第一章课后案例
第一章课后案例
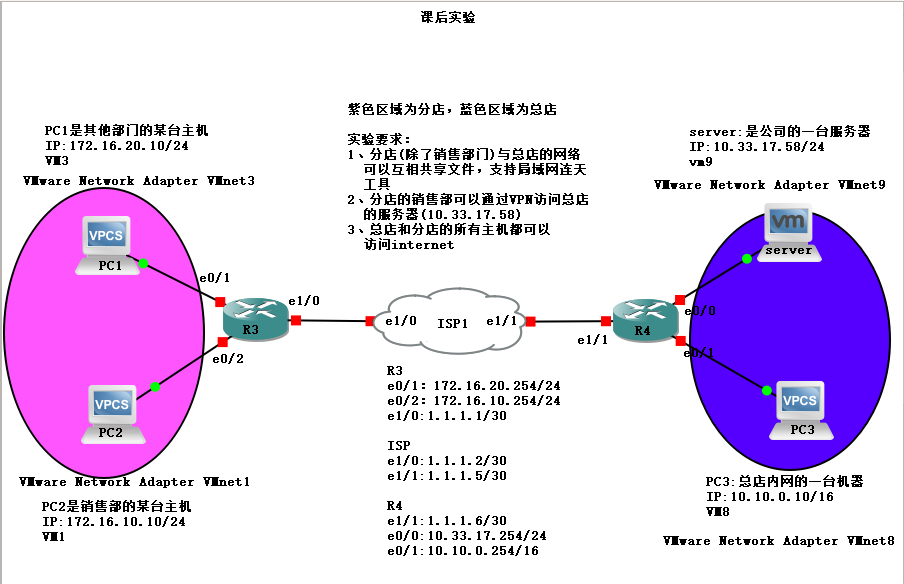
一、实验环境与要求
拓扑图如下
由于本人电脑性能不足,实在带不起来折磨多,所以我只做了可以ping通,并没有测试各种服务
配置步骤:
1、配置IP
2、R3 和 R4 配置默认路由
3、配置VPN
4、配置ACL
5、配置NAT
配置:
前两步我就不说了,基本配置
三、配置VPN
- 配置ISAKMP策略
1 R3 2 R3(config)#crypto isakmp policy 1 3 R3(config-isakmp)#encryption 3des 4 R3(config-isakmp)#hash sha 5 R3(config-isakmp)#authentication pre-share 6 R3(config-isakmp)#group 2 7 R3(config-isakmp)#lifetime 10000 8 R3(config-isakmp)#exit 9 R3(config)#crypto isakmp key 0 xuan address 1.1.1.6 10 11 R4 12 R4(config)#crypto isakmp policy 1 13 R4(config-isakmp)#encryption 3des 14 R4(config-isakmp)#hash sha 15 R4(config-isakmp)#authentication pre-share 16 R4(config-isakmp)#group 2 17 R4(config-isakmp)#lifetime 10000
- 配置预共享密钥
1 R3 2 R3(config)#crypto isakmp key 0 xuan address 1.1.1.6 3 4 R4 5 R4(config)#crypto isakmp key 0 xuan address 1.1.1.1
- 配置Crypto map
1 R3(config)#access-list 100 permit ip 172.16.10.0 0.0.0.255 host 10.33.17.58 2 R3(config)#access-list 100 permit ip 172.16.20.0 0.0.0.255 10.10.0.0 0.0.255.255 3 R3(config)#access-list 100 permit ip permit ip 172.16.20.0 0.0.0.255 10.10.17.0 0.0.0.255 4 5 R4 6 R4(config)#access-list 100 deny ip 10.10.0.0 0.0.255.255 172.16.10.0 0.0.0.255 7 R4(config)#access-list 100 permit ip host 10.33.17.58 172.16.10.0 0.0.0.255 8 R4(config)#access-list 100 deny ip 10.33.17.0 0.0.0.255 172.16.10.0 0.0.0.255 9 R4(config)#access-list 100 permit ip 10.10.0.0 0.0.255.255 172.16.0.0 0.0.255.255 10 R4(config)#access-list 100 permit ip 10.33.17.0 0.0.0.255 172.16.0.0 0.0.255.255
- 配置传输集
1 R3 2 R3(config)#crypto ipsec transform-set set-3 esp-des ah-sha-hmac 3 R3(cfg-crypto-trans)#mode tunnel 4 R3(cfg-crypto-trans)#exit 5 R3(config)#crypto ipsec security-association lifetime seconds 1800 6 7 R4 8 R4(config)#crypto ipsec transform-set set-4 esp-des ah-sha-hmac 9 R4(cfg-crypto-trans)#mode tunnel 10 R4(cfg-crypto-trans)#exit 11 R4(config)#crypto ipsec security-association lifetime seconds 1800
- 配置加密映射
1 R3 2 R3(config)#crypto map map-3 1 ipsec-isakmp 3 R3(config-crypto-map)#set peer 1.1.1.6 4 R3(config-crypto-map)#set transform-set set-3 5 R3(config-crypto-map)#match address 100 6 7 R4 8 R4(config)#crypto map map-4 1 ipsec-isakmp 9 R4(config-crypto-map)#set peer 1.1.1.1 10 R4(config-crypto-map)#set transform-set set-4 11 R4(config-crypto-map)#match address 100
- 端口应用加密映射
1 R3 2 R3(config-crypto-map)#int e 1/0 3 R3(config-if)#crypto map map-3 4 5 R4 6 R4(config-if)#int e 1/1 7 R4(config-if)#crypto map map-4
四、配置nat(PAT)
- 配置ACL
1 R3 2 R3(config)#access-list 110 deny ip 172.16.10.0 0.0.0.255 host 10.33.17.58 3 R3(config)#access-list 110 permit ip 172.16.10.0 any 4 R3(config)#access-list 110 deny ip 172.16.0.0 0.0.255.255 10.10.0.0 0.0.255.255 5 R3(config)#access-list 110 deny ip 172.16.0.0 0.0.255.255 10.33.17.0 0.0.0.255 6 R3(config)#access-list 110 permit ip 172.16.0.0 0.0.255.255 any 7 8 R4 9 R4(config)#access-list 110 deny ip 10.10.0.0 0.0.255.255 172.16.0.0 0.0.255.255 10 R4(config)#access-list 110 deny ip 10.33.17.0 0.0.0.255 172.16.0.0 0.0.255.255 11 R4(config)#access-list 110 permit ip any any
- 配置NAT
1 R3 2 R3(config)#ip nat inside source list 110 interface ethernet 1/0 3 R3(config)#int e 1/0 4 R3(config-if)#ip nat outside 5 R3(config-if)#int e 0/1 6 R3(config-if)#ip nat inside 7 R3(config-if)#int e 0/2 8 R3(config-if)#ip nat inside 9 10 R4 11 R4(config)#int e 1/1 12 R4(config-if)#ip nat outside 13 R4(config-if)#int e 0/0 14 R4(config-if)#ip nat inside 15 R4(config-if)#int e 0/1 16 R4(config-if)#ip nat inside
配置完成,最后的结果是
PC1 ——>PC3 # 可以通
PC2 ——>PC4 # 可以通
所有PC都可以ping通ISP


