2022MoeCTF整理复现(NSS平台)
一、[MoeCTF 2022]小纸条
1.jpg上的像是某种形式的猪圈密码,找一个对照表边猜边对照
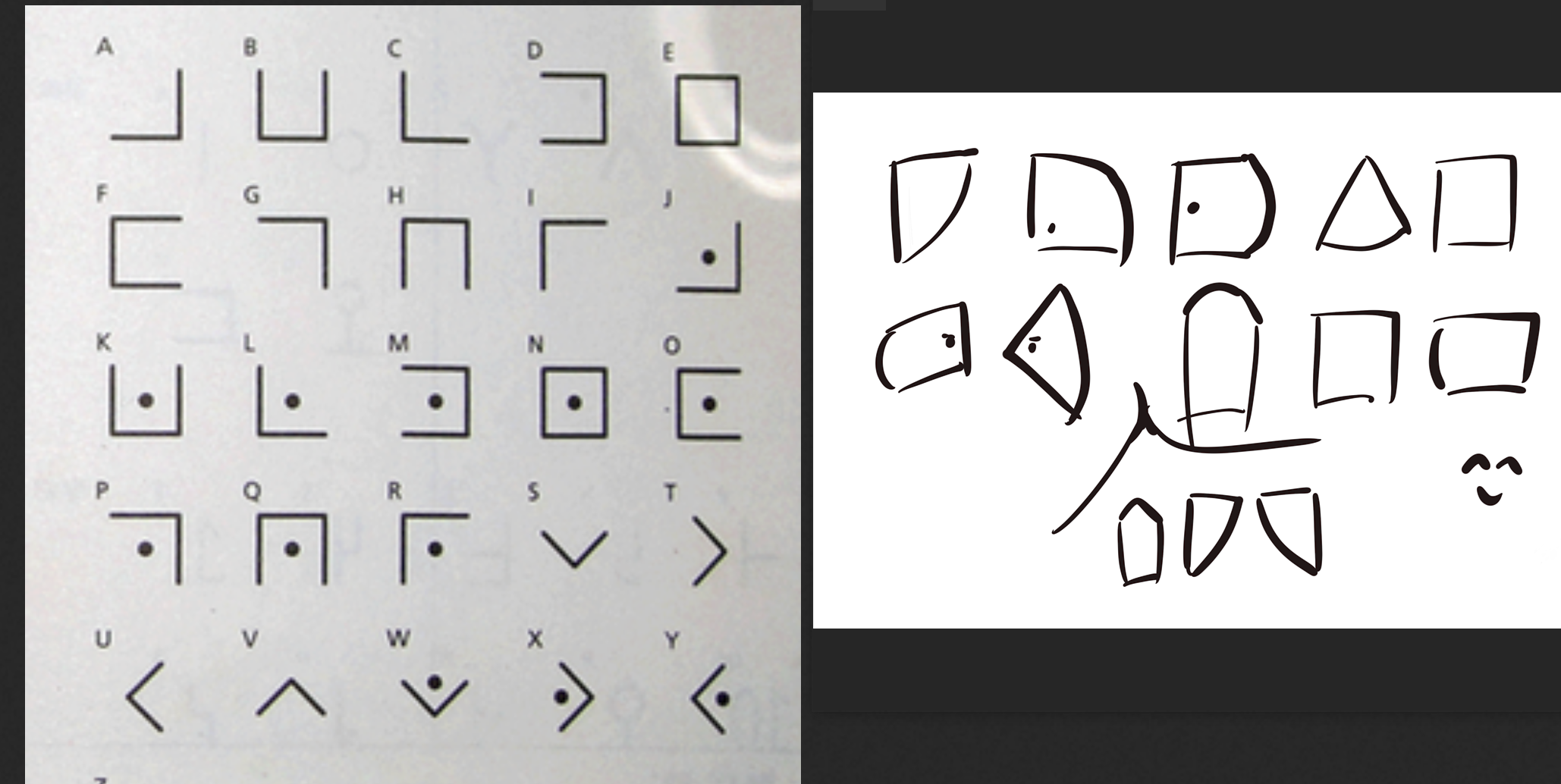
2.根据点和角的位置方向以及可能拼写成的单词,得到flag
moectf{ILOVEMYBIGBED}
二、[MoeCTF 2022]CCCC
1.得到一个C语言脚本,脚本思路就是首先定义一个名为flag的数组,然后使用for循环,flag[i]逐个与0xff进行异或,之后转为字符进行输出,直接运行程序就得到flag
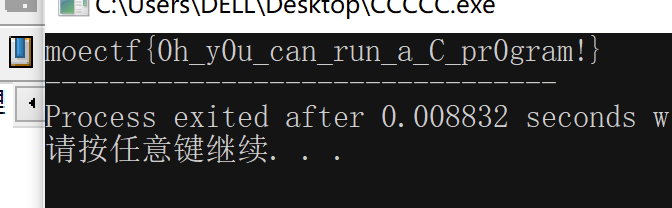
moectf{0h_y0u_can_run_a_C_pr0gram!}
三、[MoeCTF 2022]Python
1.得到一个python语言脚本,脚本思路就是首先定义一个名为enc的数组,然后进入一个for循环,enc[i]逐个先进行rol函数中的运算,然后与i相减,最后与key[i % len(key)]计算的值对应的ASCII值进行异或运算。for循环结束后逐个字符输出。
2.直接运行就可得到flag
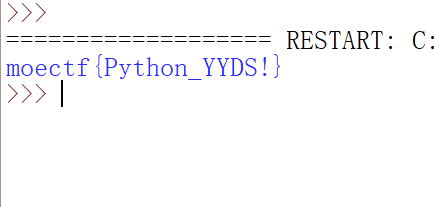
moectf{Python_YYDS!}
四、[MoeCTF 2022]run_me
1.题目提示cmd运行,那就cmd运行,得到flag
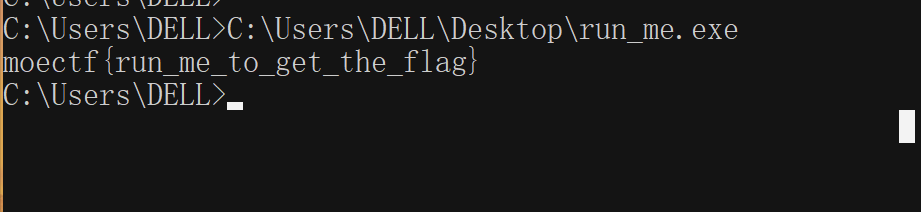
moectf{run_me_to_get_the_flag}
五、[MoeCTF 2022]run_me2
