Anatomy of computer crime
Note: Followup to this entry at http://tacit.livejournal.com/240750.html
So apparently, Macintosh users are now the targets of Eastern European organized crime.
First, a bit of backstory. Last December, I wrote an article about how I had done a Google search for my name and uncovered a massive hacking attack against a Web hosting company called iPowerWeb. iPower, a company in Phoenix, Arizona, has trouble securing their Web servers, and Russian organized crime can hack any Web site hosted by iPower completely at will.
That was last December. Today, as I write this, iPower still has not fixed their server security; each day, a whole crop of new Web sites hosted by iPower is hacked, and the hackers plant redirectors on the site that are designed to snare unwary visitors and send them to servers in Eastern Europe that attempt to infect users with computer viruses.
For the past couple of months, I have been emailing iPower every day with new lists of hacked Web sites they're hosting. Each day, I bug them to fix their computer security. Each day, they remove the virus redirectors that I tell them about, but they do not fix their server security; so the next day, more of their Web sites are hacked. Some poor sots who host Web sites with iPower have had their sites hacked over and over again.
In the past 48 hours, the nature of the hacks has changed. Between December and now, the hacks were all the same; the hackers would penetrate an iPower Web site, create a directory on the site named /her, create a directory on the site named /bad, and then create a directory with a one or two digit number as a name. The redirector pages would go in the numered directory. This made spotting hacked iPower Web sites trivially easy.
About two days ago, the hackers began changing the naming scheme of the directory. This led me on a path to discovering an entire network of compomised Web sites, feeding into an elaborate underground network of computers used to distribute computer viruses.
And they're distributing Mac viruses now, too.
If you haven't read the earlier post that I linked to above, now would be a good time to do so. It's OK, I'll wait.
Back? Good. Until a couple days ago, finding the hacked sites on iPower was a breeze, because the directory structure was always the same and the hackers used the same keywords to try to poison Google searches. Now, however, the hackers have changed the naming structure of the directories, and they are no longer using the same keywords to try to snare Google searches. They're not using my name often any more, for example.
They are using a number of sex and porn-related keywords, though, some of whihc are very unusual. The Google cache of hacked iPower Web sites provides an easy way to compile lists of words and phrases that are common to all the hacked sites, and searching on Google for these words and phrases yields a treasure trove of Web sites that have been hacked.
Interestingly, these words and phrases also show up in many, many forum posts, almost all of them on forums running phpBB or phpNuke software, and invariably old, insecure versions of this software.
It also produces lists of domains with strange names, such as http://6.bgmww-news.info/ and http://3.vxwzj-news.info/,
WARNING *** WARNING *** WARNING
The links here and elsewhere in this post are live. As of the time of this writing, they redirect to active virus distributors which can and will infect unpatched Windows computers, and in one case will try to infect Mac computers, with a virus. DO NOT click on these links if you don't know what you're doing. DO NOT allow any of these sites to download or install software onto your computer.
So we see a pattern: certain words and phrases, appearing over and over again in hacked Web sites hosted by iPowerWeb, and also appearing in messages placed on hacked phpBB and phpNuke forums, and also appearing in domains with strange names.
In each case, visiting one of the hacked iPower Web sites, reading one of the messages in a hacked forum, or visiting one of the strange domains does the same thing. And, interestingly, it reveals an elaborate network of computers all intended to transmit viruses while obscuring the source of the viruses. Ready to go down the rabbit hole? Here we go!
The central lynchpin of the entire network is a site called traffloader.info. Traffloader.info is a Web sitehosted by an outfit called leaseweb.com (Edit: As of April 8, 2008, traffloader.info is off Leaseweb and is now being hosted in the country of Moldovia), which also hosts the sites with strange domains. If you visit traffloader.info in your browser, you'll see nothing but a blank page; it sends back no HTML code at all. There appears to be nothing there.
But all the hacked iPower Web sites, all the messages placed on hacked forums,a nd all the strange domains that are hosted by leaseweb.com all redirect to traffloader.info. Specifically, they redirect to a script on traffloader.info called "go.php". Here's how it works.
A person does a Google search for certain comon, popular keywords. It might be my name, or "free sex movies," or "build ultralight helicopters"--they create hundreds of thousands of lists of popular keywords, which they place on hacked Web sites, into hacked message board posts, or onto domains they either create or hack.
