WIF - claims-based identity
最近使用了Sharepoint 2010的开发,其中包括一个新的服务STS,看了一下,主要资料如下:
现有的认证授权如Memebership的开发支持已经比较完善了,之所以引入WIF,主要是通过间接的形式抽象,使认证和授权在分布式环境下更易使用。
With the inflationary growth of distributed systems and online businesses, in the last few years the increasing need for interoperable protocols that could tear down the walls between silos became clear. The big players in the IT industry got together and agreed on a set of common protocols that would support interoperable communications across different platforms. Some examples of those protocols are SOAP, WS-Security, WS-Trust, WS-Federation, Security Assertion Markup Language (SAML), and in more recent times, OpenID, OAuth, and other open protocols.Claims-based identity promotes separation of concerns at a level never achieved before in the identity management world.
Windows Identity Foundation (WIF) is Microsoft’s stack for claims-based identity programming. It is a new foundational technology which helps .NET developers to take advantage of the claims based approach for handing authentication, authorization, customization and in general any identity-related task without the need to write any low-level code.
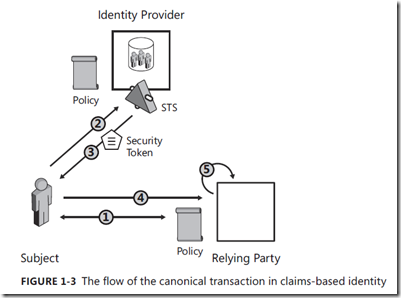
经典的claims-based identity过程
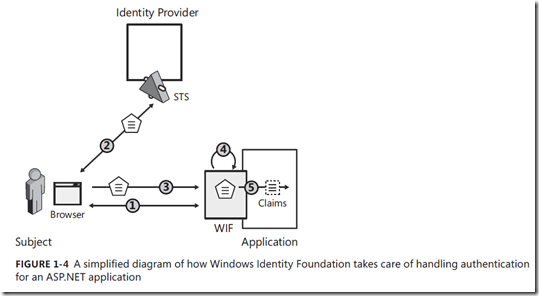
WIF的过程
identity providers (IP).
relying party (RP)
STS (Security Token Service).
WIF的具体过程:
1. WIF sits in front of your application in the ASP.NET pipeline. When an unauthenticated user requests a page, it redirects the browser to the identity provider pages.
2. Here the IP authenticates the user in whatever way it chooses (perhaps by showing a page with user name and password, using Kerberos, or in some other way). Then it manufactures a token with the required claims and sends it back.
3. The browser posts the token it got from the IP to the application, where WIF again intercepts the request.
4. If the token satisfies the requirements of the application (that is, it comes from the right IP, contains the right claims, and so on), the user is considered authenticated. WIF then drops a cookie, and a session is established.
5. The claims in the incoming token are made available to the application code, and the control is passed to the application.
参考资料
■ The WIF product home page on http://www.microsoft.com/wif
WIF Runtime 和 WIF SDK
■ The Identity Developer Training Kit at http://go.microsoft.com/fwlink/?LinkId=148795
很多的例子和概念展示
■ The WIF team blog at http://blogs.msdn.com/card
■ The IdElement Show on Channel9: http://channel9.msdn.com/shows/Identity/





【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· SQL Server 2025 AI相关能力初探
· Linux系列:如何用 C#调用 C方法造成内存泄露
· AI与.NET技术实操系列(二):开始使用ML.NET
· 记一次.NET内存居高不下排查解决与启示
· 探究高空视频全景AR技术的实现原理
· 阿里最新开源QwQ-32B,效果媲美deepseek-r1满血版,部署成本又又又降低了!
· SQL Server 2025 AI相关能力初探
· AI编程工具终极对决:字节Trae VS Cursor,谁才是开发者新宠?
· 开源Multi-agent AI智能体框架aevatar.ai,欢迎大家贡献代码
· Manus重磅发布:全球首款通用AI代理技术深度解析与实战指南