1.题目提示需要在linux环境下运行,使用kali跑一下,得到flag(感觉和nepnepxcatctf一道蛮像的)
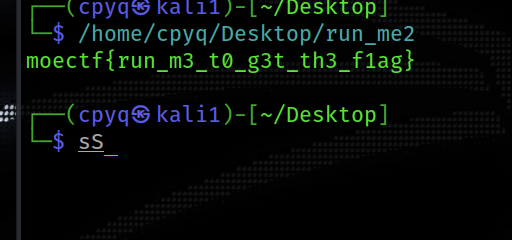
moectf{run_m3_t0_g3t_th3_f1ag}
六、[MoeCTF 2022]A_band
1.得到一堆0101,猜测是二进制编码,直接使用010进行转换-粘贴自二进制编码,得到十六进制字节
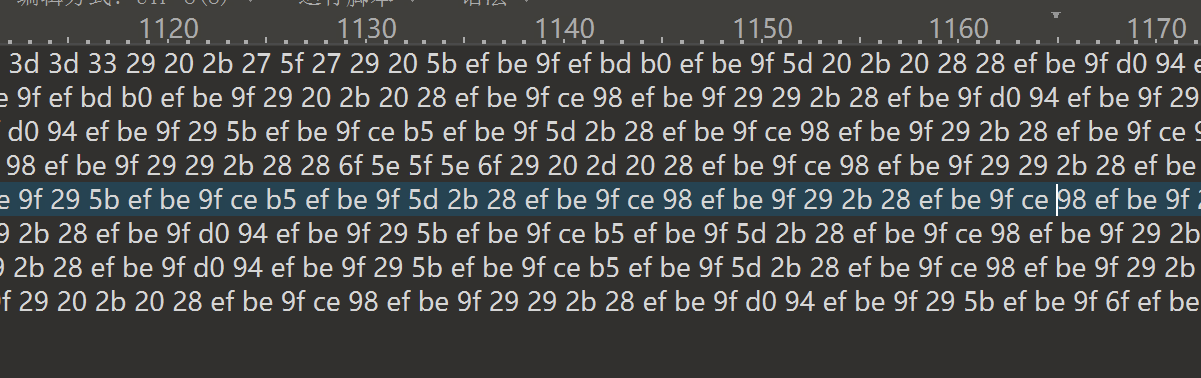
2.再以十六进制字节为文件源码-粘贴自十六进制文本,然后将编辑方式改为UTF-8,得到aaencode编码
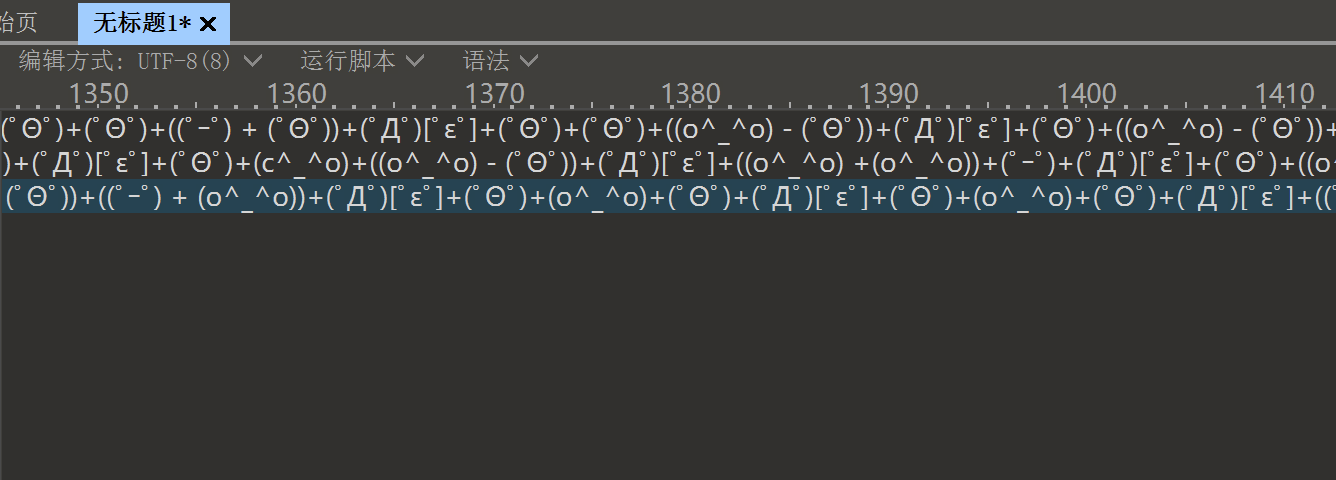
3.使用在线网站进行解密http://www.metools.info/code/aaencode214.html
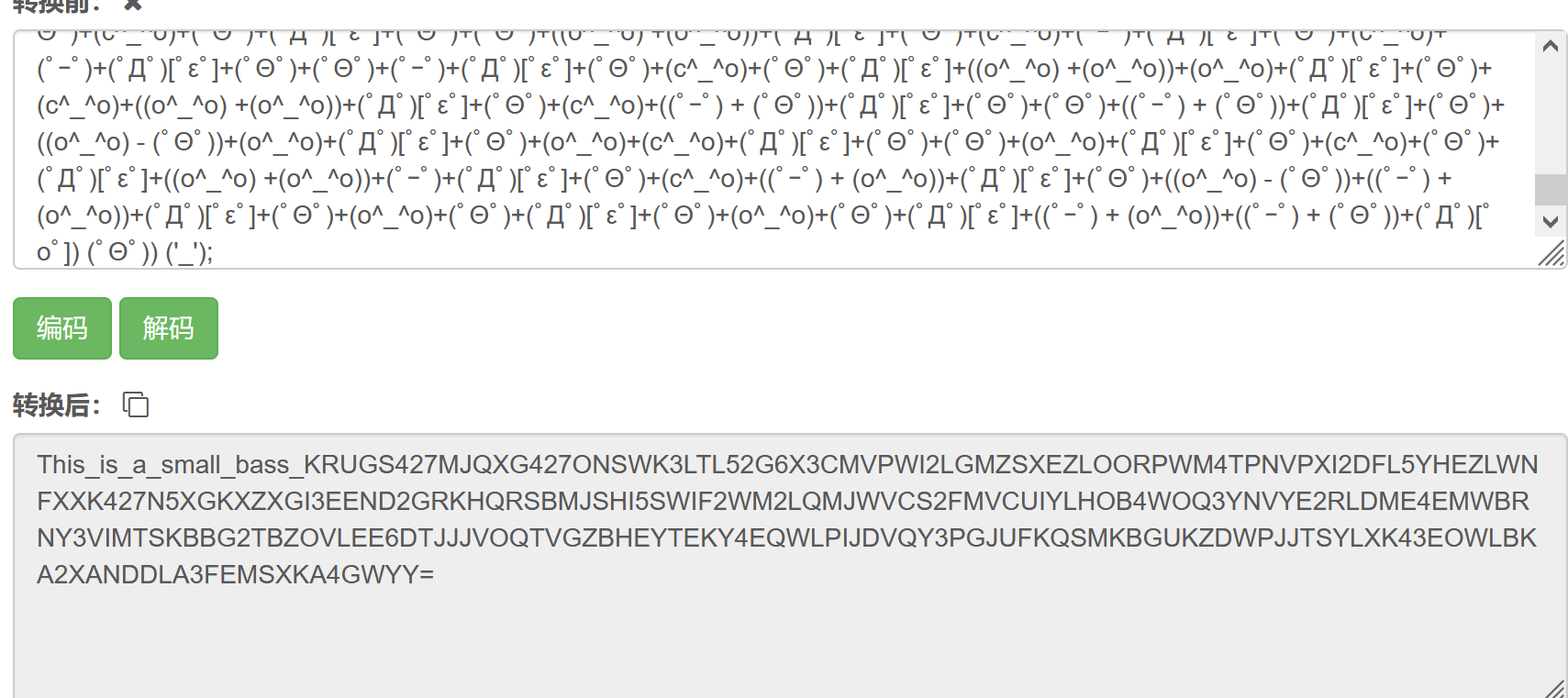
4.得到base,找个网站解密一下或者用basecrack,base32解密得到新内容
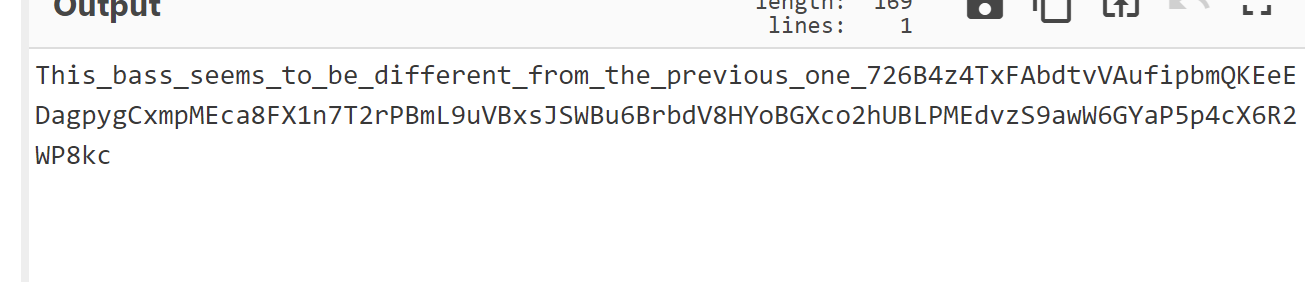
5.base58继续解密base部分,得到新的base
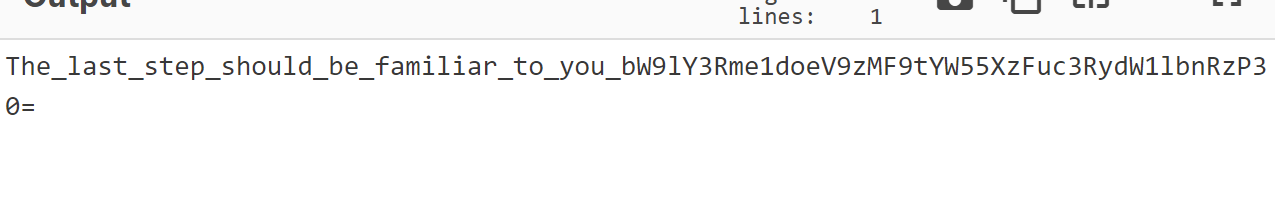
6.base64解密得到flag
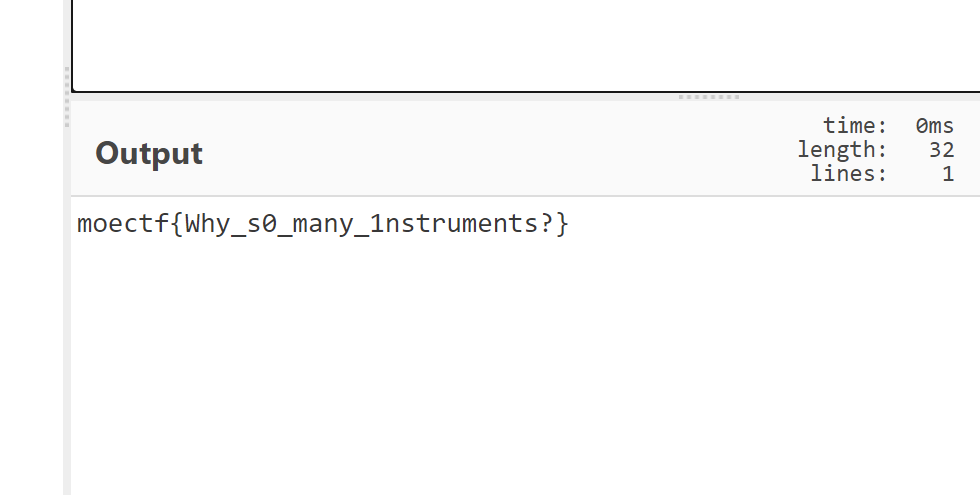
7.考的主要就是base套娃和颜文字
moectf{Why_s0_many_1nstruments?}
七、[MoeCTF 2022]bell202
