NSSCTF_RE_简简单单的解密
import base64,urllib.parse key = "HereIsFlagggg" flag = "xxxxxxxxxxxxxxxxxxx" s_box = list(range(256)) j = 0 for i in range(256): j = (j + s_box[i] + ord(key[i % len(key)])) % 256 s_box[i], s_box[j] = s_box[j], s_box[i] res = [] i = j = 0 for s in flag: i = (i + 1) % 256 j = (j + s_box[i]) % 256 s_box[i], s_box[j] = s_box[j], s_box[i] t = (s_box[i] + s_box[j]) % 256 k = s_box[t] res.append(chr(ord(s) ^ k)) cipher = "".join(res) crypt = (str(base64.b64encode(cipher.encode('utf-8')), 'utf-8')) enc = str(base64.b64decode(crypt),'utf-8') enc = urllib.parse.quote(enc) print(enc) # enc = %C2%A6n%C2%87Y%1Ag%3F%C2%A01.%C2%9C%C3%B7%C3%8A%02%C3%80%C2%92W%C3%8C%C3%BA
参照大佬的脚本:
import base64,urllib.parse flag='' enc="%C2%A6n%C2%87Y%1Ag%3F%C2%A01.%C2%9C%C3%B7%C3%8A%02%C3%80%C2%92W%C3%8C%C3%BA" key = "HereIsFlagggg" crypt=urllib.parse.unquote(enc) s_box = list(range(256)) j = 0 for i in range(256): j = (j + s_box[i] + ord(key[i % len(key)])) % 256 s_box[i], s_box[j] = s_box[j], s_box[i] i = j = 0 for s in crypt: i = (i + 1) % 256 j = (j + s_box[i]) % 256 s_box[i], s_box[j] = s_box[j], s_box[i] t = (s_box[i] + s_box[j]) % 256 k = s_box[t] flag+=chr(ord(s) ^ k) print(flag)
当初没咋看懂这个,听说是RC4,
百度词条又这么一句话

所以直接抄了源代码的加密代码,然后quote的那个加密,:
NSSCTF{REAL_EZ_RC4}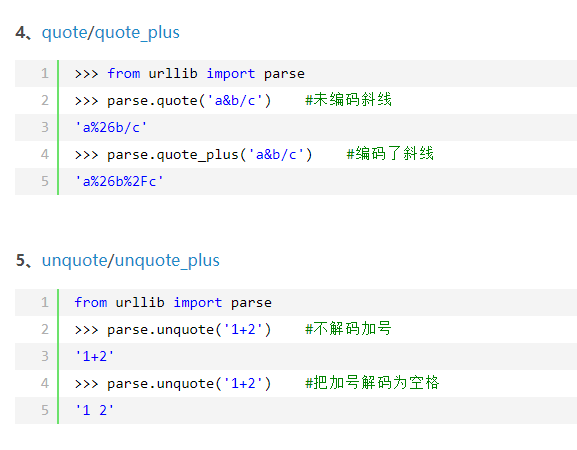
直接unquote解密就好了
博客地址:Python3 urllib.parse 常用函数示例 - <Hbw> - 博客园 (cnblogs.com)
最后得到flag:NSSCTF{REAL_EZ_RC4}





