NSSCTF_Round#1 Basic!_Misc_cut_into_thirds
raw文件,内存取证
part1:
代码:
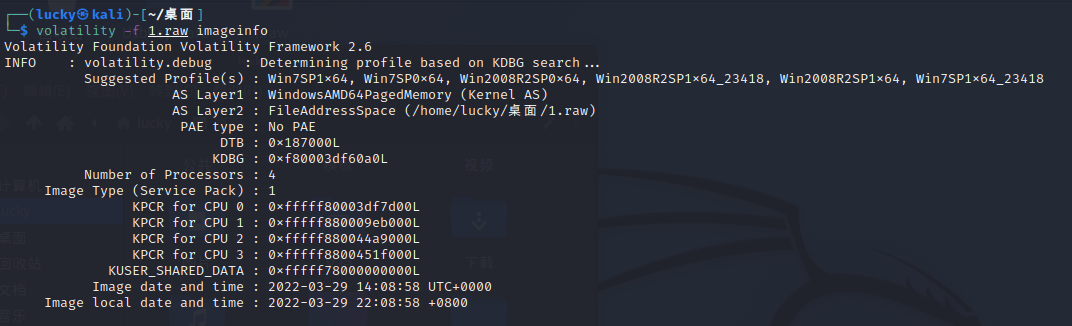
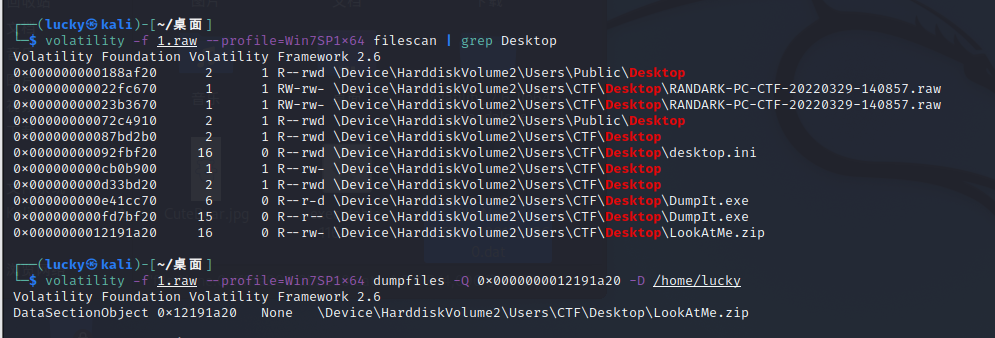
┌──(lucky㉿kali)-[~/桌面] └─$ volatility -f 1.raw --profile=Win7SP1x64 filescan | grep Desktop Volatility Foundation Volatility Framework 2.6 0x000000000188af20 2 1 R--rwd \Device\HarddiskVolume2\Users\Public\Desktop 0x00000000022fc670 1 1 RW-rw- \Device\HarddiskVolume2\Users\CTF\Desktop\RANDARK-PC-CTF-20220329-140857.raw 0x00000000023b3670 1 1 RW-rw- \Device\HarddiskVolume2\Users\CTF\Desktop\RANDARK-PC-CTF-20220329-140857.raw 0x00000000072c4910 2 1 R--rwd \Device\HarddiskVolume2\Users\Public\Desktop 0x00000000087bd2b0 2 1 R--rwd \Device\HarddiskVolume2\Users\CTF\Desktop 0x00000000092fbf20 16 0 R--rwd \Device\HarddiskVolume2\Users\CTF\Desktop\desktop.ini 0x000000000cb0b900 1 1 R--rw- \Device\HarddiskVolume2\Users\CTF\Desktop 0x000000000d33bd20 2 1 R--rwd \Device\HarddiskVolume2\Users\CTF\Desktop 0x000000000e41cc70 6 0 R--r-d \Device\HarddiskVolume2\Users\CTF\Desktop\DumpIt.exe 0x000000000fd7bf20 15 0 R--r-- \Device\HarddiskVolume2\Users\CTF\Desktop\DumpIt.exe 0x0000000012191a20 16 0 R--rw- \Device\HarddiskVolume2\Users\CTF\Desktop\LookAtMe.zip
┌──(lucky㉿kali)-[~/桌面] └─$ volatility -f 1.raw --profile=Win7SP1x64 dumpfiles -Q 0x0000000012191a20 -D /home/lucky Volatility Foundation Volatility Framework 2.6 DataSectionObject 0x12191a20 None \Device\HarddiskVolume2\Users\CTF\Desktop\LookAtMe.zip
保存文件后得到
3930653363343839
base16之后:
90e3c489
part2
代码
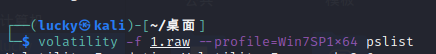
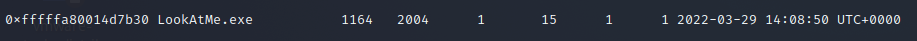
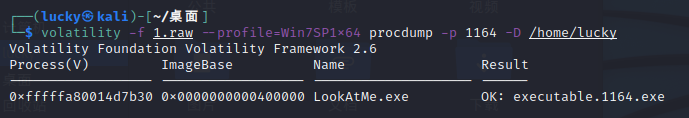
┌──(lucky㉿kali)-[~/桌面] └─$ volatility -f 1.raw --profile=Win7SP1x64 pslist Volatility Foundation Volatility Framework 2.6 Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------ 0xfffffa800042a9e0 System 4 0 99 461 ------ 0 2022-03-29 14:07:59 UTC+0000 0xfffffa8000e0cb30 smss.exe 280 4 5 32 ------ 0 2022-03-29 14:07:59 UTC+0000 0xfffffa8002da8b30 csrss.exe 368 348 9 321 0 0 2022-03-29 14:08:00 UTC+0000 0xfffffa8002da4ac0 wininit.exe 420 348 7 94 0 0 2022-03-29 14:08:00 UTC+0000 0xfffffa8002da7b30 csrss.exe 428 412 11 198 1 0 2022-03-29 14:08:00 UTC+0000 0xfffffa8001026060 winlogon.exe 476 412 6 121 1 0 2022-03-29 14:08:00 UTC+0000 0xfffffa8001058200 services.exe 520 420 16 205 0 0 2022-03-29 14:08:00 UTC+0000 0xfffffa8001062b30 lsass.exe 536 420 11 493 0 0 2022-03-29 14:08:00 UTC+0000 0xfffffa8001064760 lsm.exe 544 420 12 159 0 0 2022-03-29 14:08:00 UTC+0000 0xfffffa80010cab30 svchost.exe 644 520 15 368 0 0 2022-03-29 14:08:00 UTC+0000 0xfffffa80010f2b30 VBoxService.ex 708 520 13 132 