攻防世界MISC进阶区—48-51
48.Become_a_Rockstar
得到无类型文件,010 Editor打开为几段话,看到标示性的NCTF{),怀疑是用脚本加密后的结果,网上查了一下,得知Rockstar是一种语言,用rockstar.py解密
(引用一下github上的py:https://github.com/yyyyyyyan/rockstar-py)
运行后得到转化为的python
Leonard_Adleman = "star"
Problem_Makers = 76
Problem_Makers = "NCTF{"
def God(World):
a_boy = "flag"
the_boy = 3
def Evil(your_mind):
a_girl = "no flag"
the_girl = 5
Truths = 3694
Bob = "ar"
Adi_Shamir = "rock"
def Love(Alice, Bob):
Mallory = 13
Mallory = 24
Everything = 114514
Alice = "you"
def Reality(God, Evil):
God = 26
Evil = 235
Ron_Rivest = "nice"
def You_Want_To(Alice, Love, Anything):
You = 5.75428
your_heart = input()
You = 5
your_mind = input()
Nothing = 31
if Truths * Nothing == Everything:
RSA = Ron_Rivest + Adi_Shamir + Leonard_Adleman
if Everything / Nothing == Truths:
Problem_Makers = Problem_Makers + Alice + Bob
print(Problem_Makers)
the_flag = 245
the_confusion = 244
print(RSA)
Mysterious_One = "}"
print(Mysterious_One)
This = 4
This = 35
This = 7
This = 3
This = 3
This = 37
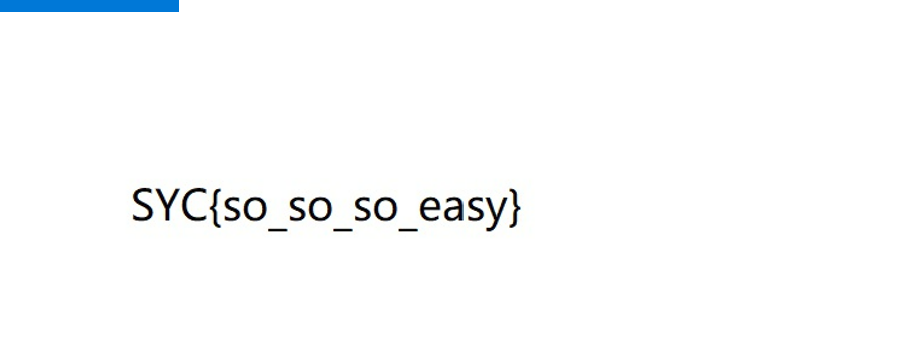
运行即可得到flag(但是在运行时需要先输入1和2)
49.小小的PDF