The person sees one of the attack pages in Google and clicks on the Google result. The page or message board post redirects the user to http://traffloader.info/go.php, and usually includes information about where the user came from, presumably so the hackers can tell which particular hacked sites are most effective. The information passed to the script varies, but often includes the name of the hacked site the user came from, and the Google keywords used.
Traffloader.info then redirects the user to any one of a bunch of other sites. These other sites might look like porn sites, and try to download a virus disguised as movie player software. They might look like virus scanner sites,and try to download a virus disguised as antivirus software. Sometimes, the sites have embedded iFrames or redirectors that will try to download additional files to the user's computer.
I've spent hours tracing the way the system works. Here's a bird's eye overview:
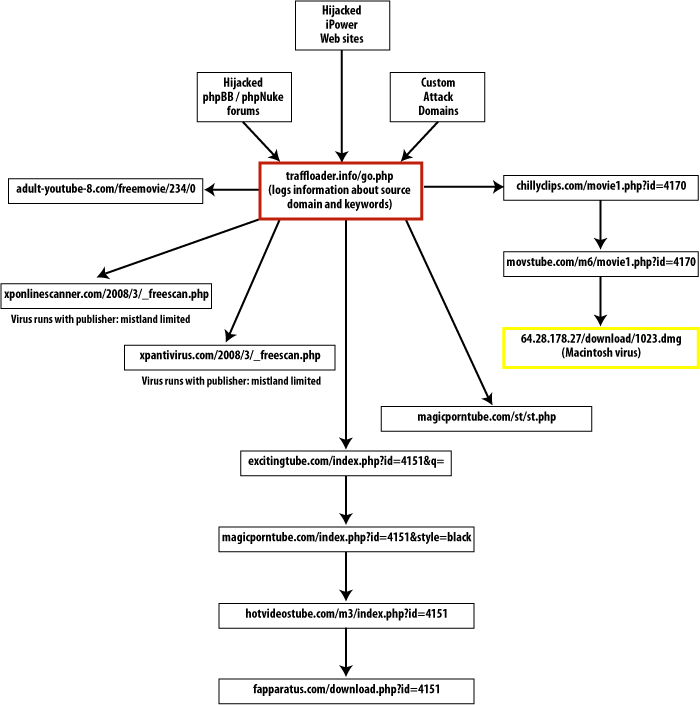
A user clicks on a Google search that leads to a hacked iPower site, a hacked forum post, or a domain hosted by leaseweb.com. The user is redirected to traffloader.info, which records information about where the user came from and what keywords he used. The script at traffloader.info then sends the user to a site such as
adult-youtube-8.com/freemovie/234/0
or
xpantivirus.com/2008/3/_freescan.php
which attempts to download a virus.
The site that the user ends up on seems to be chosen more or less at random (at least if there's a system behind it, I haven't been able to figure out what that system is yet). Some of the sites are more sophisticated than others; some of the sites redirect the user to other sites. For example, traffloader.info will sometimes send the user to a script hosted at chillyclips.com/movie1.php which will in turn send the user to movstube.com/movie1.php.
Now, movstube.com is a particularly interesting payload site. Unlike all the other sites, it attempts to attack both Mac and Windows machines; all the other sites host Windows-specific attacks.
The script at movstube.com checks the browser's "user agent". For folks who don't know a lot about how browsers work, each time your Web browser accesses a Web site, it tells the site what it is and what kind of computer you have. When you go to a Web site, your browser might say "Hi there! I'm Internet Explorer 7 running on Windows XP" or "Hello! I'm Safari running on an Intel Mac".
The script at movstube.com looks at this user agent. If it sees a Windows user agent, it attempts to download a Windows virus pretending to be movie viewer software, just like many of the other sites do.
But...
But if the script sees a Mac user agent, it sends the browser to
http://64.28.178.27/download/1023.dmg
The file 1023.dmg is a Macintosh disk image file. It contains an installer that attempts to install a piece of Mac malware variously called OSX/DNSChanger or OSX.RSPlug.A. This is a Trojan horse that attempts to modify the Mac's domain name server settings so that a Mac user who surfs the Web can be secretly redirected to sites controlled by the Russian malware writers, without knowing it.
