NSSCTF_RE_非常简单的逻辑题
flag = 'xxxxxxxxxxxxxxxxxxxxx' s = 'wesyvbniazxchjko1973652048@$+-&*<>' result = '' for i in range(len(flag)): s1 = ord(flag[i])//17 s2 = ord(flag[i])%17 result += s[(s1+i)%34]+s[-(s2+i+1)%34] print(result) # result = 'v0b9n1nkajz@j0c4jjo3oi1h1i937b395i5y5e0e$i'
逻辑很简单,就是整数除,取模运算
最开始想着逆运算取模,因为之前做密码学就试着逆着来,
瞟了一眼别个师傅的脚本,发现这种字符串ascii码取模可以直接爆破:
最开始我的代码是这样的:
flag = '' s = 'wesyvbniazxchjko1973652048@$+-&*<>' #for i in range(len(flag)): #s1 = ord(flag[i])//17 #s2 = ord(flag[i])%17 #result += s[(s1+i)%34]+s[-(s2+i+1)%34] #print(result) result = 'v0b9n1nkajz@j0c4jjo3oi1h1i937b395i5y5e0e$i' res='' num=0 for i in range(255): s1=i//17 s2=i%17 res=s[(s1+num)%34]+s[-(s2+num+1)%34] for j in range(0,len(result)-2): if res==result[j:j+2]: flag+=chr(i) num+=1 print(flag)
运行完了之后得到:-?ATjqs}Åä
很奇怪的字符
出错的原因在num最多只能增加到三十几,但是爆破需要num向255看齐,所以第二次修改就把for j循环提到255前面去:
flag = '' s = 'wesyvbniazxchjko1973652048@$+-&*<>' #for i in range(len(flag)): #s1 = ord(flag[i])//17 #s2 = ord(flag[i])%17 #result += s[(s1+i)%34]+s[-(s2+i+1)%34] #print(result) result = 'v0b9n1nkajz@j0c4jjo3oi1h1i937b395i5y5e0e$i' res='' num=0 for j in range(0,len(result)-2): for i in range(255): s1=i//17 s2=i%17 res=s[(s1+num)%34]+s[-(s2+num+1)%34] if res==result[j:j+2]: flag+=chr(i) num+=1 print(flag)
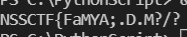
但是还是会出问题,和别个师傅的对比后发现,在j循环中,他把步长设成了2,期初一直以为两两分组只需要[i:i+2],欠缺思考了,
最终脚本:
flag = '' s = 'wesyvbniazxchjko1973652048@$+-&*<>' #for i in range(len(flag)): #s1 = ord(flag[i])//17 #s2 = ord(flag[i])%17 #result += s[(s1+i)%34]+s[-(s2+i+1)%34] #print(result) result = 'v0b9n1nkajz@j0c4jjo3oi1h1i937b395i5y5e0e$i' res='' num=0 for j in range(0,len(result)-2,2): for i in range(255): s1=i//17 s2=i%17 res=s[(s1+num)%34]+s[-(s2+num+1)%34] if res==result[j:j+2]: flag+=chr(i) num+=1 print(flag)
得到flag:NSSCTF{Fake_RERE_QAQ}


 浙公网安备 33010602011771号
浙公网安备 33010602011771号