1.首先搜索文件的名字,发现这个文件实际上是modem文件,kali上的minimodem可以分析这种文件,同时,找一下这个工具的使用手册,发现题目名称是一种FSK协议,同时也是指令要用到的参数之一

2.直接使用kali自带的minimodem,也可以去官网http://www.whence.com/minimodem/
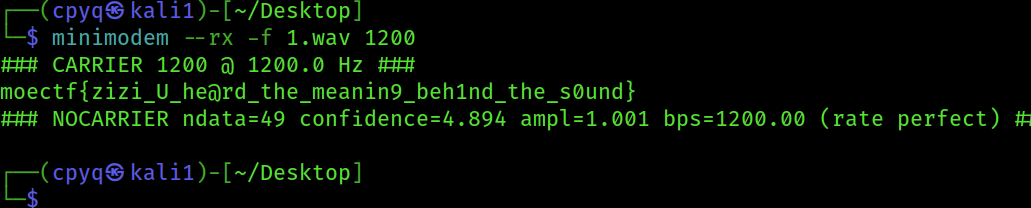
3.指令为minimodem --rx -f encoded.wav 1200 ,--rx或者-r均可,为指定读取模式;-f为读取文件;1200为bell202 bps对应参数,直接得到flag
moectf{zizi_U_he@rd_the_meanin9_beh1nd_the_s0und}
八、[MoeCTF 2022]cccrrc
1.直接打开显示加密,根据题目名字,猜测是crc32爆破,使用脚本工具,下载地址:https://github.com/theonlypwner/crc32
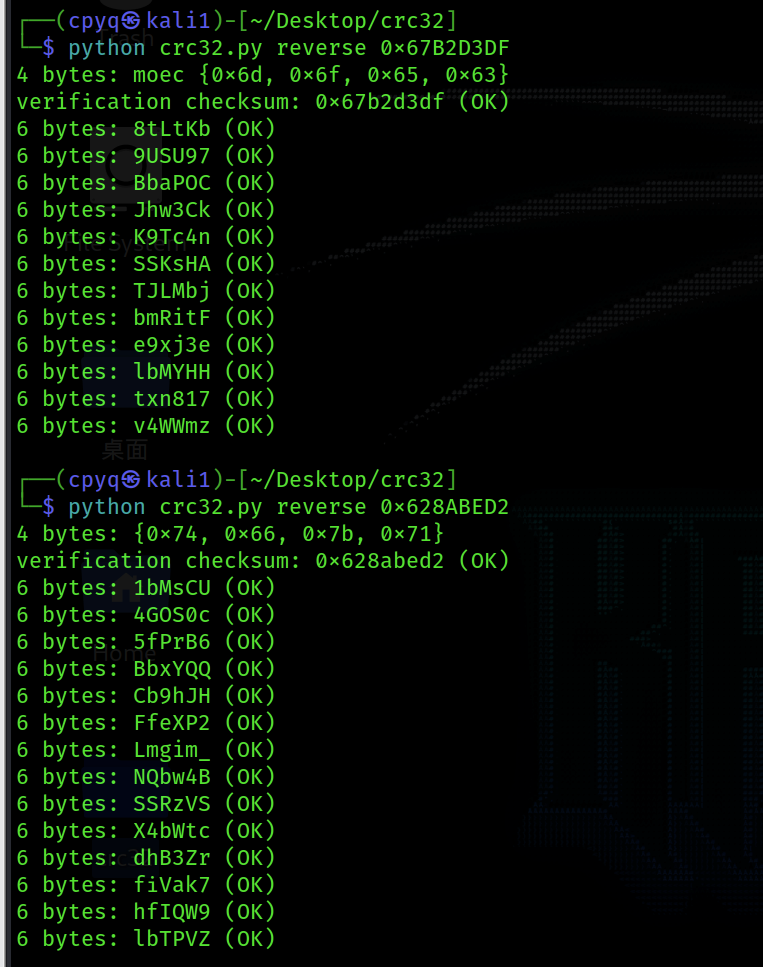
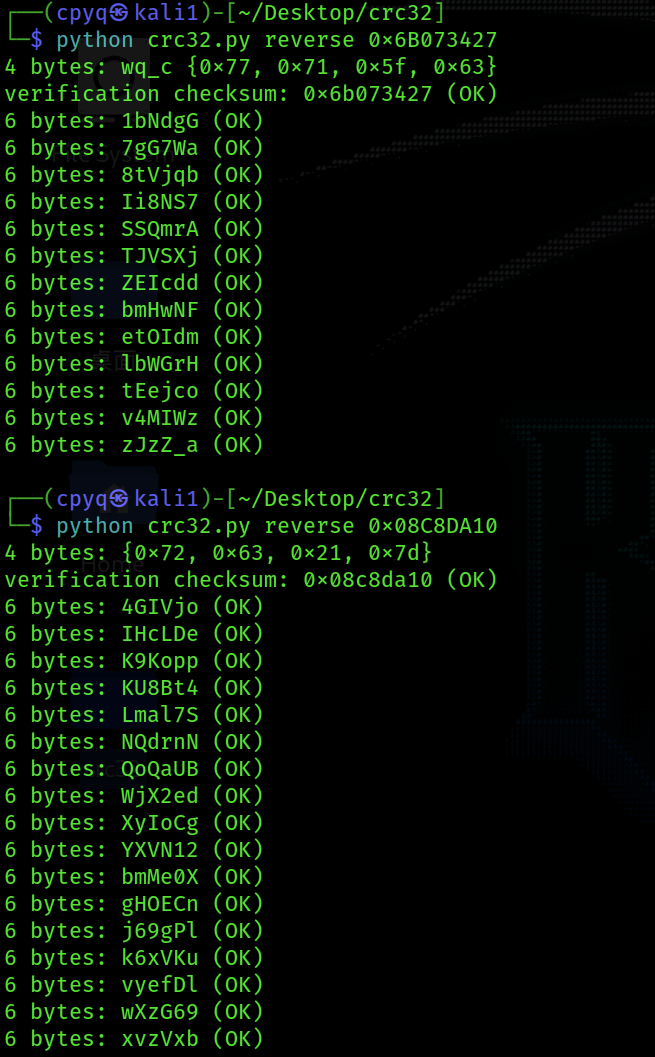
2.逐个4个txt进行爆破,按顺序找有意义的片段进行拼接(含点儿猜的成分),还有另一种方法,使用脚本进行直接获取内容,脚本末初大佬的博客里有提供https://blog.csdn.net/mochu7777777/article/details/110206427
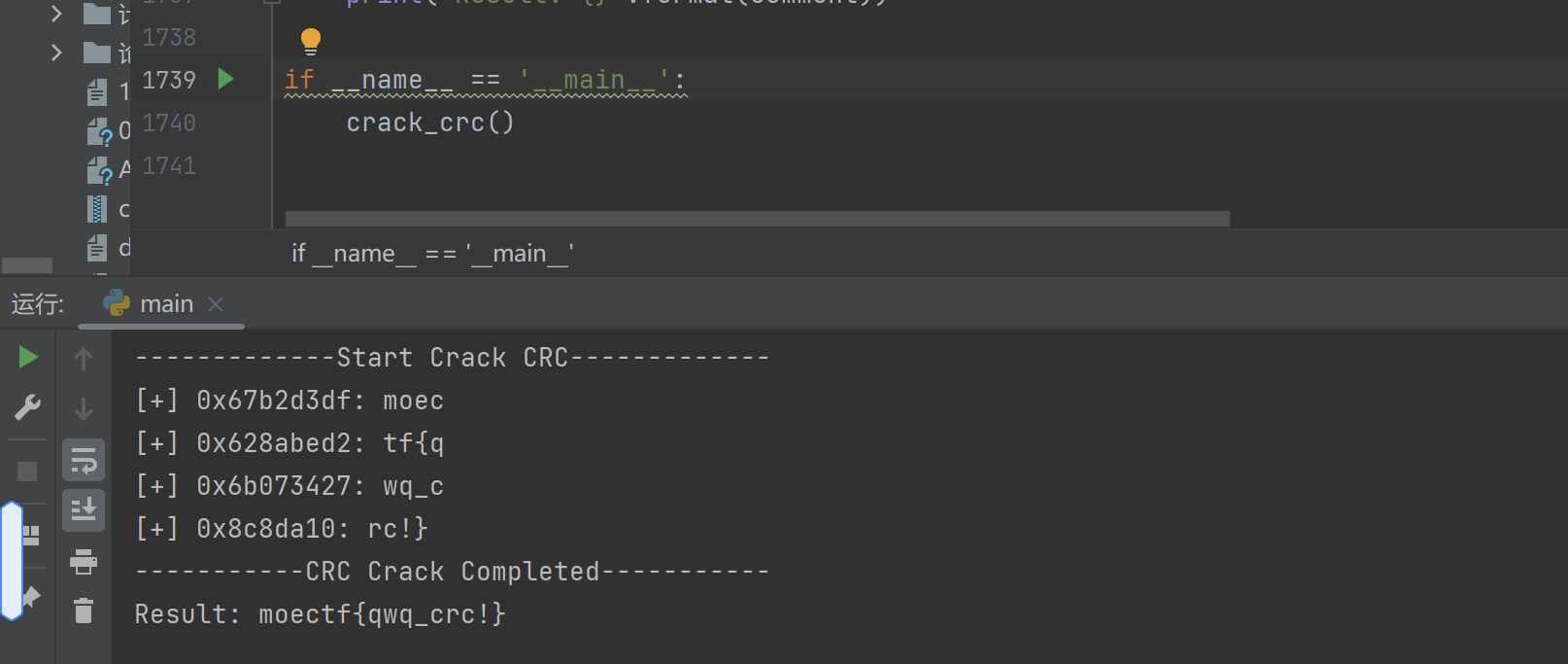
3.直接得到flag
moectf{qwq_crc!}
九、[MoeCTF 2022]Locked_bass
1.打开显示zip有密码,010打开,发现是伪加密,将09改为00,直接解压,在里面的zip中得到txt