The good news is that the Mac malware can not infect a computer without help. You must choose to install it and you must type your administrator password in order to be infected. The bad news: clearly, the Mac is now on the radar of malware writers.
Some of the sites in the network controlled by traffloader.info are believed or known to be associated with the Russian Business Network, an organized group of Eastern European criminals. The fact that the attacks on iPower use payload sites known or believed to be controlled by RBN suggests strongly that RBN is behind the iPower hacks. It also suggests strongly that RBN is either responsible for or associated with the people responsible for the Mac malware.
I first notified iPower that their Web server security had been breached last December. As of today, there are still new hacked sites appearing on their servers daily.
The whois information shows something very interesting, as well. All of these computers associated with virus distribution -- traffloader.info, movstube.com, xpantivirus.com, chillyclips.com, magicporntube.com, and so on--every one, without exception, is registered by the same registrar: a place called estdomains.com. Each of these Web sites is known to be associated with virus distribution on behalf of organized crime, yet each of them is still active and resolving, and each has the same registrar.
Yep, that's estdomains.com - the choice of organized crime.
So apparently, Macintosh users are now the targets of Eastern European organized crime.
First, a bit of backstory. Last December, I wrote an article about how I had done a Google search for my name and uncovered a massive hacking attack against a Web hosting company called iPowerWeb. iPower, a company in Phoenix, Arizona, has trouble securing their Web servers, and Russian organized crime can hack any Web site hosted by iPower completely at will.
That was last December. Today, as I write this, iPower still has not fixed their server security; each day, a whole crop of new Web sites hosted by iPower is hacked, and the hackers plant redirectors on the site that are designed to snare unwary visitors and send them to servers in Eastern Europe that attempt to infect users with computer viruses.
For the past couple of months, I have been emailing iPower every day with new lists of hacked Web sites they're hosting. Each day, I bug them to fix their computer security. Each day, they remove the virus redirectors that I tell them about, but they do not fix their server security; so the next day, more of their Web sites are hacked. Some poor sots who host Web sites with iPower have had their sites hacked over and over again.
In the past 48 hours, the nature of the hacks has changed. Between December and now, the hacks were all the same; the hackers would penetrate an iPower Web site, create a directory on the site named /her, create a directory on the site named /bad, and then create a directory with a one or two digit number as a name. The redirector pages would go in the numered directory. This made spotting hacked iPower Web sites trivially easy.
About two days ago, the hackers began changing the naming scheme of the directory. This led me on a path to discovering an entire network of compomised Web sites, feeding into an elaborate underground network of computers used to distribute computer viruses.
And they're distributing Mac viruses now, too.
If you haven't read the earlier post that I linked to above, now would be a good time to do so. It's OK, I'll wait.
Back? Good. Until a couple days ago, finding the hacked sites on iPower was a breeze, because the directory structure was always the same and the hackers used the same keywords to try to poison Google searches. Now, however, the hackers have changed the naming structure of the directories, and they are no longer using the same keywords to try to snare Google searches. They're not using my name often any more, for example.
They are using a number of sex and porn-related keywords, though, some of whihc are very unusual. The Google cache of hacked iPower Web sites provides an easy way to compile lists of words and phrases that are common to all the hacked sites, and searching on Google for these words and phrases yields a treasure trove of Web sites that have been hacked.
Interestingly, these words and phrases also show up in many, many forum posts, almost all of them on forums running phpBB or phpNuke software, and invariably old, insecure versions of this software.
It also produces lists of domains with strange names, such as http://6.bgmww-news.info/ and http://3.vxwzj-news.info/,
WARNING *** WARNING *** WARNING
The links here and elsewhere in this post are live. As of the time of this writing, they redirect to active virus distributors which can and will infect unpatched Windows computers, and in one case will try to infect Mac computers, with a virus. DO NOT click on these links if you don't know what you're doing. DO NOT allow any of these sites to download or install software onto your computer.
So we see a pattern: certain words and phrases, appearing over and over again in hacked Web sites hosted by iPowerWeb, and also appearing in messages placed on hacked phpBB and phpNuke forums, and also appearing in domains with strange names.
In each case, visiting one of the hacked iPower Web sites, reading one of the messages in a hacked forum, or visiting one of the strange domains does the same thing. And, interestingly, it reveals an elaborate network of computers all intended to transmit viruses while obscuring the source of the viruses. Ready to go down the rabbit hole? Here we go!
