1], [4, 3, 1], [3.25, 2.25, 1], [3.5, 2.25, 1], [3.75, 2.25, 1], [4, 2.25, 1], [4, 2, 1], [4, 1.75, 1], [4, 1.5, 1], [3, 1.5, 1], [3.25, 1.5, 1], [3.5, 1.5, 1], [3.75, 1.5, 1], [3, 1.75, 1], [3, 2, 1], [3, 2.25, 1], [3, 2.5, 1], [3, 2.75, 1], [5, 3, 1], [5.25, 3, 1], [5.5, 3, 1], [5.75, 3, 1], [6, 3, 1], [6, 2.25, 1], [6, 2, 1], [6, 1.75, 1], [6, 1.5, 1], [5.75, 1.5, 1], [5.5, 1.5, 1], [5.25, 1.5, 1], [5, 1.5, 1], [5, 2.25, 1], [5.25, 2.25, 1], [5.5, 2.25, 1], [5.75, 2.25, 1], [5, 2.5, 1], [5, 2.75, 1], [7, 3, 1], [7.25, 3, 1], [7.5, 3, 1], [7.75, 3, 1], [8, 3, 1], [8, 2.75, 1], [8, 2.5, 1], [8, 2.25, 1], [8, 2, 1], [8, 1.75, 1], [8, 1.5, 1], [9, 3, 1], [9.25, 3, 1], [9.5, 3, 1], [9.75, 3, 1], [10, 3, 1], [10, 2.75, 1], [10, 2.5, 1], [10, 2.25, 1], [9.75, 2.25, 1], [9.5, 2.25, 1], [9.25, 2.25, 1], [9, 2.25, 1], [9, 2, 1], [9, 1.75, 1], [9, 1.5, 1], [9.25, 1.5, 1], [9.5, 1.5, 1], [9.75, 1.5, 1], [10, 1.5, 1], [11, 3, 1], [11.25, 3, 