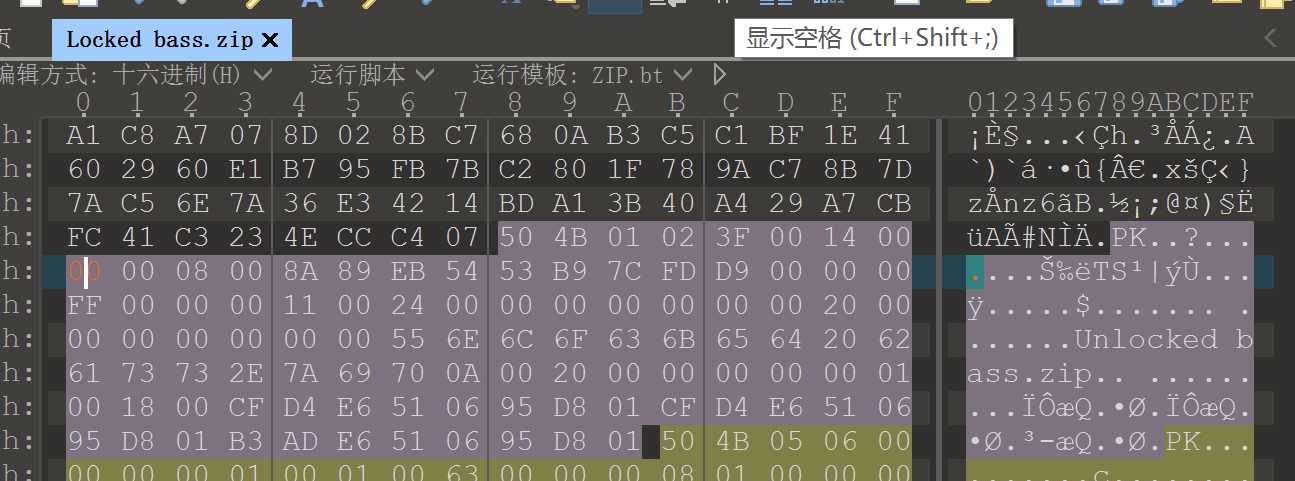
2.base64解码,得到flag
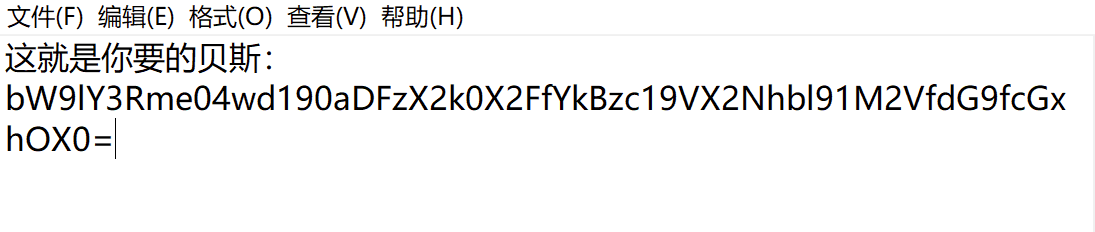
moectf{N0w_th1s_i4_a_b@ss_U_can_u3e_to_pla9}
十、[MoeCTF 2022]Misc指北
1.在pdf的末尾发现摩斯电码,厨师帽转换一下
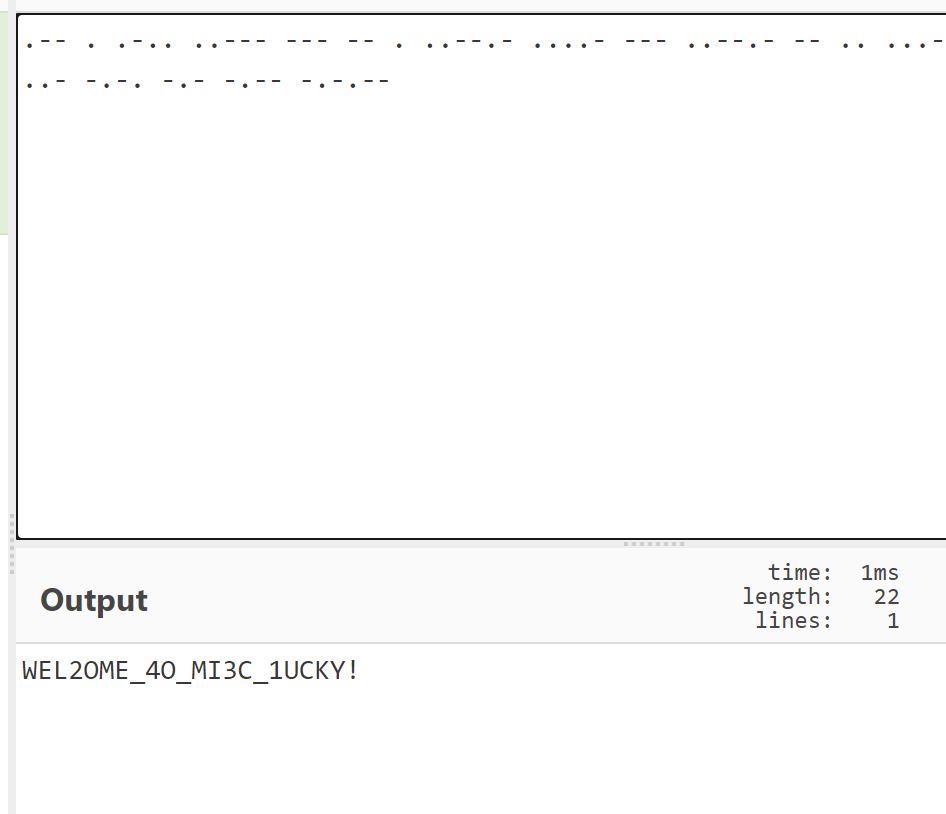
2.得到flag
NSSCTF{WEL2OME_4O_MI3C_1UCKY!}
十一、[MoeCTF 2022]nyanyanya
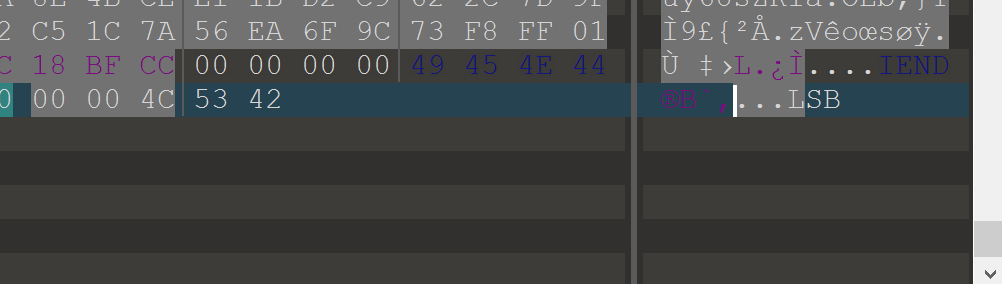
1.010打开,在末尾发现LSB,提示LSB隐写
2.使用zsteg跑一下,发现flag
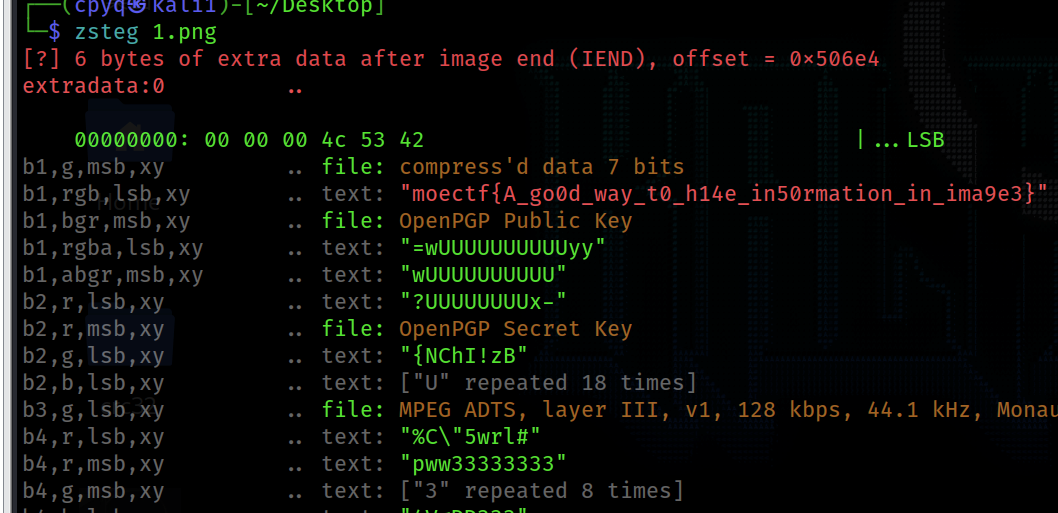
moectf{A_go0d_way_t0_h14e_in50rmation_in_ima9e3}
十二、[MoeCTF 2022]rabbit*
1.010打开,文件尾发现多余的字串,根据题目名字猜测是rabbit,无密码解密试一下
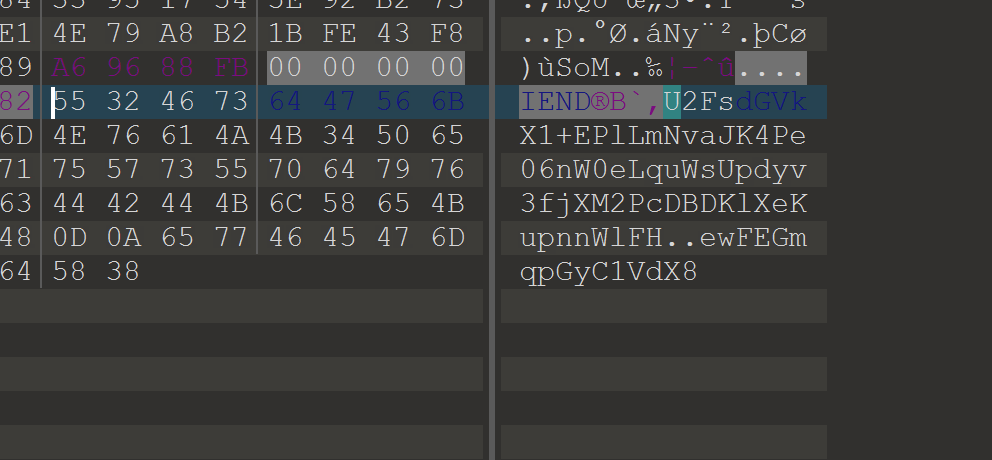
2.无密码解开,得到flag
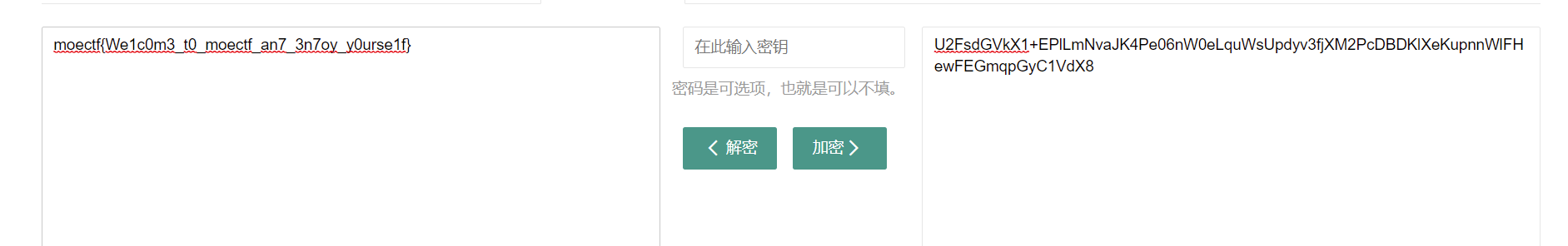
moectf{We1c0m3_t0_moectf_an7_3n7oy_y0urse1f}
十三、[MoeCTF 2022]what_do_you_recognize_me_by