The central lynchpin of the entire network is a site called traffloader.info. Traffloader.info is a Web site
But all the hacked iPower Web sites, all the messages placed on hacked forums,a nd all the strange domains that are hosted by leaseweb.com all redirect to traffloader.info. Specifically, they redirect to a script on traffloader.info called "go.php". Here's how it works.
A person does a Google search for certain comon, popular keywords. It might be my name, or "free sex movies," or "build ultralight helicopters"--they create hundreds of thousands of lists of popular keywords, which they place on hacked Web sites, into hacked message board posts, or onto domains they either create or hack.
The person sees one of the attack pages in Google and clicks on the Google result. The page or message board post redirects the user to http://traffloader.info/go.php, and usually includes information about where the user came from, presumably so the hackers can tell which particular hacked sites are most effective. The information passed to the script varies, but often includes the name of the hacked site the user came from, and the Google keywords used.
Traffloader.info then redirects the user to any one of a bunch of other sites. These other sites might look like porn sites, and try to download a virus disguised as movie player software. They might look like virus scanner sites,and try to download a virus disguised as antivirus software. Sometimes, the sites have embedded iFrames or redirectors that will try to download additional files to the user's computer.
I've spent hours tracing the way the system works. Here's a bird's eye overview:

A user clicks on a Google search that leads to a hacked iPower site, a hacked forum post, or a domain hosted by leaseweb.com. The user is redirected to traffloader.info, which records information about where the user came from and what keywords he used. The script at traffloader.info then sends the user to a site such as
adult-youtube-8.com/freemovie/234/0
or
xpantivirus.com/2008/3/_freescan.php
which attempts to download a virus.
The site that the user ends up on seems to be chosen more or less at random (at least if there's a system behind it, I haven't been able to figure out what that system is yet). Some of the sites are more sophisticated than others; some of the sites redirect the user to other sites. For example, traffloader.info will sometimes send the user to a script hosted at chillyclips.com/movie1.php which will in turn send the user to movstube.com/movie1.php.
Now, movstube.com is a particularly interesting payload site. Unlike all the other sites, it attempts to attack both Mac and Windows machines; all the other sites host Windows-specific attacks.
The script at movstube.com checks the browser's "user agent". For folks who don't know a lot about how browsers work, each time your Web browser accesses a Web site, it tells the site what it is and what kind of computer you have. When you go to a Web site, your browser might say "Hi there! I'm Internet Explorer 7 running on Windows XP" or "Hello! I'm Safari running on an Intel Mac".
The script at movstube.com looks at this user agent. If it sees a Windows user agent, it attempts to download a Windows virus pretending to be movie viewer software, just like many of the other sites do.
But...
But if the script sees a Mac user agent, it sends the browser to
http://64.28.178.27/download/1023.d
The file 1023.dmg is a Macintosh disk image file. It contains an installer that attempts to install a piece of Mac malware variously called OSX/DNSChanger or OSX.RSPlug.A. This is a Trojan horse that attempts to modify the Mac's domain name server settings so that a Mac user who surfs the Web can be secretly redirected to sites controlled by the Russian malware writers, without knowing it.
The good news is that the Mac malware can not infect a computer without help. You must choose to install it and you must type your administrator password in order to be infected. The bad news: clearly, the Mac is now on the radar of malware writers.
Some of the sites in the network controlled by traffloader.info are believed or known to be associated with the Russian Business Network, an organized group of Eastern European criminals. The fact that the attacks on iPower use payload sites known or believed to be controlled by RBN suggests strongly that RBN is behind the iPower hacks. It also suggests strongly that RBN is either responsible for or associated with the people responsible for the Mac malware.
I first notified iPower that their Web server security had been breached last December. As of today, there are still new hacked sites appearing on their servers daily.
The whois information shows something very interesting, as well. All of these computers associated with virus distribution -- traffloader.info, movstube.com, xpantivirus.com, chillyclips.com, magicporntube.com, and so on--every one, without exception, is registered by the same registrar: a place called estdomains.com. Each of these Web sites is known to be associated with virus distribution on behalf of organized crime, yet each of them is still active and resolving, and each has the same registrar.
Yep, that's estdomains.com - the choice of organized crime.