1], [11.5, 3, 1], [11.75, 3, 1], [12, 3, 1], [12, 2.75, 1], [12, 2.5, 1], [12, 2.25, 1], [12, 2, 1], [12, 1.75, 1], [12, 1.5, 1], [11.75, 1.5, 1], [11.5, 1.5, 1], [11.25, 1.5, 1], [11, 1.5, 1], [11, 1.75, 1], [11, 2, 1], [11, 2.25, 1], [11, 2.5, 1], [11, 2.75, 1], [11.25, 2.25, 1], [11.5, 2.25, 1], [11.75, 2.25, 1]] # 得到五个点 4 plt.figure() # 得到画面 5 ax1 = plt.axes(projection='3d') 6 ax1.set_xlim(0, 15) # X轴,横向向右方向 7 ax1.set_ylim(15, 0) # Y轴,左向与X,Z轴互为垂直 8 ax1.set_zlim(0, 15) # 竖向为Z轴 9 color1 = ['r', 'g', 'b', 'k', 'm'] 10 marker1 = ['o', 'v', '1', 's', 'H'] 11 i = 0 12 for x in dot1: 13 ax1.scatter(x[0], x[1], x[2], c=color1[1], 14 marker=marker1[1], linewidths=4) # 用散点函数画点 15 i += 1 16 plt.show()
运行脚本后得到:
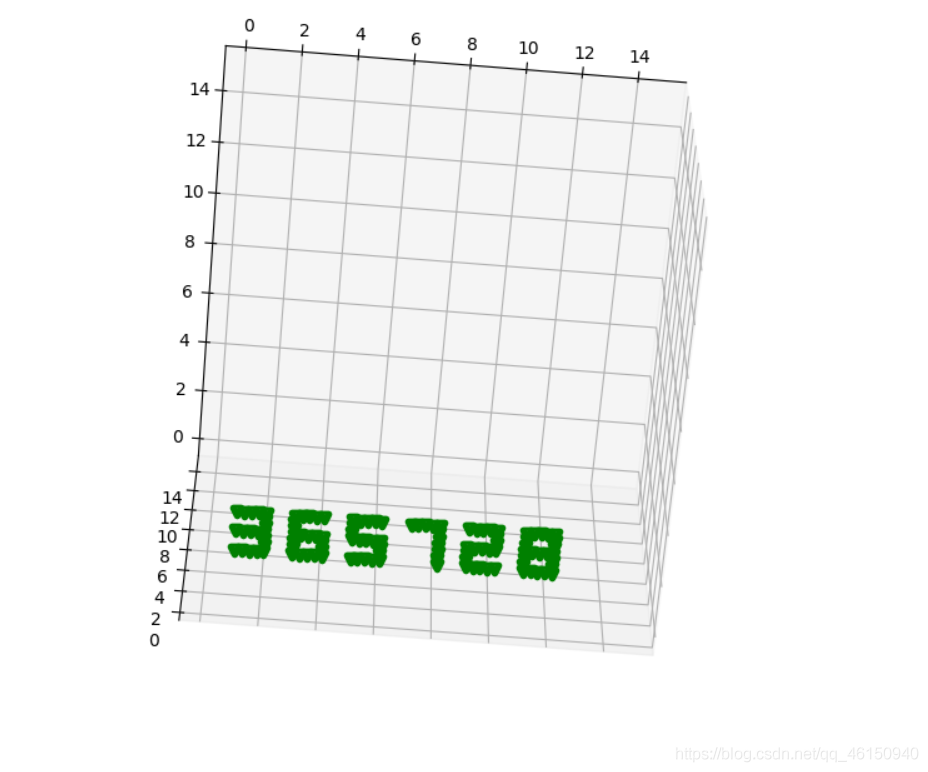
得到密码口令:365728
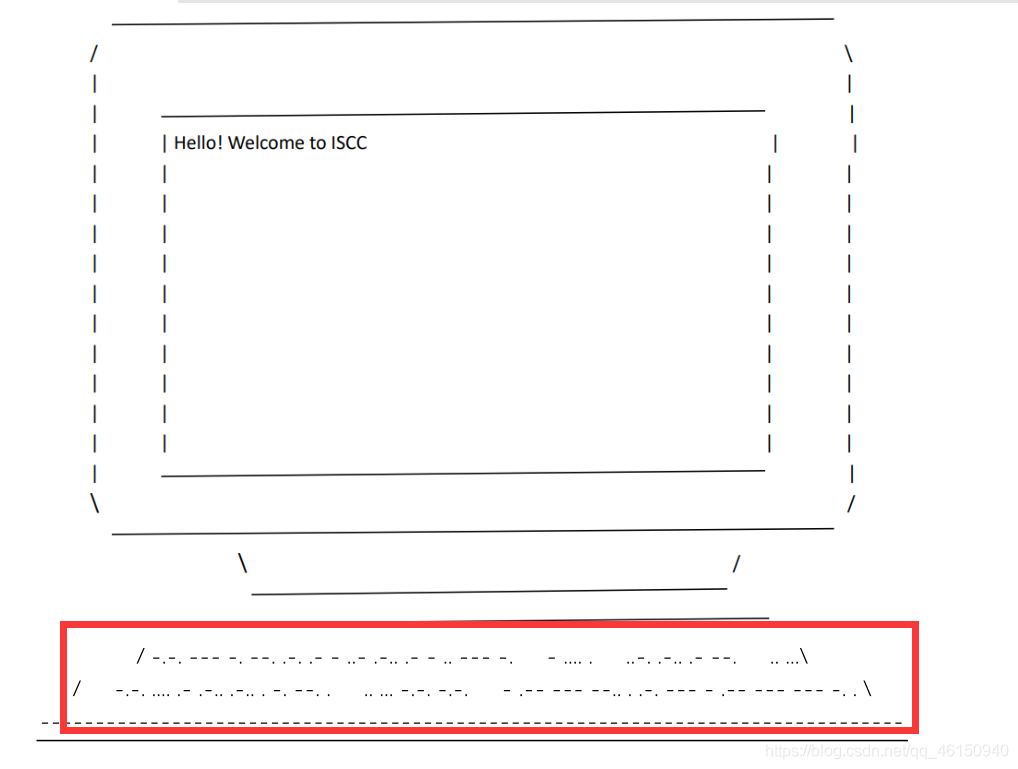
在解密后的压缩包内发现pdf,打开后在其中发现两行类似摩斯密码的段落,尝试解码
CONGRATULATIONTHEFLAGICHALLENGEISCCTWOZEROTWOONE
得出flag


 浙公网安备 33010602011771号
浙公网安备 33010602011771号