1.得到无类型文件,010打开发现开头像是png,把6C改为47
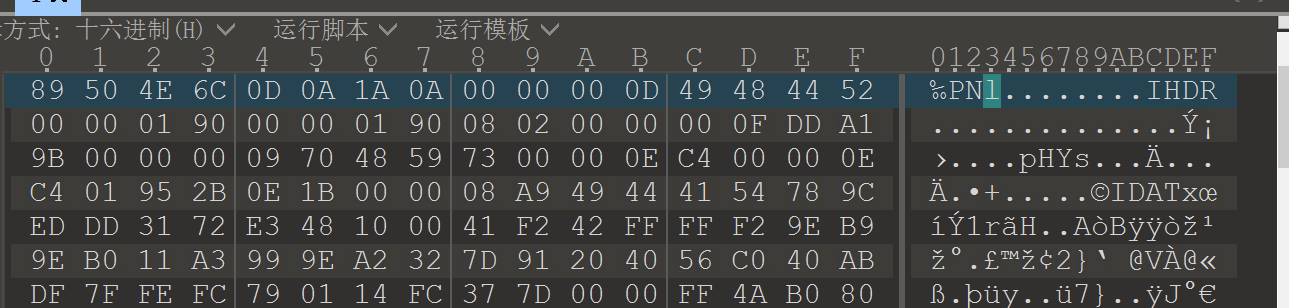
2.得到一张二维码,qr扫码得到flag
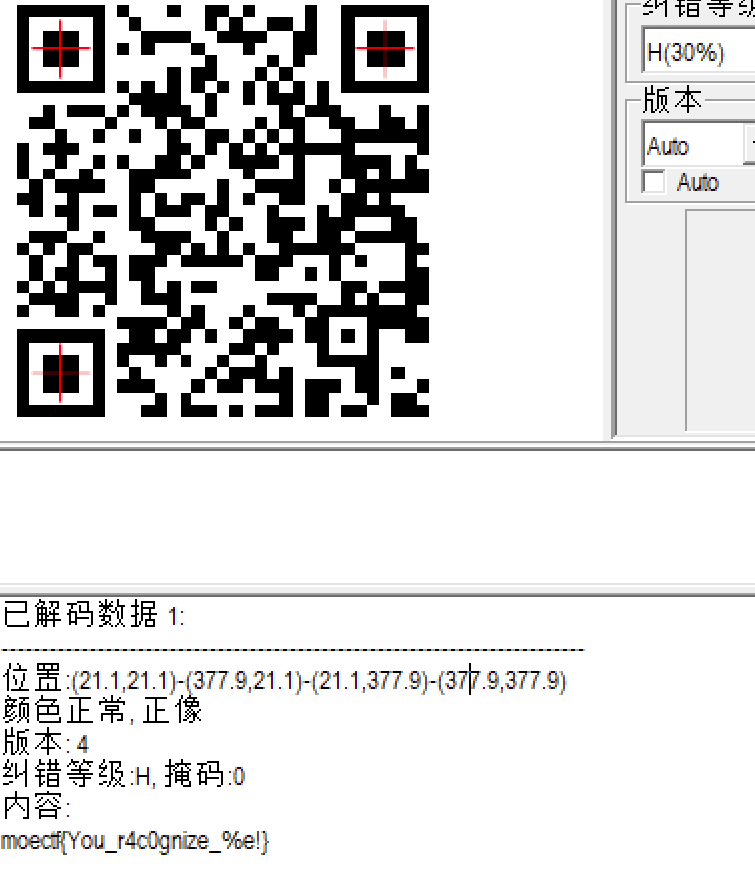
moectf{You_r4c0gnize_%e!}
十四、[MoeCTF 2022]zip套娃
1.直接打开显示有密码,没找到密码提示,直接先4位数字爆破一下,得到密码
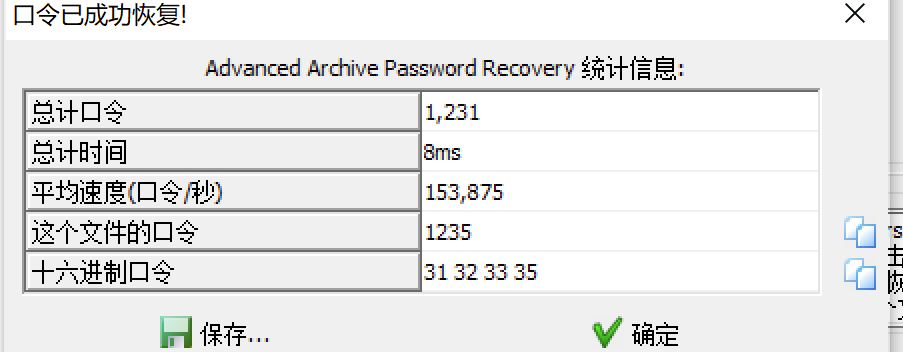
2.打开txt,明显是掩码

3.掩码爆破得到密码
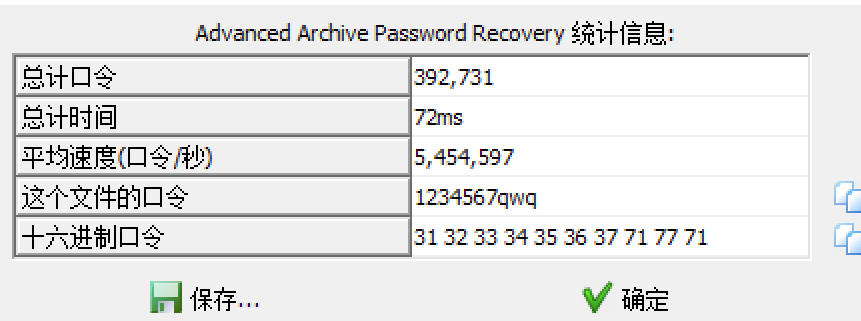
4.010打开,发现zip是伪加密,01改为00
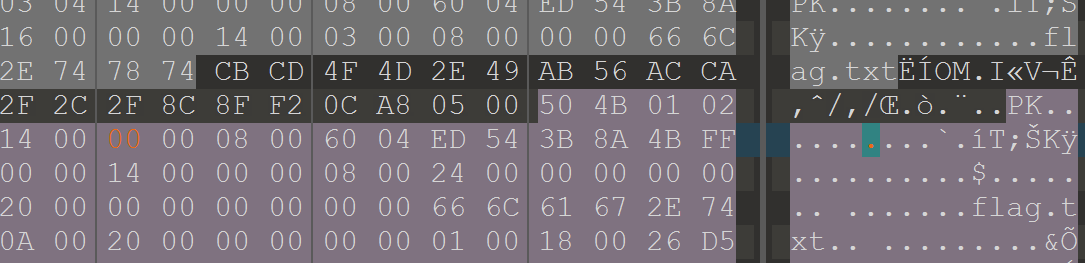
5.txt打开得到flag
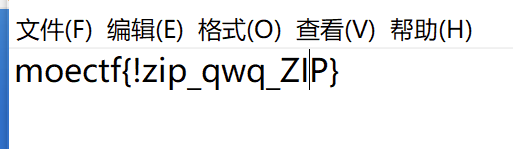
moectf{!zip_qwq_ZIP}
十五、[MoeCTF 2022]想听点啥
1.使用MuseScore可以打开whatdoyouliketohear.mscz(查了一下是乐谱文件),在乐谱的最后可以看到由音符拼成的一段字串,提示MOECTFI1iKE是密码
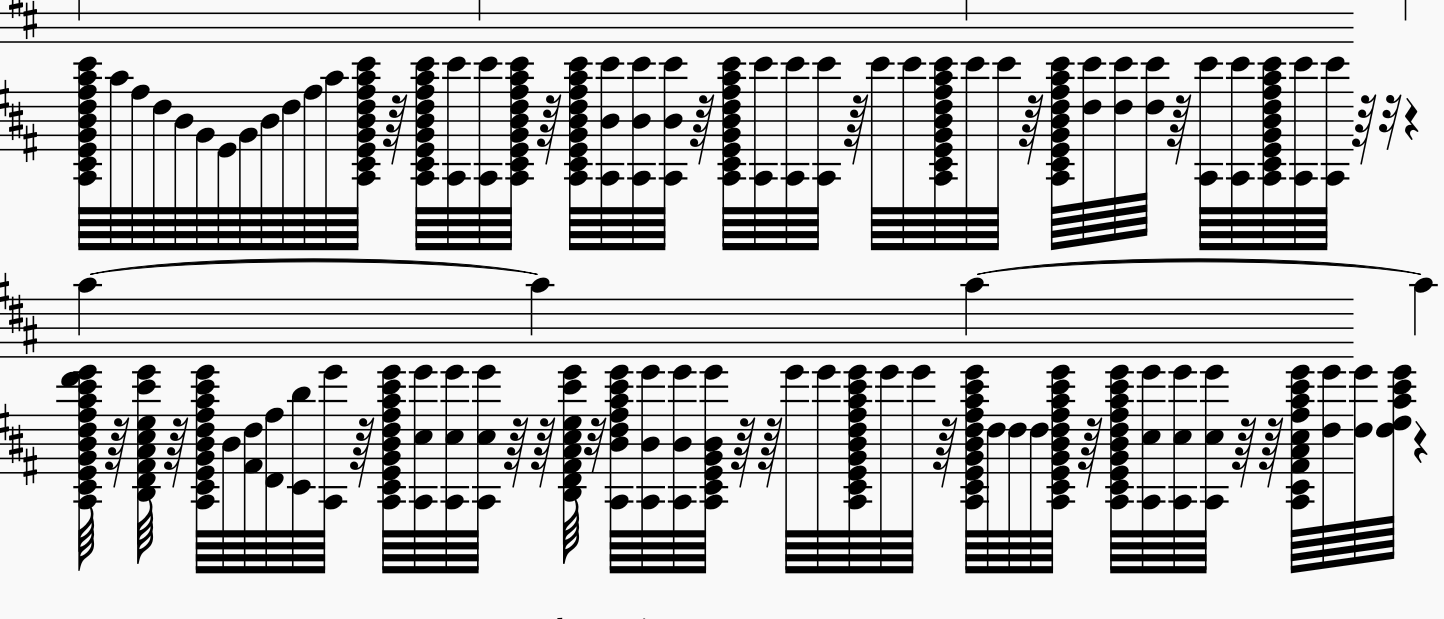
MOECTFI1iKE
2.密码解压得到一个脚本和一个txt,简单看一下代码,就是一个flag字串,逐位异或,输出字串存到txt中,利用异或的特点,异或回去,写个脚本
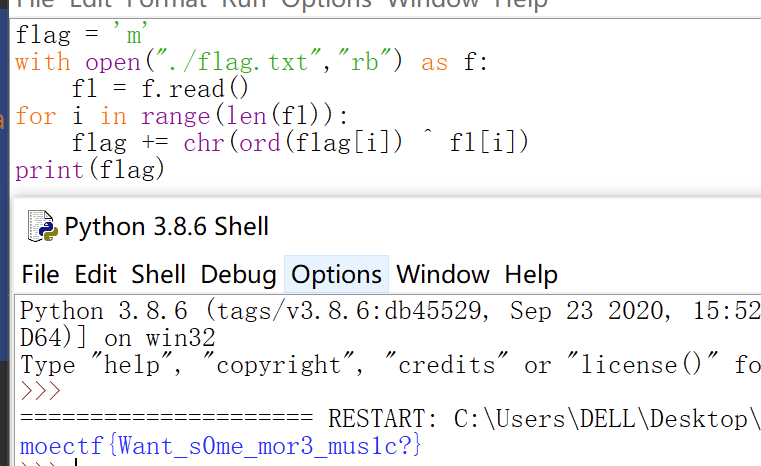
点击查看代码