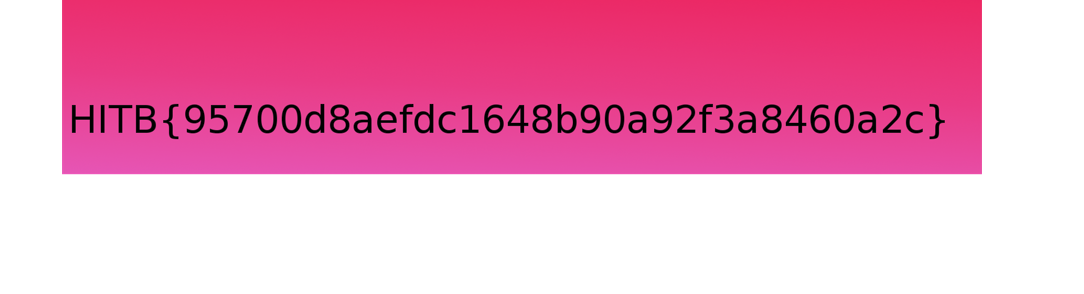
打开后,扔入kali中,binwalk一下,发现有隐藏文件,foremost分离,得到额外的一张图片,上面就是flag
50.intoU
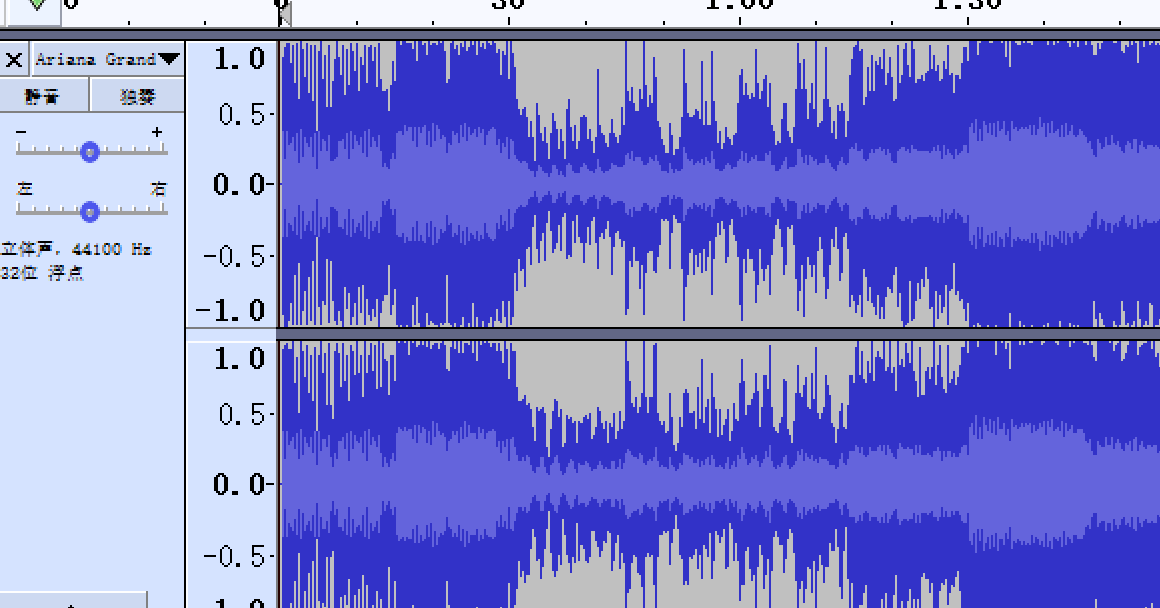
得到一个wav,直接放入Audacity中先看一下
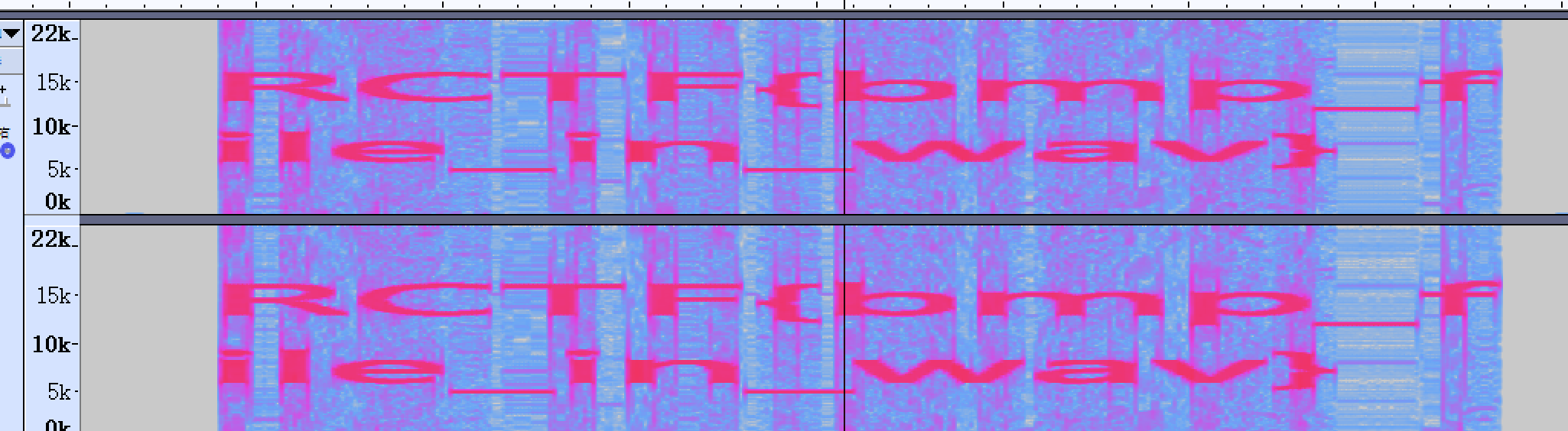
查看频谱图,缩放到合适大小后就可以在末尾看到flag
51.Cephalopod
得到pcap文件,协议分级统计,大部分为tcp
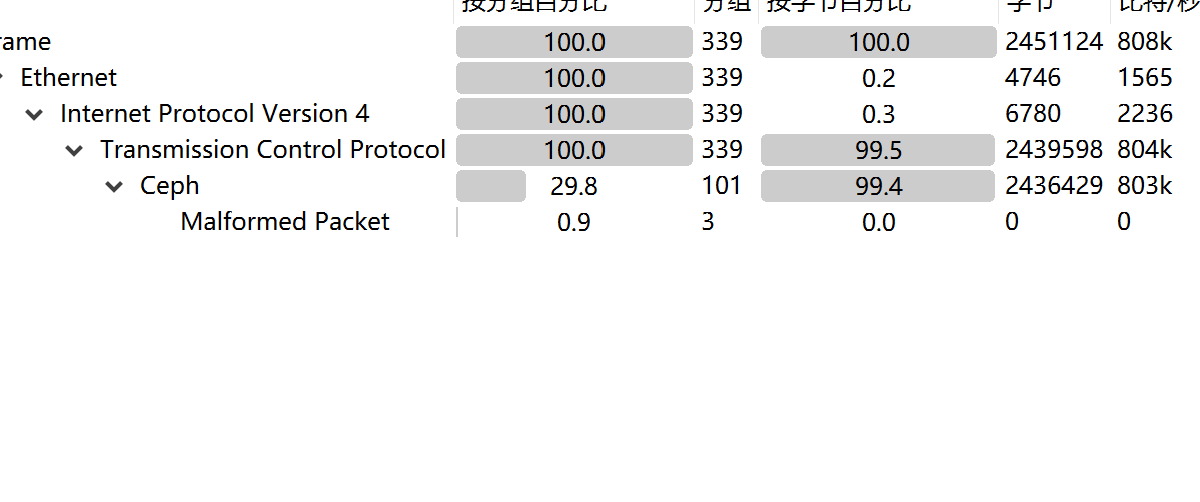
搜索关键字,flag得到png
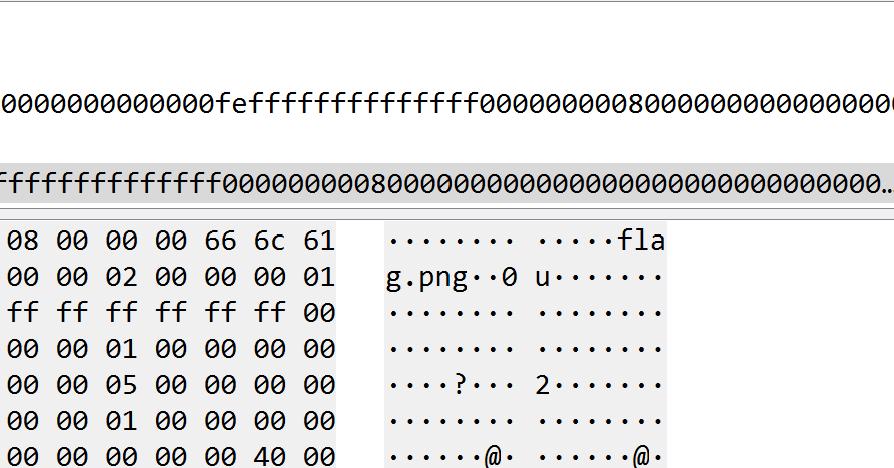
NetworkMiner跑一下什么都没找到,foremost也什么都没有,binwalk 一下确实是有png的数据,需要使用tcpxtract
安装方法:sudo apt-get install tcpxtract
提取数据:tcpxtract -f 文件名.pcap
得到两张图片,其中一张在颜色断层处有flag