BUUCTF_Re_[2019红帽杯]easyRE
64位,elf文件

查找字符串,发现一大串,看着下面的ABCDEFG就是base64
然后多层解密之后就得到一串网址:
https://bbs.pediy.com/thread-254172.htm
当然,没啥卵用
然后发现continue前面有个加密函数
exp:
s1='Iodl>Qnb(ocy' num=127 s2='y.i' s3='d`3w}wek9{iy=~yL@EC' s=[] flag='' for i in range(len(s1)): s.append(ord(s1[i])) s.append(num) for i in range(len(s2)): s.append(ord(s2[i])) s.append(num) for i in range(len(s3)): s.append(ord(s3[i])) for i in range(len(s)): flag+=chr(s[i]^i) print(flag)
得到:
Info:The first four chars are `flag`
废话

然后这里有些没见过的字符串
进函数看看
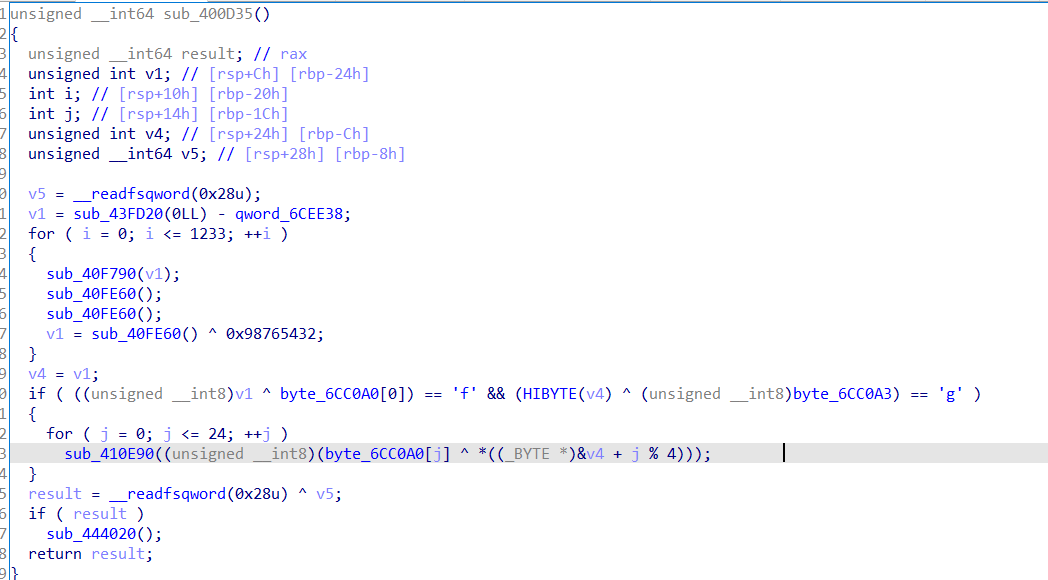
第十行的if判断
v1和.....&YA1A0进行异或==f
v4=v1
v1和.....A3进行异或==g
其实就是字符的前四位异或之后等于flag
exp
s=['40','35','20','56'] s1='flag' v4='' for i in range(4): v4+=chr(int(s[i],16)^ord(s1[i])) print(v4)
得到v4=v1=&YA1
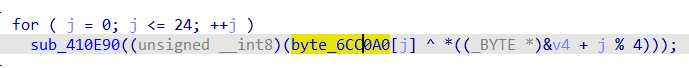
接着这个循环
exp
v4='&YA1' s=['40','35','20','56','5D','18','22','45','17','2F','24','6E','62','3C','27','54','48','6C','24','6E','72','3C','32','45','5B'] flag='' for i in range(len(s)): flag+=chr(int(s[i],16)^ord(v4[i%4])) print(flag)
get新知识
((_BYTE *)&v4 + j % 4))==v4[j%4]
flag:
flag{Act1ve_Defen5e_Test}