flag = 'm'
with open("./flag.txt","rb") as f:
fl = f.read()
for i in range(len(fl)):
flag += chr(ord(flag[i]) ^ fl[i])
print(flag)
3.得到flag
moectf{Want_s0me_mor3_mus1c?}
十六、[MoeCTF 2022]usb
1.根据特点发现是USB中的键盘流量,先使用UsbKeyboardDataHacker工具,发现无法提取数据
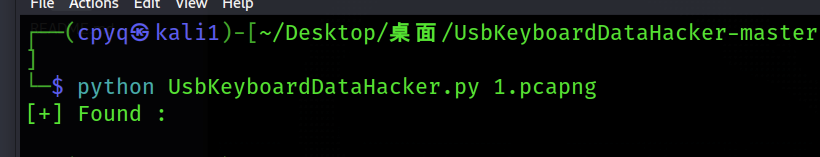
2.那就只能使用麻烦一点的方法了,先使用tshark提取其中的data数据
tshark -r usb.pcapng -T fields -e usbhid.data -Y "frame.len == 35" > data1.txt
3.把数据处理一下,0000000000000000和0200000000000000全部删去,否则会报错,使用之前积累的分析脚本和data1.txt,得到flag
点击查看代码
normalKeys = {"04":"a", "05":"b", "06":"c", "07":"d", "08":"e", "09":"f", "0a":"g", "0b":"h", "0c":"i", "0d":"j", "0e":"k", "0f":"l", "10":"m", "11":"n", "12":"o", "13":"p", "14":"q", "15":"r", "16":"s", "17":"t", "18":"u", "19":"v", "1a":"w", "1b":"x", "1c":"y