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa800110db30 svchost.exe 776 520 8 234 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa8001149b30 svchost.exe 868 520 20 396 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa800116c400 svchost.exe 904 520 25 440 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa8001178b30 svchost.exe 936 520 28 560 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa800119ab30 audiodg.exe 1016 868 6 131 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa8000c26a00 svchost.exe 348 520 15 258 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa8000ce3620 svchost.exe 1040 520 20 373 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa8000d51590 spoolsv.exe 1224 520 16 310 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa80011cfb30 svchost.exe 1256 520 17 258 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa80011e5b30 svchost.exe 1352 520 14 207 0 0 2022-03-29 14:08:01 UTC+0000 0xfffffa8001394b30 taskhost.exe 1868 520 11 186 1 0 2022-03-29 14:08:33 UTC+0000 0xfffffa80013c8b30 dwm.exe 1944 904 3 96 1 0 2022-03-29 14:08:34 UTC+0000 0xfffffa80013e8b30 explorer.exe 2004 1928 41 992 1 0 2022-03-29 14:08:34 UTC+0000 0xfffffa800144c780 VBoxTray.exe 1608 2004 15 154 1 0 2022-03-29 14:08:34 UTC+0000 0xfffffa80014d7b30 LookAtMe.exe 1164 2004 1 15 1 1 2022-03-29 14:08:50 UTC+0000 0xfffffa80014cf820 conhost.exe 300 428 2 59 1 0 2022-03-29 14:08:50 UTC+0000 0xfffffa800148cb30 DumpIt.exe 1552 2004 2 51 1 1 2022-03-29 14:08:57 UTC+0000 0xfffffa800148c060 conhost.exe 1708 428 2 59 1 0 2022-03-29 14:08:57 UTC+0000 ┌──(lucky㉿kali)-[~/桌面] └─$ volatility -f 1.raw --profile=Win7SP1x64 procdump -p 1164 -D~ /home/lucky Volatility Foundation Volatility Framework 2.6 ERROR : volatility.debug : ~ is not a directory ┌──(lucky㉿kali)-[~/桌面] └─$ volatility -f 1.raw --profile=Win7SP1x64 procdump -p 1164 -D /home/lucky 1 ⨯ Volatility Foundation Volatility Framework 2.6 Process(V) ImageBase Name Result ------------------ ------------------ -------------------- ------ 0xfffffa80014d7b30 0x0000000000400000 LookAtMe.exe OK: executable.1164.exe
32位程序,ida查找字符得到
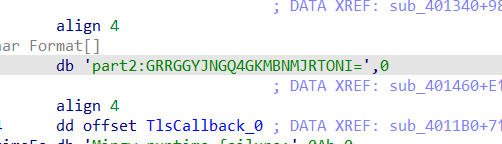
GRRGGYJNGQ4GKMBNMJRTONI=
base32后
4bca-48e0-bc75
part3
$ python2 vol.py -f /home/kali/Cut_into_thirds.raw --profile=Win7SP1x64 mimikatz Volatility Foundation Volatility Framework 2.6.1 Module User Domain Password -------- ---------------- ---------------- ---------------------------------------- wdigest CTF randark-PC-CTF part3:MTEwOTFmNWI3ZTNh wdigest RANDARK-PC-CTF$ WORKGROUP
MTEwOTFmNWI3ZTNh
base64解密
11091f5b7e3a
flag
NSSCTF{90e3c489-4bca-48e0-bc75-11091f5b7e3a}