", "1d":"z","1e":"1", "1f":"2", "20":"3", "21":"4", "22":"5", "23":"6","24":"7","25":"8","26":"9","27":"0","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"-","2e":"=","2f":"[","30":"]","31":"\\","32":"<NON>","33":";","34":"'","35":"<GA>","36":",","37":".","38":"/","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
shiftKeys = {"04":"A", "05":"B", "06":"C", "07":"D", "08":"E", "09":"F", "0a":"G", "0b":"H", "0c":"I", "0d":"J", "0e":"K", "0f":"L", "10":"M", "11":"N", "12":"O", "13":"P", "14":"Q", "15":"R", "16":"S", "17":"T", "18":"U", "19":"V", "1a":"W", "1b":"X", "1c":"Y", "1d":"Z","1e":"!", "1f":"@", "20":"#", "21":"$", "22":"%", "23":"^","24":"&","25":"*","26":"(","27":")","28":"<RET>","29":"<ESC>","2a":"<DEL>", "2b":"\t","2c":"<SPACE>","2d":"_","2e":"+","2f":"{","30":"}","31":"|","32":"<NON>","33":"\"","34":":","35":"<GA>","36":"<","37":">","38":"?","39":"<CAP>","3a":"<F1>","3b":"<F2>", "3c":"<F3>","3d":"<F4>","3e":"<F5>","3f":"<F6>","40":"<F7>","41":"<F8>","42":"<F9>","43":"<F10>","44":"<F11>","45":"<F12>"}
keys = open('data1.txt')
output = ""
for line in keys:
k = line[1]
n = line[4:6]
if k == '0':
print(normalKeys[n], end='')
elif k == '2':
print(shiftKeys[n], end='')
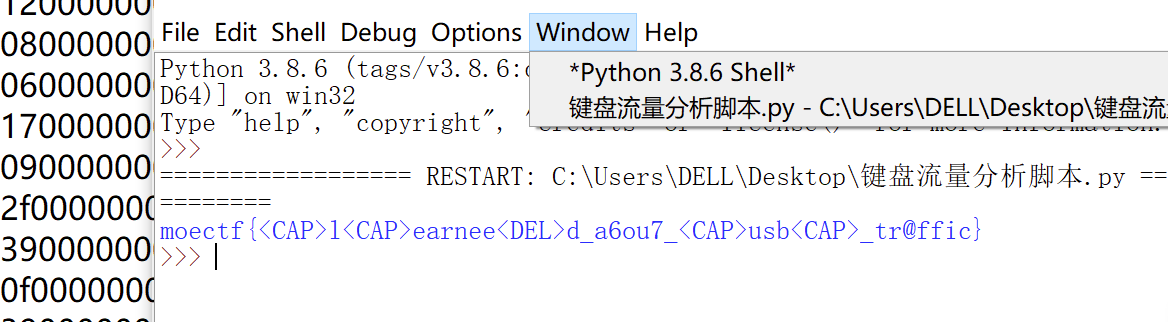
4.得到的flag中为大写,为删除,整理一下flag
moectf{Learned_a6ou7_USB_tr@ffic}



【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 分享一个免费、快速、无限量使用的满血 DeepSeek R1 模型,支持深度思考和联网搜索!
· 基于 Docker 搭建 FRP 内网穿透开源项目(很简单哒)
· ollama系列01:轻松3步本地部署deepseek,普通电脑可用
· 25岁的心里话
· 按钮权限的设计及实现